2023-6-13 22:0:0 Author: bishopfox.com(查看原文) 阅读量:7 收藏
CloudFox helps penetration testers and security professionals find exploitable attack paths in cloud infrastructure. However, what if you want to find and exploit services not yet present in your current environment? What if you lack access to an enterprise AWS environment, but want to learn?
Enter CloudFoxable, an intentionally vulnerable AWS environment created specifically to teach the art of AWS Cloud penetration testing, while showcasing CloudFox’s capabilities that help you find latent attack paths more effectively. Drawing inspiration from CloudGoat, flaws.cloud, and Metasploitable, CloudFoxable provides a wide array of flags and attack paths in a capture the flag (CTF) format.
In this blog, I’ll introduce you to CloudFoxable and show off some of the challenges, but really, you should just head over and get started!
Hello CloudFoxable!
CloudFoxable is a new intentionally vulnerable environment that you deploy into your own playground AWS account via terraform, just like you do with CloudGoat and IAM-Vulnerable. What sets CloudFoxable apart is its focus on creating as many distinct vulnerable resources and flags as possible – rewarding users for finding new entry points, lateral movement paths, and data access strategies. Bishop Fox offers CTF challenges (including hints) and a public scoreboard to see how your cloud penetration testing skills stack up against others.

FIGURE 1 - CloudFoxable CTF public scoreboard
Starting Small
One of the things I like most about flaws.cloud & flaws2.cloud is the hint based system that helps you along the way and teaches you as you go. I’ve tried to take a similar approach in CloudFoxable by making some entry-level challenges that teach the player one specific bit of required baseline knowledge for AWS penetration testing. Of course, there are also more complex challenges that are similar to CloudGoat challenges as well.
Challenge: It's a Secret
In one early challenge, to get the flag the user simply needs to evaluate what permissions they have as the ctf-starting-user and access the only flag they currently have access to, which is stored in AWS secrets manager.

FIGURE 2 - "It's a secret" challenge preview
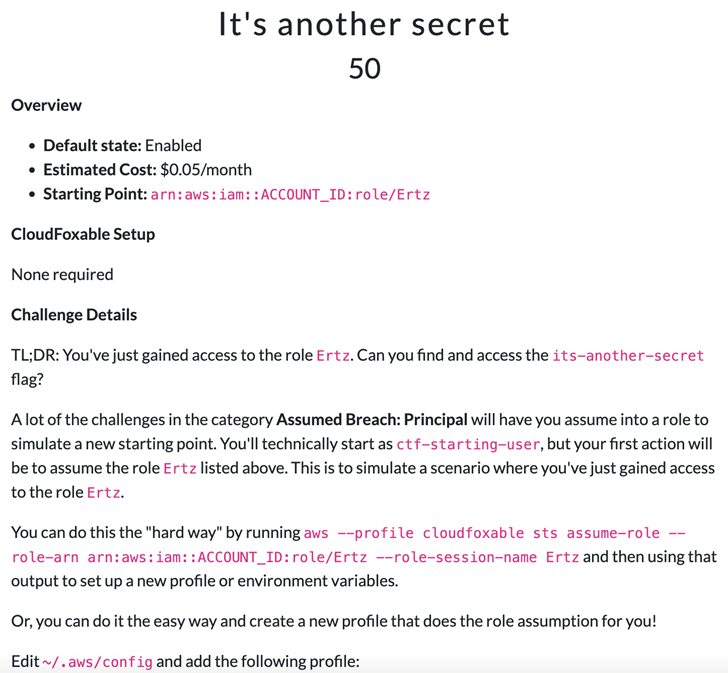
Challenge: It's Another Secret
In the next challenge, starting again as the ctf-starting-user the participant must assume another role to access the secret, adding one additional bit of complexity.

FIGURE 3 - "It's another secret" challenge preview
Challenge: Backwards
In the third challenge, we teach the concept of working backwards by which I mean that sometimes you find something interesting, but you then need to figure out who has access to the thing:

FIGURE 4 - "Backwards" challenge
Going Big
Many of the challenges in CloudFoxable are recreations of attack paths we have exploited on real cloud penetration tests at Bishop Fox. You might be surprised to find out that it is more common to find an easy to exploit path than a complex one. For example, you have compromised a user that has a single permission that allows for privilege escalation. Or you find a vulnerable service that has administrative role attached to it. However, sometimes (on the more fun penetration tests), the security team has started their journey of restricting permissions, and the only path to victory requires exploiting a complex chain of different vulnerabilities and misconfigurations. We’ve tried to include both types of challenges.
Challenge: Trust Me
One interesting challenge involves an IAM role that trusts a GitHub repository through OpenID Connect (OIDC). We’re seeing more and more clients of ours using this configuration, and this challenge was created after this attack path was exploited during a real penetration test. To participate in this challenge, users must create a new private GitHub repository they control and enter that as a variable into CloudFoxable before deploying this challenge.
After entering the repository name and deploying the challenge, participants can use CloudFox to find a potentially overly permissive trust, and they will learn how to create a malicious GitHub action that can assume the IAM role within their CloudFoxable account. With access to the role, the user can capture the flag stored in the SSM parameter store.

FIGURE 5 - "Trust" challenge
This challenge aims to educate those unfamiliar with OIDC-based role trusts about the advantages and security implications of trusting external identities, such as GitHub repositories or Elastic Kubernetes Service (EKS) clusters. Additionally, it demonstrates how to use CloudFox and other tools to quickly identify these interesting IAM roles.
Challenge: The Topic is Execution
Another set of fun challenges covers simple notification service (SNS) topics and resource trusts. In a cloud security posture management (CSPM) style check, you will be told if a topic allows anonymous actions, which is undoubtedly valuable. But what about an SNS topic with an overly permissive resource policy that allows any principal in the same account to subscribe to it? Is that OK? Is that bad? If so, how bad?
Good news! There is a challenge in CloudFoxable that highlights this potential attack path.

FIGURE 6 - "The topic is execution" challenge
What's Next
With the introduction of CloudFoxable, we encourage contributions from cloud security practitioners showcasing examples from real-world breaches and experiences. At its launch, CloudFoxable has challenges that range from very straight forward to very complicated, and we encourage contribution of challenges anywhere within this spectrum.
Many of the challenges I’ve added to CloudFoxable are representations of scenarios discovered during real-life cloud penetration tests. It is a great way to anonymously document attack chains we've discovered during penetration tests, and we'll be adding more challenges over time. Good luck and happy cloud hacking!
Subscribe to Bishop Fox's Security Blog
Be first to learn about latest tools, advisories, and findings.
如有侵权请联系:admin#unsafe.sh