
2023-10-4 13:49:42 Author: securityboulevard.com(查看原文) 阅读量:6 收藏
Introduction
Security as a Service (SECaaS) has emerged as a game-changer for businesses of all sizes. Offering a subscription-based model, SECaaS eliminates hefty upfront costs, making cybersecurity more accessible than ever. But the benefits don’t stop at cost savings.
From resource efficiency to enhanced security measures, SECaaS is revolutionizing how businesses approach cybersecurity. In this article, we’ll delve into the compelling advantages of adopting SECaaS in 2023. We will provide you with SECaaS implementation guidance to make an informed decision for your business.
What is SECaaS?
Security as a Service (SECaaS) is a cloud-based model. It allows companies to outsource their cybersecurity needs to an external provider. In essence, it combines the advantages of cloud technologies with specialized cybersecurity expertise. In today’s digital era, where cyber threats are increasingly sophisticated, SECaaS offers a cost-effective and scalable solution.
SECaaS not only alleviates the burden of in-house security management but also provides robust data protection and VoIP security. As businesses continue to digitize, the relevance of SECaaS is more pronounced. It offers myriad benefits from cost savings to enhanced security measures.

Why Small Businesses Need SECaaS
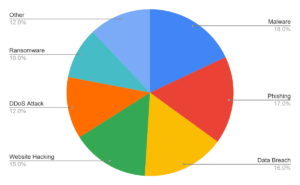
The pie chart based on data from StrongDM highlights the multifaceted cybersecurity challenges small businesses face. Malware leads the pack at 18%, closely followed by phishing at 17% and data breaches at 16%. These top three threats underscore the need for robust endpoint security and employee education. Website hacking and DDoS attacks, at 15% and 12% respectively, emphasize the importance of secure web infrastructure. Ransomware, although lower at 10%, poses a significant financial risk. The “Other” category at 12% serves as a reminder of the evolving nature of cyber threats. Small businesses often lack the resources for dedicated cybersecurity teams, making them attractive targets for attackers.
This pie chart serves as a crucial tool for prioritizing security measures based on the most prevalent risks.
Key Components of SECaaS
Security as a Service (SECaaS) is a comprehensive approach to cybersecurity, offering various essential elements to safeguard your digital assets. Here are some key components:
- Identity and Access Management (IAM): Ensures only authorized users can access specific resources, enhancing security and compliance.
- Threat Detection: Monitors data to identify and alert administrators of suspicious activities, such as unauthorized access.
- Incident Response and Remediation: Focuses on investigating security incidents and taking corrective actions to prevent future occurrences.
- Data Loss Prevention (DLP): Protects sensitive data from unauthorized access and data breaches.
- Vulnerability Management: Scans and identifies weaknesses in the system, offering solutions to mitigate risks.
- Business Continuity and Disaster Recovery (BCDR): Ensures data backup and quick recovery in case of catastrophic events.
- Managed IT Services: Includes anti-virus protection and intrusion detection to safeguard your network.
These components work in tandem to provide a robust security posture, crucial for any organization in today’s digital landscape.
How to Choose the Right SECaaS Provider
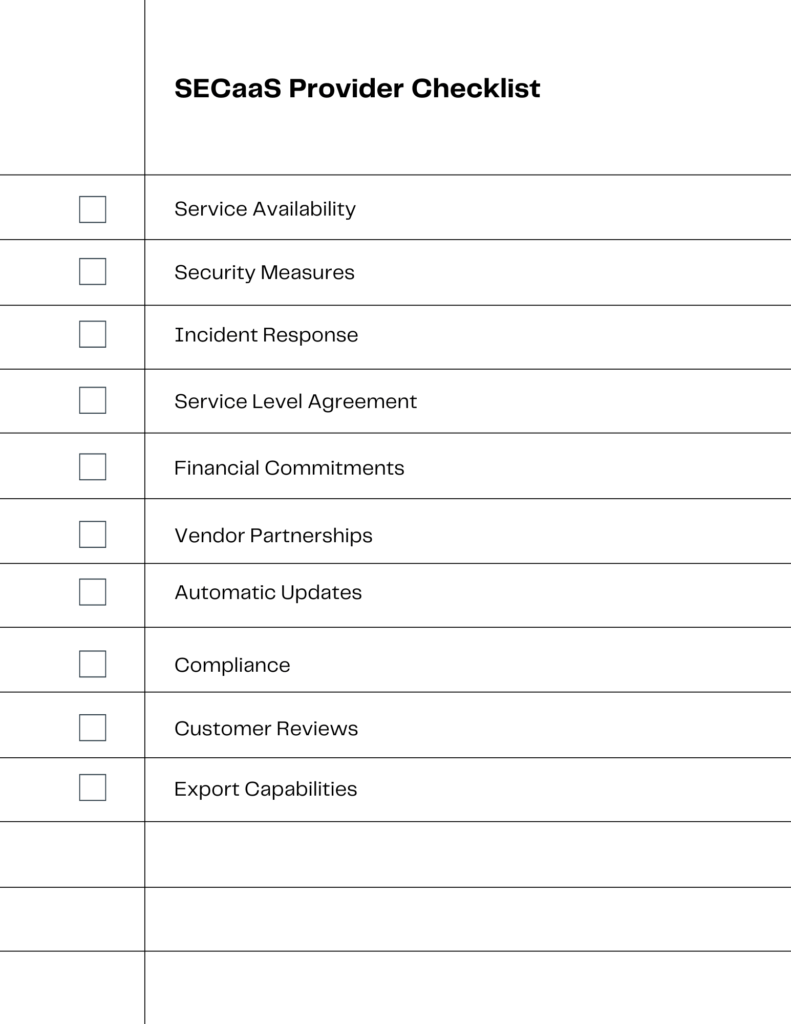
To select the ideal Security as a Service (SECaaS) provider, consider the following checklist elements:
- Service Availability: Ensure the provider offers high uptime and reliability.
- Security Measures: Evaluate the security protocols and frameworks the provider uses.
- Incident Response: Check for capabilities in incident investigation, response, and remediation.
- Service Level Agreement (SLA): Review the SLA for response times and other service metrics.
- Financial Commitments: Understand the cost structure and any long-term commitments required.
- Vendor Partnerships: Check if the provider has partnerships that can benefit your security posture.
- Automatic Updates: Ensure the provider keeps security tools up-to-date automatically.
- Compliance: Make sure the provider meets necessary compliance standards like PCI.
- Customer Reviews: Look for customer testimonials or case studies to gauge satisfaction levels.
- Export Capabilities: Confirm the ability to export logs and other data for your records[.
Implementation Steps for SECaaS
Pre-Implementation Planning
Before diving into the implementation of Security as a Service (SECaaS), pre-implementation planning is crucial. This phase sets the stage for a successful rollout, ensuring that you’re well-prepared to mitigate risks and stay within budget.
Planning Steps
- Objective Setting: Clearly define what you aim to achieve with SECaaS. This will guide your planning and decision-making processes.
- Budget Allocation: Determine the financial resources available for the SECaaS implementation. Be realistic about costs to avoid future financial strain.
- Team Formation: Assemble a cross-functional team of IT, security, and business stakeholders to ensure diverse perspectives in planning.
- Risk Assessment: Identify potential risks that could derail the implementation. Develop strategies to mitigate these risks effectively.
- Timeline Creation: Establish a realistic timeline for the implementation, taking into account potential delays and setbacks.
Pre-implementation planning is a vital first step in the SECaaS journey. By setting clear objectives, allocating a budget, forming a competent team, assessing risks, and creating a timeline, you lay a strong foundation for a successful implementation.
During Implementation
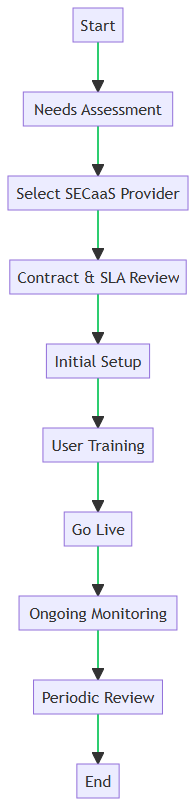
1. Start
Kick off the project by gathering key stakeholders and defining objectives.
2. Needs Assessment
Form a working group to conduct a thorough evaluation of your organization’s security needs to identify gaps and requirements.
3. Select SECaaS Provider
Choose a SECaaS provider that aligns with your organization’s needs and budget.
4. Contract & SLA Review
Review the contract and Service Level Agreement (SLA) to ensure they meet your expectations and legal requirements.
5. Initial Setup
Configure the SECaaS solution according to your organization’s specific needs.
6. User Training
Educate your team on how to interact with the new system, emphasizing best practices and security protocols.
7. Go Live
Launch the SECaaS solution and integrate it into your existing infrastructure.
8. Ongoing Monitoring
Continuously monitor the system for security threats and performance issues.
9. Periodic Review
Regularly assess the effectiveness of the SECaaS solution, making adjustments as needed.
10. End
Conclude the implementation process, ensuring all objectives have been met and the system is fully operational.
Implementing SECaaS doesn’t have to be a herculean task. By following this structured approach, you can ensure a smooth implementation process that aligns with your organization’s security needs. Remember, the key to a successful SECaaS implementation lies in meticulous planning, continuous monitoring, and periodic reviews.
Common Pitfalls and How to Avoid Them
Navigating the landscape of Security as a Service (SECaaS) can be complex. This section aims to shed light on common pitfalls businesses often encounter during SECaaS implementation. Further, it offers actionable solutions to sidestep these issues.
Inadequate Risk Assessment:
Businesses often skip thorough risk assessments, leading to mismatched security solutions. The solution is to conduct a comprehensive risk assessment to identify vulnerabilities. Based on that, one can choose a SECaaS solution that aligns with your specific needs.
Poor Vendor Selection:
Out-of-the-box solutions may not address unique security needs. Opt for customizable SECaaS solutions that can be tailored to fit your specific requirements.
Ignoring Compliance Requirements:
Non-compliance with industry regulations can result in penalties. Be sure that the chosen SECaaS solution complies with industry-specific regulations that are applicable to your company.
Overlooking Employee Training:
Employees may inadvertently compromise security due to lack of awareness. Be sure to invest in employee training programs that focus on security best practices.
Implementing SECaaS is not without its challenges. However, by being aware of common pitfalls such as inadequate risk assessment, poor vendor selection, and lack of customization, you can make informed decisions that enhance your security posture. The key is to be proactive rather than reactive in your approach to implementing a SECaaS solution.
Conclusion
In summary, Security as a Service (SECaaS) is a game-changer for small businesses. It offers robust cybersecurity solutions without the need for in-house expertise. We’ve explored its key advantages, including cost-effectiveness, scalability, and compliance. We also delved into how to choose the right SECaaS provider and avoid common pitfalls in implementation.
SECaaS is not just a trend; it’s a necessity in today’s digital landscape. It allows small businesses to level the playing field, ensuring they are as secure as their larger counterparts.
Don’t leave your business vulnerable. Take the next step—reach out to a reputable SECaaS provider for a consultation or drop your questions about SECaaS in the comments below. Your business’s security is too important to be an afterthought.
Blog Post Graphic Recommendation: A comprehensive infographic that encapsulates the entire SecaaS implementation process, from planning to post-implementation review. This can be used as a lead magnet to encourage subscriptions or social shares.
The post Mastering SECaaS: Your Ultimate Implementation Guidance for 2023 appeared first on Endpoint Security.
*** This is a Security Bloggers Network syndicated blog from Endpoint Security authored by Michael Toback. Read the original post at: https://smallbizepp.com/secaas-implementation-guidance/?utm_source=rss&utm_medium=rss&utm_campaign=secaas-implementation-guidance
如有侵权请联系:admin#unsafe.sh
