QR codes are everywhere: you can see them on posters and leaflets, ATM screens, price tags and merchandise, historical buildings and monuments. People use them to share information, promote various online resources, pay for their goodies, and pass verification. And yet you don’t see lots of QR codes in email: users often read messages on their phones without any other device handy for scanning. As such, most letters come with ordinary hyperlinks instead. Nevertheless, the attackers increasingly turn to QR codes delivered through email.
Unlike phishing links that are easy to check and block, QR code is a headache for security solutions. It takes costly and resource-heavy computer vision technology to analyze QR codes and find out what information they contain. Worse yet, while a regular link can be sorted out just by looking at it, with QR you cannot tell where it is going to take you until you scan it.
What is a QR code?
A QR code, or Quick Response code, is a 2D matrix bar code consisting of several squares and multiple dots (modules) arranged in a square pattern on a white background. QR codes can be scanned using an image processing device. It will first identify the code’s location by the squares and then read the information encoded in the dots. In addition to the actual code, the square field can accommodate decorative elements, such as a company logo.
QR codes allow to encode more data than 1D bar codes. They are often used to encode hyperlinks to various resources, such as a store catalog, a checkout page, or a building info page.
Malevolent uses of QR codes in email
Fraudsters use QR codes to encode links to phishing and scam pages. We registered the first attempts to use the trick for rogue email campaigns at the end of 2021. Those were scam messages imitating emails from delivery services, such as FedEx and DHL. The victims would be tricked into paying custom duties by scanning a QR code. The encoded link was redirecting to a fake bank card data entry page. The campaign was not very large scale and dwindled by around mid-2022. We observed new email campaigns featuring QR codes in the spring of 2023. Unlike the first one, these were after the logins and passwords of corporate users of Microsoft products.
The attackers were distributing messages advising their victims that their corporate email account passwords would soon expire. To preserve access to their accounts, the users were to scan a QR code. Some emails would come from free mail addresses, others, from domains registered recently. In some messages, the scammers added the Microsoft Security logo to the QR code to improve credibility.
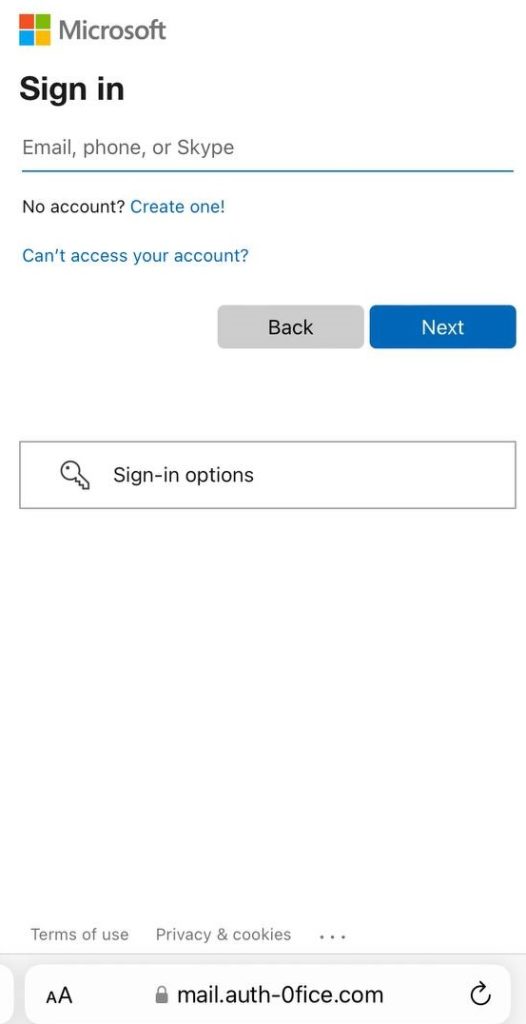
After receiving a phishing letter and scanning the code, the user would be redirected to a fake login page styled as a Microsoft sign-in page. As soon as the login and password were typed in, the attackers would gain access to the account.
In addition to messages urging users to change their password or update their personal data, we detected an undelivered email notification activity that also employed QR codes redirecting to a fake Microsoft account sign-in page.
The letter shown in the screenshot below has no QR code logo but features a “This email is from a trusted source” line to put users off their guard.
Some pages you get to see on scanning a QR code reside on IPFS resources. We explained previously how and why scammers use this distributed file system.
Statistics
From June through August 2023, we detected 8,878 phishing emails containing QR codes. The malevolent activities peaked in June with 5,063 letters, reduced to 762 letters by August.
Trends in number of phishing emails with QR codes in June-August 2023 (download)
Takeaways
Scammers benefit from using QR codes in a number of ways. First, the codes allow them to avoid detection and blocking of their emails. It is not that easy to check a QR code content, and there are no phishing links in the message. Moreover, a letter cannot be blocked for merely having a QR code inside: even though not a popular email element, a QR code can be used in legitimate correspondence as well, for example, in the sender’s automatic signature. Secondly, since the messages contain no links, there is no need to register additional accounts or domains to redirect users and thus conceal phishing. Finally, most users scan QR codes using their smartphone cameras and prefer to have the problem sorted as quickly as possible. As a result, they may overlook the address line of the page they are being redirected to, as it is not very conspicuous in a mobile browser.
On the other hand, legitimate senders hardly ever use QR codes in their mailings, so the mere presence of a QR code in an email may trigger suspicion. Furthermore, scanning a QR code requires another device, and the user may not have one readily available. Currently, we do not observe many messaging campaigns based on QR codes. We assume there aren’t many recipients who actually scan codes. Nevertheless, considering how easily the mechanism can be employed, we can also expect such attacks to increase in the near term, the campaigns themselves becoming more sophisticated and tailored to specific targets.
如有侵权请联系:admin#unsafe.sh



