You want to learn more about Elastic clusters exposed to the Internet. You know that the Elastic service runs on port 9200 so you go ahead and search on Shodan for that port and you get nearly a million results. A quick glance shows that these results include:
- CDNs
- Honeypots
- SSH servers
- Webcams
- A ton of services running on non-standard ports
You could start modifying the search query to remove all the other services but then you're still faced with the issue that:
a) If Elastic changes its banner then your query won't work anymore.
b) You will miss out on Elastic clusters that are running on non-standard ports.
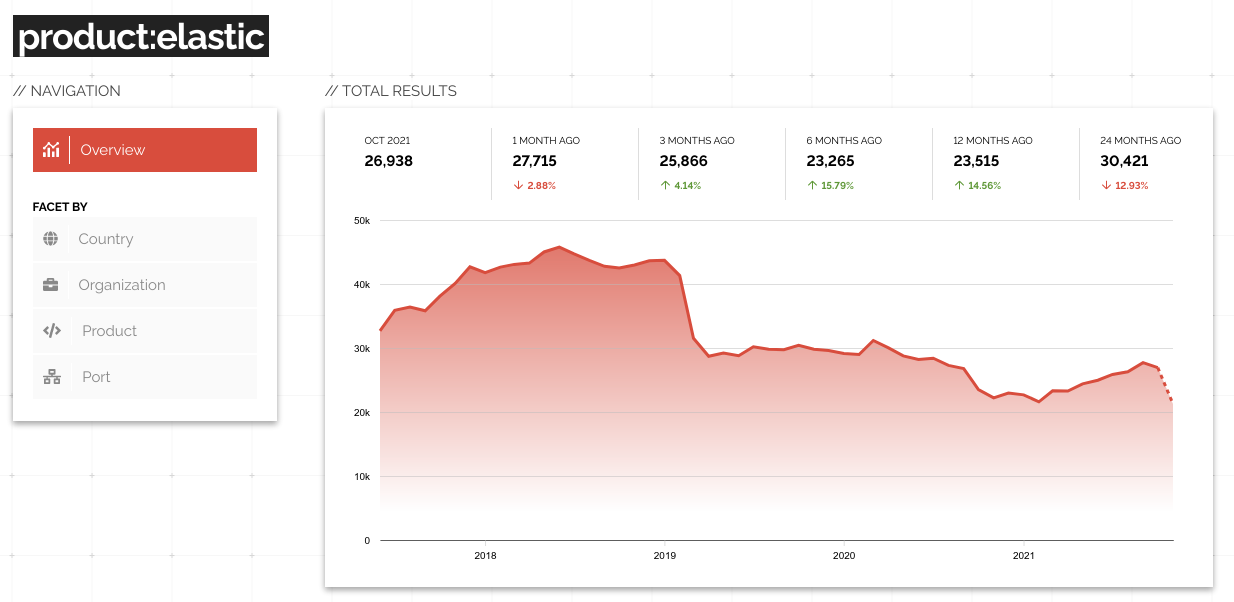
The better solution is to recognize that Shodan is able to fingerprint Elastic and sets the product property to Elastic in those cases. As a result, you can simply search for product:Elastic to get all public clusters across all the ports. And now that we have a good search query we can see how those results have changed over time to identify whether the exposure of Elastic clusters has improved or not:
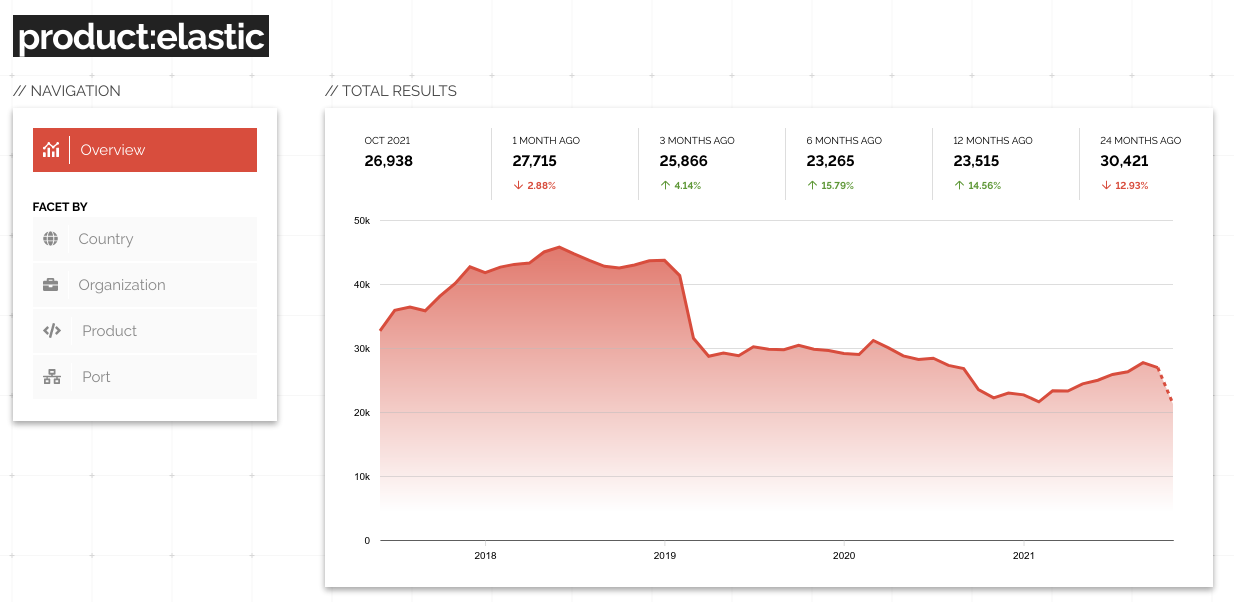
In general, if you only look at the number of open ports across the Internet you often get wildly inaccurate numbers. For example, here is how the results for port:102 have looked over time:
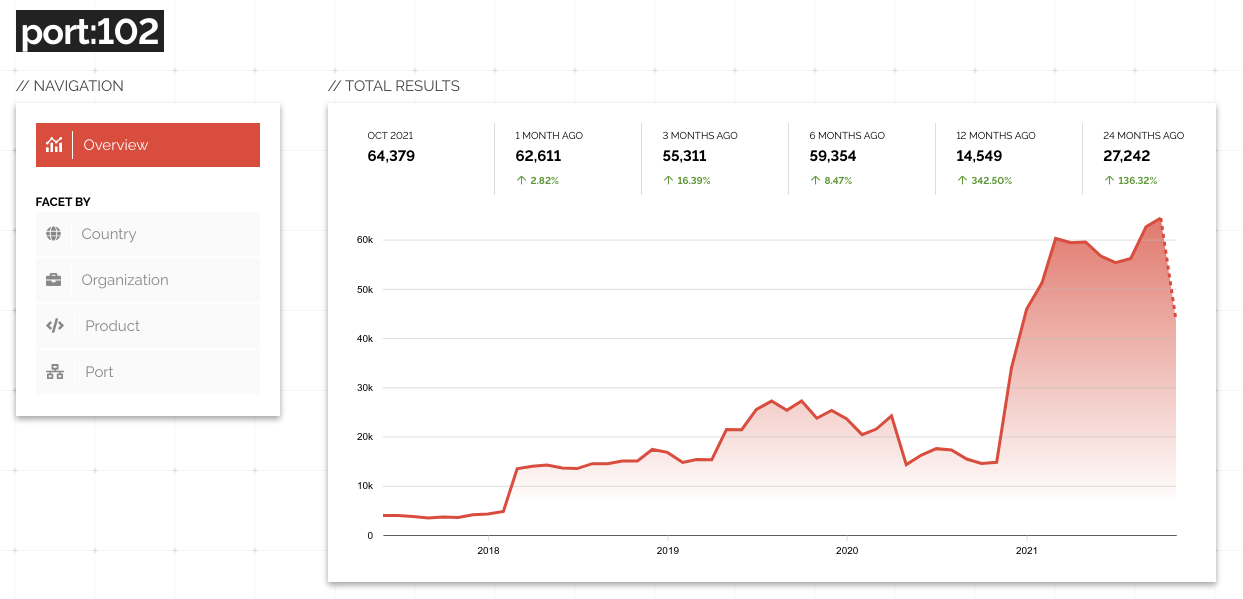
Port 102 is commonly used by the Siemens S7 industrial protocol and most likely what you're interested in when searching on that port. Based on the above image you might think there was a surge in Internet-connected industrial control systems. However, if you add the tag:ics term to filter for services that were identified as industrial protocols then you'll see a very different picture:
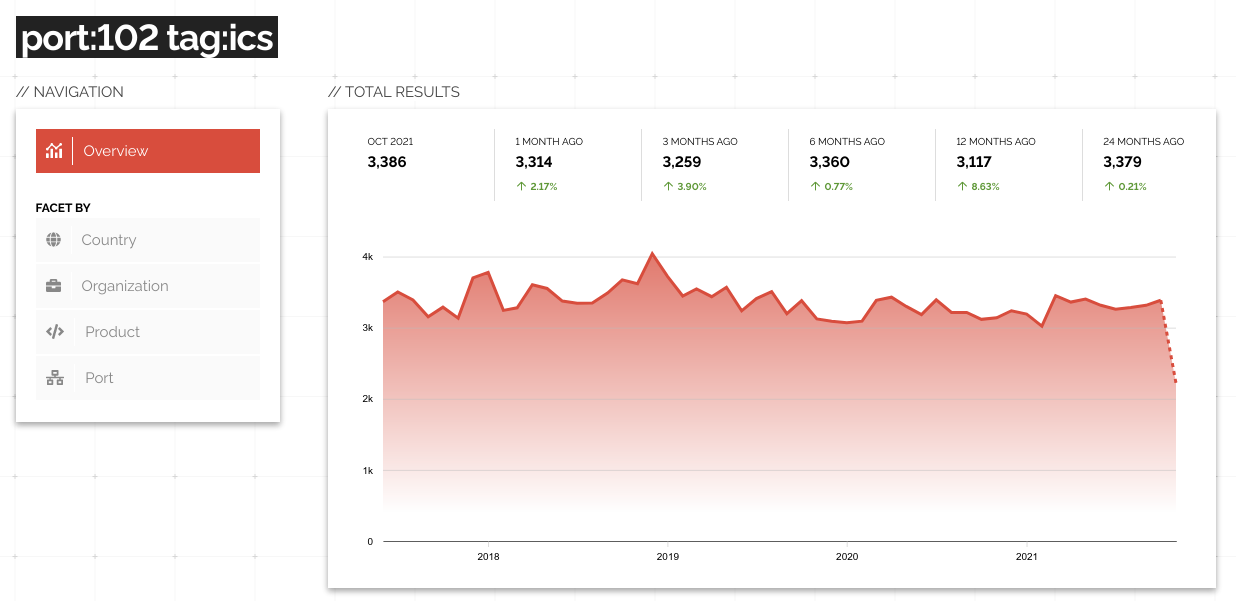
Shodan is good about identifying services on unexpected ports so whenever possible you should leverage the product, os, tag and other protocol-specific properties (http, ssl, etc.) to narrow down results. This will help you get a better understanding of how something is used across the Internet regardless of whether it was left with its default settings or whether the end-user configured it to listen on a different port.