Carders.cc - General Observations and Updates - Part 3
Digging into this data is like watching an episode of Lost. Whenever it seems like one question gets answered, about ten other questions pop up.
Before I get into details, I want to start with a comment Per Thorsheim sent me as to what other password cracking programs support salted sha1 hashes:
The sha1(lowercase_username.password_guess) is at least supported by these:
Extreme GPU Bruteforcer (www.insidepro.com) hashcat and oclhashcat (cpu/gpu respectively) www.hashcat.net
I'm kicking myself for not thinking about hashcat, since it's a extremely powerful password cracker; plus it's free. Unfortunately the GPU version doesn't support the salted sha1 hash type, but even the non-gpu version is quite nice.
As for InsidePro, it also is very good, though it does cost some money. I've had a license-free version of questionable origin offered to me before, but I turned that down. Legality aside, installing pirated software given to you by shady people at a hacker conference would just be stupid...
Also, I've been talking to Ron Bowes over at the excellent skullsecurity blog, and he and some other people are hard at work cracking the passwords. It sounds like they have some serious hardware behind the effort, so expect to see something posted on his site about that in the near future.
OK, now onto the analysis:
First of all, I'm downgrading my opinion of the skill showed by the hackers in their password cracking attack. What I didn't realize before was the extent that the users of carders.cc had been compromised previously. Just about all of the non-trivial passwords that were cracked appear in publicly available input dictionaries which are based on passwords cracked from user submitted hashes - aka hashkiller, insidepro, etc. Please note, I'm not saying they were script kiddies. The attackers were able to target the salted sha1 hash, and they knew where to get some good input dictionaries. It's just that they are not some uber-l33t password crackers, and anyone else using those input dictionaries could crack the same number of passwords in a couple of hours.
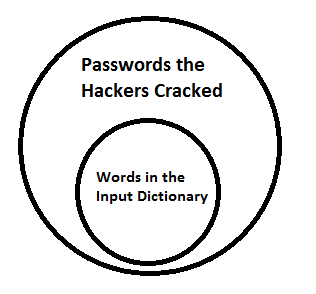
What this also means is we might be able to figure out which input dictionaries the attackers were using by looking at the hashes they cracked, vs. what the input dictionary would crack. To demonstrate this, below is a Venn diagram of what an input dictionary the attackers used would look like:

For example, there is a good chance the attackers used the InsidePro Big dictionary, since it cracks the same 598 passwords from the carders.cc list that the attackers cracked. Add in a couple of the other publicly available input dictionaries, and you get real close to the 920 total passwords they managed to crack. To put this in perspective, I've so far managed to crack 62%, (compared to the 53% that the hackers cracked), of the salted Sha1 passwords on my laptop using basic dictionaries with almost no mangling rules. I fully expect other people to blow past that mark.
Next up, initial thoughts about the carders.cc database:
What I really need to do is load all of the tables into my own database so I can do quick SQL queries, vs. manually going through the data by hand. That being said there are a few things that stick out:
- There's a lot of userids/password hashes in the carders_smf_members table that did not appear in the write-up.
- The MD5 hash is salted, but at least the salt is also available in the carders_smf_members table. The hash itself is a vBulletin3 hash type, MD5(MD5(Password).Salt). Both John the Ripper and Hashcat support this hash type.
- I'm not sure if the IP addresses stored in the table are accurate or not, since it looks like the site admins tried to obscure it in the webserver logs, but if they are, the database stores the last two ip addresses used.
- Other interesting fields include date joined, number of posts, karma level, last login date, etc.
- The above doesn't even begin to get into all of the data contained in the actual posts themselves...
That about it for this update. Let me leave you with one last fact that Ron found out:
Another interesting factoid:
Last MD5 password: 2010-01-10 21:54:01
First SHA1 password: 2010-01-10 22:40:16
So it was on January 10, 2010, later in the evening (in CDT) that they upgraded from vBulletin 3 to SMF.
*shrug* the more you know!