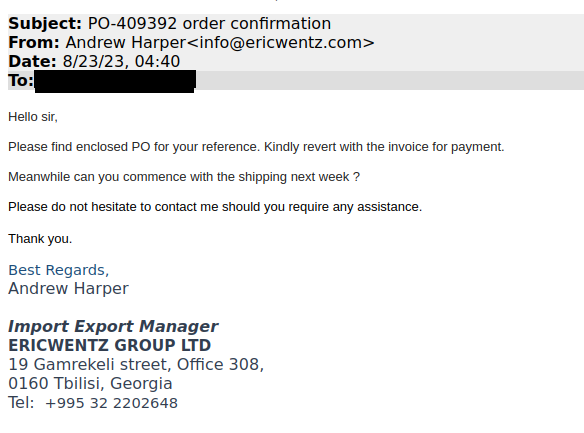
Last week I was contacted by CERT Poland. They'd observed a phishing campaign that had collected 68k credentials from unsuspecting victims and asked if HIBP may be used to help alert these individuals to their exposure. The campaign began with a typical email requesting more information:
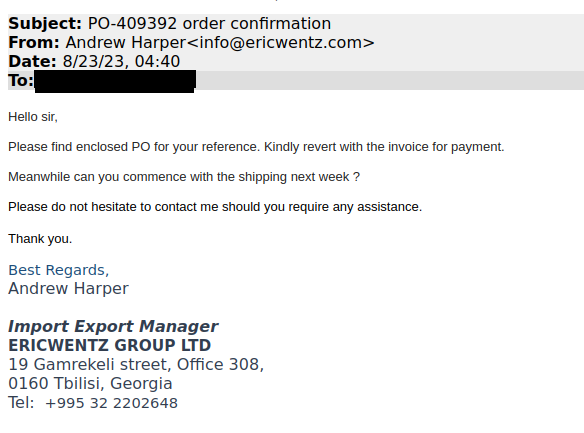
In this case, the email contained a fake purchase order attachment which requested login credentials that were then posted back to infrastructure controlled by the attacker:
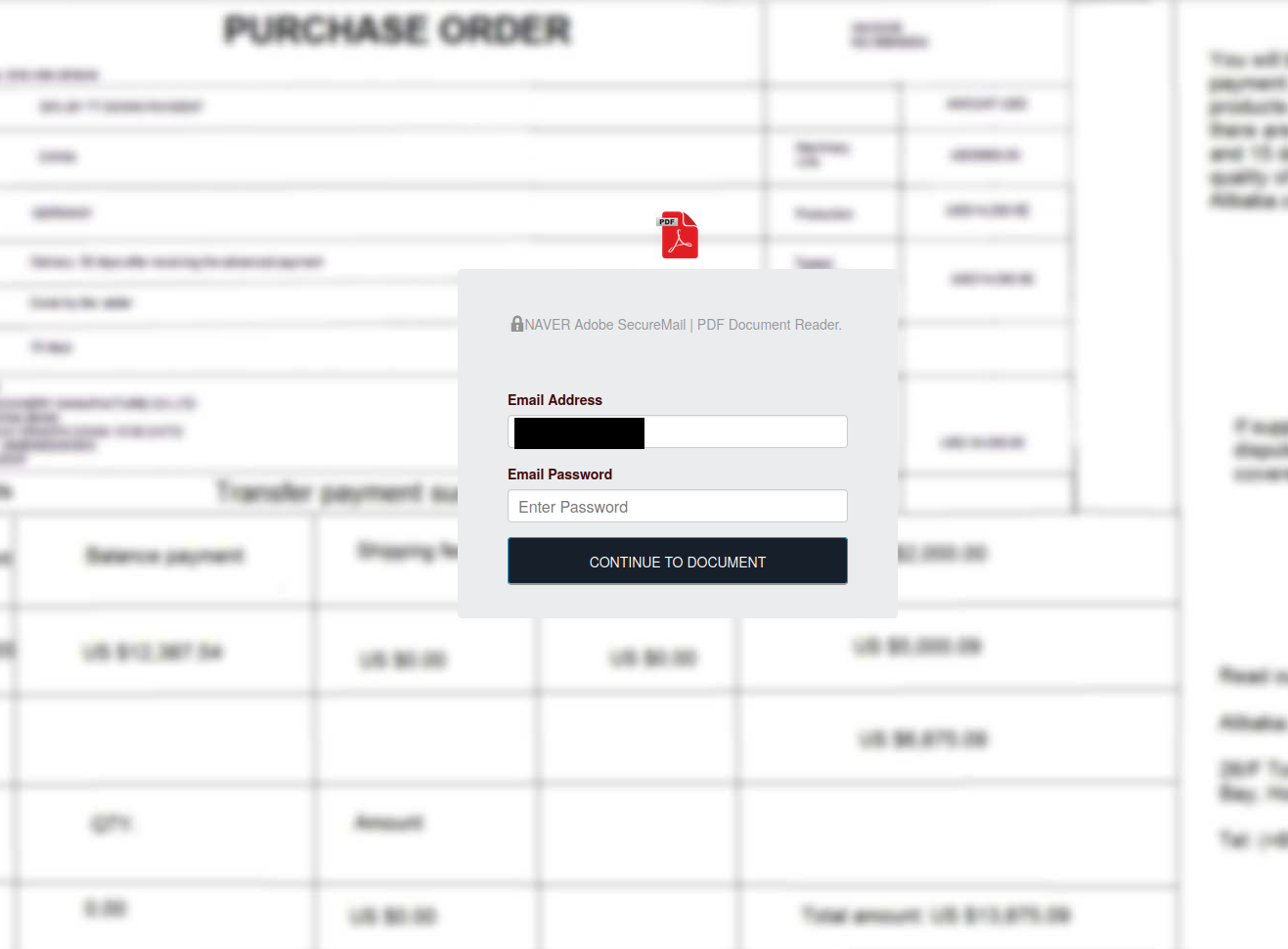
All in all, CERT Poland identified 202 other phishing campaigns using the same infrastructure which has subsequently been taken offline. Data accumulated by the malicious activity spanned from October 2022 until just last week.
The advice to impacted individuals is as follows:
- Get a digital password manager to help you make all passwords strong and unique
- If you've been reusing passwords, change them to strong and unique versions now, starting with the most important services you use
- Turn on multi-factor authentication wherever it's available, especially for important accounts such as email, social media and banking
- Never open attachments or follow links unless you're confident in the trustworthiness of their origin and if in doubt, delete the email