The blog post describes how I could have Hacked 100k+ Loyalty Programs to get free points & redeem them for free stuff or coupons.
Hope you guys are doing good, The bug was simple to exploit but it took a while to figure out and make it happen. I’ll try to keep the blog as simple as possible.
The target system was an eCommerce loyalty & rewards app that allows different platforms & stores to provide loyalty points to returning customers. The App was providing its B2B services on Platforms such as Shopify, BigCommerce & Wix, etc. Thus all those websites using their service became vulnerable According to the service provider itself they have over 100k Active customers & I was able to identify and tested exploitability on over 38k+ Top-level stores.

I was doing a pentest for a client on their web store & they had a loyalty program listed on their site, As the client needed to evaluate all possible threats I had to look for a way to increase reward points and purchase stuff with them or get massive discounts. To Make sure anything related to my client wasn’t vulnerable.
The rewards application had multiple ways to earn points and then redeem them for free gifts and discounts. The rewards could be a free item, free delivery, or maybe exchange coupons for cash such as 15000 points for $5.
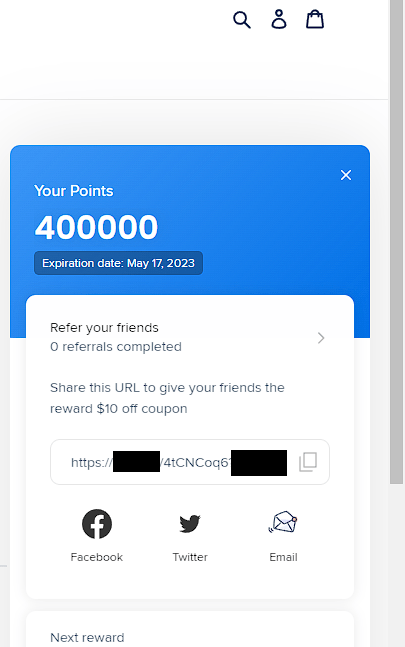
When we first open the rewards section we get a popup like this that shows our referrals & Points earned so far.
I started testing the API endpoint to see what changes it makes on my client’s site and as you signup on to the main store an account is also made on the 3rd party site containing your information that will then be used for issuing rewards and giving discounts codes.
There were multiple ways to earn rewards such as Liking the Facebook page, following on Instagram, buying something, and referral rewards. at first, I saved the following API Endpoint that gives all info of our user account.
and any changes made to your customer account on the store will also reflect on this 3rd party API.
As the platform had pretty interesting API requests I decided to google and read more about their API and they had their API Docs listed on their developer site.
After reading their API Docs the following Notice/Warning ⚠️ caught me by surprise.

According to their docs, this endpoint “Create a points transaction” isn’t available to public apps. thus someone like a customer should be able to see what goes on when an admin creates points on someone’s account and most importantly only an admin account with proper privileges should be able to adjust point balance.

But as they listed the endpoint in their public docs I decided to give it a try as a customer while having only customer privileges.

Making a Request actually did increase my points balance & having no limit to how many points can be added.
I added a few thousand Points 😁
After getting the points I could easily redeem them for a free product or discount code.
And on some web stores, they even had an option to cash in thus making coupons that can buy you the most expensive stuff as well.
In the end, you can simply use the coupons generated by this on checkout

So That’s it for the Vulnerability itself, I hope it was easier to understand and read. 👍
While testing and finding the full exploit capability of this bug was extremely fun but at the end of the day I had to let my customer know and get them to disable the rewards program for time being and multiple emails were sent off to the affected vendor and at the moment of publishing this Blog, the vendor has made the endpoint properly secure with proper permissions and the client’s back again with the rewards program.

Some key takeaways for Hackers & Developers.
For Hackers:
- Look at the target from all aspects. (customer, admin, vendor, hacker)
- Try to find API documentation and read & understand them
- Learn to build a request without API documentation.
For Developers:
- Try not to leave critical information via API docs such as endpoints that shouldn’t be public or endpoints that should be given only to subscribers.
- Properly validate API endpoints and their permission.
Thanks for Reading!

Post Views: 92