2023-9-12 23:56:37 Author: blog.qualys.com(查看原文) 阅读量:14 收藏
Qualys Blog Series – 2023 TotalCloud Security Insights by the Threat Research Unit
The 2023 TotalCloud Security Insights report from the Qualys Threat Research Unit (TRU) provides research insights, best practices, and detailed recommendations organized by five separate Risk Facts. The insights will enable organizations using cloud technologies to better understand these risks and how they can be better prepared to face those challenges in today’s threat landscape.
In this final blog post, we look at Risk Fact #5 – Keeping the pace of remediation at the cloud scale requires automation.
Using an Automated Patching Approach
Our data analysis highlights the significant value of implementing automated patch management for organizations operating in the cloud. Patch management accelerates the remediation process, offering a quicker resolution than organizations not using this tool. Also, it noticeably diminishes the number of unresolved vulnerabilities, solidifying its place as a crucial element of a robust cybersecurity program.
The threat data indicate a positive trend of automation improving remediation efforts. Automation entails varying degrees — some risky elements cannot be automated into remediation, like correcting misconfigurations and replacing unsupported software. However, most patch management functions can be automated, and the data continues showing the benefits automation provides to accelerating the pace of remediation across the vast scope of a cloud environment.
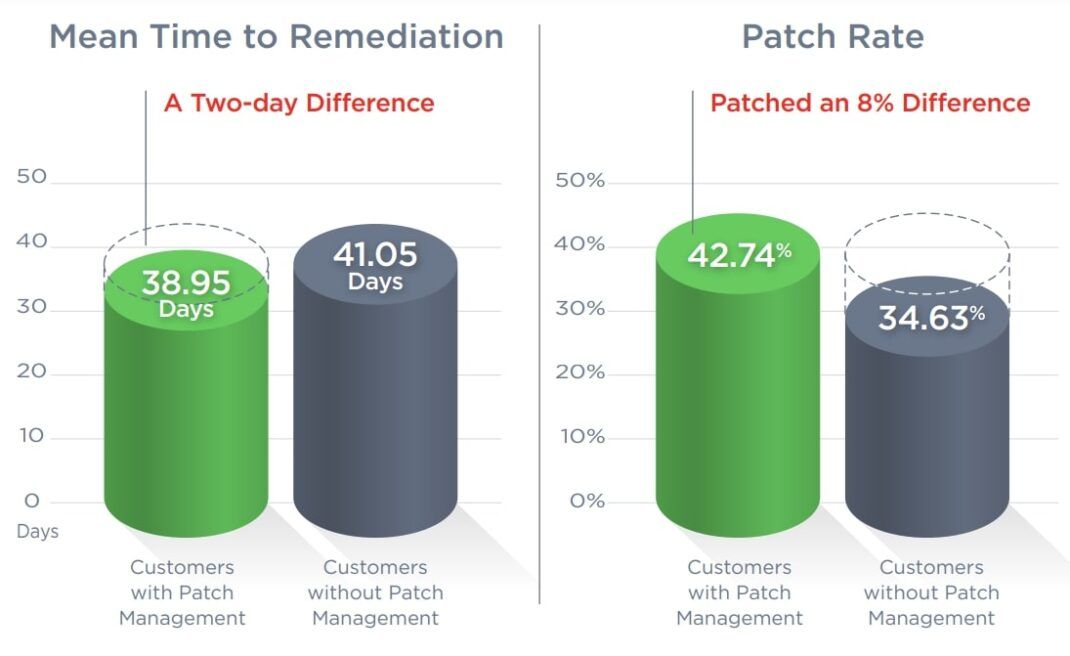
The benefits are more prominent when comparing the difference in automated patch management versus manual patch management for non-Windows patches. There is almost an 8% difference in the patch rate and a two-day difference in time to remediate.
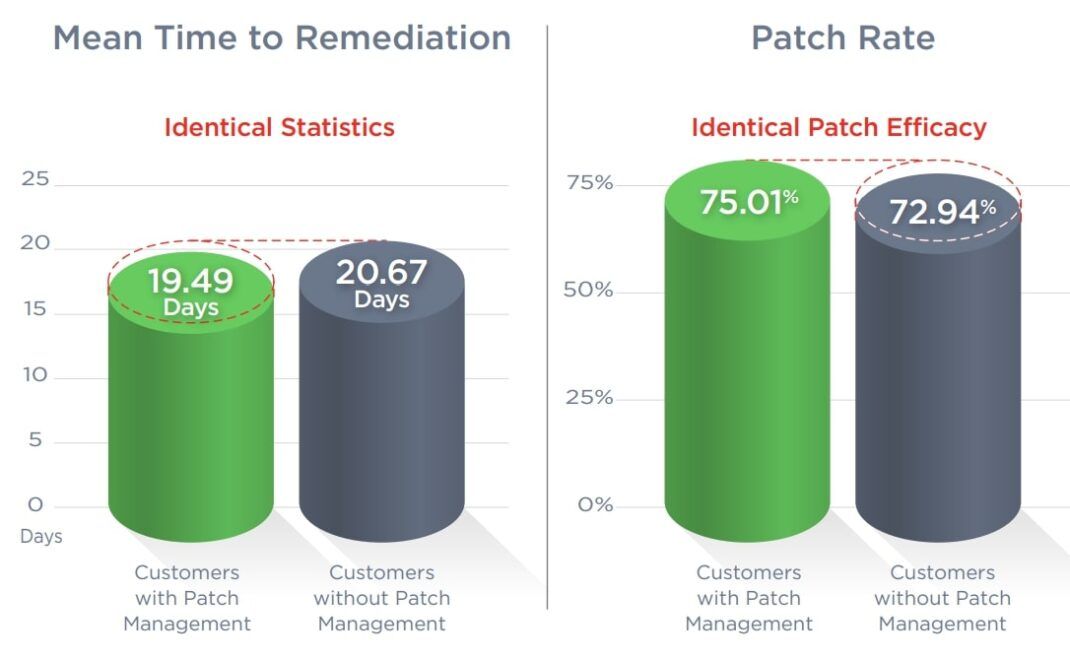
Interestingly, the difference between Mean-Time-to-Remediation for Windows patches versus everything else is identical to the statistics reported in our annual 2023 Qualys TruRisk Research Report earlier this year, specifically where the time to remediate is double for non-Microsoft patches. Even the patch efficacy is identical to the annual report, where Windows patches are applied twice as often as non-Windows patches.
In almost every instance, automated patching proves to be a more effective remediation path than hoping manual efforts will effectively deploy critical patches and keep your business safer. As Qualys customers have discovered, pairing the value of the Qualys TruRisk score with the ease of automated patching lets your business tackle your most critical weaknesses before the adversary. Who does not want to avoid an emergency call on a Friday night or over the weekend?
Understanding and Prioritizing Cloud Technical Debt
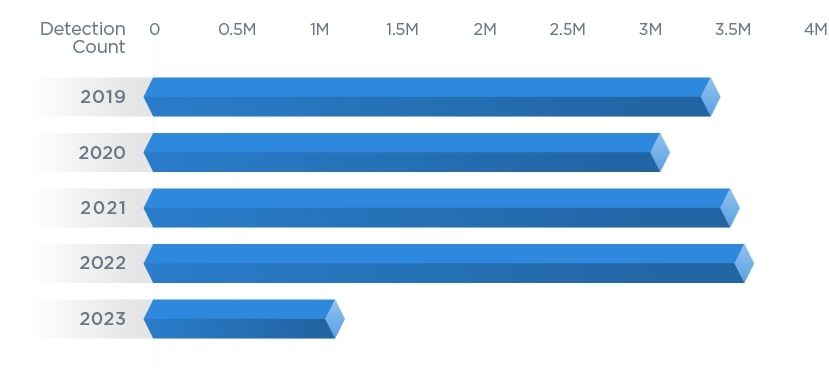
Over 60 million applications discovered during our investigation are end-of-support (EOS) and end-of-life (EOL). As a result, housekeeping is a significant challenge that globally extends into cloud workloads.
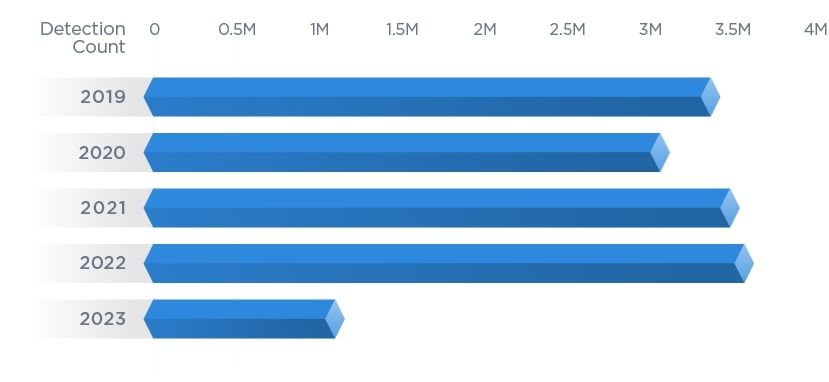
While remediating existing EOL/EOS software is critical, looking forward to and planning for similar activities is also essential. Organizations should expect an influx of software to no longer receive security updates — a massive risk for cloud-hosted applications. During the next 12 months, more than 35,000 applications will go end-of-support.
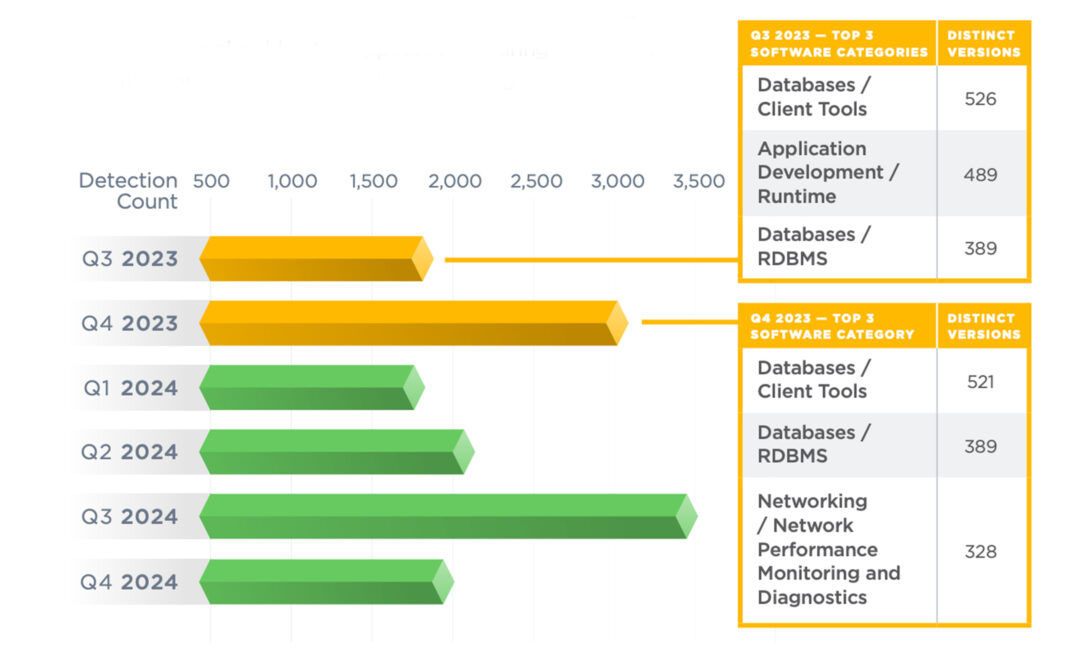
Data-hosting apps are especially at risk. Over the next two quarters, many tools for managing and running databases will no longer receive any updates, with Database Client Tools at the top of the list for both quarters. Meanwhile, the Relational Database Management Systems (RDBMS) are third and second on the Q3 2023 and Q4 2023 lists, respectively.
Databases are a critical category in cloud environments, as tracked by the Qualys Threat Research Unit, with the others being Security Software and Web Applications. For those three categories that have already stopped receiving any updates, there are more than seven million instances of such applications running in cloud environments — all require immediate remediation.
Database Servers and Web Servers typically support business-critical services. When vulnerabilities are disclosed on these software applications, teams must prioritize patching them. However, if these are end-of-support (EOS), patches are no longer provided by the software publisher. In this case, teams struggle to upgrade/migrate them to newer versions because they first need to test compatibility, perform regression testing, and plan downtime.
Critical Insights from Risk Fact 5
Addressing the issue of End-of-Support (EOS) and End-of-Life (EOL) software is an urgent priority, given that more than 60 million applications currently running in organizations’ clouds.
We recommend that organizations create a plan to replace EOS/EOL applications — especially with the looming halt of security updates for over 35,000 applications in the next 12 months. Organizations should prioritize critical software categories, such as databases, security software, and web applications, which face significant risk once updates cease.
To learn more about the five cloud security Risk Facts and detailed recommendations, download your copy of Qualys 2023 TotalCloud Security Insights.
Read the previous blog from this series: Malware in your Cloud Means Exploitation is Underway
Get the full Qualys 2023 TotalCloud Security Insights and learn about all five Cloud Risk Facts now.
如有侵权请联系:admin#unsafe.sh