2017-10-15 01:50:0 Author: bartblaze.blogspot.com(查看原文) 阅读量:3 收藏
Sage, also known as SageCrypt, is an interesting ransomware variant - emerged somewhere in December last year, and is believed to be a variant of the CryLocker ransomware.
There's a good blog post on BleepingComputer on the first version of Sage, id est "Sage 2".
Yesterday, a personal friend of mine reached out, as his "computer started talking" and his files appeared to be encrypted. And indeed, it appears he suffered the latest variant of Sage: Sage 2.2
Sage 2.2 appears to have been out for a while, at least since February of this year:
— MalwareHunterTeam (@malwrhunterteam) February 21, 2017
Some figures of Sage 2.2 follow below:
 |
| Figure 1 - Sage 2.2 desktop background |
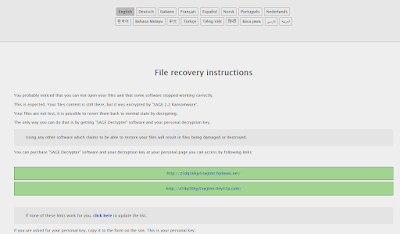
| Figure 2 - Sage 2.2 file recovery instructions |
The message reads:
You probably noticed that you can not open your files and that some software stopped working correctly.
This is expected. Your files content is still there, but it was encrypted by "SAGE 2.2 Ransomware".
Your files are not lost, it is possible to revert them back to normal state by decrypting.
The only way you can do that is by getting "SAGE Decrypter" software and your personal decryption key.
Typical features of Sage 2.2, include, but are not limited to:
- Refresh or update of payment pages is possible;
- Ransom note (!HELP_SOS) and portal, including CAPTCHA;
And...
It speaks! Just like Cerber did at some point, Sage 2.2 has a message for the victim using Microsoft SAPI:
| Figure 3 - VBscript which will speak to the victim (click to enlarge) |
Interestingly enough, even though the version number still indicates 2.2, there's at least one slight change:
- Deletion or purge of backup catalog/history by using:
wbadmin delete catalog -quiet
The portal or decryption pages look as follows, stepping through:
| Figure 4 - Sage 2.2 user login portal |
| Figure 5 - Captcha |
| Figure 6 - Language selection |
| Figure 7 - Final portal |
The victim can choose from a multitude of languages, and, at the final portal, there is a special price for the decryption, for a selected time (7 days): currently 0.17720 BTC, which is about $1000.
As usual, there's a Payment, Test decryption, Instructions, and even a Support tab:
| Figure 8 - Payment tab |
| Figure 9 - Test Decryption tab |
| Figure 10 - Instructions tab |
| Figure 11 - Support requests tab |
Sage 2.2 will append the .sage extension to encrypted files and currently, it does not appear files can be decrypted without the cybercriminal's help.
As always, try to restore from a backup if possible, and avoid paying the ransom.
Additionally, have a look at my ransomware prevention page, on how to protect yourself.
IOCs
如有侵权请联系:admin#unsafe.sh