
2023-9-22 21:0:31 Author: www.sentinelone.com(查看原文) 阅读量:17 收藏
The Good | New Working Group to Focus Efforts on Threats in Undermonitored Regions
This week at the annual LABScon cybersecurity event, SentinelLabs launched a concerted effort against state-aligned cyber activities in areas like Africa and Latin America – regions that often receive less representation within the threat intelligence industry.
Researcher Tom Hegel unveiled a new “Undermonitored Regions Working Group” (URWG), calling for security researchers worldwide to pool analytic capabilities, telemetry, resources, and local expertise to build a unified front against geopolitical cyber operations occurring in such regions.
Up now at #LABScon23: SentinelLabs researcher Tom Hegel with an examination of China’s strategic use of technological soft-power strategies @TomHegel pic.twitter.com/yVVorVhZIs
— LABScon (@labscon_io) September 21, 2023
China has a long history of using soft power diplomacy to achieve its objectives in Africa. Hegel said many African nations present a highly complex and dynamic environment caught in debt-trap diplomacy with China. Through various cyber operations designed to form a foundation of influence over the continent, these attacks have focused on government, finance, and telecommunications sectors to strengthen their foothold.
As China continues to finance large critical infrastructure projects in African countries, it is imperative for the cyber research community to better understand what will likely be a future threat arena.
Efforts like URWG aim to incentivize strategic intelligence on the state of threat operations in Africa while pointing the spotlight on how to improve the communities’ understanding of China’s geostrategic ambitions. By establishing a concentrated channel for collaboration amongst cyber threat researchers and analysts now, cross-national efforts like URWG are key to closing situational awareness gaps in the changing cyber threat landscape and addressing issues arising in less-monitored regions that are too often sidelined in wider cybersecurity discussions.
URWG is currently made up of participants from several security vendors and is recruiting new members looking to creatively disrupt current and future PRC-backed operations.
The Bad | Multiple Organizations Breached with Old Malicious Thumb Drive Trick
Further contemplating malicious activity by Chinese-linked threat actors, security researchers this week revealed that hacker group UNC53 recently attacked at least 29 organizations with a blast from the past – malware-laden USBs. Taking advantage of those in developing countries known for their continued use of older technologies, UNC53 infected dozens of networks within the African branches of US and European firms.

Thumb drive attacks are considered an old-school approach to the more technologically forward regions of the world. However, for victim organizations in Egypt, Ghana, Kenya, Madagascar, Tanzania, and Zimbabwe that appear to have overlooked the need for device control, it has proved an effective route to compromise. UNC53’s attacks involved a decade-old malware payload dubbed “Sogu” and a variant of PlugX used as a loader. The malware is spread via USB drives found amongst shared computers in local internet cafés and print shops.
China has been known to employ Sogu and PlugX over the past decade, and newer versions were noted in January of 2022 that were traced back to infected thumb drives.
According to security researchers, UNC53 may be focused on targeting African operations specifically, given their strategic and geoeconomic interest in the continent. Since the passing-along of thumb drives casts such a wide net, UNC53’s efforts could be interpreted as an indiscriminate way of conducting cyber espionage as they can then pick out high-value targets from many.
The rising reappearance of USB malware shows that even older methods of attack are still potent when used in the right environment. With many multinational operations employing remote workers in developing geographies of the world, all types of infection vectors must be considered relevant and addressed by security practitioners.
The Ugly | Sandman APT Targets Telecom Sector With LuaDream Backdoor
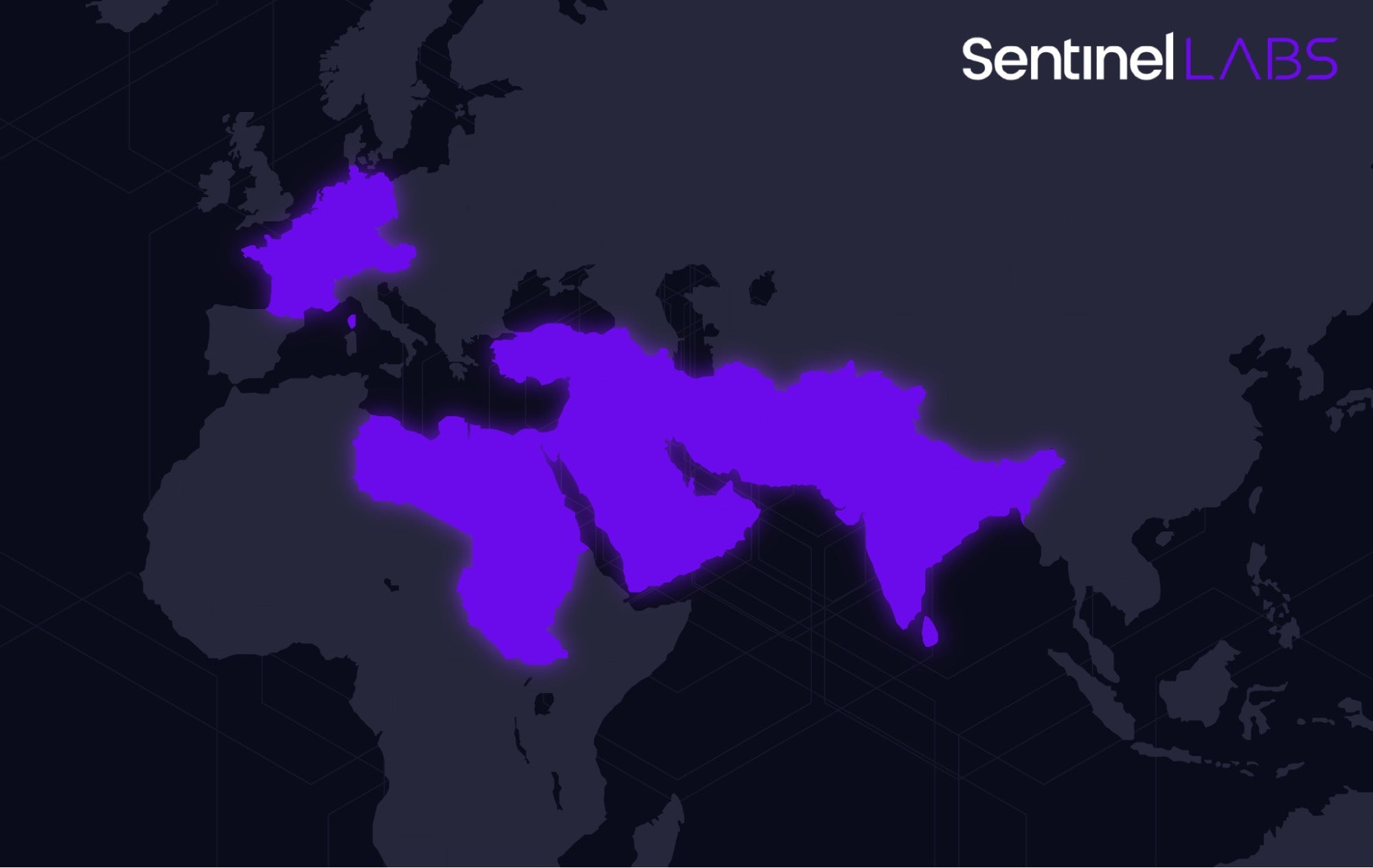
Researchers reported new activity by a mystery threat actor this week that has set its sights on targeting telecommunication providers across the Middle East, Western Europe, and South Asia.
Dubbed Sandman, the newly-identified threat actor has been observed deploying a rare, modular backdoor that leverages the LuaJIT platform to infect its victims. Researchers have dubbed the malware “LuaDream” and characterized it as a part of a well-executed and actively developed project of considerable scale.
Over several weeks in August, Sandman stole administrative credentials and performed reconnaissance using the Pass-the-Hash technique to infiltrate targeted workstations, many of which belonged to managers in the victim organizations.
After gaining access, Sandman limited its activities to deploying folders and files required for loading and executing LuaDream, refraining from any further actions. The cluster of activities attributed to Sandman were described as strategic lateral movement with minimal engagement to evade detection and analysis.
For now, the threat actor seems to be focused on targeting data-rich telecom providers, and its operations strongly indicate cyber espionage as the primary objective. The researchers speculate that the APT group may be a private contractor or mercenary group, similar to the enigmatic Metador. Both Metador and now Sandman make up an emerging class of threat actors that continue to operate in the shadows with impunity.
This recent cluster of activity throws into sharp relief the ongoing innovation and development efforts of cyber espionage-based threat actors, again underscoring the importance of collaboration and intel sharing amongst the threat research community. Indicators of compromise for LuaDream are listed here.
如有侵权请联系:admin#unsafe.sh