Some say, CVE-2022-42889 is the new Log4Shell, for which we developed our own tool to enumerate affected hosts back in 2021. Others like Rapid7 argue that it may not be as easy to exploit like Log4Shell. Regardless of the severity and exploitability of this vulnerability, we quickly morphed a clone of our Log4Shell plugin into an open source tool that can detect this vulnerability reasonably well.
Unlike with Log4Shell, we found no trivial way to do nesting with variable expansion, so we have no hostname or username detection this time for the first release. Although these could be added easily through code execution, this requires OS-specific payloads, which just didn’t feel like a necessity for an MVP. Pull requests are welcome, though, so if you feel like adding this, we would be happy to merge a properly written patch.
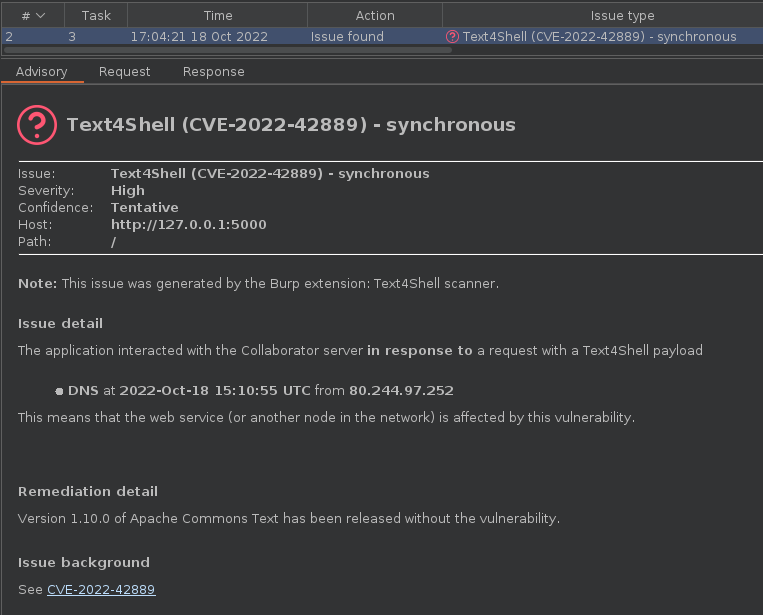
Although the PoC presented in the original GitHub advisory contained RCE in itself, we chose the “dns” method mentioned by Rapid7 in their blog post. This way, we have a simple yet reliable detection method to use with Burp Collaborator that doesn’t depend on any OS-specific behavior.
Just as with Log4Shell, we created a Burp Extender plugin that registers itself as an Active scanner check and generates payloads. Synchronous interaction is logged using built-in scanner, while a background thread polls for Collaborator interactions once per minute to test for hosts and services doing asynchronous processing.
The plugin can be downloaded from our GitHub repository under a GPLv3 license, pre-built JARs can be found on the Releases page, bug reports and pull requests are welcome.
