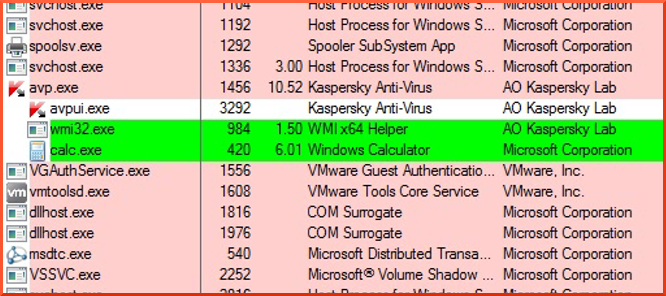
I had the pleasure to present my research about the IPC mechanisms of Kaspersky products at the IV. EuskalHack conference this weekend. My main motivation for this research was to further explore the attack surface hidden behind the self-defense mechanisms of endpoint security software, and I ended up with a local privilege escalation exploit that could be combined with an older self-defense bypass to make it work on default installations. I hope that the published information helps other curious people to dig even deeper and find more interesting pieces of code.
The presentation and some code examples are available on GitHub.
My local privilege-escalation exploit demo can be watched here:
The exploit code will be released at a later time on GitHub, so you can have some fun reconstructing it based on the slides ;)
