Endpoint security products provide an attractive target for attackers because of their widespread use and high-privileged access to system resources. Researchers have already demonstrated the risks of complex input parsing with unmanaged code and even sloppy implementation of client- and server-side components of these products. While these attacks are still relevant, it is still generally overlooked how security software breaches some important security boundaries of the operating system. In this research we first present a generic self-defense bypass technique that allows deactivation of multiple endpoint security products. Then we demonstrate that self-defense can hide exploitable attack surface by exploiting local privilege escalation vulnerabilities in 6 products of 3 different vendors. You can download our whitepaper here:
Bare-Knuckled Antivirus Breaking (PDF)
The following part of this blog post contains demonstration videos and some additional notes about the exploits described in the paper. We will also use this post to publish up-to-date information about affected vendors and fixes.
In the middle of 2017 we started looking into COM hijacking as a generic technique for defeating the self-defense features of endpoint protection products. These features are meant to prevent interference with the processes of security products in order to prevent unauthorized users and malware from deactivating protections, hiding activities, etc. Although COM hijacking is known for a really long time, all products that we tested were affected by this bypass method.
Our first successful demonstration for self-defense bypass was against Kaspkersy products. The following video shows the technique against the free version of their endpoint security software (Kaspersky Free Antivirus), but it also can be used in the same fashion against Internet Security, Antivirus and Endpoint Security:
As we can see, after self-defense was bypassed, the application accepts any password for accessing sensitive settings.
In this early version of the attack we rebooted the test machine to make sure that cached COM registrations won’t interfere (you can skip to 01:45), but this is not required in practice. Also, sorry about the glitches, recordmydesktop still can’t produce decent .ogv files…
While we wouldn’t consider self-defense as a security boundary (or their bypasses as vulnerabilities), some vendors may see them as such. Based on this thought we started to examine the features exposed after self-defense was bypassed. As it turned out, features related to the generally available “quarantine” functionality may provide us with powerful file access primitives. This idea was independently published by Florian Bogner in November 2017 under the AVGater “brand”. One of our additions to Florian’s result is that quarantine restoration may be exploitable even if its use is prohibited by application policy: since in many cases permission checks are only performed by a user-level process, an attacker can bypass them after self-defense is bypassed (this can be seen as the local IPC equivalent of client-side security checks).
The following video shows our exploit against Bitdefender Antivirus Plus:
The sliding switches on the quarantined UI should only be active for administrative users, we unlock them from inside the process with the self-defense bypass payload. After this the AVGater technique can be used for privilege escalation: in this case overwriting the service DLL of the Bitlocker Drive Encryption Service.
In case of Gravityzone – the cloud-based product of Bitdefender – the quarantine restore feature can be exploited trivially:
From Symantec we tested the Norton Security Deluxe and Symantec Endpoint Protection products. Both of these could be exploited for privilege escalation after self-defense was bypassed:
The colliding AVGater research allowed us to observe how different vendors respond to public vulnerability disclosures that not mention them explicitly:
- The recording of Bitdefender Gravityzone was made on 27th November, 17 days after the AVGater research became public. Although Bitdefender updated some of the relevant code, Gravityzone and Antivirus 2018 products are still vulnerable as of 30th December 2017.
- Although Kaspersky was shown with a logo in the AVGater publication, no detailed information was published about the affected products. According to our tests, all Kaspersky home products were vulnerable until December 2017 (fixed either by Patch E or F).
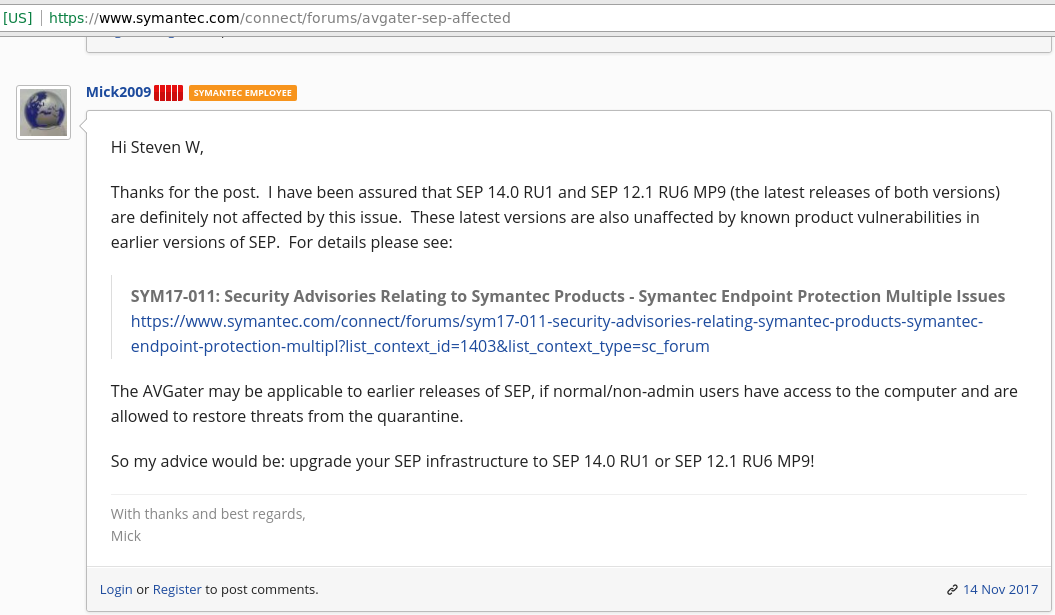
- Contrary to Symantec’s statement, we could successfully demonstrate the vulnerability against SEP 14.0 RU1. This may be because the vendor considered function-level controls of the application to be sufficient to workaround the problem.
</figure>
Proof-of-concept code is available on our GitHub.
Update 2018.06.13.
We haven’t seen security advisories from Symantec that would clarify the situation regarding the described issues. SYMSA1418 only covers issues prior to Symantec Endpoint Protection 12.1 RU6 MP9 and 14 RU1, while the described issues also affected former versions of 14 RU1 (as shown in the demo video above, BID101502 and BID101504 list all affected versions ). However, our technical tests showed that recent versions of SEP perform Impersonation when restoring files from the quarantine, that mitigates the demonstrated, quarantine based attack vector.
Bitdefender Total Security is still affected by the vulnerabilities and can be exploited:
The latest Total Security product doesn’t show any significant improvements regarding self-defense or the quarantine restoration process. The only difference we observed was that the directory browser window doesn’t let users manually provide the destination path for quarantine restoration:

Since Bitdefender doesn’t seem to release security advisories, we couldn’t determine if this was an actual attempt to fix the issues. We demonstrated exploitability by using directory junctions, and triggered our payload using the universal elevation of privilege technique described by James Forshaw.
UPDATE 2018.11.28.
Clement Lavoillotte‘s great GreHack’18 presentation “Abusing Privileged File Manipulation” includes some of the vulnerabilities and techniques described here, as well as additional interesting exploitation techniques. It seems that CVE-2018-5236 is a collision with the Symantec issue discussed above.