2023-9-29 17:19:19 Author: securityboulevard.com(查看原文) 阅读量:19 收藏
Intro: mTLS — The Unsung Hero of Cybersecurity
Picture this: You’re a secret agent on a high-stakes mission. You have a briefcase full of confidential information that you need to hand over securely. Sure, you could pass it to another agent, but how do you know you can trust them? Here’s where mTLS or Mutual Transport Layer Security steps in as the cryptographic equivalent of your secret handshake, your insider code, your double-lock system. If you’re serious about cybersecurity, this isn’t just a "nice-to-have" feature; it’s non-negotiable.
What is TLS? The Building Blocks of mTLS
Before diving into the mTLS universe, let’s take a step back and examine its roots: TLS, or Transport Layer Security. Think of TLS like a padlock on a door; it’s the standard form of cryptographic protocol that makes secure web surfing possible. When you visit a website and see a little padlock icon next to the URL, that’s TLS doing its thing, safeguarding your data from eavesdroppers.
TLS, Deconstructed
| Components | Functionality |
|---|---|
| Cipher Suites | A set of algorithms that help in key exchange and hashing |
| Digital Certificates | Confirms the identity of the server you’re connecting to |
| Handshake Protocol | A set of rules to establish keys for data encryption |
Now, TLS operates under a simple principle: authentication and encryption between a client (that’s you) and a server (the website you’re visiting). But it’s mainly one-way traffic meaning, the server presents a digital certificate to prove it’s legit, but the client doesn’t have to reciprocate.

Herein lies the limitation. It’s as if you’re meeting someone for the first time and only they have to show their ID. Sure, you can trust them to some extent, but what about them trusting you? That’s where mTLS flips the script.
In a few, mTLS isn’t just TLS on steroids, but an entirely different league when it comes to ensuring both parties can trust each other, not just one way, but both ways. And if you’re navigating the treacherous waters of API security, cloud services, or even IoT devices, understanding mTLS isn’t just beneficial it’s essential.
What Makes mTLS Different from TLS? Two-Way Trust, Unveiled

You’ve mastered the basics of TLS, that one-way trust street. Now, let’s venture into the bustling avenue of mTLS, where trust flows in both directions. Imagine a high-stakes poker game; you wouldn’t show your cards to just anyone. What if both players had to prove their identity before laying down any bets? That’s the essence of mTLS a mutual authentication handshake, a two-way street of verifying "You are who you say you are."
The Two-Way Handshake: Authentication Leveled Up
In TLS, only the server goes through an identity check. In mTLS, both the client and server pull out their "digital IDs" during the handshake. This is like a double authentication lock, with both parties swapping keys to open each other’s padlocks simultaneously.
Feature Face-off: TLS vs mTLS
| Features | TLS | mTLS |
|---|---|---|
| Authentication | Server-side only | Server and Client |
| Data Encryption | Yes | Yes |
| Use Cases | Web browsing, Email | APIs, IoT, Intranets |
| Complexity | Moderate | Higher |
Benefits: More Than Just Double Authentication
- Enhanced Security: With both parties authenticated, risk of data interception drops dramatically.
- Precise Access Control: You can customize permissions, narrowing down who gets access to what.
- Audit Trails: Knowing who accessed what and when, makes compliance and auditing simpler.
- Reduced Attack Surface: With each client verified, malicious actors have fewer windows to exploit.
Why this is a Game Changer
Imagine a vault that needs two keys to open. You have one; your trusted partner has the other. Both keys are required to unlock the vault. That’s mTLS in a nutshell a fail-safe against unauthorized access, elevating your cybersecurity from a basic padlock to a full-fledged security system.
In environments where a breach could be catastrophic think medical databases, financial systems, military networks mTLS isn’t just a fancy add-on. It’s a fundamental layer that fortifies the security architecture.
The Uniqueness of mTLS: Final Take
By this point, it should be crystal clear: mTLS isn’t just an upgrade or an additional feature to slap onto TLS. It’s a sophisticated, foolproof approach to ensuring two-way trust in an increasingly mistrustful digital landscape. And in today’s world, where data breaches are just another headline, two-way trust isn’t a luxury; it’s a necessity.
Why mTLS Matters: When Security Is not Optional, It is Essential
If you think mTLS is a nice-to-have feature that’s reserved for highly sensitive government operations, think again. The applications of mTLS are broad, spanning multiple industries and use cases. It’s like a Swiss Army knife in the toolbox of cybersecurity. So where does mTLS really stand out? Let’s deep-dive into the sectors where this technology is more than just a shiny extra it’s the linchpin.
APIs: The Backbone of Modern Business
APIs are everywhere from powering your mobile apps to connecting software systems. Without a robust security layer, they’re ripe for exploitation. With mTLS, both parties in the API transaction must authenticate themselves, dramatically reducing the risk of unauthorized data access.
Healthcare: Beyond HIPAA Compliance
You can’t put a price on patient data. Not only does mTLS satisfy stringent HIPAA regulations, but it also adds another layer of impenetrable security, ensuring that sensitive medical records are only accessible by verified entities. It’s like a double-locked medicine cabinet that only opens with two unique keys.
Financial Sector: Money Talks, Security Shouts
When it comes to banking and trading platforms, a single data breach can result in colossal financial losses. With mTLS, access is tightly controlled, leaving no room for identity spoofing or data leaks. It’s not just about protecting your assets; it’s about safeguarding your trust in the system.
IoT Devices: The Smarter They Get, The Safer They Need to Be
As our homes and cities get smarter, they also get more vulnerable to attacks. Whether it’s a smart thermostat or an entire power grid, mTLS ensures that only authenticated devices can connect and transmit data. That way, your smart fridge won’t leak your grocery list to cybercriminals.
Remote Work: Security Beyond the Office Walls
The home office is the new normal, but security shouldn’t take a backseat. With mTLS, businesses can ensure that only authorized employees have access to internal resources, making remote work as secure as being in the office minus the commute.
Military & Government: National Security Starts with Digital Security
When the stakes are sky-high, there’s no room for error. mTLS adds a virtually unbreakable layer of security, making it an integral part of military and governmental digital infrastructures.
mTLS, the Hero You Didn’t Know You Needed
You wouldn’t use a paperclip to lock a treasure chest. In a world where data is gold and cyber pirates are aplenty, mTLS is your fortress versatile, reliable, and damn near impregnable.
So the next time you wonder if mTLS is overkill, remember this: In an age where digital threats are evolving faster than ever, can you afford not to have the best security tech in your corner?
How mTLS Works: The Blueprint of Unbreakable Security
Decoding mTLS requires dissecting its building blocks, much like understanding a complex machine. Let’s expand on those key elements Certificate Issuance, Handshake Process, and Data Encryption to fully grasp how this impenetrable shield functions.
Certificate Issuance: Digital IDs, Verified and Vetted
For mTLS to work, digital certificates think of them as unique digital passports are mandatory for both the client and the server. These often come from a Certificate Authority (CA), a trusted entity in the cybersecurity landscape.
Client Certificate Process:
- Send a request to a CA for a certificate.
- CA validates your identity and domain.
- Post-validation, the CA issues the certificate.
- Install this certificate on your device or application for use in mTLS.
Server Certificate Process:
- Likewise, request a certificate from a CA.
- Validation of server and domain by the CA.
- CA issues the server certificate.
- Admin installs it on the server to affirm its legitimacy to clients.
Types of Certificates:
| Self-Signed | CA-Issued | Enterprise CA |
|---|---|---|
| Free | Costs involved | Internal use |
| Quick to create | Validation needed | Controlled |
| Less secure | Highly secure | Secure & Private |
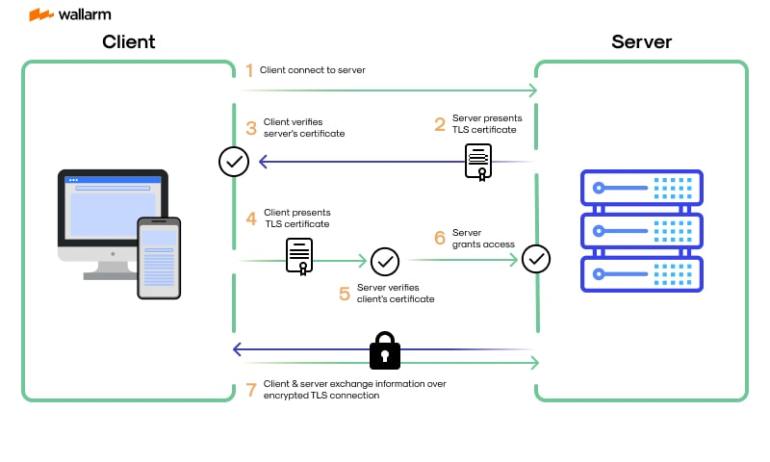
Handshake Process: The 7-Step Symphony of Trust
The mTLS handshake isn’t just a meet-and-greet; it’s a full fledged ritual for establishing trust.
-
ClientHello: The client initiates by sending a "Hello" message. This contains cryptographic algorithms it supports, and a randomly generated value for session identification.
-
ServerHello: Server replies with its own "Hello," picking the strongest mutually-supported algorithms. It also sends its own random value for session identification.
-
Server’s Digital Certificate: Server delivers its certificate for verification. This proves that the server is genuine and not an imposter.
-
Client’s Digital Certificate: The client reciprocates by sending its own digital certificate. This ensures mutual trust by validating the client to the server.
-
Verification: Both the server and the client confirm the validity of each other’s certificates by checking against their list of trusted CAs. If something’s amiss, the handshake fails.
-
Key Exchange: Both parties engage in a secure exchange of keys. These keys are not the actual encryption keys but values used to derive them.
-
Finalization: A ‘Finished’ message is sent from both ends, cementing the handshake and establishing the encrypted session.
Data Encryption: The Cyber Vault
Post-handshake, you’ve essentially built a private, encrypted tunnel for data to travel through.
Encryption Mechanics:
- Both parties generate symmetric keys based on the exchanged values from the handshake.
- These keys are exclusive to each session, offering another layer of protection.
Popular Encryption Algorithms:
- AES (Advanced Encryption Standard)
- DES (Data Encryption Standard)
- RSA (Rivest–Shamir–Adleman)
- ECC (Elliptic Curve Cryptography)
The Assembly: Certificates, Handshake, Encryption
In summation, the certificate issuance preps the stage with verified digital IDs. The elaborate 7-step handshake establishes mutual trust, confirming that both IDs are authentic. Finally, data encryption acts as the impenetrable vault, securing the passage of information.
When these pieces come together, mTLS isn’t just a series of steps or algorithms; it’s a harmonized system where security is the cornerstone. In an age where cyber threats loom large, mTLS offers a sanctuary, a nearly invincible fortress for your digital interactions.
Setting Up mTLS: Your Roadmap to Unshakable Security
Getting mTLS up and running might look like a high-stakes game of Jenga, but it’s easier than you think. Let’s walk you through the setup, making this fortress of security a reality for your server.
Pre-requisites: The Tools of the Trade
Before diving in, gather your gear. Here’s what you need:
- A server with HTTPS support (Nginx, Apache, etc.)
- OpenSSL or a similar tool for certificate management
- Administrative access to the server
- Client devices or software capable of mTLS
Step 1: Generating Certificates – The ID Cards
Both the client and the server need their own digital certificates. These can be obtained from a Certificate Authority (CA) or generated in-house for testing purposes.
-
Server Side: Use OpenSSL to generate a self-signed certificate or obtain one from a CA.
<code>openssl req -x509 -newkey rsa:4096 -keyout server_key.pem -out server_cert.pem -days 365</code>
-
Client Side: Similar process but store this certificate on the client device/application.
<code>openssl req -x509 -newkey rsa:4096 -keyout client_key.pem -out client_cert.pem -days 365</code>
Step 2: Server Configuration – The Rulebook
Configuring your server to require mTLS is the next milestone.
-
Nginx: Add these lines to your configuration file.
<code>ssl_client_certificate /path/to/ca_cert.pem; ssl_verify_client on;</code>
-
Apache: Modify your
.conffile with these lines.<code>SSLCACertificateFile /path/to/ca_cert.pem SSLVerifyClient require</code>
Step 3: Client Configuration – VIP Pass
Installing the client certificate ensures it can partake in the mTLS handshake.
- For web browsers, import the client certificate through settings.
- For applications, embed the certificate within the app’s codebase.
Step 4: Testing – Dry Run
Before going live, run a thorough test to ensure both client and server can complete the mTLS handshake.
-
Execute a cURL command to mimic a client-server interaction.
<code>curl https://your-server.com --cert client_cert.pem --key client_key.pem</code>
-
Review logs and metrics to confirm that the mTLS handshake was successful.
Step 5: Go Live – Unleash the Beast
If your tests are all green, you’re ready to roll. Activate the server configurations and let the secure data flow!
To Sum It Up: Setup, Secure, Soar
Set up the certificates, tweak the server, configure the client, run a test, and you’re airborne. You’ve just established a high-security channel between client and server. Welcome to the sanctuary that is mTLS, where digital threats are left knocking on an unbreakable door.
mTLS in Action: Where This Security Powerhouse Reigns
mTLS isn’t just a buzzword; it’s a frontline warrior in several industries and systems. From healthcare to finance, it’s the unsung hero safeguarding critical data. Let’s unpack the realms where mTLS takes center stage.
Healthcare: The Shield of Patient Data
Handling sensitive health records requires more than just a password. mTLS ensures that both the data requester and the data provider are verified, offering a double lock on patient information.
- Telemedicine: Ensures secure video conferencing between doctors and patients.
- EHR Systems: Keeps electronic health records secure during transfers and updates.
Finance: The Vault of Transactions
Money talks, and it needs to do so securely. mTLS secures transactions and sensitive financial data across various platforms.
- Online Banking: When you’re moving funds or checking accounts, mTLS ensures it’s really you.
- Stock Trading Apps: Real-time trading demands real-time security.
IoT: The Gatekeeper of Devices
The Internet of Things is a sprawling network, and mTLS keeps it tightly knitted.
- Smart Homes: Think door locks, thermostat controls—all shielded.
- Industrial IoT: Machine-to-machine communication is secured, preventing unauthorized data sharing.
eCommerce: The Protector of Trust
Security breaches are bad for business, period. mTLS keeps customer data secure and trust intact.
- Payment Gateways: A double verification system for transactions.
- User Authentication: Securely logs in customers, protecting personal data and order history.
Government: The Guardian of National Data
When national security is on the line, mTLS is often in the background, acting as a guardian angel.
- Defense Systems: Ensures that commands and data are sent and received by authenticated entities.
- Public Records: Keeps citizen data secure, accessible only by authorized personnel.
Cloud Services: The Watchtower of Data
Cloud storage and computing services hold a treasure trove of data, making them a hot target for cyber threats. mTLS stands guard, ensuring only authorized access.
- Data Centers: Encryption and mutual verification protect against unauthorized data access.
- API Endpoints: Secure data exchange between different cloud services or components.
Think of mTLS as the multi-talented star player on a sports team. Whether it’s handling sensitive health records or locking down a smart home, it’s there, ensuring secure and verified interactions. In a world rife with cybersecurity threats, mTLS is more than a protocol; it’s your digital peace of mind.
Common Misconceptions about mTLS: Myths, Busted
Let’s clear the fog. mTLS is often misunderstood, and that’s partly because of myths and half-truths floating around. Time to pull the plug on these misconceptions.
Myth 1: mTLS is Overkill for Most Applications
Reality Check: mTLS isn’t an over-the-top, luxury suite of security; it’s a high-grade lock where a padlock won’t do. For applications dealing with sensitive data, it’s not overkill it’s a must.
Myth 2: Setting up mTLS is Complex and Time-Consuming
Reality Check: With the right guidance, setting up mTLS can be streamlined and manageable. Sure, it’s not a one-click solution, but the steps are straightforward. And the time invested pays off in robust security.
Myth 3: mTLS Slows Down Systems
Reality Check: While it’s true that encryption processes can add latency, modern hardware and efficient algorithms make this impact negligible. mTLS doesn’t mean you’re trading speed for security; you can have both.
Myth 4: mTLS and TLS Serve the Same Purpose
Reality Check: Think of mTLS as TLS on steroids. While both protocols secure data transfer, mTLS adds a layer by also verifying the client. It’s not just a fancier TLS; it’s TLS plus a bonus level of trust.
Myth 5: mTLS is Only for Web-Based Applications
Reality Check: Nope. mTLS is versatile. It’s used in IoT, internal microservices, mobile applications, and more. Wherever two-way verification is beneficial, mTLS can step in.
Myth 6: Using Self-Signed Certificates is Enough
Reality Check: Self-signed certificates can work for testing or internal setups but lack the validation that comes from a trusted Certificate Authority. For enterprise-level or public-facing applications, a CA-issued certificate is the gold standard.
Myth 7: mTLS is Cost-Prohibitive
Reality Check: The costs are variable. Open-source tools and self-signed certificates can be free. CA-issued certificates and hardware may involve investment, but that often pays for itself by preventing costly security breaches.
Myth 8: mTLS Makes Your System Unhackable
Reality Check: No system is 100% unhackable. While mTLS adds a strong layer of security, it’s not a magic bullet. Complement it with other security measures for a comprehensive defense.
Truth Serum: mTLS Clarified
The idea that mTLS is overly complex, or unnecessary, or slows down systems is plain and simple mythology. It’s a potent layer in a well-rounded cybersecurity strategy. So next time you hear someone doubting the efficacy or necessity of mTLS, hit them with the facts. Myths, consider yourselves busted.
Best Practices for Implementing mTLS: The Road Less Traveled, Now Made Easy
Implementing mTLS can feel like navigating a labyrinth without a map. Don’t sweat it; we’ve got the compass. Turn the daunting into the doable with these ironclad best practices.
Tactic 1: Start with a Risk Assessment Know Your Battlefield
The first step isn’t code; it’s comprehension. Conduct a risk assessment to figure out your security needs. Identify where data is most vulnerable and where mTLS can serve as your knight in shining armor.
Tactic 2: Use CA-Issued Certificates No Skimping on Credentials
Don’t opt for the easy way out with self-signed certificates unless you’re testing or in a closed environment.
- Good: Self-signed for testing.
- Better: CA-issued for production.
<code class="language-bash"># To request a CA-issued cert, typically: openssl req -new -key yourdomain.key -out yourdomain.csr</code>

Tactic 3: Version Matters Stay Updated
Using outdated TLS versions is like fighting dragons with a toothpick. Always opt for the latest version. Keep both your server and client configurations updated.
- Don’t: TLS 1.1 or below
- Do: TLS 1.2 or above
Tactic 4: Cipher Suites Choose Wisely
Select cipher suites that offer robust encryption without compromising on performance. AES-GCM and ECDHE are usually solid choices.
- Weak: RC4, DES
- Strong: AES-GCM, ECDHE
<code class="language-bash"># Example Nginx Config ssl_ciphers 'ECDHE-RSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-GCM-SHA384';</code>

Tactic 5: Monitor and Rotate Certificates — Vigilance Pays
Certificates aren’t forever. Monitor their expiration and set up automated processes for renewal and rotation.
<code class="language-bash"># To view certificate details: openssl x509 -in certificate.crt -text -noout</code>
Tactic 6: Implement Strong Authentication Policies No Weak Links
mTLS is about mutual trust. Apply strict authentication policies to ensure that only legitimate clients can connect. Be wary of wildcard or multi-domain certificates for critical applications.
Tactic 7: Test in Stages Baby Steps to Giant Leaps
Don’t go from zero to hero in one go. Test the mTLS setup in stages: start with a non-critical application, validate the setup, and then roll it out wider.
Tactic 8: Make Use of Monitoring Tools Your Security Radar
After mTLS is live, don’t kick back and relax. Use monitoring tools to keep tabs on certificate statuses, failed authentications, and overall system health.
Tactic 9: Maintain Documentation Your Playbook
Detailed documentation is your friend for future updates or audits. Document the entire mTLS implementation process, protocols used, certificate details, and any custom configurations.
Tactic 10: Two-Factor Authentication (2FA) Double Lock Your Vault
When possible, layer mTLS with two-factor authentication. A certificate verifies the device; 2FA verifies the user. It’s like a two-step handshake that’s twice as secure.
<code class="language-bash"># For example, integrating 2FA with SSH ssh -o "AuthenticationMethods publickey,keyboard-interactive" user@server</code>
Tactic 11: Set Alerts for Unusual Activity Early Warning System
Configuring alerts for abnormal patterns or multiple failed authentication attempts isn’t paranoid; it’s prudent. Early detection can thwart potential breaches.
<code class="language-bash"># Sample log alerting setup in a Linux system grep 'authentication failure' /var/log/auth.log | mail -s 'Alert' [email protected]</code>
Tactic 12: Optimize for Scalability Future-Proof Your Fortress
As your network grows, your mTLS setup should scale seamlessly. Opt for solutions that offer easy certificate management and allow for straightforward addition of new clients.
Tactic 13: Implement Rate Limiting Slow Down Invaders
Rate limiting controls the pace at which requests are processed. It’s like adding speed bumps on the road for potential invaders, buying you extra time to detect and counter threats.
<code class="language-bash"># Nginx rate limiting example limit_req_zone $binary_remote_addr zone=authlimit:10m rate=1r/s;</code>
Tactic 14: Periodic Security Audits — Check Your Armor
Don’t just set it and forget it. Regularly audit your mTLS configurations, review logs, and update security policies to align with emerging threats and compliance standards.
Tactic 15: Employee Training — Your First Line of Defense
All your mTLS efforts can be undone with a single click by an uninformed employee. Training isn’t just beneficial; it’s crucial. Make sure everyone understands the hows and whys of mTLS.
Final Notes: Continual Vigilance, Not Just a Setup
Remember, mTLS isn’t a one-time achievement; it’s a constant state of vigilance. Once you’ve set it up, it needs tending, fine-tuning, and periodic upgrades. But with these best practices in your pocket, you’re not just implementing mTLS—you’re mastering it. Keep this guide as your ongoing reference, and let mTLS do what it does best: unyielding, unwavering security.
FAQs about mTLS: Quickfire Answers to Your Burning Questions
Questions pop up. mTLS, after all, is a complex beast. But guess what? We’ve got straightforward answers. Let’s blast through the most common queries.
Q: Is mTLS the same as 2-way SSL?
A: Almost. mTLS is a type of two-way SSL, but it adds an extra layer by authenticating both client and server.
Q: Do I need a separate certificate for each client?
A: Not necessarily. You can use wildcard or multi-domain certs for multiple clients, but it’s less secure for critical applications.
Q: Is mTLS only useful for financial or healthcare sectors?
A: Nope. It’s versatile. IoT, e-commerce, internal microservices you name it, mTLS secures it.
Q: Does mTLS replace the need for firewalls or VPNs?
A: No. Think of mTLS as a specialized guard, while firewalls and VPNs are your general security forces. They work better together.
Q: How does mTLS affect API security?
A: It boosts it. mTLS verifies both ends of the data transfer, making API calls more secure.
Q: Can I implement mTLS on a mobile application?
A: Absolutely. Mobile or desktop, if it needs secure communication, mTLS fits the bill.
Q: Is mTLS foolproof?
A: No security measure is 100% foolproof, but mTLS gets you close by offering robust two-way authentication.
Conclusion: The Last Word on mTLS For Now
We’ve dug deep into mTLS from the basics to the nuances, from real-world applications to best practices, and even busted some myths. The aim? To make you as savvy about mTLS as possible.
Why? Because mTLS isn’t just an add-on; it’s an integral part of a robust security landscape. It’s the secret handshake that ensures the club is exclusive and secure. It’s the gatekeeper and the bouncer, all rolled into one.
So, implement it wisely, use it liberally, and question it constantly to ensure it’s living up to its full potential. With this guide, you’re not just an mTLS user; you’re an mTLS champion. Armed with knowledge, go forth and secure!
The post What Is mTLS? The Essential Guide You Can’t Afford to Miss appeared first on Wallarm.
*** This is a Security Bloggers Network syndicated blog from Wallarm authored by Ivanwallarm. Read the original post at: https://lab.wallarm.com/what-is-mtls-the-essential-guide-you-cant-afford-to-miss/
如有侵权请联系:admin#unsafe.sh
