Don't call it a comeback ... Ok, maybe it is
Has it really been four years since my last post!? Well I guess it has! So a better question is: "What has changed for me to bring this blog back?"
Well last February I got rid of my apartment, took leave of my job, and hiked all 2185.3 miles of the Appalachian Trail from Georgia to Maine. During that time I realized how much blogging meant to me. Long story short, I've been working with my employer to figure out how I could restart this blog now that I'm back.
I don't want to spend too much time on this news post but I might as well end it on one more question: "What should you expect?" That's up in the air right now and I plan on remaining flexible, but I feel one thing I have to contribute to the research community is the fact that I really do enjoy constructing and running experiments. I may not be the best coder, l33t3st password cracker, or have a million dollar cracking setup, but I do have mad Excel skills and I love digging into algorithms. Right now I'm investigating the new PRINCE tool from At0m, creator of Hashcat, (You can get it here) so hopefully I should have a post up about it in a couple of days.
 |
| Balance, I have it |

Popular posts from this blog
Tool Name: PRINCE (PRobability INfinite Chained Elements) Version Reviewed: 0.12 Author: Jens Steube, (Atom from Hashcat) OS Supported: Linux, Mac, and Windows Password Crackers Supported: It is a command line tool so it will work with any cracker that accepts input from stdin Blog Change History: 1/4/2015: Fixed some terminology after talking to Atom 1/4/2015: Removed a part in the Algorithm Design section that talked about a bug that has since been fixed in version 0.13 1/4/2015: Added an additional test with PRINCE and JtR Incremental after a dictionary attack 1/4/2015: Added a section for using PRINCE with oclHashcat Brief Description: PRINCE is a password guess generator and can be thought of as an advanced Combinator attack . Rather than taking as input two different dictionaries and then outputting all the possible two word combinations though, PRINCE only has one input dictionary and builds "chains" of combined words. These chains can have 1 to N wo

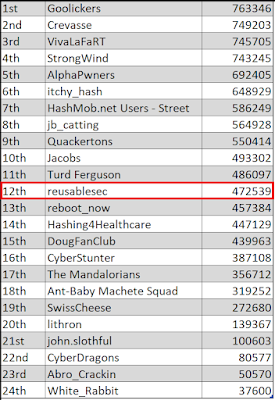
“We do not learn from experience... we learn from reflecting on experience.” -- John Dewey Introduction: KoreLogic's Crack Me if You Can (CMIYC) is one of the oldest as most established password cracking competitions. Held every year at Defcon, it serves as a great way to pull together password enthusiasts from all over the world and provides a shared use-case that drives password cracking tool development throughout the rest of the year. This year I competed as a street team and managed to finish in 12th place: Now that I've had a week to look back on things, there certainly are strategies where I could have done better. The first is with my cracking setup. I had two systems I used. My primary cracking system was still my laptop running an Ubuntu VM utilizing WSL on a Windows 11 install. My secondary system was the computer I described setting up in this blog post . Primary Laptop: CPU: i7-8640U CPU RAM: 16 GB Storage: 500GB SSD Desktop Computer: CPU: Intel i5-7600k, 1 p
But first, a quick responses to one of the previous comments, (since it really did merit a front-page post). Tfcx posted: The initial vulnerability was posted 29th November on a hacking forum called darkc0de here: http://forum.darkc0de.com/index.php?action=vthread&forum=11&topic=13082 Thanks, as that really helps narrow down the timeframe, (and reading that post and related posts was interesting if a bit depressing). The hack itself appears pretty straightforward once you see it, (like most things once the solution is presented to you it's easy, but finding it in the first place is hard). I'm still interested in the hacker Igigi, and have been tossing about all sorts of theories; but I'll refrain from posting them here since they are all pure WAGs right now. Now on to the main topic: Per Thorsheim wrote: I would like to see a comparison of Twitters 370 banned passwords against the top 370 or so passwords stolen from rockyou (http://www.techcrunch.com/2009/12/27/twi
文章来源: https://reusablesec.blogspot.com/2014/12/dont-call-it-comeback-ok-maybe-it-is.html
如有侵权请联系:admin#unsafe.sh



