Yes I know the name of the post is very intriguing and you probably think I am throwing a tutorial on How to actually Rob Banks, but not really this blog comes from a story that I wanted to demonstrate with a little bit of images and demos, the Cayman Bank manifesto from Phineas Phisher [1] and some other APT examples, but also I wanted to demonstrate this in a fun scenario all in Virtual Machines and copying SOME of the techniques utilized for this Bank Hack.
This isn’t meant for one to think that they will be Elite Hackers for hacking Banks and such, it’s only a fun scenario where I challenge myself to keep learning and maintain sharp skillZ.
But let’s modify some of the things that he did of course and make it a little more Red.
When he was talking about his skills their was a mention on how he wasn’t an APT or some elite hacker where he has a team that builds custom tools, just a guy that lives off the land[2] like Phineas say’s “I’m just one guy” . Yeah, he doesn’t seem to like the cyber security community as we have fallen to protecting the greater evil that is mentioned a couple times, like Big Corps, Mans in suits, Corrupt Law Enforcement. As cool as it sounds living the dangerous life, the hacker vigilante Mr. Robot style of life, we can’t all afford that, as we got a lot to lose, but what if we didn’t??[3].
Let’s say these boundaries have seize to exist, we got nothing to worry about we don’t care anymore, we start doing things that we never even imagined doing, which in this example is to Rob a Bank. As the techniques mentioned were a little bit old, but still reliable such as using [4] PowerShell. I’ll take it up a notch since so many security protections have been deployed and with the technology BOOM from COVID we have noticed some incredible features both in Offensive and Defensive, so the security features I’ve implemented will be similar to a small bank with some security, the IT guy knows his stuff but to a level.
[1] Phineas Fisher | The Anarchist Library
[2] https://lolbas-project.github.io/#
[3] ”It’s Only After We’ve Lost Everything That We’re Free To Do Anything”
[4] https://twitter.com/424f424f/status/1383256013994749954
Infrastructure
########### Stay Safe ###########
- Use a VPN
Make it complicated to find you, do some research on your [1] VPN provider. Do they save logs?, Is there a DNS Leak somewhere, are they known for previous breaches, do they allow anonymous payments?. Anything good to stay away from bars.
- Hello Neighbor
Use someone else’s Wi-Fi, you have no idea how simple passwords are used from AT&T, Xfinity and Spectrum to mention a few, the technicians need to apply a password then and there, and sometimes for convenience the users phone number is used, a good tip on how to build a wordlist starting with the area code then work from there Wifite, Reaver, AirCrack [2].
- In the Matrix
Virtualize everything! Workstations, Linux Boxes, your Internet persona and your IRL are 2 completely different people do not mix them! Encrypt the Drives, there are multiple options [3] VeraCrypt, [4] TrueCrypt, [5] CryptSetup
[3] VeraCrypt - Free Open source disk encryption with strong security for the Paranoid
[4] https://truecrypt.sourceforge.net/
[5] cryptsetup / cryptsetup · GitLab
Recon
Now I will use some OSINT techniques to know a little bit more about my target. These techniques will all be passive to demonstrate how valuable the Internet is and if you take your time to dig a little deeper you should find at least some interesting information that will help in Initial Access.
OSINT
One of the tips given by Phineas is that plenty of information is already available for us when trying to look for anything that can get us into the internal network of the bank, sometimes just visiting the page we can see plenty of information already.
Site:
Previously mentioned, the initial access vector utilized in the manifesto was a zero-day vulnerability discovered in the SonicWall VPN. However, as we do not possess a zero-day exploit, we are resorting to the tried-and-true method of phishing. As the saying goes, there are no better words than those of the man who teaches OPSEC to those who wish to conceal as much as possible from authorities and cherish their privacy.
To continue enumerating the site, we need names, emails, phone numbers, social media. Anything that can help us in sending our payload to the users. Remember phishing comes in various forms [1], but the popular one’s are emails.
I like to run various tools that enumerate in a similar way to achieve the same goal, sometimes we miss something because other tools do the same enumeration but in a different from that they pull more or less information, in this step I’m just going to use a web crawler ZAP [2] which has been great to me in my assessments, and of course it’s open source. A second option that also is quite fast is Photon [4]
ZAP:
It’s good to look at the site manually as well, and just browse the site as a regular user, but remember you are trying to hide your tracks and you are trying to give as little as information possible about yourself. So a good thing I like to use is a User Agent Spoofer, the user agent acts like a digital footprint where it tells the site, which browser, operating system, etc. has visited the website.
You can see in my logs the User Agent is being spoofed correctly and is hiding our real OS and other little pieces of information that the User Agent is giving.
When looking for usernames/emails we have to be thorough, gather as much information as possible.
Since we are targeting (Spear Phishing) we want to be as detailed as possible with our pretext and we don’t want to be another spammer, we want to be careful with our email servers as well it’s important to test[3] and send slow and clean emails, depending on the format utilized by the corporation we are targeting a good tip is to send emails to recruiters, public figures of the sort and maybe HR when looking for a job, sales and marketing are a great option and you can see the email format being utilized.
You can see in the example below the template used for an email format:
(I’m hiding it, because you know)
A nice trick for finding emails is to visit the Contact Page some websites contain a support page or a form where we can reach out to the company and the email is publicly available.
The email domain used for the company is shown when we utilize the contact form, checking the About Us sometimes gives out information about the “TEAM”, people that currently work at the location just to make them look a little more friendly and approachable, they give out info such as favorite places to eat, dogs name, hobbies and such, usually this is good info for building passwords.
We found some probable users here, it’s a small list but perfect for personalizing our pretext on each user. But we need to find the email format on how the emails are built, these usually come in ways like:

These are some of the email format examples in which we can locate valid emails, once we find the formatting, we can locate other users as well. I’ll build an email list using this with the current users found on the About Us page.
Will continue with sending emails now to our target but we will require a little more information tobuild viable pretext for our phishing.
[1] Common Phishing Techniques
[2] GitHub - zaproxy/zaproxy: The ZAP core project
[3] https://www.mail-tester.com/
[4] GitHub - s0md3v/Photon: Incredibly fast crawler designed for OSINT.
Initial Access
As mentioned previously there was a Sonic Wall Exploit that was utilized to gain Initial Access[1] but since that’s out of the question will use spear phishing attachemnts a Sub-Technique from Phishing some attachment examples can be Word, Excel, PowerPoint, HTA, VBS and many other file types to send and get execution.
A way to choose your initial payload is looking at job postings for the place you are targeting you can sometimes see what they require and the technologies they are working with:
This info gives out potential information on how to approach our attachments, is it a Windows or Mac environment are they utilizing Office? LibreOffice? but for now we can use attachments such as Office documents.
Building our payload[2] can be a tedious task since we have to consider EDR, AV and other security products that are on site, but since this is just a playground we know that we can work with office documents with macros enabled, some security features but not as complicated as Phineas called for since it was a small bank in the real scenario that meterpreter payloads can do the job, no shame with that since this can be customized and worked on but just for reference on what I’m talking about.
As my next choice I have to work with a C2 that will get all my agents called back my choice here is Havoc C2 a great tool developed using Go, C and ASM. I’ve been working pretty much with it lately and have been loving it. You are open to choose any other C2 I won’t be explaining Havoc here since I’ve done it already in the past [3]. I added some OPSEC considerations and evasions already built within Havoc and edited the profiles so it looks like regular HTTP/HTTPS traffic.
Now to build the payload I’ll use a private framework I’ve been working on for Initial Access.

The framework builds an obfuscated/encrypted macro-enabled word document. The tool uses multiple options I researched on for Win32 API and some evasion techniques for the word document, just like on the manifesto.
” I am not an APT with a team of coders who can make me customized tools. I am a simple person who subsists on what the terminal gives “.
And of course, I just use what my skills allow me and the great open-source research available to customize or build other techniques from them.
Now our pretext is needed to get the user we are targeting to download and run our word document, for this we don’t need to be that imaginative anymore as Ai [3] can be a powerful but scary thing.
We can work with this and customize some instructions to get the user to enable or disable some necessary security implementations so our macro enabled document can run with no problems. Which you can see it’s something shown when MOTW is bypassed if not a different warning would appear not allowing the user to enable the macros but this tells the user that macros are in the word document.
As you can imagine phishing is a great initial access vector but can be troublesome and get complicated as so much security is applied to protect the company but so much security and restrictions tend to break things. So, companies here and there tend to disable them so the workflow can be less complicated.
We sacrifice security for commodity
When our infrastructure, the quality of payloads and our evasion has been valuated. Our chances of success are quite high, spear phishing has greater of a chance for success. Remember we want to play it nicely and slowly, OPSEC is important, we don’t want to lose our access, remember were trying to access a Bank, which is no joke as small as it may be the connections for investigations are similar to bigger banks, that’s why you have to consider that as small as the place can be it still has some security implementations, and our area of discovery can get smaller.
Now let’s get our hands dirty.
[1] Hardware Hacking Workshop Online | Registration
[2] Weaponization - Red Team Notes 2.0 (Shame on me)
Recon & Persistence
We need to start gathering information on the machine and the user we are currently working with some questions to ask are who are we, where are we and what permissions do we have on the user or host, these steps are usually a factor for us to decide on what to do next, will currently focus on Host Enumeration as there is much info that we can retrieve from the workstation itself and that way we may avoid for the time being creating malicious traffic to other workstation an example being the Domain Controller (DC) since when we approach the Active Directory (AD) Enumeration will be talking abouthis one a lot.
Now let’s check our permissions and who are we?
A warning on our persistence:
We must be careful as in real life we don't want to make very unforgivable mistakes [1], as this would give us time behind bars, let's get an idea on our persistence we can add some little bit of sazz onto the technique [2] or probably do some research and find a new method.
In our enumeration we need to take in consideration when using C# and custom tools when running these custom tools built in C# we want to move onto another process, sometimes our current process doesn’t hold the capacity to execute correctly or even returns us output from our tool. We must move by injecting:
Now let’s test the custom tool.
Now that we’ve located the startup folder, we can place a binary here or script and it will run with no issues. This example searches for the StartUp folder location for persistence.
But now we need to look for stuff, what’s on the host? Are we admins, where are we? Who are we? Permissions? Domain Admin?!! Sometimes this information doesn’t come easy, but sometimes it is [3][4]. Automation is key here, but we do want to consider that our behavior is also being monitored by security products looking for malicious or strange actions not usually done on a regular work day.
Some tools for searching interesting files on a host are SaruonEye[]5 and Snaffler[6].
When using SauronEye I recommend avoiding the “–contents” flag it will take a lot for the output to even show on the C2 and some don’t even have enough for all that info.
Since it’s a TXT it’s easy to just read it from the terminal
Good found some nice CC info but this won’t do the bank holds more info than just that! We need to keep looking but according to SauronEye and Snaffler that’s it .
I guess now is a good time to escalate our privileges, our current user can’t do much and only has access to its current machine but maybe another one can help us move to other places.
For lateral movement I recommend making the recon for this part as targeted as possible. We don’t want queries as this will most likely send an alert.[5] Let’s make sure we only target our current user, should be important to know as much of who we are [6]. Remember PowerShell and C# are going to be your best friends here. Integrated with Windows, native no dependencies, what more can we ask. Also since AD is a pretty big topic it’s good to be prepared [7][8][9][10][11][12][13].
Before going on enumerating the entire domain let’s take a look at where we currently at our current host, great tools for local enumeration and other types have been compiled in the SharpCollection[14] github repo these are C# binaries that are meant to be run as standalone or in-memory (convenient) using a C2 Framework (Cobalt Strike, Covenant, Empire, Havoc). One of the tools of interest from experience is Seatbelt [15] which has been incredibly helpful in my engagements and has automated enumeration for User and Host information.
If I were to get lucky, I do like to check some common things that give me a ton of information for my next steps a quick check is the OS Info:

What security am I going up against depending on my usage PowerShell or C#:

And Hotfixes look for some quick wins and probably can escalate my privileges using an exploit instead of relying on finding credentials, which is still not bad and need.
This does not mean to not look at everything the tool gives you, it’s just some quick looks so take your time and check it out. Since we aren’t admins, we can’t see that much on the Host so seatbelt has flags that we can utilize to categorize the type of enumeration we are looking for on the host or on the user, this next flags show interesting files that were last worked on:
Some interesting info is to see what the user has accessed recently, maybe some interesting websites were visited where the user is asked for credentials, interesting files where user information is worked upon. It can be quite interesting the files that were recently accessed
We can also have a look at using our Custom Tool, I’ve built a small POC using C# that does quite similar searches like Seatbelt but I added some little other things such as finding some privesc opportunities.
From the enumeration we can notice that the user visits certain sites frequently during work hours it can be quite interesting some of the finds.

Might be able to find credentials, let’s take a look.
Nice, some credentials and it seems to be for the Local HelpDesk account info that was shown when I used my POC, I could’ve simply used simple CMD commands, but we have no clue if the Command Line is being logged so it’s best to use some custom tools that use API to call for information here I called to check which users are in the local Administrator group.

Since we found some Local Administrator credentials we can move on our persistence, we got some great information.
One easy place to leave persistence is in the Startup Folder as previously mentioned but it’s not the most OPSEC considered method but a very simple one. The file left behind will execute every time the user logs back onto its session it’s nice to verify who we are.
But we are going to take a different approach and will use a stealthier approach as we have Administrator Privileges, we can intercept execution on a DLL of our choice without affecting the original process.
In this example the user works with Microsoft Edge in the work environment, the technique will be implementing is Koppeling [16] the techniques allows you to prepare any arbitrary DLL for hijacking as long as we provided the final path of the reference DLL, which in our case its a DLL loaded by Edge named dbghelp.dll we can see this DLL is being loaded in an Edge path Location by using Procmon and applying the “NAME NOT FOUND” and CreateFile Filters for the tool.
For building the exports and proper payload we need to give it the target payload and the referenced payload (which is the one we want to copy its exports from). I used the C# binary for this.
Placing the DLL into the proper location when loading edge will not break its functionality and crash the binary where there might be some sort of investigation. Make sure to use quotes if the path contains a blank space in a folder name such as “Program Files.”
We can verify our call back to our C2.
With this method of persistence, we are confident that it will not crash the process and actually run under the radar when executing this happens because AV/EDR take in consideration that a legitimate process is being executed so this way we are also aware on when the user is active, since we won’t get a call back unless the user executes Edge.
This does come with some things to consider, that we need to move fast onto another process as we did previously when we injected to get our tools working, we need to be careful as if the user closes Edge our connection will die as well and of course will just have to wait until the next execution for that, but we got stuff to do!!
[1] Patchwork APT caught in its own web
[2] https://persistence-info.github.io/
[3] Qbot and Zerologon Lead to Full Domain Compromise
[5] Kerberoast with OpSec | Microsoft 365 Security
[6] https://www.setquotes.com/give-me-six-hours-to-chop-down-a-tree/
[8] Active Directory Pentesting Notes
[9] Active Directory Methodology - HackTricks
[11] Recon - Initial Access - Pentesting & Red Teaming Notes
[13] https://ppn.snovvcrash.rocks/
[16] GitHub - monoxgas/Koppeling: Adaptive DLL hijacking / dynamic export forwarding
Lateral Movement, Active Directory, Kerberoasting and SQL Servers
As we keep enumerating the Host Machine we notice we are at a dead end there is a whole network of workstations and we need to keep moving to look for more interesting data at the bank, we need to reach domain admin to at least say we PWNED the bank we need to focus a little longer on the Active Directory this time, will move onto using the SharpView tool this will allow us to stay in memory using the C2 Framework, unfortunately persistent PowerShell scripts are still not available at this time this way we could have utilized PowerView for Havoc but you can still utilize the popular scripts available for Domain Enumeration as well.
Finding AD information is quite important now that we need to get around the network, we need Computer Names, User Names, Permissions, Access anything that we can use as a means to know where to move next or if we have permissions to move around [1].
For this we need to know first where we are again now but in the Active Directory, we know the host and user we are currently working with but what is the Domains name? Are there more Computers connected? Devices? Users? Let’s look at the Domain.
Ok now we are familiar with the Domain name of the Active Directory and there seems to be no other child domains that we might need to pivot to let’s look now at the users maybe there is info on them that we can rely on to move laterally.
We have a quick list on users that are available in the Domain this enumeration I just asked for the names of the users, but I can request the full information on each user individually if I see someone interesting for this I would need to request the samaccountname property so I can use the “-Identity” parameter on SharpView and properly request all the info for that user.
Now let’s just grab the identity of 1 user considering we don’t want to send a bunch of queries to the DC in a short amount of time as this will get us flagged, one of the good things about SharpView is that it’s using legitimate LDAP traffic.
We see above that Adrian is a Domain Admin[2][3] but we can’t move here yet, we got no info on the user besides he’s a Domain Admin and no permissions really stand out we also need to find a way to reach him, now we do have a bunch of active directory techniques that we can work on[4] but instead of guessing we can actually get a path on us for where to go next, here comes bloodhound[5] with this
Attackers can use BloodHound to easily identify highly complex attack paths that would otherwise be impossible to quickly identify. And true to that since it would take us some time to recognize the patterns and paths for us to move on the network so we can automate and find this using BloodHound with the easy .NET Binary we can run this all in-memory as well so no worries on leaving artifacts on the host, let’s run this.
Beautiful lets see what happened here, I added some extra parameters because we want to be stealthy right?
I change the default values of some actions such as throttle, jitter and threads, because we aren’t in a hurry, one of my favorite things about this is that it now tells you which version of BH is it compatible to, so no more guessing on the version, the status interval was unnecessary but I wanted to show the progress of the tool so I just upped it up a notch so that we receive the output a little more slower, I avoided the cache to be written to disk and kept solely in memory, as well as encrypted the Zip File so AV/EDR doesn’t have access to our graph and renamed the ZIP File so it doesn’t look like a standard bloodhound created zip file, now let’s setup BloodHound and import the Graph.
Setting up bloodhound shouldn’t be complicated install Neo4J, build an empty DB and start bloodhound after neo4j then importing the zip file should be easy.
Now I have to take a look at the Computers in the Domain since we are trying to move onto another host or if possible, impersonate another user while searching we find an interesting one a SQL Workstation, let’s take a more detailed look at this Node.
Seems that we do have some paths to reach this Workstation, but the problem is that:
- We need a Domain Admin
- We need to reach DC.
Let’s check if any user has a way to reach out to this workstation, which we see that one of the users does have a SPN tied to them and it links back to the DBSQL workstation this doesn’t guarantee that the user has a way to access the workstation but only the SQL Instance, but taking in consideration that SQL is also a treasure trove of opportunities let’s work with it.
Now we could have checked this as well utilizing SharpView and the SPN parameter that will look for users that have a Service Principal Name attached to them which this means that users are Kerberoastable[6][7] in this case we can request a ticket and crack it offline, this works because, ANY user is allowed to request a ticket-granting service (TGS) ticket for any SPN, and parts of the TGS may be encrypted with the RC4 using the password hash of the service account assigned the requested SPN as the key.
A good OPSEC method is to use “Rubeus kerberoast /stats” this won’t query the user’s and will look for only SPN tied to an account using LDAP.
Let’s request a ticket for the user utilizing Rubeus and crack the hash offline. Something I do want you to consider is Do not request tickets for the ENTIRE Domain, research your targets, it’s super important to hide in the logs if we aren’t disabling these or tampering with, I will show below a single Kerberoast Request on a Sea of Logs which can be taken as a benign action.
But we can also use our C2s built-in get-spns which does not leave a log 4769 log:
Havoc:
Havoc Logs:
Rubeus Logs:
We notice that Madison requested a ticket for Joselin, but this is a simple, single request that has the potential to hide in the logs or can be the only hint left behind that the network was even compromised while Havoc does a better job in hiding as we just see Logon status which can blend with the rest of the logs. Let’s move on to Cracking this hash will use hashcat [9] for that.
hashcat.exe -m 13100 -a 0 hashes wordlist
- Type of hash
- Attack method
- Hash file
- Wordlist to utilize.
- Extra: Use rules to mutate words (password, p4$$w0rd)
Fantastic we cracked the ticket for jnovoa and grab the cleartext credentials for the user, this will help us to move onto a new workstation and get more info on the new location, now since we know that this is a SQL Instance maybe let’s give it some SQLRecon work onto it now that we have credentials, for this will use the SQLRecon [8] Tool.
SQLRecon has some great options to look for SPNs related to SQL Services as well but we can avoid that since we have already located what we needed, will use some of the enumeration modules to check out the instances available in the Domain:
With this information now we can connect and enumerate the workstation to see what our current user can access, potentially finding some type of path that will allow us to jump onto the workstation or maybe just simply find some loot.
Now we can gather more information after that successful query on the workstation this time let’s look at what permissions the user has on the SQL Instance:
We can look at the users available in the Instance as well:
Move on with some good stuff let’s look at the Databases available and if we have access to some interesting ones:
We see some standard ones, let’s look at the master one this usually is the default one to start working on let’s take a look at the Tables available for that one:
Nice now let’s look at the columns for that table:
This looks like has some potential for us to grab, this time let’s send an SQL Query and grab all the info available in these Columns:
Thank you Havoc group for helping me figure out I need to escape the Double Quotes (“)
Jackpot! Got the banks Full DB Dump we now grab this juicy loot and now try to hop onto this workstation since we read all the data, but we now need to get some command execution access the workstation now, maybe we can keep moving or find more interesting files that would help our progress to move forward I think Domain Admin is close!
Now SQL allows command execution with the right permissions, maybe we can enumerate and find out if the feature XP_CMDSHELL [10] is enabled if it is we can immediately execute code, but if it isn’t then we might need the correct permissions to enable this feature, now the SQL Query to verify this goes as follows.
We see in the 3rd column that the config value is set to 0, but we need this set to 1, according to our previous enumeration the user seems to be an admin on the master DB and with this we can change the configuration, with SQLRecon we can achieve this with the EnableXP Module:
Nice we verify those 0’s turned into 1’s:

Executing commands now should be easy utilizing SQLRecon we utilize the XPCmd Module now:
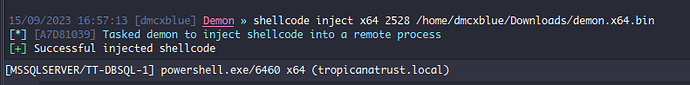
Looks like we are running as the service account on the TT-DBSQL-1 Workstation with command execution we can now enumerate and gain more lay of the land on this new host but instead of running the command every single time we must work onto getting a stable Demon for our C2.
Now there are some really good options on how to move next leave a DLL for another Hijack, maybe copy a binary and replace a legitimate one, a bunch of idea’s but for this I want to use PowerShell, since we can run powershell in the command utilized in XP_CMDSHELL we can actually get a demon to connect back, but unfortunately Havoc doesn’t have native powershell code to execute, but that won’t stop us, we want this money!! So will grab Havoc shellcode and convert it properly to be used on a Shellcode Loader built in PowerShell.
Now with the framework I built this can be automated, the science behind it isn’t really complicated.
But let’s break it down, the tool will use a template for a simple CreateThread PowerShell Loader and place the shellcode on the script. Not much to it but of course we still have to add some methods of obfuscation or encryption to get past AV/EDR
A simple launcher and our tools indicate that Defender does not detect this script, but let’s test that out.
Will host our payload on our attacking machine and the call it from the SQL Instance executes utilizing the OLE Module since we utilize hyphens for PowerShell and we can’t escape it properly with SQLRecon so moving onto using OLE is a better alternative as we are not utilizing SQL Queries to execute commands.
When executing we see that we got no connection
Now let’s verify why is that.
Well of course it is getting detected, my thought process here is to try some encryption first them move onto obfuscating and finally encoding we might not need to apply so many layers of obscurity if simply one can get us through in this example, I’ll start with AES encryption.
Now after having some issues, it seems that I could not get past the SQLRecon Queries and methods to execute code, so I moved to another option since I have jnovoa’s Password I can make a token and impersonate that token for later use with SharpSQL with this I was able to continue and execute commands.

And SharpSQLPwn, due to unfortunate issues this needed to be done on the workstation leaving an artifact on disk but this would still be ok to work on with a C2, currently cannot get it to work.
SharpSQLPwn will authenticate and run the command.
We see on our http server that it has pulled the PowerShell script.
Since this was an SMB Shellcode technique, we need to use the pivot commands from Havoc to connect to the named pipe that was created.
We are running as the Service Account on the new host we can verify with the whoami built in command from Havoc.
I don’t understand why it says unresponsive and the call back time is longer than 2 sec (around 5-10 sec) but it works decided to move our session onto a more stable process by injection
Fantastic we moved onto the new host we have a demon calling back to our C2 we managed to bypass AV and currently on this workstation, let’s start exploring. Now service accounts are meant to be there for being a separate account that is only intended for the access of a resource, so we need to move onto another user to leave our persistence on this workstation.
One thing that service accounts are vulnerable to is the Potato [11] attack, if an account contains the SeImpersonatePrivilege this allows the account to impersonate any local accounts which here will target the SYSTEM account.
For this example will use GodPotato[12] as it’s been tested and worked on to be functional on Windows 10 & 11. It is also built in C# so we can execute this in memory. GodPotato is simple to utilize, and we can give it a simple command to run while it does the rest for us:
Perfect we have elevated our privileges and managed to get SYSTEM commands, let’s upgrade to a C2 Demon connection now using the same PowerShell script as before while using the GodPotato method.
We had to place the binary on the host as I was receiving errors using .NET in-memory by placing the binary on host and using the current user for executing on a location everyone has access to write on (Public Folder) we can get good results for executing some binaries, this is NOT a recommendation as we are leaving an artifact behind, but it is still a way to execute an achieve a goal, work with what you’ve got.
Since we are currently running as SYSTEM why not look at what the SAM Dump has to offer us, the C2 has a great built-in function for this and can help us achieve this.
Now I’ll just use PowerShell to compress these files into one nice ZIP file.
We download next for this.

And we can check our loot that this has been downloaded successfully.
Will unzip this file on our attacking machine and grab the hashes offline, with this we don’t need to run any more tools on the workstation and worry about detection, we can actually do this in the safety of our attacking host now and get some more valuable info, even if we don’t get cleartext credentials, hashes are still viable since there are techniques such as Pass the Hash (PTH).
Will utilize the pypykatz[13] python tool a great alternative if you love running just on Linux
[1] https://www.exploit-db.com/docs/english/46990-active-directory-enumeration-with-powershell.pdf
[2] Journey to Domain Admin and Enterprise Admin: A Practical Internal Red Team Scenario
[3] Active Directory security groups | Microsoft Learn
[5] GitHub - SpecterOps/BloodHound: Six Degrees of Domain Admin
[6] Kerberoasting - Red Team Notes
[7] https://www.sentinelone.com/cybersecurity-101/what-is-kerberoasting-attack/
[9] GitHub - hashcat/hashcat: World's fastest and most advanced password recovery utility
[10] xp_cmdshell (Transact-SQL) - SQL Server | Microsoft Learn
[11] Potatoes - Windows Privilege Escalation · Jorge Lajara Website
[12] GitHub - BeichenDream/GodPotato
[13] Dumping credentials (offline) :: Kaluche — Windows - RedTeam / Pentest - Infosec
Constrained Delegation & Domain Admin
With our previous hashes we noticed that we got almost nothing related to AD, no other domain user or object that we can work with but that is nothing to worry about as sometimes there are stuff that can usually fly unexpected under our recon, we did find great information on the Domain and some possible techniques that we can utilize for lateral movement let’s just give a quick glance at our enumeration.
The workstation we currently are working with has Delegate permissions to another workstation, so now we have a path and where to move on next.
Constrained Delegation [1] is a way to limit exactly what services a particular machine/account can access while impersonating other users. The “service” specified is a service principal name that the account is allowed to access while impersonating other users. In this case we have a Constrained one because a specific resource was tied to this delegation, and we can only access that specified resource, or can we? Now Rubeus takes advantage of (Alberto Solino’s) [2] great discovery about how the service name (sname) is not protected in the KRB-CRED file [3], only the server’s name is.
Since we got SYSTEM or the Machine Account, we can utilize this account to request a ticket to impersonate a user that has access onto the workstation it we can utilize different methods to grab the ticket with the tgtdeleg technique or since we have the hash for the machine account we can use the rc4 flag we can change the service into an alternative one that we can utilize to move onto the host. We can target some of the services depending on what we are looking for in Lateral Movement [4]
Will test our ticket and we noticed that now we have READ access onto the remote host, but our interest is to move onto the host, gaining a Demon, since there were a few users on the Domain, we’ve been testing with the users we haven’t had access to which in this case was agarcia
With this potential lateral movement, we can look at the options we have. We can change the altservice to HTTP or HOST, these will allow us to use WinRM, WMI, PowerShell Remoting or PSEXEC to move onto the network. Giving our session the HOST and HTTP allows use to use WinRM, WMI one of the ways to test WMI is simple executing commands and expect a Code: 0 which means it completed with no issues, but WinRM has a Test-WSMan PowerShell Command which we can verify what computers in the domain has this enabled. We can verify this way.
The output confirms that the feature is enabled, we can move forward and execute commands.

Nice now onto a new workstation will keep utilizing our built PowerShell script to gain access onto this workstation and get a new Demon to work with.
Nice we are running with the highest privileges on the new workstation, the path to DA is getting closer the more we move around, and just like before will start enumerating in on the New host again, rinse and repeat people this way we won’t miss anything and make sure we are checking all our boxes, enumeration mostly comes from experience for what to look keep practicing, read reports to get an idea on what’s been searched for or what is common to find.

As you see here an interesting file type I like to search for are KeePass files, let’s download this file and look at any credentials available. Usually, the files by setup will contain a password so cracking this is another step of the way will utilized hashcat again.
Looks like the password here is what is considered a keywalk [5] a combination of keys that seem really complicated but with patterns it is something really easy to guess. Now that we have recovered the Database file let’s open this and see what we find.
Cleartext credentials for mgarcia user, it seems it was also being used to install applications or such and instead of asking for the password it was just saved. Now let’s go back and see what this user has access on.
Well, it seems that this user has DCSync privileges. This means we can simulate to be a DC and request the hashes of ALL the users in the Domain, and remember our goal, was to reach Domain Admin.
Well this simplifies this, there’s multiple tools that can help us achieve DCSync so let’s get to it.
Will impersonate the user by creating a token using Havoc built-in feature token [6]
We can now DCSync in the context of mgarcia now, I’ve utilized SharpKatz to consist with the in-memory, but it seems that SharpKatz drops a txt file onto the host, an IOC left behind.
Download or read the file and take a good look at the last step, we have completely compromised the Domain found some interesting files and moved on the domain the most silent way that our skills allow, do consider that these techniques even though in-memory they still exist during execution so EDRs are still capable of finding these techniques unless we consider stack spoofing, sleep encryption and many others.
Now even though we can use the NTLM hashes to compromise the user, it’s no fun so let’s go ahead and crack it.
Nice, completed challenge, we managed to get initial access, bypass security products, done some active directory enumeration, lateral movement, SQL recon and exploitation, password cracking, in-memory execution utilized methods to get around the network find interesting files and finally take usage of a user’s permissions to obtain all the hashes in the network which helped us achieve a Domain Admins users’ credentials.
Well thanks for following me in this little Adventure for corporate hacking, Bank Fraud, and some small red team knowledge. Now go and Rob Banks!
Legally…
Memorandum: To my Family and Friends. The only people I would hack banks for.
[1] Constrained Delegation - Red Team Notes 2.0
[2] https://twitter.com/agsolino
[3] Kerberos Delegation, SPNs and More... – SecureAuth
[4] How Attackers Use Kerberos Silver Tickets to Exploit Systems – Active Directory Security
[5] Block These Top Keyboard Walk Patterns Found in Compromised Passwords- Specops Software
[6] Understanding Impersonation via Access Tokens | by goswamiijaya | SecureBit | Medium