2023-10-4 02:50:26 Author: blog.sucuri.net(查看原文) 阅读量:19 收藏
Default configurations in software are not always the most secure. For example, you might buy a network-attached home security camera from your friendly neighborhood electronics store. While these are handy to keep an eye on your property from the comfort of your phone, they also typically come shipped with a default username and password. And since they are connected to the web, they can be accessed from anywhere. Attackers know this, and Internet of Things (IoT) devices like this are common targets for malware that hijack devices using default passwords, making them part of huge DDoS botnets like Mirai.
The same can be said about the default settings of modern CMS. While the WordPress core is generally considered secure (and certainly more secure than a web-attached security camera by default) there are some improvements that can be made to harden WordPress further against attacks.
WordPress comes shipped with some default configurations (mostly related to the wp-admin panel) which need to be adjusted for improved security. While lots of attention is given to mass-infections resulting from severe vulnerabilities, the everyday compromises affecting WordPress sites (often stemming from unprotected wp-admin panels in particular) receive less airtime. And while WordPress has improved its security considerably over the years, some issues primarily related to limiting access control remain present.
In this post we will review some of the default configurations which can contribute to these infections and what you can do as a WordPress website owner to improve your security posture, keep attackers at bay, and protect your website from malware.
Convenience vs. security
Security can be a nuisance. Keeping track of countless login details across your ever-expanding catalogue of online accounts can contribute to “password fatigue” for example.
Generally speaking, what tends to be convenient tends to be insecure — and what tends to be secure is often inconvenient. The password “pass123” is easy and convenient to remember but trivial to guess and compromise. Sadly, security and convenience are often directly opposed to one another, with gains in one often resulting in losses for the other. Much effort has been invested into bridging this gap – for example the introduction of password managers, but this has resulted in brand new security issues; for example the LastPass compromise of 2022, stemming from the newly introduced issue of a “single point of failure”.
Similarly, we can say the same for WordPress and the default configurations that it comes shipped with. It’s fair to say that the meteoric rise in popularity that WordPress has had on the web over the last 20 years is in no small part due to its ease of use, accessibility and convenience. If you want to quickly get a website up and running for your blog, small business or hobby there’s no better alternative than WordPress. However, this convenience comes at a cost – not having to jump through hoops and bend over backwards just to login to your wp-admin administration panel also means that attackers don’t have to either.
Much like any out-of-the-box software the issues can be addressed. WordPress has an exceedingly rich repository of plugins which allow us to configure the baseline installation into something which is perhaps a little more cumbersome to use day-to-day but much more resilient to withstanding attacks from threat actors.
Let’s explore some of these default configurations, why they are problematic, and ways that we can address them to improve security and ensure that your website is not “low-hanging fruit” for attackers to compromise.
Unprotected admin panels
If you go to any random website running WordPress and navigate to the /wp-admin URL, this is usually what you see:
This is, of course, a prompt to enter in the administrator username and password, and in an out-of-the-box WordPress installation this is the only thing standing between your website and threat actors.
Ideally, this login prompt should not be publicly accessible at all, and restricted only to allowed IP addresses, or hidden behind a non-standard URL. However, this same login page is used not only by administrators but also by other user roles like subscribers, customers, and editors, so the usage of robust passwords is a must.
Unfortunately, the fact that the wp-admin panel is out in the open like this renders it vulnerable to brute force attacks. Moreover, the fact that the administrator URL (wp-admin) is identical for all out-of-the-box WordPress websites is itself problematic: No probing, guessing, or investigating is required for the attackers to know exactly where to start their attack.
By default, WordPress also does not come shipped with additional login security such as two factor authentication, so additional measures to secure this page are highly recommended to have the most secure website possible.
In earlier versions of WordPress a fresh installation would automatically generate the default administrator user with the name “admin“. This was particularly problematic with respect to brute force attacks because the attackers didn’t even have to obtain a list of administrator user names. This has since been fixed, and administrators are now required to specify a custom admin name during the installation process.
However, you might think to yourself, “Well, now that that’s fixed nobody is going to know what my admin account is named, so why is this a risk? Wouldn’t they have to figure that out too?”
Unfortunately, it is very easy to obtain the list of admin user names from a default WordPress website.
User enumeration attacks
Default WordPress installations are vulnerable to what is called a “user enumeration attack“. This essentially allows anybody to coax WordPress into spitting out the admin users on a website. This is due to the existence of permalinks — essentially the ability to list posts and pages, specifically from certain authors. This stems from the origins of WordPress being primarily a blogging platform, and the convenience of being able to share content across websites.
The way it works is actually quite simple. WordPress allows you to navigate to the posts of a particular author like so:
https://example.com/author/nameHowever, rather crucially, WordPress also allows us to do the same thing but by specifying their user identification number. Instead, all we must do is navigate to the following:
https://example.com/?author=1With the number in question being the user ID of the administrator user. This will spit out a page of all posts published by the user in question. What this also does is tell you the user name used to log into the WordPress environment.
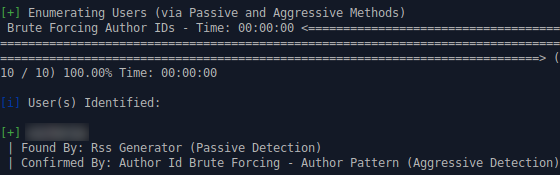
With the assistance of some handy-dandy tools such as WPScan this becomes much easier! Here is an example output of the following command:
wpscan --url example.com --enumerate uAs we can see below, this coaxes the primary admin user out of the website.
If we were an attacker at this point we would have all the information we need to begin a brute force attack.
This is not an attempt to scare users, but simply a reminder of the importance of using strong passwords and multi-factor authentication to prevent login compromise, which should stop any brute force or website-takeover through wp-admin in its tracks.
No limit to failed login attempts
Speaking of brute force attacks, this brings us to our next problematic default configuration: Lack of restriction on the number of failed login attempts. Out-of-the-box WordPress contains no limit or restrictions on the number of incorrect login attempts that can be made.
Compare this with the popular mobile operating system iOS: At six failed logins you get locked out for one minute, seven for five, eight for fifteen, and ten for an hour. This graduated approach to discouraging brute force attempts is of course not perfect but it is sufficient to deter or at least significantly slow down the most egregious attempts at breaking in. The fact is that multiple failed authentication attempts in a row tends to indicate that someone is trying to break in, and measures need to be put in place to deter that.
Coupling all of this with a universal administration URL and publicly accessible login panel this creates a perfect environment for abuse.
Direct editing of files
Although for the most part it would already be considered game over once an attacker has breached your admin panel there are more issues at play here and more trouble that attackers can cause after this point.
Another glaring issue with a default, out-of-the-box WordPress website is the ability to edit files directly on the server. This is done via the “Theme File Editor” or “Plugin File Editor” from wp-admin.
When you navigate to Tools → Theme/Plugin File Editor, admin users are granted the capability of editing the actual PHP code within their themes or plugins. See the example below of how easy it is to place a backdoor on the website from this interface:
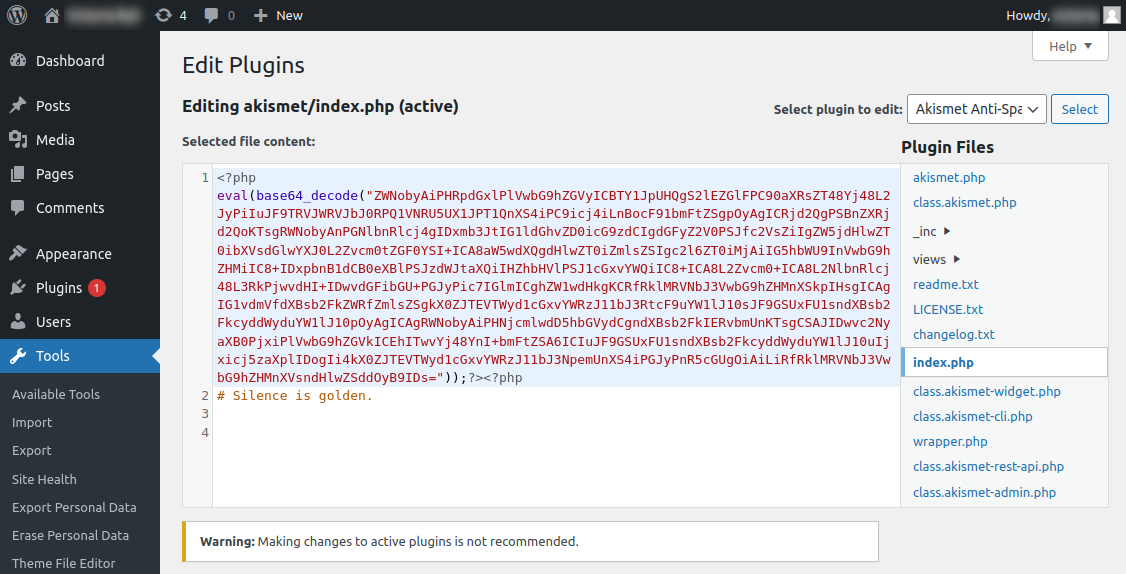
This way, even once a compromise is discovered and the admin’s password is changed by the website owner the attackers will still have access to the environment (they also frequently add malicious administrator users).
Another favorite tactic of the attackers is to (mis)use the wp-file-manager plugin in order to upload bogus/malicious plugins or themes containing backdoors, spam doorways and other malicious content:
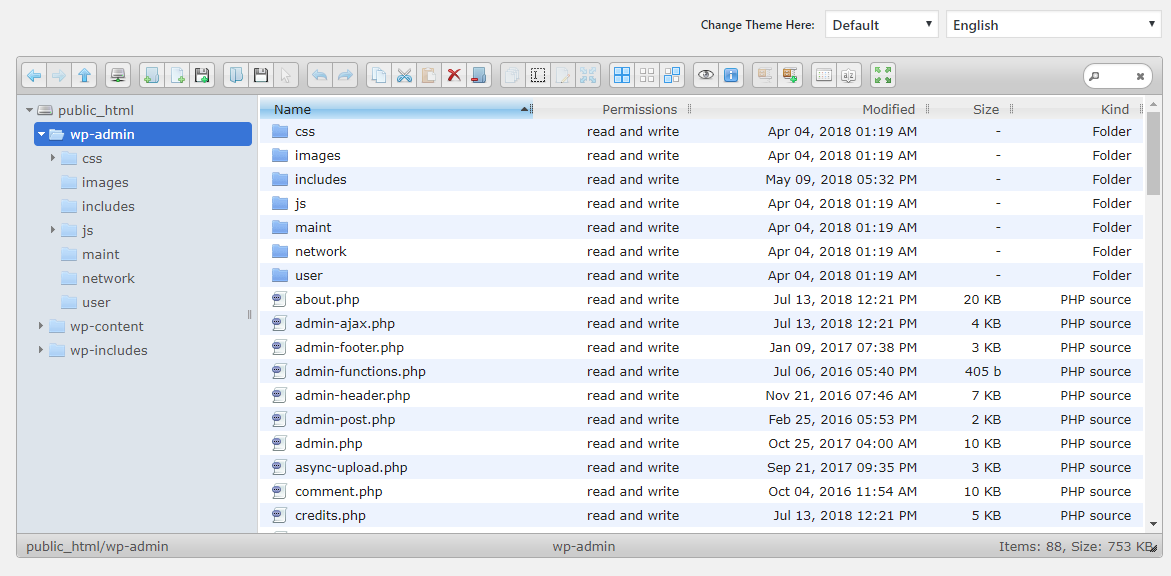
In fact, not a single day goes by that I do not see this exact plugin present on a compromised WordPress environment.
Put your best foot forward and prioritize website security
Website owners don’t often think of or prioritize security until it’s too late and, frankly, I can’t really blame them. Very few people start building a website with the intention of dealing with threat actors. People want to be left alone with their sites so they can blog, discuss their hobbies, listen to their music, sell their wares, manage their businesses and everything else that people have websites for. But, once a compromise happens and their website gets blocklisted by Google all of a sudden security becomes the most important thing in the world overnight.
Having a good security posture from day one is the best antidote for such situations, and starting with a secure configuration from the get-go is going to go a long way in ensuring that you won’t have to deal with a nasty (and expensive!) website compromise down the road.
A shifting landscape
The web is a very different place today than it was 20 years ago. WordPress was just getting started, everybody knew Tom from MySpace, and your parents hadn’t yet joined Facebook so it was still a cool place to hang out with your friends.
From a security standpoint, threat actors were not nearly as sophisticated as they are today, nor as well organized. Attacks tended to focus more on notoriety rather than financial gain, and the tools that were available were primitive when compared to what is used today. In today’s web, organized criminal enterprises use top-of-the-line exploit kits to compromise eCommerce websites, steal credit card details en masse and sell them on the black market; most of those victim websites in recent years run WordPress.
CMS platforms have had to keep pace with the ever-evolving threat landscape. For example, after having had an entire family of malware named after its eCommerce platform, Adobe implemented a few changes to out-of-the-box Magento websites: 2FA is enabled by default, the URL to access the admin dashboard is randomized and different for every website, and other enhanced protections such as improved protection against SQL injections and clickjacking have been implemented.
Similarly, WordPress has also implemented some improvements over the years for which its developers deserve credit. For example, automatic updates were implemented for those users who opt-in to it, there has been a push to encourage the use of robust passwords, and user role definitions have been enhanced to encourage least-privileged access. However, in its steadfast dedication to ease-of-use and convenience (arguably the keys to its overwhelming success), the issues with limiting access control outlined above in this post remain ever-present. This renders the platform stubbornly susceptible to chronic brute force attacks and the security issues which follow.
What to do next?
Fortunately there are solutions to all of the problems that I listed above. By utilizing the rich open-source repository of WordPress plugins there is a solution to every issue described in this article. These are all outlined in a previous blog post on WordPress hardening.
Remember, every security improvement can sometimes cause a corresponding decrease in convenience. Every website is different so you’ll need to consider carefully what the best balance between the two is for your situation. If you have a small blog, you may be content with enabling automatic updates and putting some strict limits on failed login attempts. On the other hand, if you run a successful WooCommerce store and handle sensitive information like payment data you may want to have some more skookum measures in place.
If you would like some help securing your website, you can also consider placing your site behind our website firewall service. Creating robust access control rules on your site is just a few clicks away!
如有侵权请联系:admin#unsafe.sh