2018-2-26 06:44:0 Author: bartblaze.blogspot.com(查看原文) 阅读量:5 收藏
In this blog post, we'll have a quick look at fake versions of Steam Desktop Authenticator (SDA), which is a "desktop implementation of Steam's mobile authenticator app".
Lava from SteamRep brought me to the attention of a fake version of SDA floating around, which may be attempting to steal your Steam credentials.
Indeed, there are some fake versions - we'll discuss two of them briefly.
Fake version #1
The first fake version can be found on steamdesktopauthenticator[.]com. Note that the site is live, and appears at the top of Google Search when searching for "Steam Desktop Authenticator".
| Figure 1 - Fake SDA website |
When downloading the ZIP file from the website, and unzipping it, we notice the exact same structure as you would when fetching the legitimate package - with one difference: the main executable has been modified.
File details:
Name: Steam Desktop Authenticator.exe
MD5 hash: 872abdc5cf5063098c87d30a8fcd8414
File size: 1,4446 KB
Version: v1.0.9.1
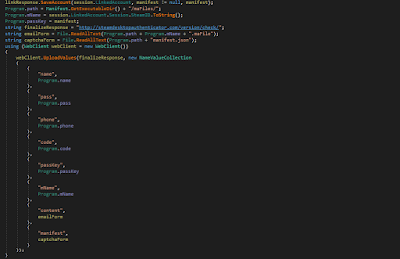
Note that the current and real SDA version is 1.0.8.1, and its original file size is 1,444 KB - 2 bytes of difference can mean a lot. Figures 2 and 3 below show the differences.
| Figure 2 - Sending credentials to steamdesktopauthenticator[.]com |
| Figure 3 - Sending credentials to steamdesktop[.]com |
Indeed, it appears it also attempts to upload to another website - while digging a bit further, we can also observe an email address associated with the domains: mark.korolev.1990@bk[.]ru
While I was unable to immediately find a malicious fork with any of these domains, Mark has likely forked the original repository, made the changes - then deleted the fork. Another possibility is that the source was downloaded, and simply modified. However, it is more than likely the former option.
Fake version #2
This fake version was discovered while attempting to locate Mark's fork from the fake version above - here, we have indeed a malicious fork from GitHub, where trades/market actions appear to be intercepted, as shown in Figure 4 below.
| Figure 4 - Malicious SDA fork (click to enhance) |
Currently, when trying to access the malicious site lightalex[.]ru with a bogus token, a simple "OK" is returned - it is currently unknown whether market modifications would be successful.
Interestingly enough, when digging deeper on this particular domain, which is currently hosted on 91.227.16[.]31, it had hosted other SteamStealer malware before, for example cs-strike[.]ru and csgo-knives[.]net.
The malicious fork has been reported to GitHub.
Disinfection
Neither fake SDA versions reported here appear to implement any persistence, in other words; remove the fake version by deleting it, and perform a scan with your current antivirus and a scan with another, online antivirus, or with Malwarebytes for example.
Additionally, de-authorize all other devices by clicking here and select "Deauthorize all other devices".
Now, change your password for Steam, and enable Steam Guard if you have not yet done so.
Prevention
Prevention advise is the usual, extended advise is provided in a previous blog post here.
You may also want to take a look at SteamRep's Safe Trading Practices here.
Always download any software from the original source - this means the vendor's website, or in this case, the official SDA repository on GitHub:
https://github.com/Jessecar96/SteamDesktopAuthenticator
Conclusion
SteamStealer malware is alive and well, as seen from my January blog post. This is again another form of attempting to scam users, and variations will continue to emerge.
Follow the prevention tips above or here to stay safe.
Indicators
如有侵权请联系:admin#unsafe.sh