2022-6-2 04:0:0 Author: bishopfox.com(查看原文) 阅读量:13 收藏
In our most recent Tool Talk, we featured ripgen, a super-fast tool for conducting subdomain discovery. Justin Rhinehart, Senior Analyst, joined Joe Sechman, AVP of R&D, to discuss the importance of subdomain discovery in security testing, the low-down on ripgen, and real-world examples highlighting ripgen’s attributes. Subdomain discovery is one of the first important steps for attack surface discovery and we are excited to share why our Cosmos team loves using ripgen to accomplish this.
Subdomain Discovery – How Vital Is It to Security Testing?
With 67% of our Tool Talk participants considering it critically important, it’s clear that subdomain discovery plays a vital role in security testing. But what is it exactly and why is it important? As the name implies, subdomain discovery is the process of discovering subdomains of any given domain. As to why it’s important, the answer mainly lies in the way some subdomains are used.
Subdomains are intended to direct users to other services or applications of a higher-level domain, i.e., https://blog.brand.com point users to the blog within the ‘Brand’ domain. Sometimes, there are several variations of the same service and each one is represented by a subdomain. In some instances, however, some subdomains serve as staging environments for testing purposes.
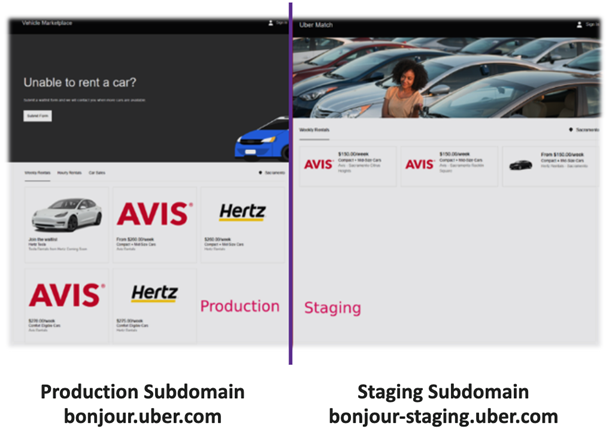
In our example below, the one on the left is a production subdomain, while the one on the right is a staging subdomain.

Because staging subdomains aren’t meant for public consumption, the people who use them, presumably software/web developers, sometimes fail to apply stringent security measures or remove when no longer in use. For example, many subdomains used for staging readily accept admin/admin login credentials as well as other widely known credential pairs. These weak credentials can be quite trivial for threat actors to guess or brute force and gain unauthorized access.
Worse, a staging environment may be connected to a backend that is attached to a staging database. Although called a ‘staging database’, the data contained in that database might very well be a snapshot from production, so developers have access to representative data for testing.
Note: Insecure subdomains don’t need to have the word ‘staging’ in them. Some organizations use the word ‘dev’ or ‘development’ or ‘qa’, and so on. It really depends on the vernacular or language the organization chooses to adopt. In fact, some aren’t necessarily staging environments.
The bottom line is that unknown subdomains can be highly vulnerable. The goal of subdomain discovery is to discover them, so you can see the full scope of the potential attack surface of your domain.
As practitioners of offensive security, our objective is to discover these subdomains before the bad guys do. That’s where ripgen comes into play.
The Basics
Ripgen is a tool that takes a list of subdomains, divides them into individual words, and then generates several more subdomain permutation possibilities based on information found on that list. The tool eliminates the guesswork by using only the few bits of information that you know and the target organization’s established naming conventions.
This is substantially helpful in subdomain discovery, especially if you’re working from a zero-knowledge perspective and don’t have any definitive source of truth for subdomains (like a zone file).
What ripgen does is by no means a new technique. It’s based on the concept of subdomain permutations, which is already being applied by several other tools. However, the amount of subdomain permutations it generates and the speed in which it does it – makes it a winner in our books.
ripgen in Action
Saying that ripgen generates ‘several more subdomain permutations’ is actually an understatement. In one real-world example, subfinder, a generic tool for finding subdomains, managed to find 369 domains. When those results were piped into ripgen, it created a wordlist of 843,000 potential subdomains.
It’s not just the number of permutations that makes ripgen a handy tool for subdomain discovery. ripgen is a rust-based version of dnsgen (an older, more popular subdomain discovery tool that’s written in python). Because ripgen is written in rust, it’s much faster. A wordlist that might take 5 minutes for dnsgen to generate can probably be done in 10-30 seconds using ripgen.
As one of our favorite tools, ripgen speeds up the discovery process, which is huge from an offensive security standpoint, where our consultants must outpace advanced, modern adversaries.
In one test, our Cosmos Team discovered a staging version of a target that had admin API keys hardcoded in the actual source code of the site that weren’t in the production version. The staging environment also had several other functionalities that weren’t intended to be made public. If these flaws had been discovered by a threat actor, the site could have been critically compromised.
Sometimes, the subdomains we discover through ripgen even surprise our customers. When that happens, we get remarks like, “Oh, we didn’t even know this was a thing.”
ripgen works best when you feed it words you know the target uses. Doing so allows it to fine tune its permutations. Also, because hundreds of thousands of results can be quite overwhelming, our consultants may also tweak ripgen to keep results under 1,000 subdomains.
Final Words
Subdomain exploitation will continue to provide low hanging fruit for threat actors to take advantage of; however, there are a few best practices that organizations can follow to quickly improve subdomain hygiene. Proper accounting, attribution of ownership and tracking the purpose of domains can go a long way towards reducing risks of your attack surface. With a bit more focus, security teams can avoid the problem of hidden and unknown subdomains that leave attack surfaces unnecessarily vulnerable.
To learn more about subdomain discovery, check out the ripgen episode of our Tool Talk series.
Subscribe to Bishop Fox's Security Blog
Be first to learn about latest tools, advisories, and findings.
如有侵权请联系:admin#unsafe.sh