2019-03-18 17:55:50 Author: hackernoon.com(查看原文) 阅读量:145 收藏
By default ssh logs out ssh attempts , wether they’re successful or not , what it doesn’t do by default is log out the passwords they’ve tried.
So i thought it would be a good idea to slightly modify ssh to log them passwords too.
So here we go , you will need to quickly compile openssh , zlib and openssl
Note you have to have build essentials gcc glibc-devel and others…
Nothing to note up there other than:
sed -e 's/struct passwd \* pw = authctxt->pw;/logit("Honey: Username: %s Password: %s", authctxt->user, password);\nstruct passwd \* pw = authctxt->pw;/' -i auth-passwd.cI am basically injecting a little logit() call before the struct definition , check the code of auth-passwd.c if you wanna know more about it.
So that will compile zlib , openssl and openssh and will prefix it all to
/opt/openssh2
You can start openssh as follows:
/opt/openssh2/dist/sbin/sshd -f /opt/openssh2/dist/etc/sshd_config
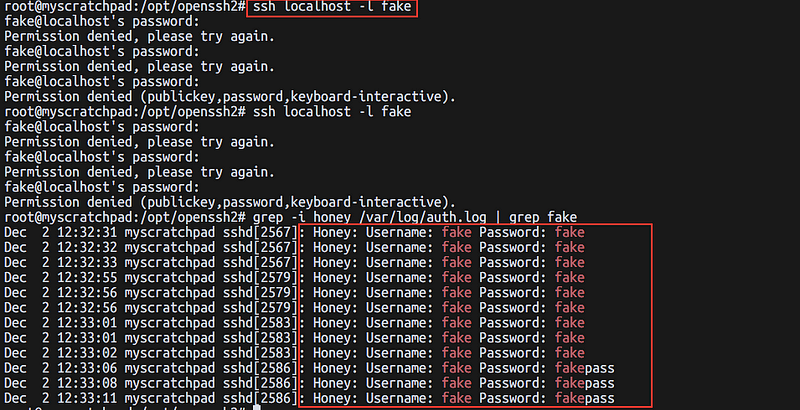
That should get the daemon going , and you can try a few fake attempts to login over ssh:
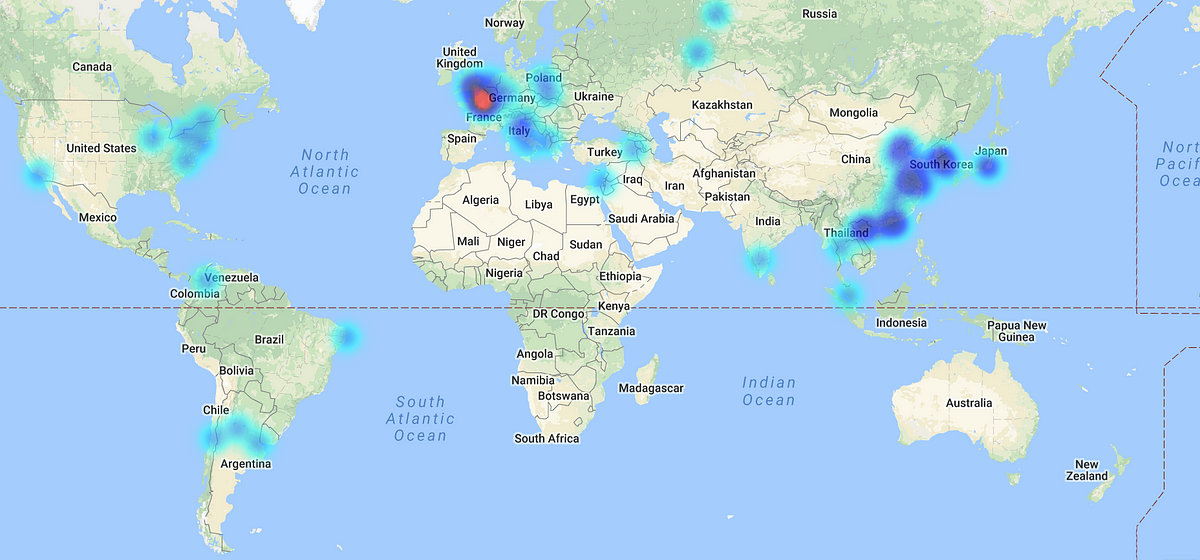
After 10 hours , the results are quite interesting:
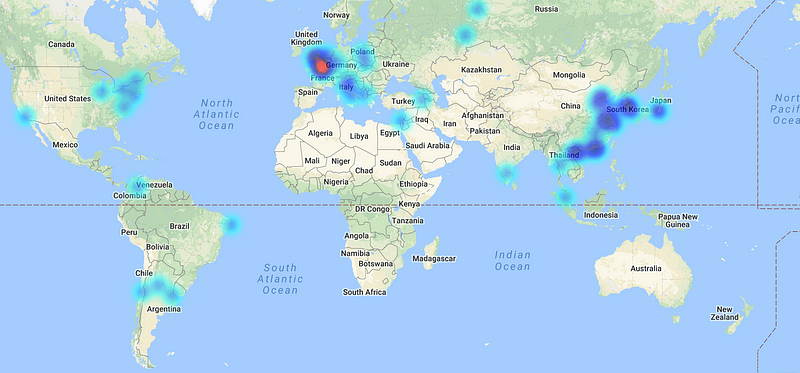
First , countries that i got hits from: (Thanks to ipheatmap.azurewebsites.net)
"HR Pula"
"CN Wuchuan"
"KR Seoul"
"DE Frankfurt am Main"
"NL "
"CN Shenzhen"
"RU Yekaterinburg"
"RU Nyagan"
"US Boydton"
"CN Kunshan"
"CN Hefei"
"TH Kamphaeng Phet"
"CN Beijing"
"HK Hong Kong"
"IL Tel Aviv"
"FR "
"PL Inowrocław"
"PL Krakow"
"IT Giugliano in Campania"
"FR Paris"
"GB London"
"VN Hanoi"
"VN Hanoi"
"VN Hanoi"
"CN Zhengding"
"CN Dongyangshi"
"CN Qingdao"
"CN Bengbu"
"CN Shanghai"
"US Los Angeles"
"IN Bengaluru"
"KR Seoul"
"KR Bucheon-si"
"KR Yangsan"
" "
"JP "
"CL "
"FR "
"JP Tokyo"
"US Buffalo"
"HK "
"CN Lianyungang"
"CN Beijing"
"US Chicago"
"AR Villa Allende"
"US Piscataway"
"AL "
"BR Recife"
"IT Soci"
"CO Bucaramanga"
"AR "
"TR Ağrı"
"FR "
"CA Montreal"
"MY Kuala Selangor"
"FR Ivry-sur-seine"
"FR "
(Thanks to ipinfo.io) (you can curl it and jq it)
So now the most frequent passwords!
46 password
43 123456
36 1234
29 admin
29 12345
17 abc123
16 root
11 support
10 test
10 123
9 ubnt
9 fucker
9 fake
8 raspberry
8 guest
8 admin123
7 password123
7 default
7 123456789
6 user
6 alpine
6 12345678
6 111111
5 wubao
5 ubuntu
5 raspberrypi
5 manager
5 git
5 1234567
4 system
4 operator
4 mysql
4 1
4 000000
4
3 waldo
3 tomcat
3 postgres
3 pi
And the most used users were:(counting the attempts)
1689 root
72 admin
31 test
24 postgres
21 jenkins
14 user
13 mysql
12 support
12 fake
11 nagios
11 deploy
10 oracle
10 guest
9 mother
9 hadoop
8 vagrant
8 tomcat
8 pi
8 git
7 ubuntu
6 zabbix
6 weblogic
6 user1
6 debian
6 backup
5 prueba
I’m gisting the full thing , so you can find look your fav password in there :)
如有侵权请联系:admin#unsafe.sh
