
2023-8-8 14:46:53 Author: blog.projectdiscovery.io(查看原文) 阅读量:11 收藏
Introduction
We are excited to announce the release of Nuclei Templates v9.5.8, which brings with it a comprehensive collection of C2 server detection templates. In this blog, we will delve into the world of C2 server detection over the internet. C2 servers, also known as Command and Control servers, play a pivotal role in the command and control infrastructure utilized in cyber attacks, including botnets. Acting as a centralized communication hub, C2 servers facilitate communication between attackers and compromised devices, commonly referred to as "bots" or "zombies."
By exploring various methodologies and leveraging threat hunting techniques, we aim to provide insights into the detection of C2 servers. Our focus lies on developing Nuclei templates to enhance the threat hunting process.
Detecting C2 servers is a challenge due to the ever-evolving techniques employed by attackers. However, security professionals and researchers utilize various approaches to identify these malicious servers. Here are some common methods:
- Network Traffic Analysis: Analyzing network traffic patterns for suspicious communication and anomalies.
- Signature-based Detection: Utilizing known signatures or patterns associated with C2 activity.
- DNS Monitoring: Monitoring DNS queries and responses to identify potential C2 server connections.
- Behavioral Analysis: Examining abnormal behaviors and communication patterns to detect C2 activity.
- Malware Analysis: Analyzing malware samples to identify indicators of C2 server communication.
These are all important and valid ways of detecting C2 servers. We hope to be able to add to your security arsenal and help you explore enhancing your threat hunting process by including Nuclei templates in your workflow.
Detecting C2 Servers with Nuclei
We'll cover three ways of identifying C2 servers with Nuclei:
- Default SSL Certificates: Identifying C2 servers through default SSL certificates
- Body Hash: Calculating cryptographic hashes of response bodies to detect known C2 server signatures.
- JARM: Analyzing server fingerprints generated during the TLS handshake to uncover C2 servers.
Default SSL Certificates:
Default SSL certificates are commonly used in scenarios where devices or software need to initiate secure communication immediately without requiring users to obtain and install their own SSL certificates. These certificates are often found in various network devices such as routers, firewalls, load balancers, and web servers.
There are various methods used to identify C2 servers. They include using default SSL certificates, including self-signed certificates and SSL serial numbers.
Detecting a Cobalt Strike C2 server using a default SSL certificate:
Cobalt Strike servers come with a default certificate that displays specific values for the serial number, the issuer, the subject, and the certificate validity. We can use Nuclei templates to find these specific values. If the SSL Certificate Serial is 146473198 it is likely a Cobalt Strike Server. We can use tlsx to get the SSL serial number of a server.
Target: 110.40.184.247
-cn argument displays subject common names and -j is for json output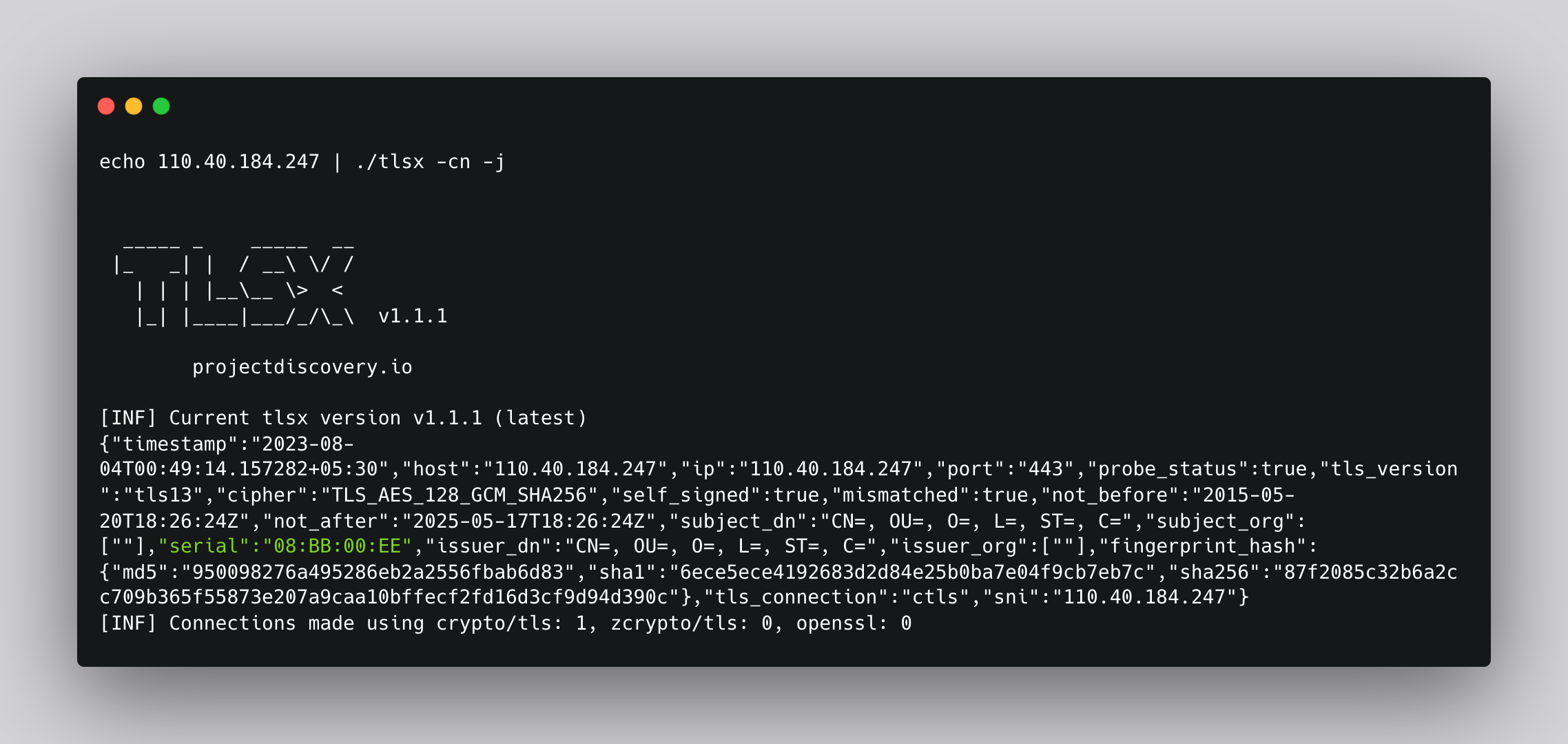
Next, the DSL helper function contains() can be used here to match serial numbers
Matcher Syntax:
matchers:
- type: dsl
dsl:
- 'contains(serial,"08:BB:00:EE")'Final Template:
id: cobalt-strike-c2
info:
name: Cobalt Strike C2 - Detect
author: pussycat0x
severity: info
description: |
Cobalt Strike gives you a post-exploitation agent and covert channels to emulate a quiet long-term embedded actor in your customer's network.
reference:
- https://blog.sekoia.io/hunting-and-detecting-cobalt-strike/
metadata:
max-request: 1
verified: "true"
shodan-query: ssl.cert.serial:146473198
tags: ssl,c2,ir,osint
ssl:
- address: "{{Host}}:{{Port}}"
matchers:
- type: dsl
dsl:
- 'contains(serial,"08:BB:00:EE")'
extractors:
- type: json
json:
- ".serial"Detecting Asyncrat C2 with CNAME
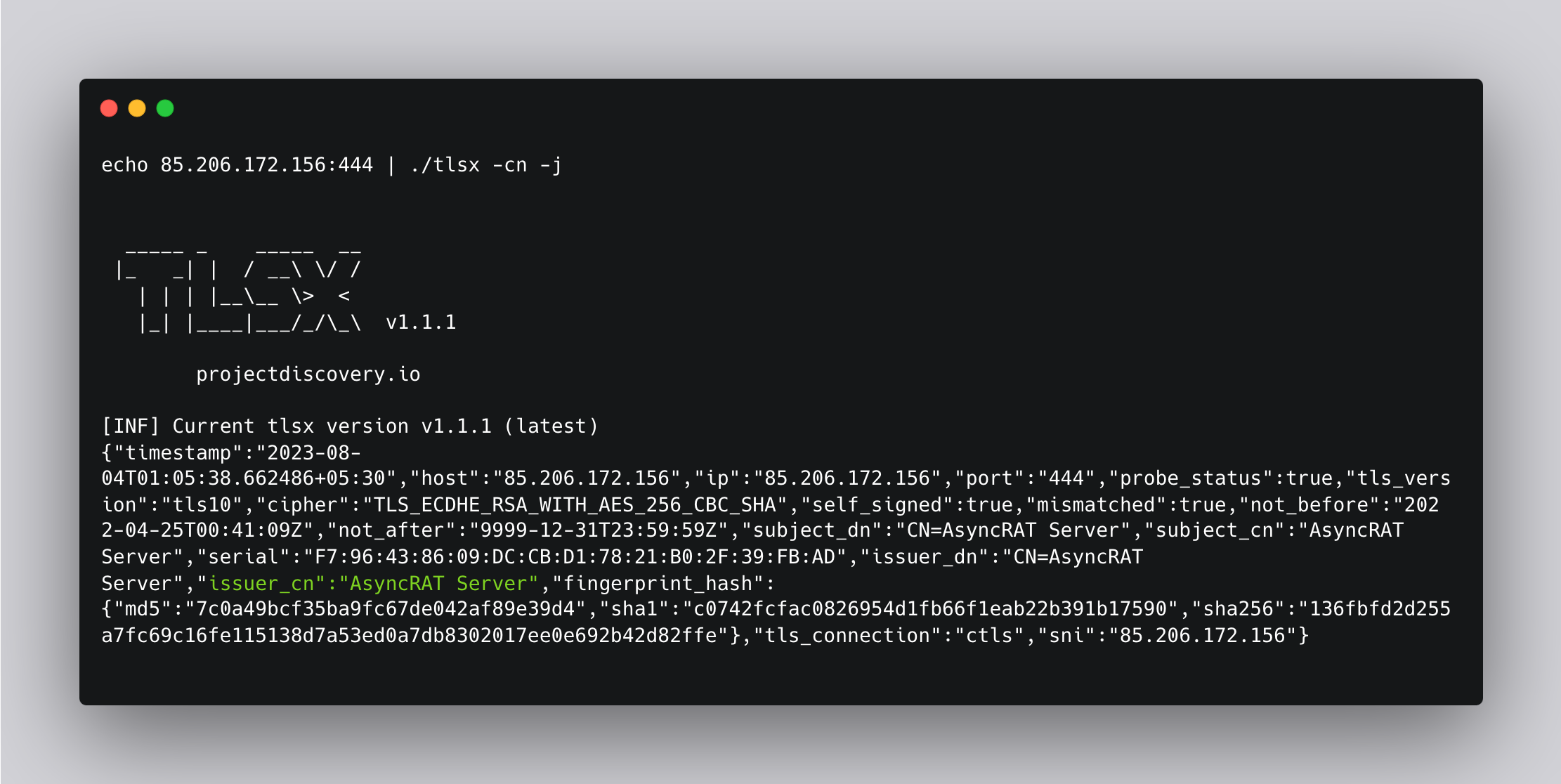
Here is another example template to Detect Asyncrat C2 using Common Name (CNAME). Asyncrat is a malware remote access tool. You can confirm a server is using Asyncrat if the SSL Certificate Issuer CN (part: issuer_cn) contains the phrase AsyncRAT Server.
Let’s use tlsx again for getting issuer_cn
Command: echo 85.206.172.156:444 | ./tlsx -cn -j
Target: 85.206.172.156:444
Matcher Syntax:
matchers:
- type: word
part: issuer_cn
words:
- "AsyncRAT Server" Final Template:
id: asyncrat-c2
info:
name: AsyncRAT C2 - Detect
author: johnk3r
severity: info
description: |
AsyncRAT is a Remote Access Tool (RAT) designed to remotely monitor and control other computers through a secure encrypted connection. It is an open source remote administration tool, however, it could also be used maliciously because it provides functionality such as keylogger, remote desktop control, and many other functions that may cause harm to the victim’s computer. In addition, AsyncRAT can be delivered via various methods such as spear-phishing, malvertising, exploit kit and other techniques.
reference: |
https://malpedia.caad.fkie.fraunhofer.de/details/win.asyncrat
metadata:
max-request: 1
verified: "true"
shodan-query: ssl:"AsyncRAT Server"
censys-query: services.tls.certificates.leaf_data.issuer.common_name:AsyncRat
tags: c2,ir,osint,malware
ssl:
- address: "{{Host}}:{{Port}}"
matchers:
- type: word
part: issuer_cn
words:
- "AsyncRAT Server"
extractors:
- type: json
json:
- " .issuer_cn"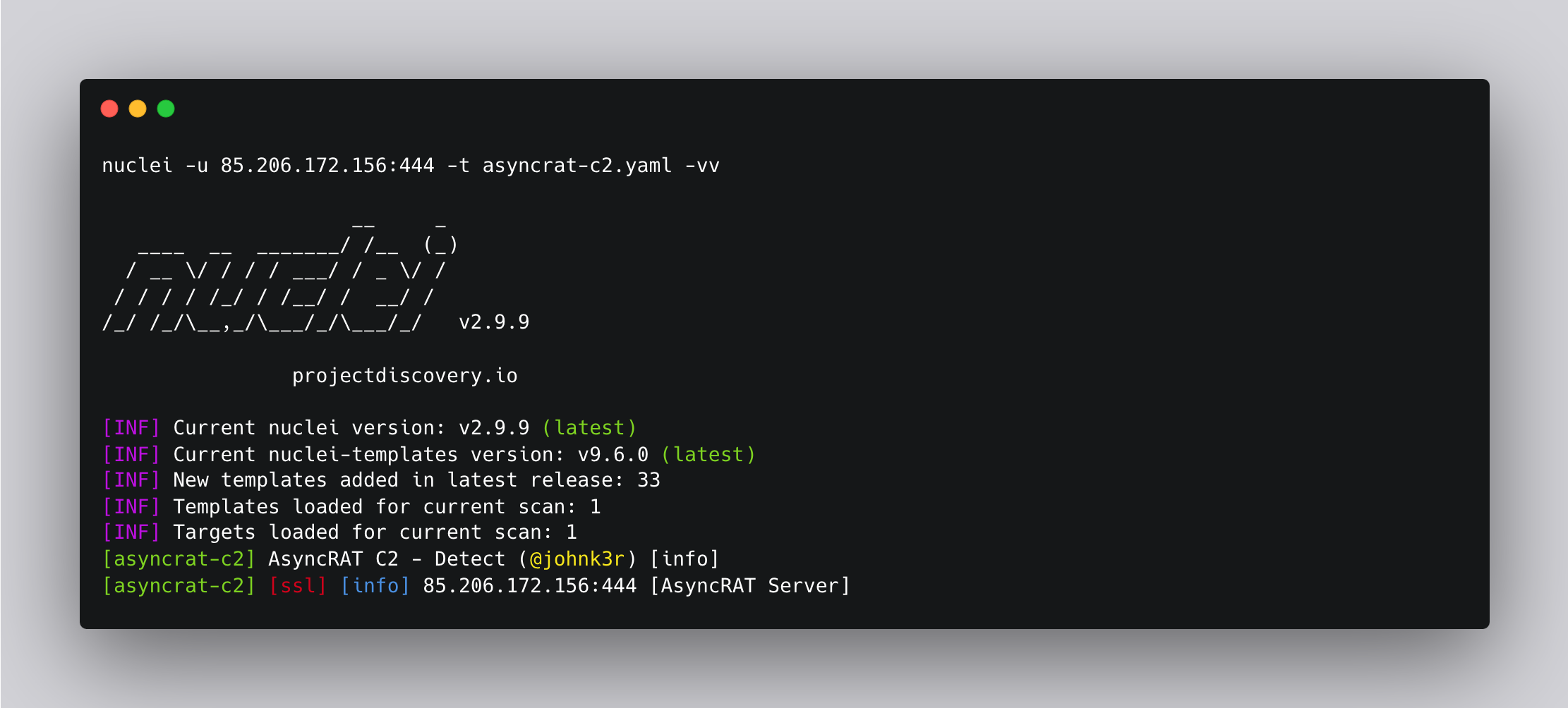
For more, click here: https://github.com/projectdiscovery/nuclei-templates/tree/main/ssl/c2
Body Hashes:
Hashing the response body involves calculating a cryptographic hash value from the content of the server's response before it is sent back to the client. By comparing these hashed response bodies, we can detect potential C2 servers. We can use httpx to generate a response body hashed with different algorithms.
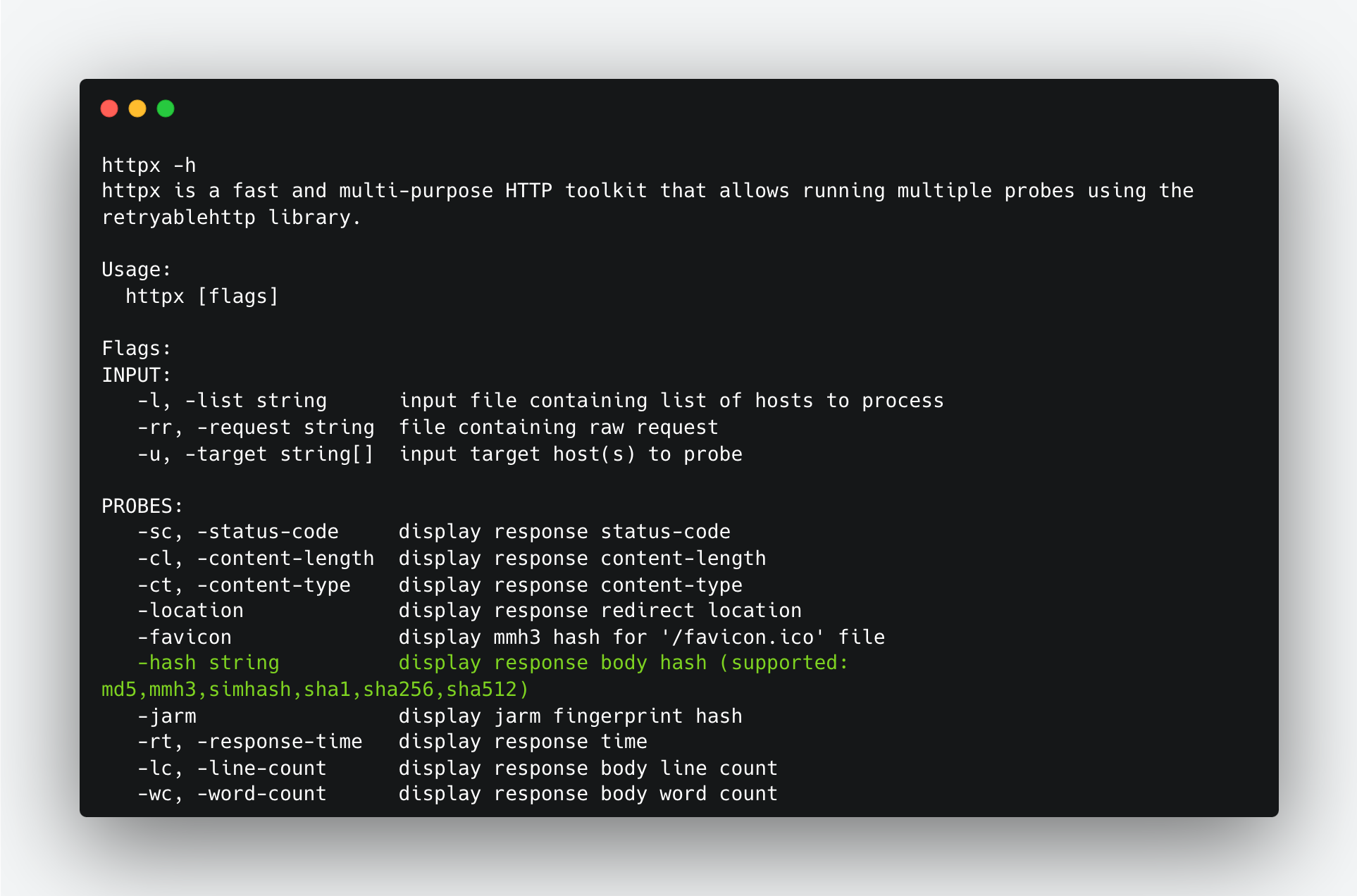
We can use -hash argument to generate a body response from host. Here we generated a sha1 body response.
Target: http://52.196.50.60/
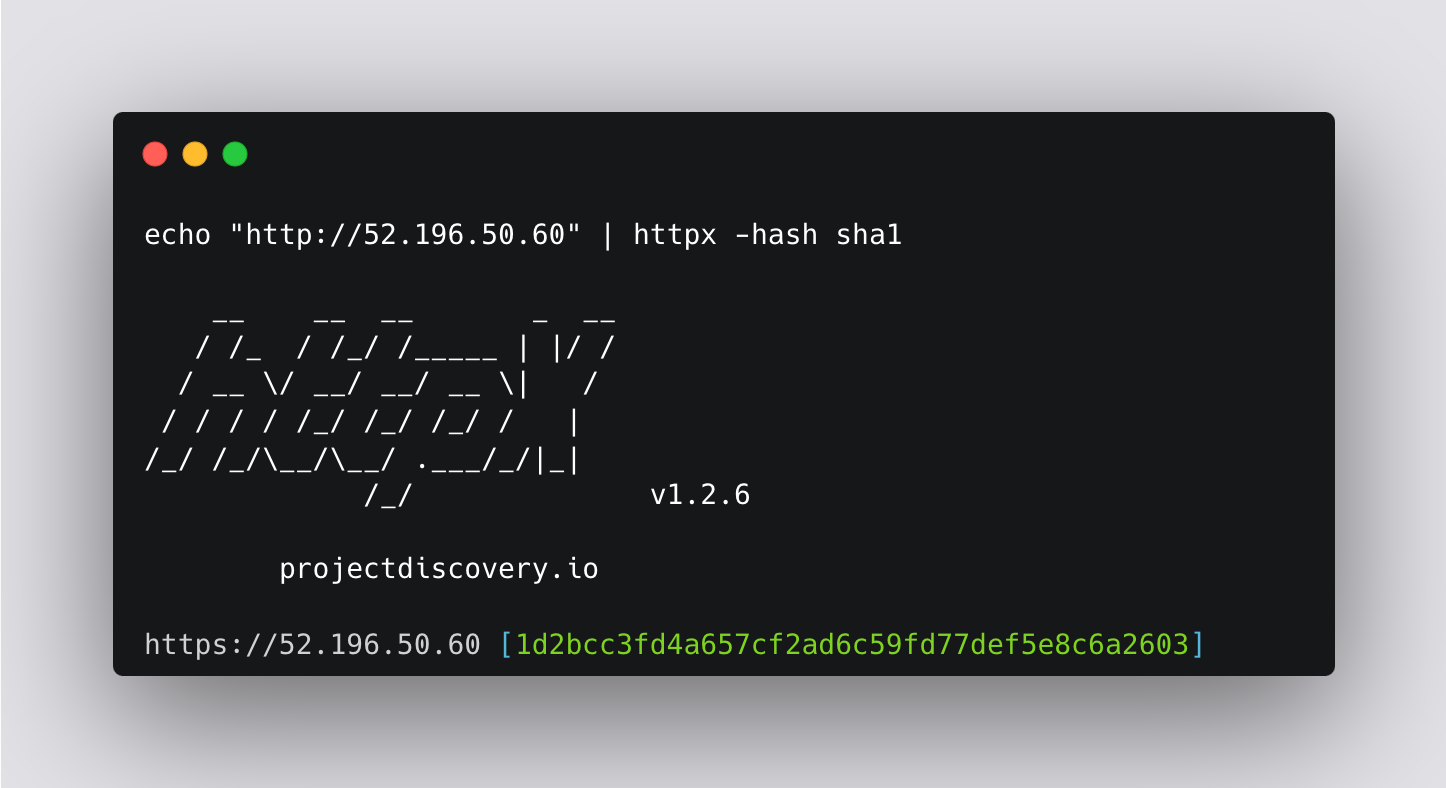
1d2bcc3fd4a657cf2ad6c59fd77def5e8c6a2603.We can use the DSL helper function sha1() with the body element to match the response body hash.
Matchers Syntax:
matchers:
- type: dsl
dsl:
- "("XXXXXXX" == sha1(body))"We can use this in the detection of Brute Ratel 4 servers. Let’s insert this matcher into a template.
Final Template:
id: brute-ratel-c4
info:
name: Brute Ratel C4 - Detect
author: pussycat0x
severity: info
description: |
Brute Ratel C4 (BRc4) is a legit red-teaming tool designed from the ground up with evasion capabilities in mind, but in the wrong hands can cause significant damage. Learn how to protect your organization with our Brute Ratel C4 Spotlight.
reference:
- https://bruteratel.com/
metadata:
verified: "true"
shodan-query: http.html_hash:-1957161625
tags: c2,bruteratel,c4
http:
- method: GET
path:
- "{{BaseURL}}"
matchers-condition: and
matchers:
- type: dsl
dsl:
- "(\"1a279f5df4103743b823ec2a6a08436fdf63fe30\" == sha1(body))"
condition: and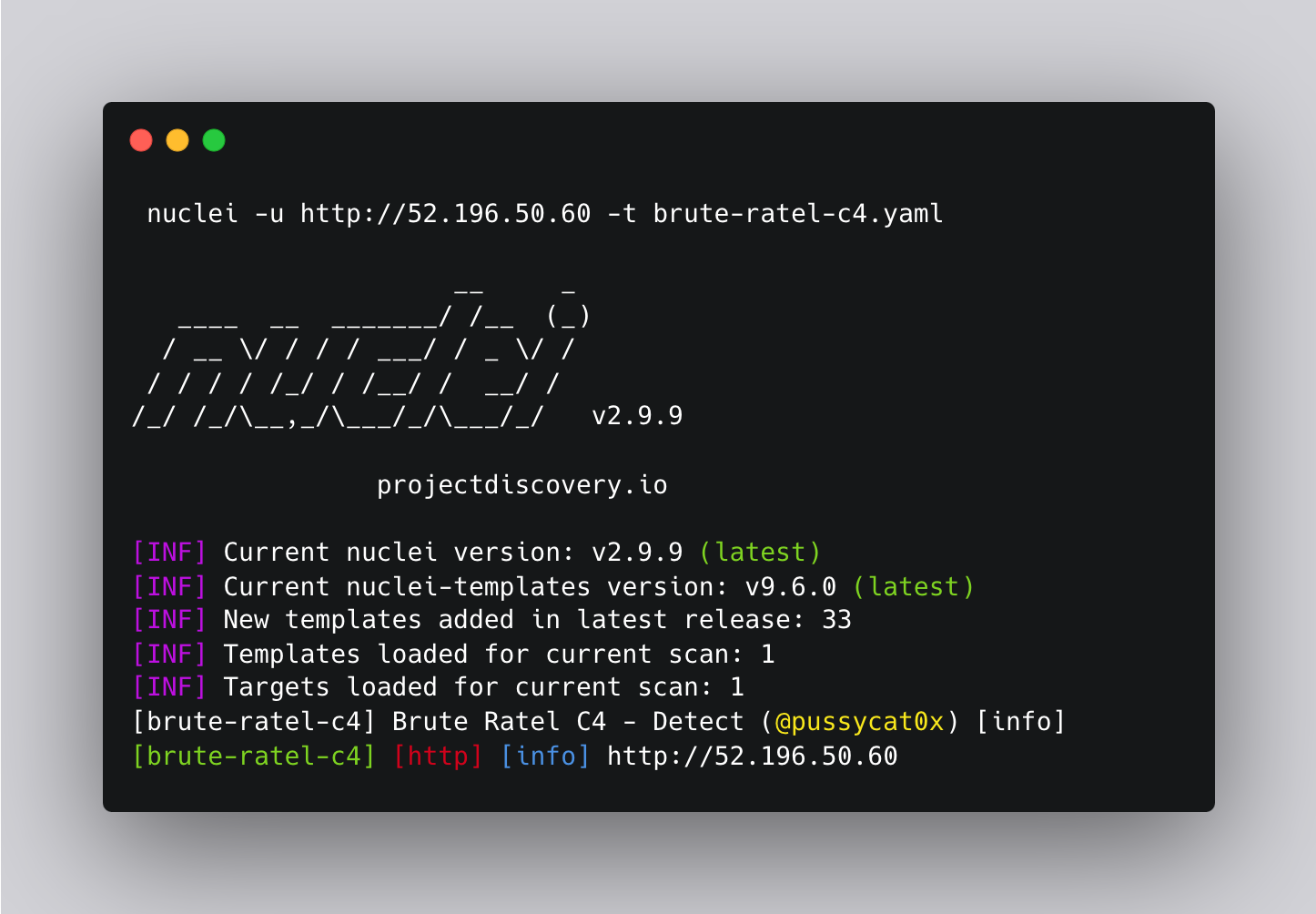
Examples: https://github.com/projectdiscovery/nuclei-templates/blob/main/http/exposed-panels/c2
JARM:
JARM is a technique that analyzes the server's TLS handshake process, focusing on various aspects such as cipher suite ordering, extensions, and their values to generate a fingerprint for the server. By comparing these fingerprints, we can identify potential C2 servers. Tlsx’s JARM argument can be used to get the JARM fingerprint for a target.
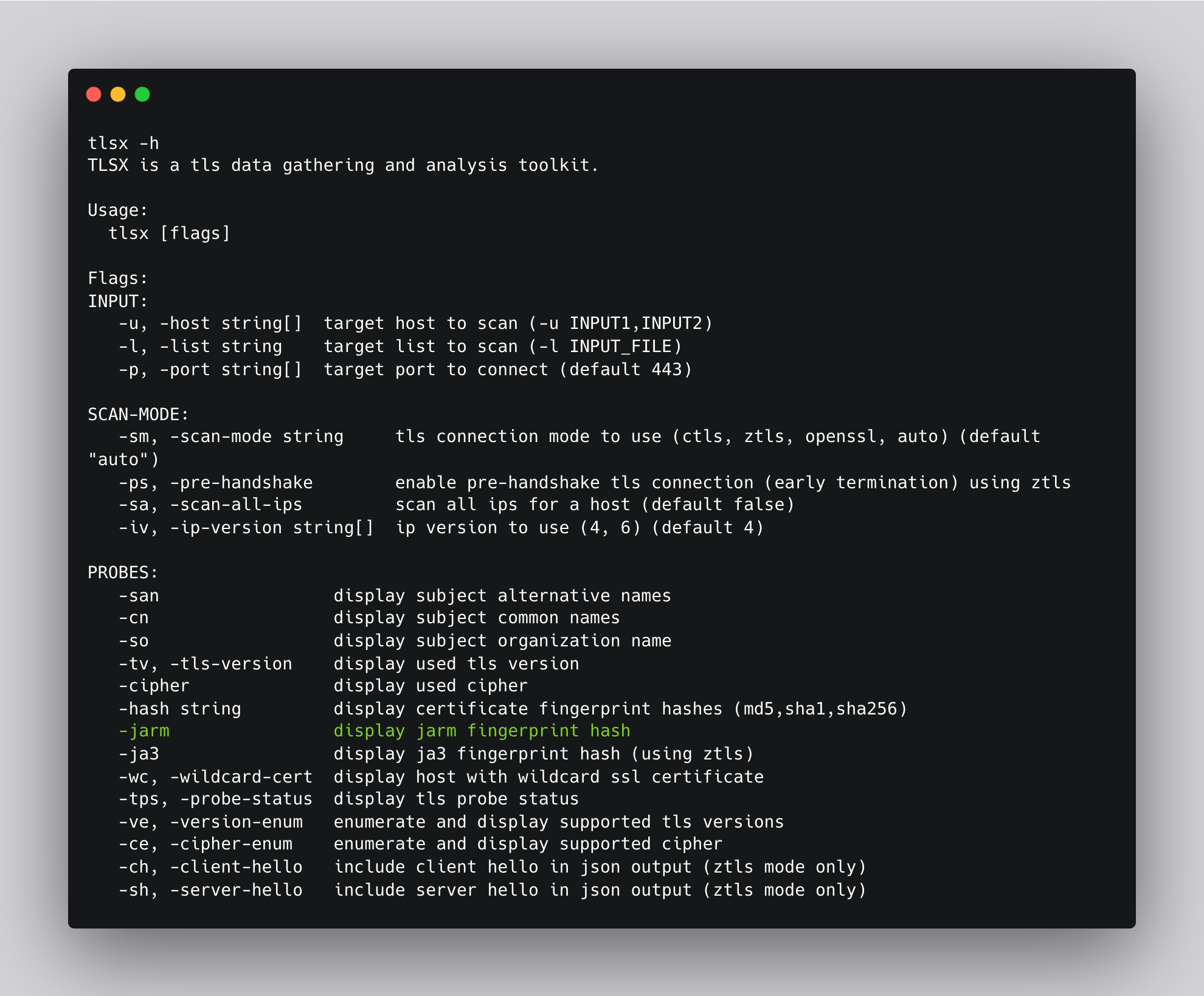
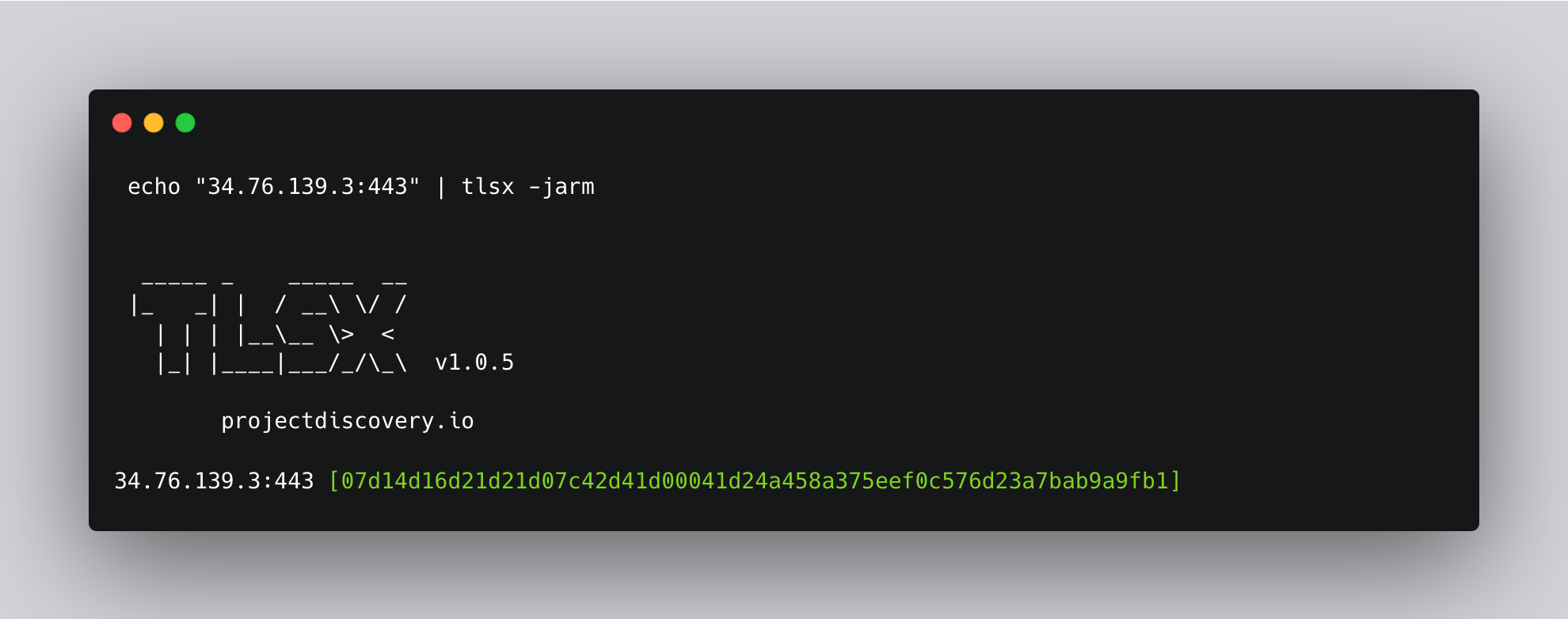
In this template, the jarm() - helper can be used to fetch JARM hashes from target host.
Jarm uses lots of probes, hence it might be implemented as a helper function like jarm() to minimize the execution time, and the result should be stored in some internal kv cache to avoid recalculating it multiple times.
The jarm helper will calculate the TLS finger print value of Hostname and it’s condition with our predefined JARM Value.
Matchers Syntax:
matchers:
- type: dsl
dsl:
- "jarm(Hostname) == 'xxxxxxxx'"To prevent false positives, we've opted for the TCP protocol over HTTP when utilizing JARM. To achieve this, we'll be transmitting placeholder data to the remote host. Meanwhile, the engine will process and store the hash results, which will later be cross-referenced with our template for validation. Finally, we convert the data into a hex value.
- inputs:
- data: 2E
type: hexJARM being used to detect a Cobalt Strike C2 server.
Final Template:
id: cobalt-strike-c2-jarm
info:
name: Cobalt Strike C2 JARM - Detect
author: pussycat0x
severity: info
description: |
Cobalt Strike gives you a post-exploitation agent and covert channels to emulate a quiet long-term embedded actor in your customer's network.
reference:
- https://blog.sekoia.io/hunting-and-detecting-cobalt-strike/
metadata:
verified: true
shodan-query: ssl.jarm:07d14d16d21d21d07c42d41d00041d24a458a375eef0c576d23a7bab9a9fb1+port:443
tags: jarm,c2,ir,osint
tcp:
- inputs:
- data: 2E
type: hex
host:
- "{{Hostname}}"
matchers:
- type: dsl
dsl:
- "jarm(Hostname) == '07d14d16d21d21d07c42d41d00041d24a458a375eef0c576d23a7bab9a9fb1'"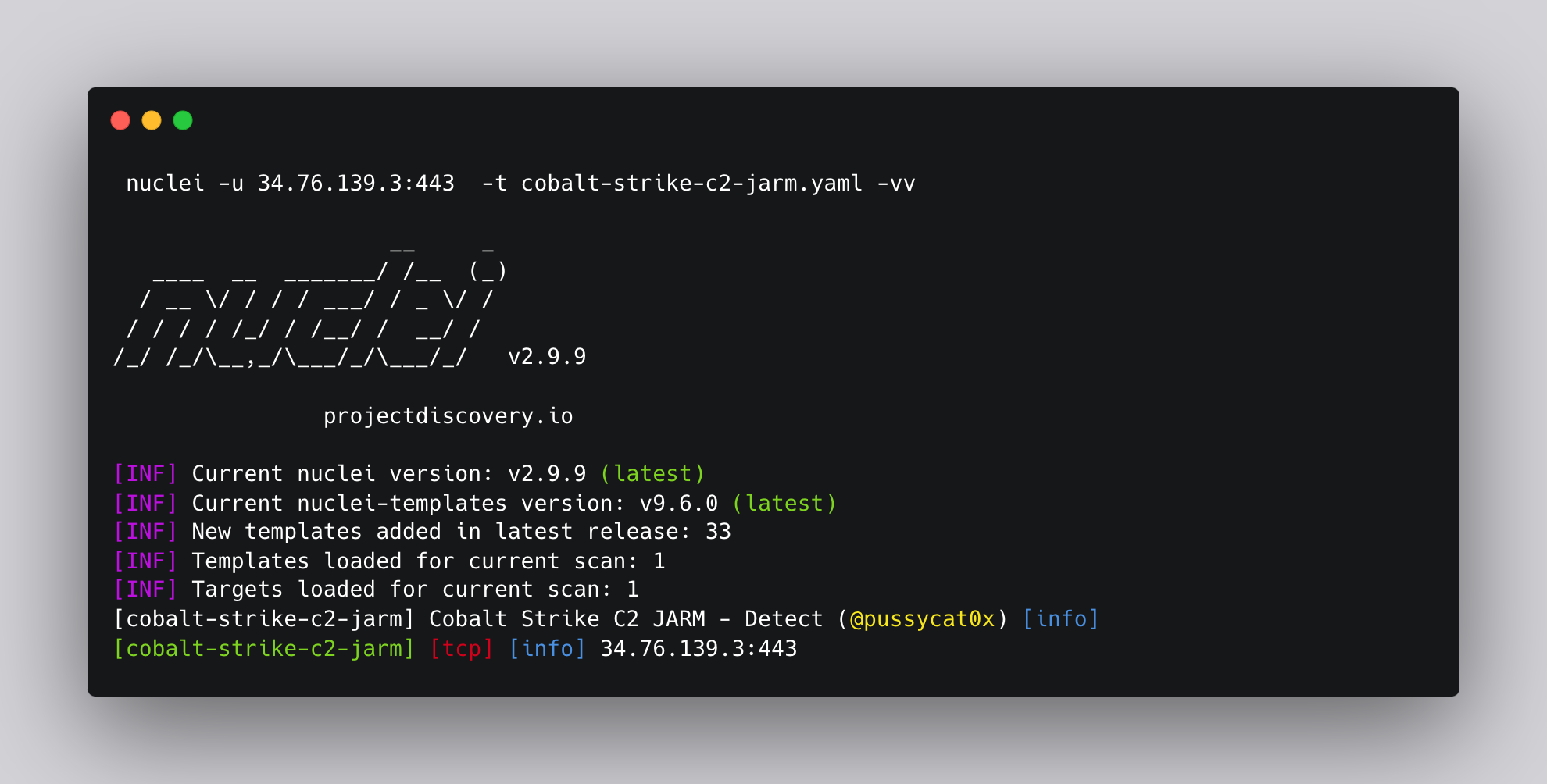
Conclusion
C2 server detection is crucial for identifying and mitigating cyber threats. Nuclei templates offer a powerful and flexible framework to enhance the threat hunting process. By using various detection techniques like default SSL certificates, body hashes, and JARM, security professionals can efficiently identify potential C2 servers and take appropriate actions to protect their systems and networks.
We encourage the community to actively contribute to the Nuclei templates repository (https://github.com/projectdiscovery/nuclei-templates/tree/main/ssl/c2). Encouraging open collaboration ensures that the community benefits from diverse perspectives and expertise, leading to more effective and innovative solutions. By sharing new and updated templates, we can collectively strengthen threat intelligence and improve the overall security posture against C2 servers. Let's collaborate and make the internet a safer place for everyone. Happy hunting!
We are excited to announce the release of Nuclei Templates v9.5.8
如有侵权请联系:admin#unsafe.sh