
2023-8-30 19:38:7 Author: www.forcepoint.com(查看原文) 阅读量:14 收藏
For years, the problem with concealed malware has been addressed by trying to detect it before it reaches the target destination. However, every time a new method of detection is devised, attackers remain one step ahead, working out new ways of evading current technologies. Using everything from highly evasive exploits and steganography to polymorphic and poly formatted files.
Detection-based defences simply can’t keep up…
Stop The Threats of Tomorrow, Today.
If someone said, there’s a way to eliminate malware forever! It would definitely sound too good to be true, right? That’s because we’re so accustomed with detection-based solutions, that ultimately will never provide complete protection of your data.
That’s why leading cybersecurity professionals worldwide are turning their attention to prevention-based cybersecurity technologies and solutions.
Forcepoint’s Zero Trust Content Disarm and Reconstruction (CDR) technology has zero reliance on detection when looking to determine if files and images contains a threat. It doesn’t try to make educated guesses as to whether some particular piece of content is intrinsically good or bad. Instead, Zero Trust CDR trusts nothing and renders everything safe, using a unique process called transformation. Defeating any potentially malicious content embedded in documents and images – even zero-day attacks.
Whatever the exploit and whatever the motive, Zero Trust CDR ensures that documents and images are entirely threat-free with no false positives.
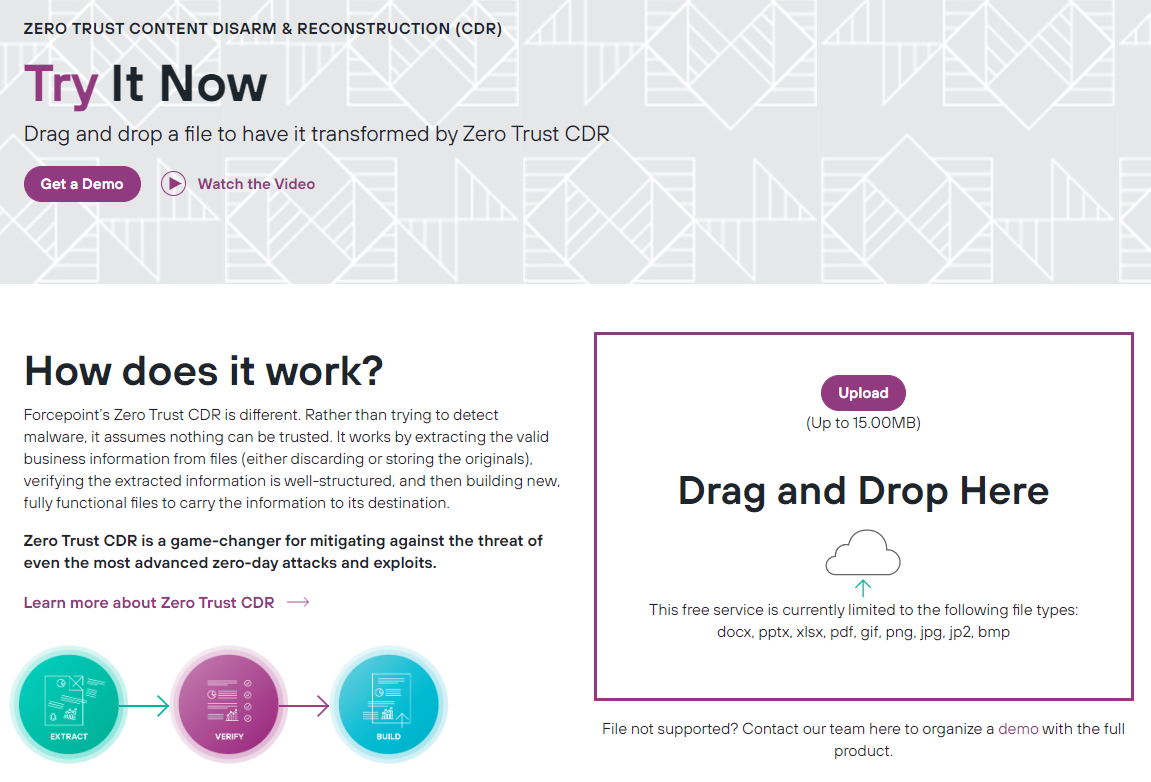
Still sound too good to be true? Understandable, that’s why we’ve created an online version of the Zero Trust CDR Technology.
Drag and drop any file and have it transformed and ready to download completely malware free within seconds. Try it online here.
Transform your Cyber Defence
Zero Trust CDR has been tested and proven against over 30 million viruses, and completely eliminates all malware including:
- Zero-day exploits.
- Ransomware attacks.
- Sandbox evading detonation attacks.
- Fileless malware - That takes advantage of applications to “live off the land”, never being written to disk and therefore never being seen by detection-based virus scanners.
- Polymorphic malware.
- Image-based malware attacks and Steganography.
- If there is a threat carried or concealed in digital content, Zero Trust CDR will defeat it.
Read the 30 Million Viruses Report
Zero Trust CDR Deployment Capabilities
Zero Trust Content Disarm and Reconstruction (CDR) can be deployed alongside or instead of your existing defences. Email (on-premise or directly integrated with Microsoft 365 Mail,) web, file uploads and downloads, portal protection, social, chat and more. Including within Cross Domain Solutions or any scenario that involves accepting data from an untrusted source.
How Does it Work?
Rather than trying to detect malware, Zero Trust CDR’s transformation technology works by:
- Extracting the valid business information from files (either discarding or storing the originals.)
- Verifying the extracted information is well-structured and then,
- Building a brand-new file to carry the information to its destination.
This transformation-based approach is recommended by multiple government cyber agencies because it delivers complete malware protection, every time.
See how it works in our 2 minute explainer video.

What Are The Key Business Benefits You Can Expect?
Upgrade to Prevention Technology
- Completely threat-free files that are pixel perfect and fully editable.
- No risk from even the most sophisticated attacks.
- No exposure to unknown threats or “zero day” malware.
- Stops malware, malicious file uploads and protects isolated networks.
- Secure your data and reduce the risk of ransomware.
Highly versatile
- Transforms a wide range of the most popular/ maliciously used file formats including Office files, images, see more file formats.
- Including PDFs, the most commonly used format by attackers.
- Is available for web browsing, email, file upload, file sharing and many more use cases.
- Choice of on-premise, virtual and cloud-native deployment options.
Easy to deploy.
- Replace or bolster your current detection-based anti-virus at the boundary or augment an existing defence.
- Zero Trust CDR Cloud Solutions be deployed and working within hours.
- Can be integrated into native cloud applications with as little as 4 lines of code.
- Protect Microsoft 365 inboxes with a direct integration API.
Reduces operational costs.
- Reduced administrative costs - no signature updates/security patches required.
- Reduced SOC costs/remediation costs.
- Easy to manage.
Forcepoint’s Zero Trust Content Disarm and Reconstruction (CDR) solves the biggest cybersecurity problem of the information age. How do we stop incoming malware?
By giving complete confidence that incoming files and data are malware-free. Zero Trust CDR drives home just how crucial it is to move beyond detection and get ahead of threats and cybercriminals alike.
Don’t wait until it’s too late, upgrade to prevention cybersecurity today with Zero Trust CDR.
Schedule a demo call with a Zero Trust CDR Specialist here.
如有侵权请联系:admin#unsafe.sh