2020-2-19 09:14:22 Author: blog.securitybreached.org(查看原文) 阅读量:2 收藏
Hey guys so this blog post is about doing static analysis of an Android App, And due to insecure storage of SMS API credentials I was able to Takeover the SMS API here’s a Short POC of the issue.
I decided to do a writeup on this as of increasing messages from new learners regarding doing Analysis of Android App for bug bounty. This is a basic POC guide for them i hope it helps somehow.
Tutorial How to?
So While testing a company had an Android App in scope I downloaded the App in my Android Phone and pulled out the apk for a static analysis, You can also download APK from websites such as
After pulling the APK there are a few different methods to decompile it to get the Java classes files and start working on them & you need a few tools Installed for it. These are available for both MacOS & windows.
After setting these up just simply put the Targeted android App APK file in a separate Directory, Then rename its extension to .zip from .apk, Then extract the zip file in the same directory you will find some files such as, xml docs, path files, resources like templates etc in the folder look for a classes.dex file, there can be one or more than one classes.dex files in the directory.
Now you need to use the tool such as dex2jar to convert the dex file to a java file for this you can simply use the command as
dex2jar classes.dex or if this doesn’t work look for the vision of dex2jar installed and use accordingly i.e d2j-dex2jar classes.dex

Running the command will create a jar file in the directory such as classes_dex2jar.jar etc. once it’s done you need to use the second handy tool a Java decompiler to decompile the jar file to reach the sources in it. for that i prefer using JD-GUI. just open the jar file in it and you can see the java sources files now you can save all of them to a separate folder


And that’s how you gonna get the code to read, understand & look for stuff in it. This was kinda hard way to do it you can do this all with a tool such as
https://github.com/MobSF/Mobile-Security-Framework-MobSF/wiki/1.-Documentation Pretty Useful, Easy, Fast & accurate you can get the same source by simply uploading the APK to it.
Back to the POC:
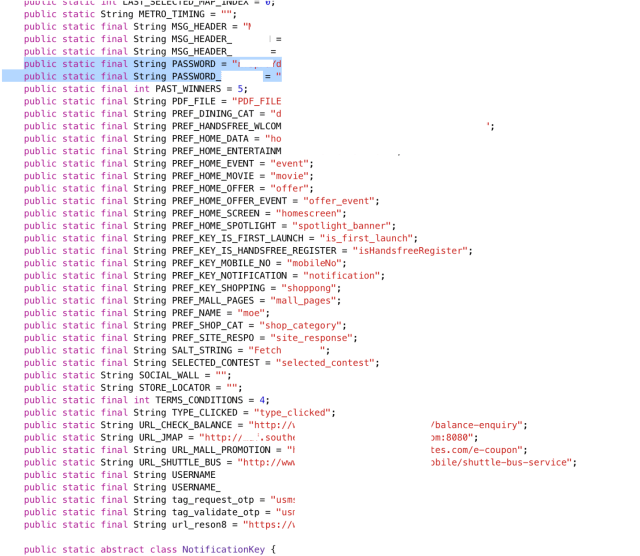
So after doing this all to my targeted Android APP i sat down to read the files and look for information in my checklist when i stumbled upon a file that was named Constant.java. The file was in the SMS path of the android app and contained some juicy information such as “Username, Loacation, Password, Some hidden Endpoints and SMS API URL”

Digging further into it revealed that they are using https://www.reson8.ae/ a 2 Way & Bulk SMS Platform for Enterprises & Marketing so i used the disclosed SMS creds on the platform and got neat clean access to the SMS gateway.

That’s All it took to get into the SMS API Gateway. i could have send SMS, Marketting Updates, download customers phone numbers, recharge etc
Takeaways:
- For Bug Hunters i’ll say always do static analysis of APK before moving towards dynamic testing and other stuff, look for juicy endpoints and make a list and test them on web & mobile as well.
- For companies i’ll say don’t store such information in Apps and if it’s necessary encrypt them properly.

如有侵权请联系:admin#unsafe.sh