2020-3-17 10:59:21 Author: blog.securitybreached.org(查看原文) 阅读量:1 收藏
Hey Everyone,
My name is M.Qasim Munir and this is my first blog article that I’m writing about getting started in android apps pen-testing. I hope this article will help you with learning something new.
Getting Started in Android apps Pen-testing (PART-1):

Amazing development and growth in mobile apps have carried a bunch of vulnerabilities that attackers are ready to exploit. if you are developing applications for Android and iOS devices and you’re not up to speed on pen-testing strategies, you have to get into it quickly.
In this article, I’m not gonna only write about android apps pen-testing but I’ll also describe how to setup Android testing LAB/ENVIRONMENT including different open source tools and scripts.
Pen-testing android apps require different methodologies than web applications. The difference is that you have to figure out a different method by reverse engineering applications. Additionally, you need to set up a virtual or real device according to which type of applications you wanna test.
Let’s get started:
Android Architecture:
Android is an open-source Linux-based system created for a wide array of devices. The below diagram shows the major components of the Android platform.

System Apps:
Android comes with different sets of apps for SMS, Email, internet browsers, etc. Any third-party application can become the user’s default usage.
Native C/C++ Libraries:
Some core Android system components, such as ART and HAL, are built from native code that requires native libraries written in C and C++.
Java API Framework:
The Android OS is available to you through APIs written in the Java language. These APIs form the building blocks you need to create Android apps by simplifying the reuse of core, modular system components.
Linux Kernel:
The foundation of the Android platform is the Linux kernel. For example, the Android Runtime (ART) relies on the Linux kernel for underlying functionalities such as threading and low-level memory management.
Android Security Model:
Android’s Security Model consists of two parts:
-
- UID Separation
- Sandboxing
Security between android application and the system is enforced at the process level through different Linux facilities, such as user and group IDs. there’s another mechanism called “Permission” that enforces different restrictions on the specific operations that a particular process can perform.
I won’t cover the comprehensive details of the security model. So, let’s move to the main thing.
Contents of an APK File:

-
- AndroidManifest.xml
- Assets Folder
- META-INF Folder
- Lib Folder
- Res Folder
- Classes.dex
- Resources.arsc
AndroidManifest.xml:
AndroidManifest.xml contains the name of the application, version, access rights, referenced libraries, etc. this file usually present in the form of Android binary XML that can be converted into understandable form (Plain-text XML) with different tools.
Assets Folder:
This directory contains application assets.
META-INF Folder:
META-INF directory contains the following files:
-
- MF (The Manifest file)
- RSA (The Certificate of the application)
- SF (Contains resources and SHA1-Digest)
Lib Folder:
The lib directory contains the compiled code of the software layer of a processer. this directory further splits into more directories.
-
- Armeabi (Code for all the ARM-based processors)
- arm64-v8a(code for all ARM64 processors)
- x86 (compiled code of x86 processors)
- MIPS (compiled code for MIPS processors)
Res Folder:
Res directory contains the resources that are not compiled into resources.arsc
Classes.dex
Classes.dex are the classes that are compiled in the dex file format understandable by Dalvik virtual machine. (Dalvik is a discontinued process virtual machine in Google’s Android operating system that executes applications written for Android.)
Resources.arsc:
This file contains pre-compiled resources.
Attack Surface:
The below figure shows all the possible attack aspects of pen-testing an android app.

Setting up the Android testing Environment:
Android pen-testing can be done on both Real devices or VM emulators.
Mobile Devices:
If you wanna test applications that involve any attraction with the camera or fingerprint components including how the device behaves then I would suggest doing it on real mobile devices. make sure that you have the right USB drivers installed on your mobile device and a USB cable in very good condition otherwise, you could face many problems.
Choosing the right Operating System:
Android pen-testing on windows operating system is a little bit difficult due to the unavailability of tools for Windows OS. however, an open-source android apps pen-testing distro called “Santoku ISO” specially made for android apps pen-testing. I would recommend using this distro if you running windows operating system. You can also use this on Linux or macOS but I don’t recommend this as this could slow down your system. you can install the same tools on Linux or macOS.
Installing Android Emulator:
There are many android emulators available on the internet, But which one is good for pen-testing?
In my opinion, Genymotion is the best android emulator for pen-testing because it is easy to set up and use and it offers excellent user experience.
You can Download Genymotion Android Emulator from here: https://www.genymotion.com/download/
Please note that you also need to install VirtualBox to work with Genymotion. Genymotion emulator doesn’t work without VirtualBox. So you can download Genymotion with a single package from the official Genymotion site.

Now choose the emulator type and install. it. I’ve installed three emulators:
-
- Google Nexus 5 (Android 8.0, API-26, Density-420)
- Samsung Galaxy S7 (Android 6.0, API-23, Density-640 XXXHDPI)
- Samsung Galaxy S8 (Android 7.0, API-24, Density 640 XXXHDPI)
You can install devices according to your requirements.

Configuring android emulator:
After installing the emulator choose any device and install it then start it from the GUI.
Install Open GApps from the option located on the top right corner.

Genymotion is x86 based emulator, So If you try to install an application which has ARM code, Genymotion will throw an error:
an error occured while deploying the file.
This probably means that the app contains ARM native code and your Genymotion device cannot run ARM instructions. You should either build your native code to x86 or install an ARM translation tool in your device.

This error will prevent you from installing a lot of apps that you would need to install for bug bounty hunting.
The solution for this error is to install ARM-Translation-Tool which can be downloaded from here: https://github.com/m9rco/Genymotion_ARM_Translation
After downloading the ARM-Translation-Tools simply drag and drop it into the Genymotion and restart the emulator and it will be installed.

Note: Please Download the Translation tool according to your android version.
Android Debug Bridge (ADB):
Android Debug Bridge (ADB) is a versatile command-line tool that lets you communicate with a device. The ADB command facilitates a variety of device actions, such as installing and debugging apps, and it provides access to a Unix shell that you can use to run a variety of commands on a device. It is a client-server program that includes three components:
- A client, which sends commands. The client runs on your development machine. You can invoke a client from a command-line terminal by issuing an ADB command.
- A daemon (ADB), which runs commands on a device. The daemon runs as a background process on each device.
- A server, which manages communication between the client and the daemon. The server runs as a background process on your development machine.
Installing ADB:
macOS:
brew cask install android-platform-tools
Linux/Debian:
sudo apt-get install adb
Fedora/SUSE
sudo yum install android-tools
In case if the above commands are not working you can download it from here: https://developer.android.com/studio/releases/platform-tools
Connecting Adb to the mobile device over TCP & USB cable:
If you wanna test android apps on your mobile device then you need to connect Adb with mobile devices using data cable or TCP (Over Network). Let’s do it,
Get a good quality data cable and attach your mobile device to PC/Laptop. Now navigate to mobile settings and enable USB debugging in your phone (A necessary step). now follow the below commands.
adb devices

This command will list devices connected to ADB.
Connecting over TCP:
Connect your phone using the USB cable to PC/Laptop. now enter the below command:
adb tcpip 5555

you will see a port is restarted now disconnect the mobile phone (remove the USB cable). and connect the phone over TCP using the below commands:
adb connect <ip address of device>:<port>
adb devices
After connecting the mobile device, you can use the below command to get a shell in android.
adb shell

the connection will be successful.
Configuring Genymotion with BurpSuit:
First of all, you need BurpSuit to intercept traffic. You can Download BurpSuit from here:
Now let’s configure proxies. Open burp & navigate to the “Proxy Tab” and then “Options Tab”, from here uncheck the selected proxy i.e (127.0.0.1). now open a terminal and enter command “ifconfig” and search “VBOX interface” copy that IP and paste it in the Burp new proxy listener as shown in the below images:



Open mobile wifi and modify the Wifi network with the same proxy used in the BurpSuit.

Now open any internet browser and browse “http://burp”.There will be an option located in the top right corner to download the proxy CA certificate.

The next step is to open any file manager and move to the download folder and rename “cacert.der” to “cacert.crt” and then navigate to Mobile settings > Security > User Credentials > Install from SD Card select the certificate and install it.


Setting up Frida:
FRIDA is a Dynamic instrumentation toolkit for developers, reverse-engineers, and security researchers. It helps you to inject JS snippets into native apps of Android, iOS, Linux, Mac & Windows. In other words, you can inject your own scripts into the black box processes.
You can install Frida & Frida-Tools into your PC by using below commands:
pip install frida-tools
pip install frida

Now the next part is installing the Frida server in an android emulator. To install Frida into your android you need to determine which architecture your android is running. Follow the below steps to determine your Android architecture.
- Start the android emulator and use ADB to get a shell. now type “uname -a” in the ADB shell and check what architecture it is running.

- As you can see here it is 32-bit Architecture so we need to find 32-bit architecture Frida-Server.
- I’m running 12.8.14 version of Frida, So we need to install the same version of Frida-Server into our android emulator.
- You can find Frida server according to your android emulator from here: https://github.com/frida/frida/releases
- Now I’ve to find Frida android server 12.8.14.
- After downloading frida android server you can unpack it by “unxz {frida-xx-xx-xx-xxxx}”
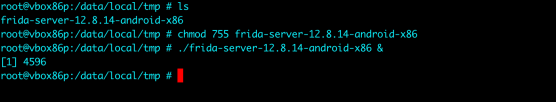
- Now push the unpacked frida server to “/data/local/tmp” directory in android emulator.

- Change Frida-Server file permissions by using the command “chmod 755 frida-server” and run Frida server.

- Now open a terminal in your system and type “frida-ps -U” you shall see that a list of processes has appeared.

So, That’s all for the Part (1) folks. In part (2) I’ll write about different attacks and other tools required for pen-testing.
Stay tuned and share your thoughts on it. Thanks!
Also, Have a look at Hacking SMS API Service Provider of a Company |Android App Static Security Analysis | Bug Bounty POC
如有侵权请联系:admin#unsafe.sh