2023-10-5 17:0:14 Author: blog.elcomsoft.com(查看原文) 阅读量:20 收藏
We have exciting news: iOS Forensic Toolkit 8 is now available for Windows users in the all-new Windows edition. The new build maintains and extends the functionality of EIFT 7, which is now approaching the end of its life cycle. In addition, we’ve made the Toolkit portable, eliminating the need for installation. Learn what’s new in the eights version of the Toolkit!
Windows Edition
We’ve released iOS Forensic Toolkit 8 almost exactly one year ago. At the time, the eights version of the Toolkit was exclusive to macOS, while Windows users were served by EIFT 7, which was maintained and updated alongside with the newer and greater EIFT 8. Today, we are making iOS Forensic Toolkit 8 available to Windows users and finally discontinuing iOS Forensic Toolkit 7, which has now reached its end-of-life.
The Windows edition of iOS Forensic Toolkit 8 offers the familiar feature set carried over from EIFT 7, which includes advanced logical and low-level extraction with the help of the custom extraction agent. Forensically sound bootloader-level extraction is still exclusive to the macOS edition though.
Limitations of the Windows Edition
Compared to macOS, the Windows edition has the following limitations:
- No checkm8 support (yet). Bootloader-level extraction remains exclusive to macOS for the time being.
- Signing the extraction agent requires an Apple ID enrolled in Apple Developer Program. macOS users can use developer and ordinary Apple IDs.
Going Portable
We changed the way iOS Forensic Toolkit is installed and used. On a Windows system, EIFT 8 will no longer require installation. Just download the all-new portable package, unpack the archive with the password provided in your registration email, and start using the Toolkit right away!
Selective Folder Access During Low-Level Extraction
The updated low-level extraction agent now allows experts to pull individual folders or just the file system metadata such as file names, sizes, and timestamps. We’ve made a few other changes to the extraction agent, which are listed below.
The new function is implemented via a couple of extra commands: extract and metadata. The -o switch specifies path to the output folder, while the optional -p switch points to the source file or folder in the iOS file system to be extracted. If no -p switch is present, the tool will extract everything starting with “/private/var/” (the root of the data partition).
Command-line Interface
While EIFT 7 was built around a console-driven menu, iOS Forensic Toolkit 8.41 brings advanced user experience built around the command line. Why did we transition from the menu to a command-line interface? The main reason was the significantly increased number of functions supported by the new build, linked to the growing list of supported extraction methods, device models, and iOS versions. On the one hand, this new functionality introduced exciting possibilities; on the other hand, it led to increased complexity in use. For instance, when using checkm8 extraction, one or more additional commands may be required to unlock the data partition or to mitigate various issues, which could not be hidden behind a single menu item. As a result, we arrived at the current solution: a command-line interface that provides full control over each step of the process.
The transition to a command-line interface offers users a level of granular control that could not be achieved before. This granular control over the extraction process is crucial given the diverse range of iOS devices and system versions. With the CLI, forensic experts can respond to unexpected hiccups or device-specific requirements during the extraction process. Ultimately, the shift from a menu-based system to a command-line interface reflects our commitment to providing forensic professionals with the tools they need to catch up with the increasing diversity of the iOS ecosystem.
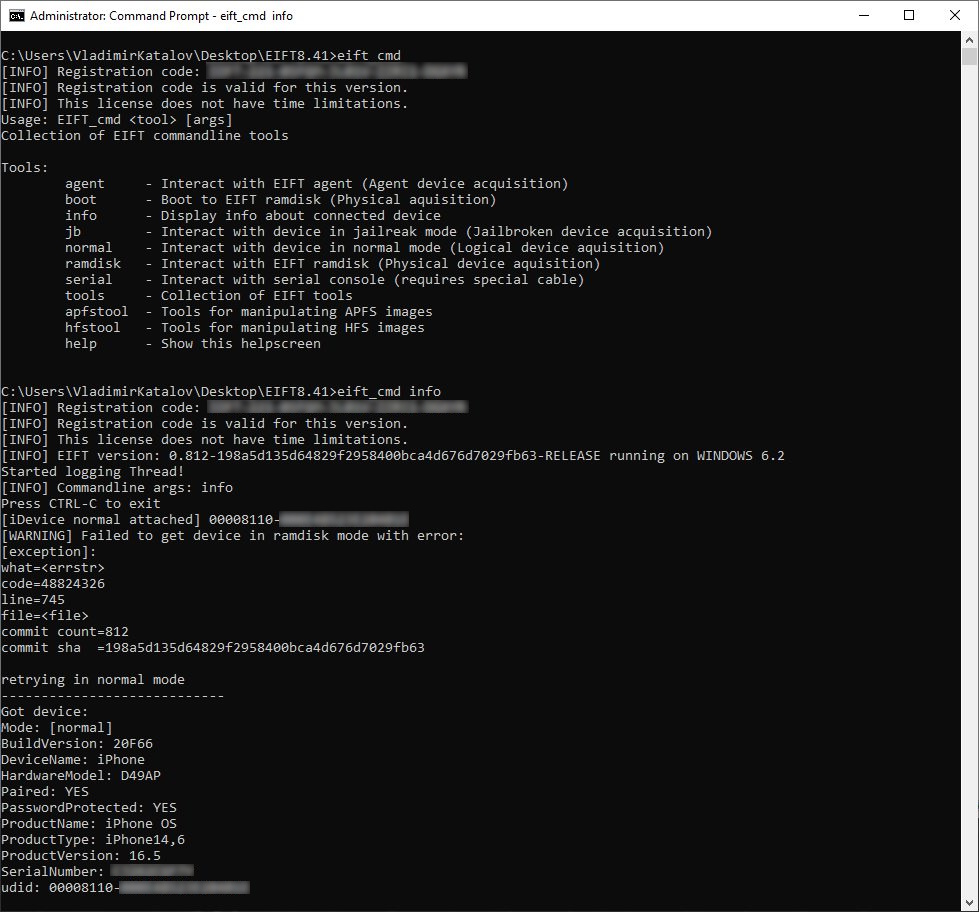
This is how the new UI looks like:
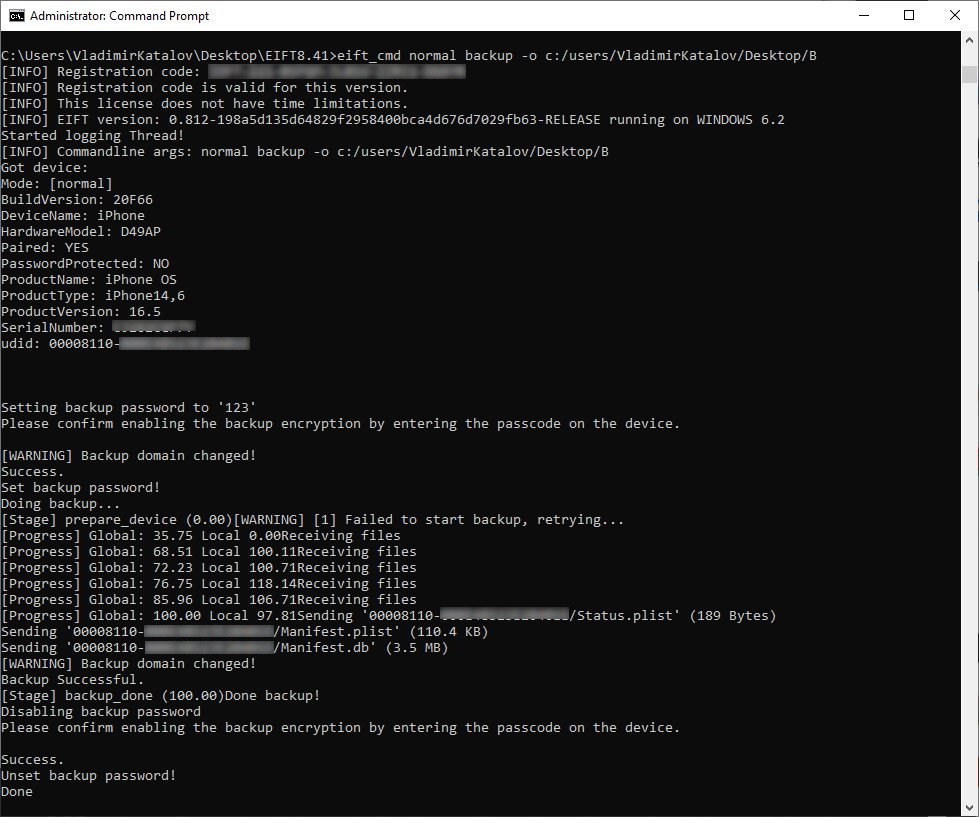
Creating a backup (note the temporary password ‘123’):
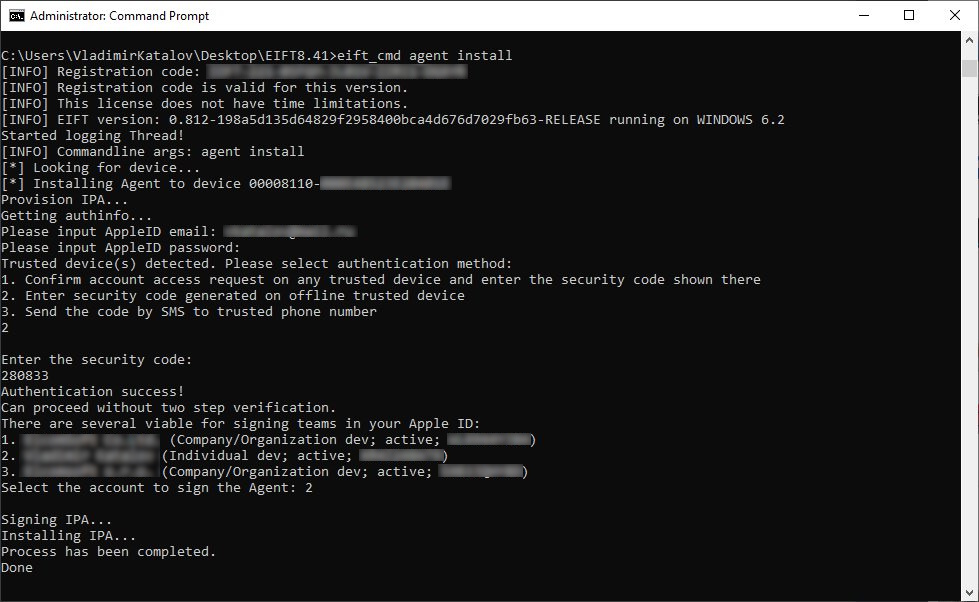
Sideloading the extraction agent:
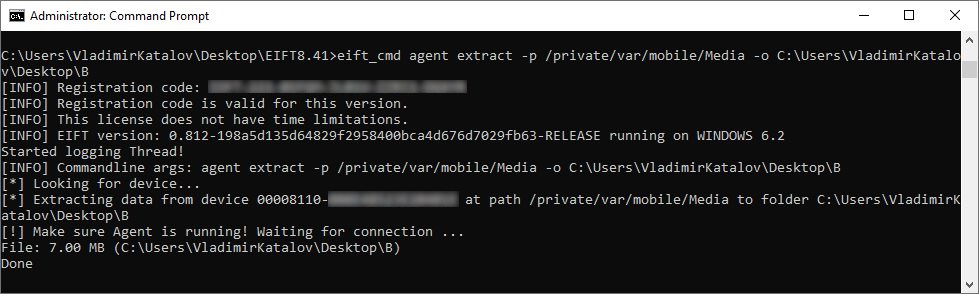
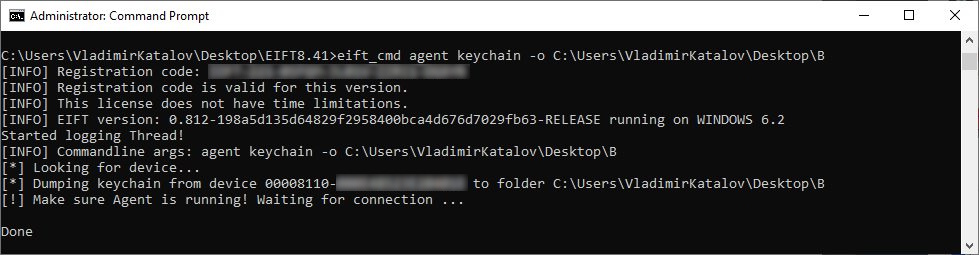
Pulling the file system, keychain, and file system metadata through agent-based extraction:
New Commands
While Windows users will be introduced to CLI with this new build, macOS users have been using the new UI for about a year. The new build introduces several new commands for extraction agent, and modifies the function of the output switch.
Previously, the extraction agent supported two commands: tar and keychain, complemented with the -o switch specifying the output file name, e.g.:
EIFT_cmd agent keychain -o passwords.xml EIFT_cmd agent tar -o data.tar
While you could specify the full path, e.g. “-o /Users/ElcomSoft/Desktop/data/data.tar”, that syntax is now deprecated. Instead, the mandatory -o switch must be used to specify output path (and not a file name as it used to be in the previous build). Starting with this release, file names will be assigned automatically. You’ll have to use the -o switch when pulling the file system image, extracting the keychain, or accessing individual files, folders, or file system metadata.
Examples
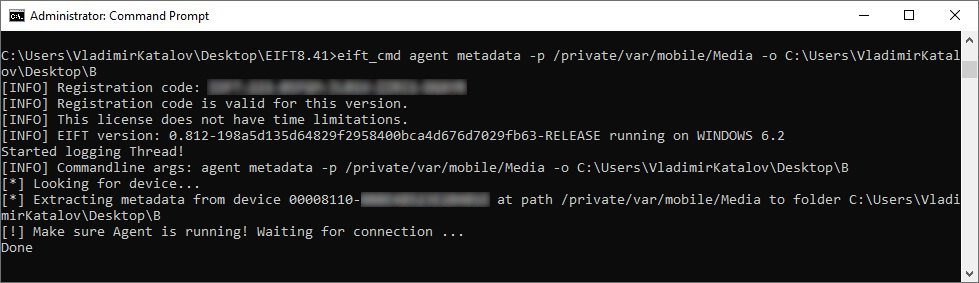
Extract file system metadata from the Media folder:
EIFT_cmd agent metadata -p /private/var/mobile/Media/ -o /Users/ElcomSoft/Desktop/metadata/
Extract the complete Media folder:
EIFT_cmd agent extract -p /private/var/mobile/Media/ -o /Users/ElcomSoft/Desktop/data/
Extract full file system image of the user partition:
EIFT_cmd agent extract -o /Users/ElcomSoft/Desktop/data/
Extract a single file Photo.jpg from the media album:
EIFT_cmd agent extract -p /private/var/mobile/Media/DCIM/Photo.jpg -o /Users/ElcomSoft/Desktop/data/
Going Multiplatform
The release of the Windows edition marks a significant step towards true multiplatform compatibility. We are actively working on a Linux edition, with an official announcement expected soon. Stay tuned!
REFERENCES:
![]()
Elcomsoft iOS Forensic Toolkit
Extract critical evidence from Apple iOS devices in real time. Gain access to phone secrets including passwords and encryption keys, and decrypt the file system image with or without the original passcode. Physical and logical acquisition options for all 64-bit devices running all versions of iOS.
Elcomsoft iOS Forensic Toolkit official web page & downloads »
如有侵权请联系:admin#unsafe.sh