Jan 1, 2000
8 min read
Translate
Any typos? Any idea to suggest? Feedback appreciated!
- Stream @ twitch.tv/thelaluka
- Replays @ youtube.com/@TheLaluka
- Alerts @ twitter.com/TheLaluka
- Community @ discord/ThinkLoveShare // Still in early work 😇
Past Streams
- S01-E45-FR | Technology Watch August & PoC of RTX - part 2
- Keywords: Frycos, FortiNAC, ProjectDiscovery, Adobe ColdFusion, RCE (Remote Code Execution), StackOverflow, Prefix, Reference types, Bytecode, Datadog, DASH 2023, New Feature, Identity risks, Infrastructure vulnerabilities, Bugra.ninja, CloudShell, Command Injection, Espanso, Hyprland, Installation, Jdxcode, RTX, Features
- Guests: @Fransosiche
- S01-E44-FR | Technology Watch August & PoC of RTX - part 1
- Keywords: ArsTechnica, Hackers, Cryptographic keys, Video recording, Power LEDs, HashiCorp, Business Source License, Google Cloud, VRP Awards, Sec-Consult, DNS Analyzer, DNS Vulnerabilities, Burp Suite, CVE-2023-24068, CVE-2023-24069, YesWeHack, Black Box Testing, Web Application, Devco.re, Google Search Appliance, Podcast, Esoteric Web Vulnerabilities, Semgrep, Supply Chain, IETF, RFC9420, Qualys, OpenSSH, RCE, Hackndo, Keytap3, File Format Commons, Securinets Quals, Cookieless Duodrop, IIS Auth Bypass, App Pool Privesc, ASP.NET Framework, CVE-2023-36899, Redteamrecipe, Container Attacks, Allabtai, GPT-3, Text Summarization
- Guests: @Fransosiche
- S01-E43-FR | Technology Watch Jully
- Keywords: Ghostccamm, Strapi, Vulnerabilities, TheRegister, Windows XP, Activation cracked, Cruftbox, Metaverse, Warlord, Jsoncrack, Binary-offensive, Infection Chains, Vcluster, Virtual Clusters, ADCSKiller, Chameleon, Psycrypto, Contest, 12factor, Unicode, Confusables, Kuenzi, Toothbrush, Libcurl-crlf, Socket, Safe NPM, GoSecure, AWS WAF, SQL injection, MSSQL, Phind, React-admin, JSON server, CNIL, Data transfers, European Commission, Troy Hunt, Have I Been Pwned, Domain searches, RayanleCat, Workshop, CME, Lehack, GPT Engineer, Smol-ai, Developer, MetaGPT, Ragnar, Cococry, CLIG, Samwitteveenai
- Guests: None
- S01-E42-FR | Stranger Stream x Stranger Case part 2⁄2
- Abstract: The final episode of our collaboration with Stranger Case, delving deeper into the enigmatic mysteries and underlying themes.
- Guests: @Stranger_Case, @esnabretagne
- S01-E41-FR | Stranger Stream x Stranger Case part 1⁄2
- Abstract: An in-depth analysis of the Stranger Case CTF series in collaboration with the creators and the ESNA school director, examining plot details, character development, and production secrets.
- Guests: @Stranger_Case, @esnabretagne
- S01-E40-FR | Pwning Libre Office - CVE-2023-2255, Macro Holes & Macro Shells
- Abstract: An exploration of a critical vulnerability in LibreOffice (CVE-2023-2255) that allows for remote code execution and SSRF using macro scripts.
- Guests: @Icare1337
- S01-E39-FR | Patching xDebug with ChatGPT, Hooking specific PHP functions
- Abstract: Detailed session on the usage of ChatGPT in patching xDebug, focusing on hooking specific PHP functions to inspect them, finding bugs and improving software security.
- Guests: @Icare1337
- S01-E38-FR | Google DistroLess 101 - PoC with GoLang & AutoHeal
- Abstract: A beginner’s guide to Google’s Distroless Docker images (small, clean, secure), demonstrating a proof of concept with GoLang and the AutoHeal feature.
- Guests: @sigabrt9
- S01-E37-FR | Shell in the Ghost - Polishing the CVE-2023-28879
- Abstract: A follow-up discussion on the CVE-2023-28879 vulnerability, focusing on refining the exploit method and improving defense mechanisms.
- Guests: @sigabrt9
- S01-E36-FR | PoC Shambles - An IOT 0-day carver
- Abstract: An episode exploring Shambles for the creation of Proof of Concept zero-days vulnerabilities in Internet of Things (IoT) devices.
- Guests: @olivier_boschko
- S01-E35-FR | Spip email/eval n-day - Analysis with Snuffleupagus
- Abstract: Analyzing the Spip email/eval n-day vulnerability using the Snuffleupagus PHP security module, highlighting the risk factors and mitigation techniques.
- Guests: @olivier_boschko
- S01-E34-FR | Openai Whisper - Video Transcript & Translate
- Abstract: Introduction and walkthrough of OpenAI’s Whisper open source tool, focusing on video transcription and translation capabilities.
- Guests: @0x1sis

- S01-E33-FR | Technology Watch May
- Keywords: Agarri, Burp, Noperator, Zip Snip, Mizu, YouWatch, Neodyme, CSGO, 0day, Assetnote, Sitecore, CVE-2023-25690, POC, Postmaniac, Tin-Z, ChatGPT, Escaping memory, Rez0, Prompt Injection, Charmbracelet, Mods, AST Explorer, IP Royal, Sneaker Proxies, Malcat, Anvaka, Map of GitHub, OpenAI, Audio API, Speech-to-Text, Whisper, EmbraceTheRed, Webpilot, Data Exfil, Markdown Injection, Audeye
- Guests: @0x1sis
- S01-E32-FR | StHack2023 Challenges, KongLua 02 - Far Fetched Debugger
- Abstract: Delving into StHack2023’s challenges, specifically the KongLua 02 challenge, featuring an extensive overview of advanced debugging techniques.
- Guests: @YanZaX
- S01-E31-FR | StHack2023 Challenges, KongLua 01 - Creds Digger
- Abstract: Discussion on the KongLua 01 challenge from StHack2023, focusing on efficient techniques to unearth sensitive credentials.
- Guests: @YanZaX
- S01-E30-FR | StHack2023 Challenges, Turn Around
- Abstract: An exploration of the Turn Around challenge from StHack2023, shedding light on advanced problem-solving strategies in cybersecurity.
- Guests: @YanZaX
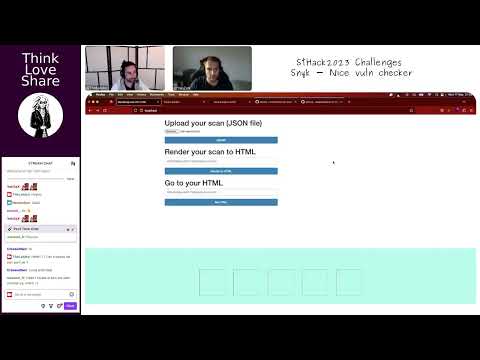
- S01-E29-FR | StHack2023 Challenges, Snyk - Nice vuln checker
- Abstract: Review of the StHack2023 challenge Snyk - Nice vuln checker, highlighting its features as a vulnerability checker and showcasing how it can be exploited in real-world automatisation.
- Guests: @YanZaX
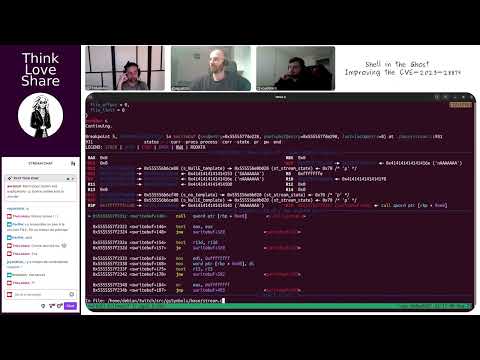
- S01-E28-FR | Shell in the Ghost - Improving the CVE-2023-28879 P3
- Abstract: Third part of the deep dive into CVE-2023-28879, focusing on fine-tuning the exploit technique, understanding, and mitigating the defense mechanisms.
- Guests: @sigabrt9, @voydstack
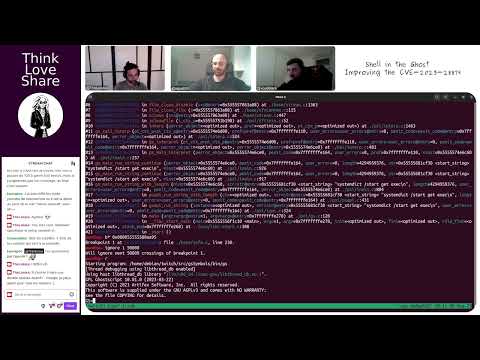
- S01-E27-FR | Shell in the Ghost - Improving the CVE-2023-28879 P2
- Abstract: Second part in the series exploring the CVE-2023-28879 vulnerability, continuing the conversation on the techniques to exploit and mitigate it.
- Guests: @sigabrt9, @voydstack
- S01-E26-FR | Shell in the Ghost - Improving the CVE-2023-28879 P1
- Abstract: The first part of an in-depth exploration of the CVE-2023-28879 vulnerability, focusing on techniques to exploit it with binary corruption and heap shenanigans.
- Guests: @sigabrt9, @voydstack
- S01-E25-FR | Technology Watch April - Latest tools & Articles
- Keywords: Bounty Targets Data, KBD Audio, Hyprland, ChatGPT Splitter, Lexfo, SSHimpanzee, ProjectDiscovery, AlterX, Subdomain Enumeration, PortSwigger, Cross-Site Scripting, GitHub, Ruby and Rails, Scoper, Intigriti, XSS Challenge, Java Exploitation, VBulletin Exploits, Containrrr, Watchtower, Giraffe Security, Google Remote Code Execution, Burp Professional Community, WhatBreach, RTX, Ghostccamm, Strapi Vulnerabilities, QEMU, Firmware Emulation, Spaceraccoon, CodeQL, Semgrep, CDK for Terraform, Pulumi, ProjectDiscovery PDTM, Static Analysis, FireBounty, SANS, SSH Konami Code, Regulator, CFReal, Ten, RenovateBot, YouTube
- Guests: @BitK_, @Midniblue
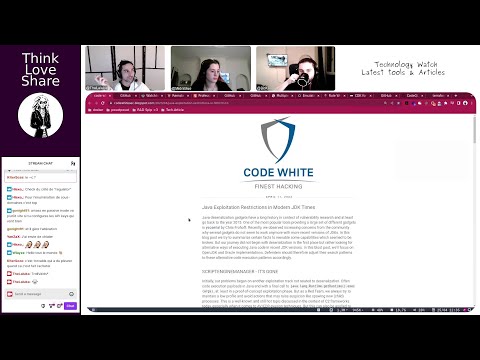
- S01-E24-FR | PoC of Tree-Sitter Python - Php AST parsing for 0day research
- Abstract: Presentation and exploration of a proof of concept for using Tree-Sitter Python for PHP AST parsing, focusing on zero-day vulnerability research.
- Guests: @BitK_, @Midniblue
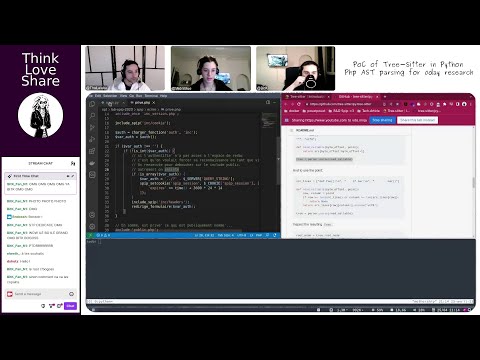
- S01-E23-FR | PoC du Screen Crab de @Hak5 - Courtesy de @BitK_
- Abstract: Demonstration of the Screen Crab tool by Hak5, detailing its features and potential applications in cybersecurity operations.
- Guests: @0x1sis
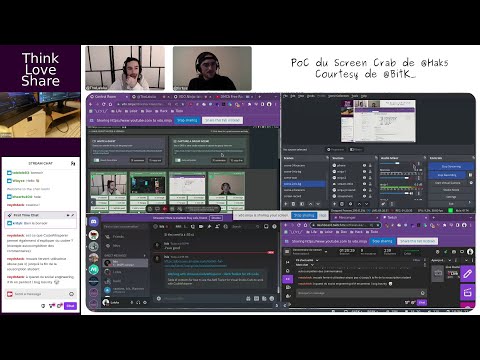
- S01-E22-FR | DeV de Autopaster - un tool “paste to fuzz”
- Abstract: Introduction and walkthrough of Autopaster, a “paste to fuzz” tool, highlighting its design and functionality in security testing.
- Guests: @0x1sis
- S01-E21-FR | PoC de AWS CodeWhisperer - le Copilot sauce AWS
- Abstract: Demonstration of AWS CodeWhisperer, discussing its capabilities as an AWS-specific alternative to GitHub’s Copilot tool.
- Guests: @0x1sis
- S01-E20-FR | Demo of the Burp ReconAIzer OpenAI-based extension
- Abstract: Showcasing the Burp ReconAIzer extension, demonstrating its potential in leveraging AI to improve web security testing workflows.
- Guests: Hisxo/@adrien_jeanneau
- S01-E19-FR | Introduction to CDKTF: build InfraAsCode with MORE Code
- Abstract: Introduction to CDKTF, exploring how it can be used to write more effective and maintainable Infrastructure as Code.
- Guests: Hisxo/@adrien_jeanneau
- S01-E18-FR | Create a BurpSuite (dir-logger) python extension
- Abstract: A tutorial on creating a Python extension for BurpSuite, focusing on the dir-logger feature and its utility in web application security testing.
- Guests: @0x1sis
- S01-E17-FR | PoC The ja-netfilter Instrumentation Framework
- Abstract: Exploration and proof of concept of the ja-netfilter Instrumentation Framework, detailing its applications and effectiveness in network security.
- Guests: @0x1sis
- S01-E16-FR | Play with the latest IDA 8.2 free release
- Abstract: An exploration of the new (and free!) features of IDA 8.2, including pseudo-code genration for x86_64.
- Guests: None
- S01-E15-FR | PoC ruff (ultra-fast python linter)
- Abstract: Demo and discussion on the ultra-fast Python linter, ruff.
- Guests: None
- S01-E14-FR | PoC Codon (python compiler to binay/ELF)
- Abstract: Overview of Codon, a Python to binary/ELF compiler, or is it? vsauce intro playing
- Guests: None
- S01-E13-FR | Caido PoC - What it’s worth & RoadMap
- Abstract: An in-depth look at Caido’s potential and future, including their roadmap.
- Guests: @YanZaX
- S01-E12-FR | Java Introspection with Frida on linux - Variant Vulnerability Analysis
- Abstract: Discussion on Java introspection with Frida-RE and vulnerability analysis.
- Guests: @YanZaX
- S01-E11-FR | Automated google-traduction on static GoHugo websites
- Abstract: How to automate Google translation on static GoHugo sites.
- Guests: None
- S01-E10-FR | CodeQL CLEAN WrapUp, Working PoC on golang pd-simpleserver part 4⁄3
- Abstract: Concluding the CodeQL series with a PoC on a simple Go server.
- Guests: @hugow_vincent
- S01-E09-FR | CodeQL PoC on Jolokia/Java & pd-simpleserver/golang part 3⁄3
- Abstract: Applying (trying to apply) CodeQL to Jolokia/Java & pd-simpleserver/golang.
- Guests: @hugow_vincent
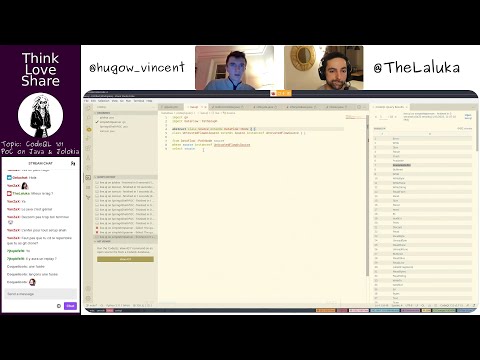
- S01-E08-FR | CodeQL PoC on Jolokia/Java & pd-simpleserver/golang part 2⁄3
- Abstract: More on CodeQL with focus on Jolokia/Java & pd-simpleserver/golang.
- Guests: @hugow_vincent
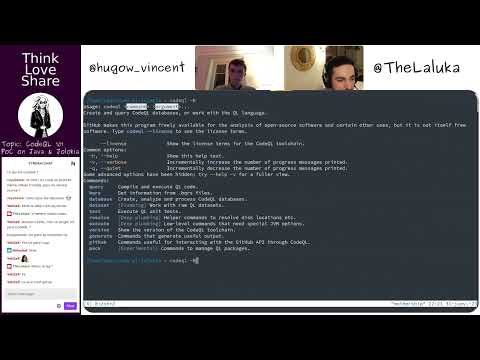
- S01-E07-FR | CodeQL PoC on Jolokia/Java & pd-simpleserver/golang part 1⁄3
- Abstract: Introduction to CodeQL with a PoC on Jolokia/Java & pd-simpleserver/golang.
- Guests: @hugow_vincent
- S01-E06-FR | Reviewing the PortSwigger Top 10 Web Hacking Techniques Nominations of 2022, part 3⁄3
- Abstract: Final review of the PortSwigger Top 10 Web Hacking Techniques of 2022.
- Guests: None
- S01-E05-FR | Reviewing the PortSwigger Top 10 Web Hacking Techniques Nominations of 2022, part 2⁄3
- Abstract: Continued review of the PortSwigger Top 10 Web Hacking Techniques of 2022.
- Guests: None
- S01-E04-FR | Reviewing the PortSwigger Top 10 Web Hacking Techniques Nominations of 2022, part 1⁄3
- Abstract: First look at the PortSwigger Top 10 Web Hacking Techniques of 2022.
- Guests: None
- S01-E03-EN | Creating a docker-compose Web Hacking lab for kong & konga
- Abstract: Tutorial on creating a web hacking lab for Kong & Konga using docker-compose.
- Guests: None
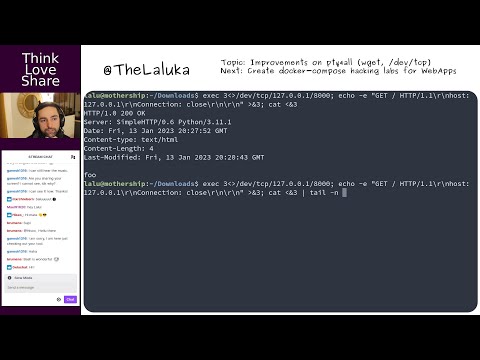
- S01-E02-EN | pty4all improvements, implementing curl, wget, and bash /dev/tcp fallback methods!
- Abstract: Exploring improvements to pty4all and implementing safe fallback methods.
- Guests: None
- S01-E01-FR | Say NO to Wordpress, and YES to Static Sites (PoC with GoHugo & MailChimp)
- Abstract: A case for static sites over Wordpress for security purpose, using GoHugo & MailChimp.
- Guests: None
EaMDFxfcQHY