
Analyzing MIME Files: a Quick Tip, (Sun, Oct 1st)
2023-10-1 15:51:42 Author: isc.sans.edu(查看原文) 阅读量:15 收藏
2023-10-1 15:51:42 Author: isc.sans.edu(查看原文) 阅读量:15 收藏
In my blog post "Quickpost: Analysis of PDF/ActiveMime Polyglot Maldocs" I explain how to search through MIME files with my tool emldump.py to find suspicious/malicious content:
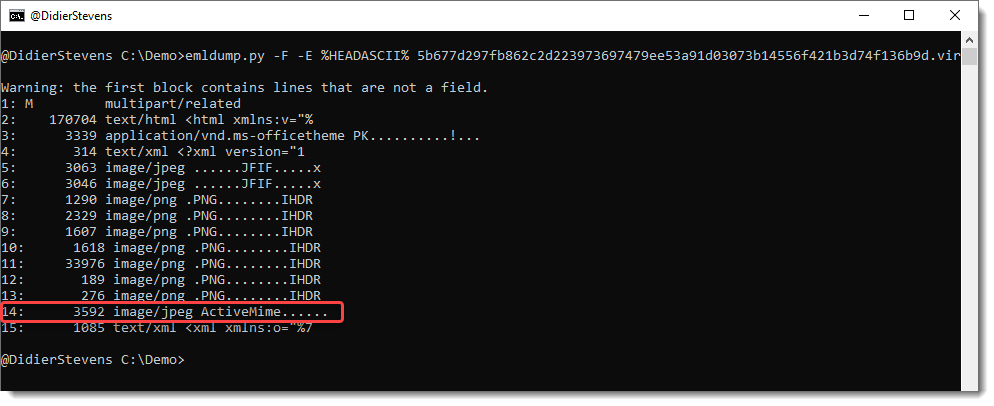
I have now released a new version of emldump.py, that can output the content of all parts in JSON format.
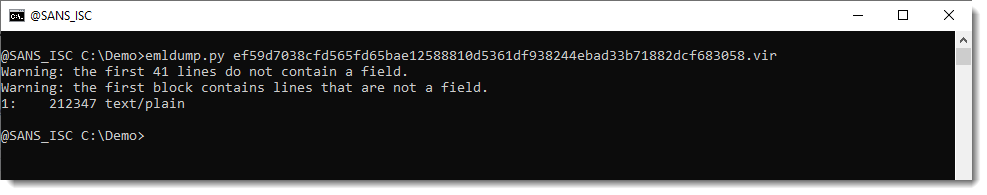
This is done with option --jsonoutput:
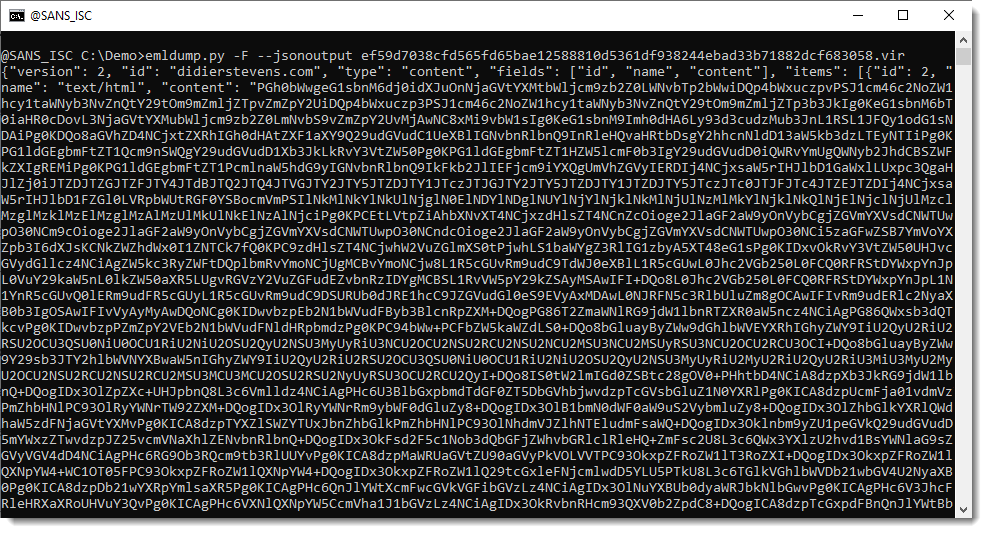
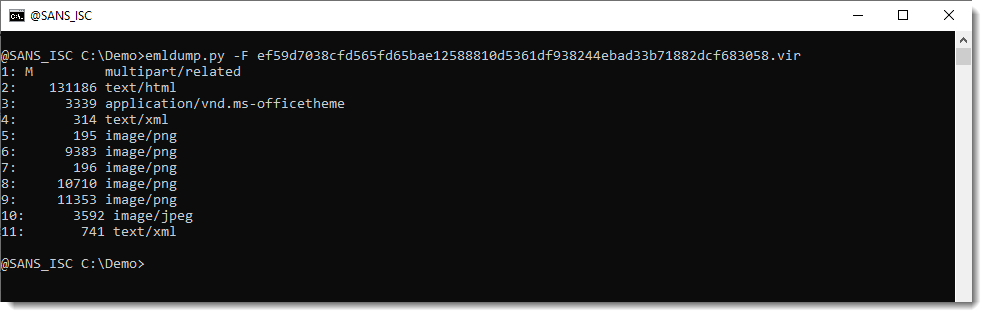
This JSON output can then be consumed by different tools I develop. One of them is file-magic.py, a tool to identify files using the libmagic library.
Here file-magic.py identifies all parts of the MIME file:
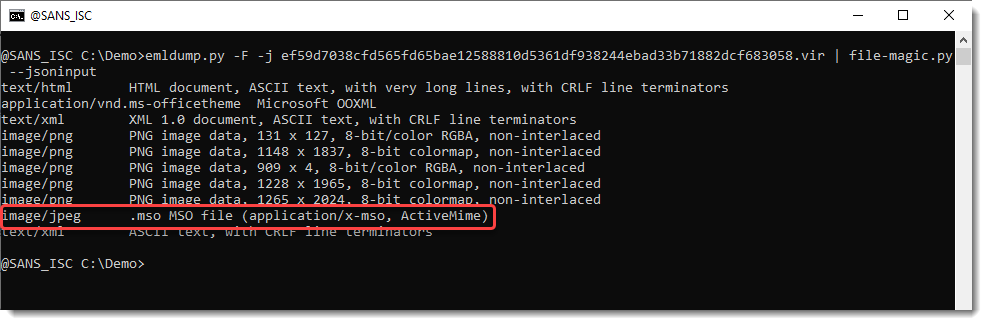
And it becomes clear that the JPEG parts is not actually an image, but an MSO/ActiveMime file that can contain VBA code.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com
文章来源: https://isc.sans.edu/diary/rss/30266
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh