
2023-9-28 23:58:20 Author: securityboulevard.com(查看原文) 阅读量:5 收藏
Fortify your defenses against SMS toll fraud by detecting and thwarting malicious bots early in the funnel, elevating your attack protection and securing your financial interests.
The threat known as SMS toll fraud has become a significant financial challenge, causing companies to lose tens of billions of dollars each year.1 This issue has been worsened by the evolving tactics of fraudsters. In the early days of protecting against SMS toll fraud, companies employed several strategies that, while innovative at the time, have become less effective due to the changing attack tactics. Approaches like simple CAPTCHA, static keyword blocking, and sender ID whitelisting became outdated as attackers uncovered ways to bypass these techniques.
In their place, modern technologies and strategic measures are being used to analyze behavior and identify patterns that could indicate fraudulent activity, such as regular audits and updates. But to be truly effective, the number one way to defend against SMS toll fraud is to catch it before it has a chance to propagate. This effort requires an understanding of how attackers try to pull off this sneaky, costly attack.

RECOMMENDED RESOURCE
Snapchat Identifies Critical Risk & Shows Direct Savings with AWS & Arkose Labs
How SMS Toll Fraud Works: the Mechanics of an Attack
Before we look at how to stop SMS toll fraud in its tracks, let’s quickly review what it is and where it fits into the overall SMS fraud picture. SMS toll fraud is a growing form of cyberattack where scammers abuse account registration, 2FA, and similar mechanisms to send large volumes of SMS messages to premium-rate numbers, resulting in fraudulent SMS charges to businesses. While it fits under the umbrella of international revenue share fraud (IRSF), it is all about attackers getting in and out quickly, capitalizing on the surge of high-volume, high-cost SMS messages, while ensuring these charges are invoiced to unsuspecting companies.
At a very high level, here’s what a typical attack looks like from a business POV.
- The business app or website receives a slew of new registration, login, or other requests from the attacker posing as legitimate consumers.
- The business uses SMS messages to send codes or OTP (one-time password), via its SMS provider, to these “consumers” for web authentication.
- The SMS service provider sends that traffic to the regional telco.
- The regional telco(s) then sends that traffic to a premium number provider.
- The premium number provider then sends the inflated bill back to the business.
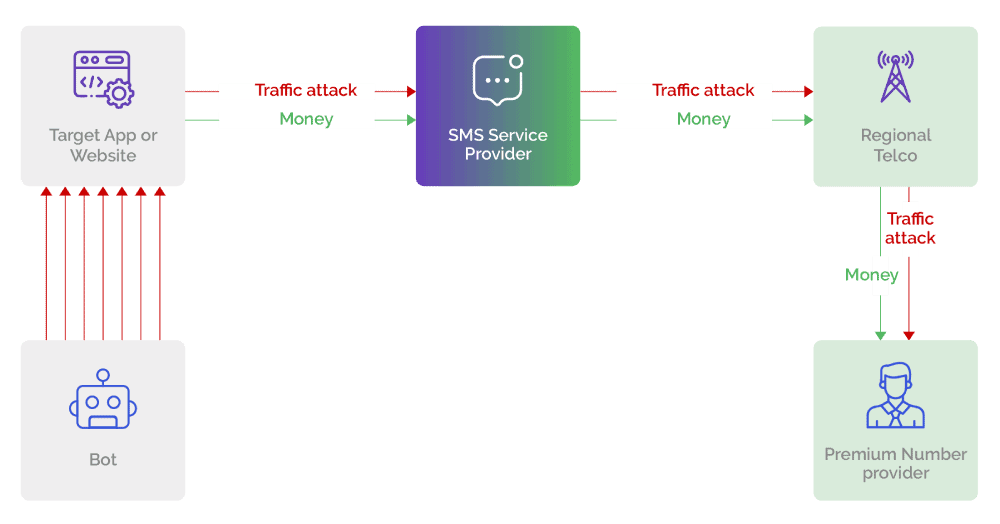
What isn’t clear from this diagram is what is happening behind the scenes, on the telecom and attacker’s side. To truly understand how SMS toll fraud works and how to stop it, it’s important to dig into the financial motivations behind the attacks.
Follow the Money
In the simplified view of an attack above, it’s easy to see how the toll fraud attack takes place. What’s less clear is what the attackers have to gain. To the business, it may seem the attack starts when attackers launch fake registration or other schemes, but in reality it starts when the bad actors hatch the criminal scheme.
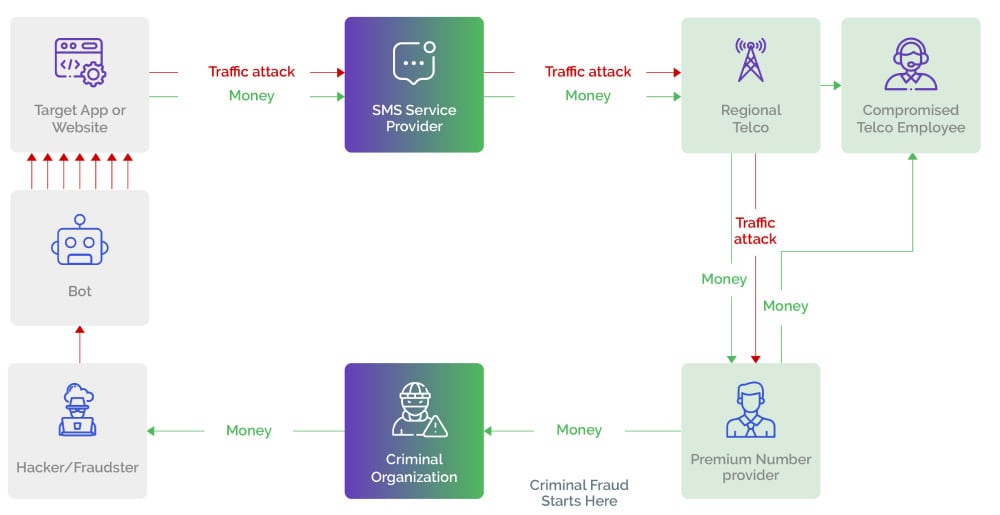
The criminal fraud starts when bad actors collude, and they may be any, all, or some combination of the following: an employee at a regional telecommunications company, an employee at a premium-number provider, a criminal organization, and/or a fraudster who carries out the actual attack.
Here’s one such scenario:
- A compromised employee at a regional telco gains access to a set of premium-rate phone numbers and shares those numbers with a criminal organization.
- The criminal organization passes those numbers along to a fraudster.
- The fraudster initiates an attack on the business by registering fake accounts.
- The business uses SMS messages to send one-time passwords, via its SMS provider, to the purported new accounts.
- The SMS service provider sends that traffic to the regional telco.
- The regional telco sends that traffic to a premium number provider.
- The premium number provider sends the inflated bill back to the business.
- The business pays the inflated bill.
- The colluding telco, the criminal organization, and the black hat hacker split the illegal gains.
Part of the reason SMS toll fraud has become so lucrative is because the bad actors can easily carry out these attacks at scale. Unlike in the past, where it would take a long time to manually execute an attack, today attackers can achieve scale in a matter of seconds. They can use the latest technologies including easily available bots and bots-as-a-service complete with technical support, to quickly launch attacks and make massive financial gain.
To increase their income from the SMS toll fraud, attackers try to maximize the number of SMS messages sent out. Therefore, they use bots and automation to key in thousands of mobile numbers in apps, web forms and websites that trigger enormous amounts of SMS messages in no time. Since the targeted digital platform cannot recall the SMS messages once initiated, it can only absorb the costs associated with the fraud.
Stopping the SMS Toll Fraud Madness
This begs the question: How can businesses best protect themselves from SMS toll fraud?
At first glance it might seem that stopping SMS toll fraud at the source, the colluding telecoms, might be the most effective approach. But this doesn’t take into account the history of SMS toll fraud and its current ramifications. Originally, the original targets of SMS toll fraud were telecom carriers themselves, as some unscrupulous elements within a carrier network seized this opportunity to make money.
For instance, an SMS message that originated in the US and was destined for, say, Country X, would travel through Carrier 1 to Carrier 2, who would deliver it to a carrier in Country X. Now, if Carrier 2 decided to forward the number to a premium number that was priced higher instead of the intended number, the new carrier would charge the money back to the previous carriers.
To ward off the losses, telecom carriers started pushing back the burden of termination charges back to the originator, which today is the digital platform (your business’s website or app). If a premium-rate number provider today charges, say, $15 for every message, your digital platform now has to pay $15 for that SMS. This financial incentive makes it a rather lucrative proposition for attackers.
A more effective way to stop SMS toll fraud is to keep the attack from happening in the first place.
Blocking Attacks Up the Funnel
Unfortunately, businesses usually realize they have been attacked only when they see the inflated telecom bills. By then it is too late, and they cannot take any corrective action. That said, businesses are now taking note of this growing challenge and are looking out for ways to combat it.
Because bad actors make money by conducting these attacks at scale, i.e., using automated attack tools like bots, global brands use bot detection and prevention solutions up the funnel to protect themselves from the losses accrued from SMS toll fraud, while ensuring superior account security of their genuine consumers.
Arkose Labs is one such solution that provides modern businesses with superior protection against bot-driven SMS toll fraud attacks. Arkose Labs acts as a gatekeeper on a registration page, identifying and stopping malicious bots from initiating automated outflow of fraudulent SMS messages at scale.
Arkose Bot Manager triages the incoming traffic and, based on real-time risk-assessment of every user, administers Arkose MatchKey challenges to suspicious sessions while allowing genuine traffic to continue unhindered. Using a combination of innovative identity proofing and targeted friction, Arkose MatchKey, the proprietary challenge-response authentication mechanism, prevents bots from creating fake accounts. And it all comes with 24×7 SOC support.
By blocking malicious bot-driven traffic at the beginning of the funnel, Arkose Labs protects the digital platform from massive financial losses and provides superior protection against SMS toll fraud in the long-term.
Avoid inflated telecom bills and protect your business from SMS toll fraud. Book a demo now to learn how to block SMS toll fraud attempts before bots bombard your digital platform.

RECOMMENDED BLOG
Telecom Fraud Trends
*** This is a Security Bloggers Network syndicated blog from Arkose Labs authored by Arkose Labs. Read the original post at: https://www.arkoselabs.com/blog/prevent-sms-toll-fraud-attacks/
如有侵权请联系:admin#unsafe.sh
