Intro
In this blog post, I’ll demonstrate why XMPP is of interest to penetration testers, security researchers, and defenders. Misconfigured XMPP servers are an excellent way to retrieve sensitive data (such as employee and customer usernames, internal chat logs, or Pub/Sub data) from a company, establish a foothold in their infrastructure, and inform further attacks. A simple Shodan search returns hundreds of thousands of internet-facing XMPP servers alone, indicating its continued popularity.
The eXtensible Messaging and Presence Protocol (XMPP), also known as Jabber, is an application-layer protocol with instant messaging at the core of its functionality. As the name suggests, the protocol is designed to be extensible. Since development began in 1999, support has been added for features such as chatrooms, publish-subscribe, voice, video, and more. This extensibility has led to wide adoption of XMPP both as a simple chat platform and as a foundation for more full-featured products such as teleconferencing systems. Many organizations may be using and exposing misconfigured XMPP services without even realizing it.
XMPP is used in just about every industry you can imagine. During penetration testing engagements at Bishop Fox, sensitive data has been recovered from XMPP servers used by medical offices, heavy industry, manufacturing, financial services, dating apps, technology companies, satellite telecom, and more. As mentioned above, XMPP was generally used in two ways by most organizations:
- Chat server - Using XMPP in its standard manner, such as instant messaging among a company’s employees
- XMPP as an underlying technology - Building an application or service that integrates the XMPP protocol, such as a dating or other mobile app that uses XMPP to support chat and buddy lists between users. Two popular examples of this are the now-deprecated Google Talk and Facebook Chat.
XMPP Extensions
The following sections detail the various XMPP Extension Protocols (XEPs) that are interesting for penetration testers. XEPs provide additional features on a Jabber server, such as Multi-User Chat (chatrooms), the ability to exchange vCards, VoIP, and much more. Hundreds of XEPs have been published over the years, providing a variety of functionality that may be of interest from a security perspective.
Registration
XMPP servers optionally support registration (typically via XEP-0077: In-Band Registration) for new users or anonymous authentication. While some XMPP servers are intended to be public, many are misconfigured to allow for registration or anonymous authentication. This is true for both standard XMPP servers and when XMPP is used as the underlying protocol in a larger product. The vulnerabilities detailed in this blog post basically stem from this misconfiguration: a private XMPP server that supports registration or anonymous authentication.
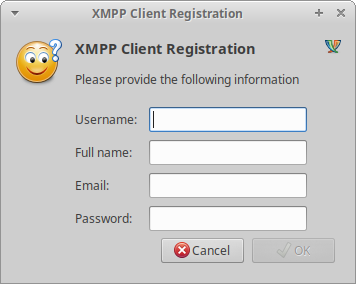
For example, the screenshot below shows an in-band registration on an XMPP server using Pidgin. Although this XMPP service was used for a company’s internal communications, the server was internet-facing and configured to allow registration.

Upon registering, attackers can make further use of XMPP features and extensions supported by the server.
Roster
Many XMPP servers are configured to provide a default roster (buddy list) upon login, especially in corporate environments. In some cases, they provide immediate insight into company staff and structure, information that could be valuable to the penetration tester. The screenshot below demonstrates a default roster from a company which includes the full name, title, and username of 217 employees. This data could be used to inform further attacks, such as targeting a specific department, impersonating another employee, or leveraging the usernames for password-spraying attacks. I have previously observed default rosters on corporate XMPP servers that revealed full company structures.

This data and its value is similar to what’s retrieved using the Jabber Search functionality discussed below. It is still worth mentioning, as some servers will provide a default roster without supporting Jabber Search and vice versa.
Service Discovery
XEP-0030: Service Discovery provides a means to query an XMPP server for its supported XEPs. The screenshot below shows the result of a service discovery request in Pidgin.

An attacker may then investigate each service supported by the server.
Jabber Search
XEP-0055: Jabber Search can provide a treasure trove of information for attackers about an organization. Below is an example of using the search functionality in Pidgin, demonstrating how you can search against several fields:
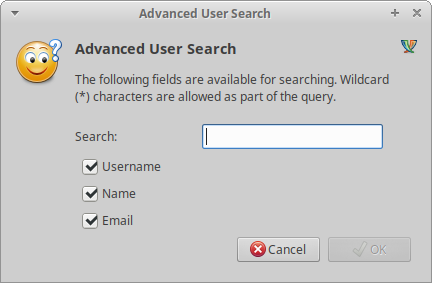
Fortunately, Jabber supports wildcard search, allowing for easy retrieval of all results. I have observed two particularly interesting trends:
- XMPP integrated with Directory Services: Many XMPP servers support authentication via the standard XMPP mechanism and via Directory Services. This allows for registration via the standard mechanism while retrieving information on users who use other authentication methods such as LDAP. When configured in this manner, querying the XMPP search feature returns details on every user in the organization, often including real names, usernames, and email addresses. I’ve observed XMPP servers returning thousands of directory users, resulting in extremely valuable lists of usernames comprising entire organizations. These lists of usernames could be used for password-spraying attacks against email or other services used by the organization, phishing campaigns, and more.
- Customer Information: As stated previously, XMPP is used under the hood of many applications. This frequently results in every user of the application having an account on the XMPP server via one authentication mechanism or another. This means that calling Jabber search returns a list of every user or customer of the application. In some contexts, the usernames themselves were sensitive information. Examples include medical applications where Jabber usernames are lists of patients, or services where a list of customers would be beneficial information to a competitor.
To me, the potential for password-spraying attacks is the biggest benefit of the Jabber Search feature. For those organizations who are leaking thousands of Directory Services usernames via their Jabber service, the chances of at least one user with “Winter2021” as a password is high, and most organizations have several external-facing services such as email, VPN, SSH, RDP, etc. to brute-force. A misconfigured Jabber server could well be the first step to a larger breach of a target organization. Of course, the potential for password spraying is the same when simply attacking the users of an application that has leaked its user list via Jabber.
Highlights seen on engagements from the Jabber Search feature:
- An internet-facing teleconferencing system which both integrated with Directory Services and used XMPP as an underlying protocol, leaking over 600 domain usernames
- A satellite communications solution leaking its entire customer list
- A medical application that leaked patients’ real names
- A mobile payment application that leaked usernames
Multi-User Chat (MUC)
XEP-0045: Multi-User Chat provides chatroom features over XMPP. This is where things get really interesting from a security perspective due to the sensitive nature of information shared over internal company chats and more. MUC is similar to chatrooms over other protocols like IRC, supporting functionality such as room discovery, private rooms, room topics, and so forth. Another very useful feature for the penetration tester is discussion history. XMPP MUC can be configured to allow for retrieval of the chatroom’s discussion history once a user joins. This means that an attacker only needs to join an MUC room for a moment to recover this chat history, instead of waiting for people to talk.
Highlights seen on engagements from the Multi-User Chat feature:
- Technology companies chatting about technical details such as internal web applications/hostnames and sharing Google Doc links
- A medical office discussing patient names, conditions, and treatments
Publish-Subscribe
XEP-0060: Publish-Subscribe provides Pub/Sub functionality over XMPP. As you might expect, this extension is almost always used when integrating XMPP with a larger product that requires a message brokering service.
While this feature is less commonly used in my experience, it is still worth remembering on an engagement.
Highlights seen on engagements from the Pub/Sub feature:
- A business ISP exposing customer usernames and phone numbers via Pub/Sub
- An education technology company that used the Pub/Sub service for several of their products. The Pub/Sub service delivered messages containing student-teacher communications including text and photos.
Analyzing XMPP Servers at Internet Scale
After realizing the value that misconfigured XMPP servers could provide to a penetration tester, I wondered how prevalent this issue might be on the internet. I used the Slixmpp library to write a Python script that would accept a list of IP addresses, attempt to determine if registration or anonymous authentication was supported by the XMPP server, then write the results to an SQLite database.
Shodan made it simple to acquire hundreds of thousands of IP addresses hosting an XMPP server. Although it would be possible to scan all ~300,000 XMPP servers found on Shodan, I only scanned a subset of this data. No doubt there are still many other misconfigured XMPP servers out there, such as on non-standard ports.
At the time of writing this blog post, I scanned a total of 70,226 XMPP servers from Shodan. This resulted in the following breakdown:
- 7% (4912) of XMPP servers supported registration
- 3.4% (2401) of XMPP servers supported anonymous authentication
Without authenticating to any of the XMPP servers found on Shodan, my experiences with misconfigured XMPP servers on client engagements would strongly suggest that some of these internet-facing servers are vulnerable to leaking sensitive data.
Conclusion
As demonstrated by the figures above, although misconfigured XMPP servers are not the most common service you may encounter during a penetration test, they can provide a big payoff if you do. In addition, there are certainly more XEPs out there that could leak sensitive data other than the ones mentioned above. There are 165 active, stable, or proposed XEPs listed on the official XMPP website, not to mention all the custom XEPs used inside various organizations.
If you’re performing a penetration test, include XMPP in the list of services you review for misconfigurations. From a defensive perspective, I would recommend looking for any XMPP services exposed by your organization or integrated with your applications, especially in any teleconferencing or messaging solutions. Ensure that they do not allow registration or anonymous authentication as appropriate and disable any unnecessary XMPP extensions.
Subscribe to Bishop Fox's Security Blog
Be first to learn about latest tools, advisories, and findings.
如有侵权请联系:admin#unsafe.sh