2018-5-6 01:20:0 Author: bartblaze.blogspot.com(查看原文) 阅读量:7 收藏
In this quick blog post we'll have a look at BKRansomware, a Vietnamese ransomware that wants you to top up its phone.
Update: 2018-05-06, scroll down for the update, added to the conclusion.
Analysis
This ransomware is named "BKRansomware" based on the file name and debug path. Properties:
- MD5: 892da86e60236c5aaf26e5025af02513
- SHA1: 6f36c02161a83a3683921fc73319474157f4fb92
- SHA256: c23f695a19346bf3a5b21fb5a281771808953930d8dcb0a359f163ba0329305f
- Compilation timestamp: 2018-05-03 10:04:35
- VirusTotal report:
c23f695a19346bf3a5b21fb5a281771808953930d8dcb0a359f163ba0329305f
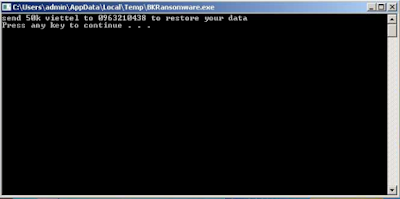
BKRansomware will run via command line and displays the following screen:
| Figure 1 - Ransom message |
The ransomware message is very brief, and displays:
send 50k viettel to 0963210438 to restore your data
Viettel is a form of credit for mobile phones, used in Vietnam and neighboring countries. It is part of "Viettel Group" (Tập đoàn Công nghiệp Viễn thông Quân đội in Vietnamese), a mobile network operator in Vietnam. (Wiki link).
As such, it appears the creators are in desperate need of more credit so they can make calls again :)
It only encrypts a small amount of extensions:
.txt, .cpp, .docx, .bmp, .doc, .pdf, .jpg, .pptx, .png, .c, .py, .sql
Encrypted files will have the .hainhc extension appended. Fun note: files aren't actually encrypted, but encoded with ROT23. For example, if you have a text file which says "password", the new content or file will now have "mxpptloa" instead.
Noteworthy is the debug path:
C:\Users\Gaara\Documents\Visual Studio 2013\Projects\BKRansomware-20180503T093651Z-001\BKRansomware\Release\BKRansomware.pdb
The extension mentioned above, "hainhc" may refer to the following handle or persona on Whitehat VN, a Vietnamese Network security community:
https://whitehat.vn/members/hainhc.59556/
Conclusion
While BKRansomware is not exactly very sophisticated, it is able to encrypt (or rather encode) files, and is unique in the sense that it asks you to top up a mobile phone.
Update: it appears this is a ransomware supposedly used for testing purposes, for both coding and testing VirusTotal detections. However, there seems to be a lot of "testing" going on, including keyloggers. Draw your own conclusions.
Follow the prevention tips here to stay safe.
IOCs
如有侵权请联系:admin#unsafe.sh