
2023-10-6 09:33:5 Author: securityboulevard.com(查看原文) 阅读量:9 收藏
Introduction
Navigating the maze of device management is a common challenge for small businesses. With a diverse range of devices—smartphones, tablets, laptops—each with its own set of applications and security settings, the task becomes increasingly complex. This is where Mobile Device Management (MDM) becomes a game-changer for small businesses.
MDM streamlines the management of multiple devices, ensuring security and efficiency while reducing the burden on IT personnel. In this comprehensive 2023 guide, we’ll delve into why MDM is crucial for small businesses and how to make the most of it.
Why MDM is Crucial for Small Businesses
The absence of an MDM solution can expose small businesses to a myriad of risks and challenges. Without centralized control, each device becomes a potential entry point for cyber threats. Data breaches, unauthorized access, and malware attacks are just a few of the security risks that can wreak havoc on your business. Additionally, the lack of an MDM solution can lead to inefficiencies, as IT personnel must manually manage each device, a time-consuming and error-prone process.
On the flip side, implementing an MDM solution offers a host of benefits. First and foremost, it enhances security by enabling features like remote lock, data wipe, and device encryption. It also streamlines operations by automating tasks such as software updates and device enrollment. Furthermore, MDM solutions offer scalability, allowing your device management strategy to grow as your business expands.
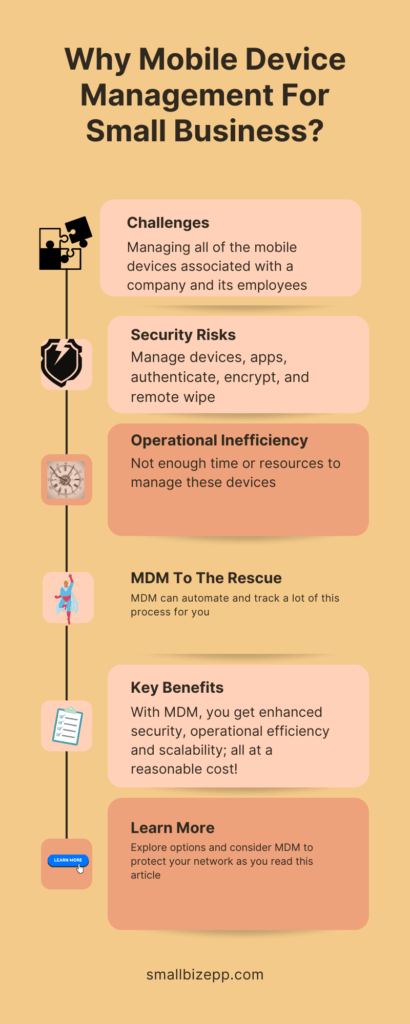
Key Features of an Ideal MDM Solution
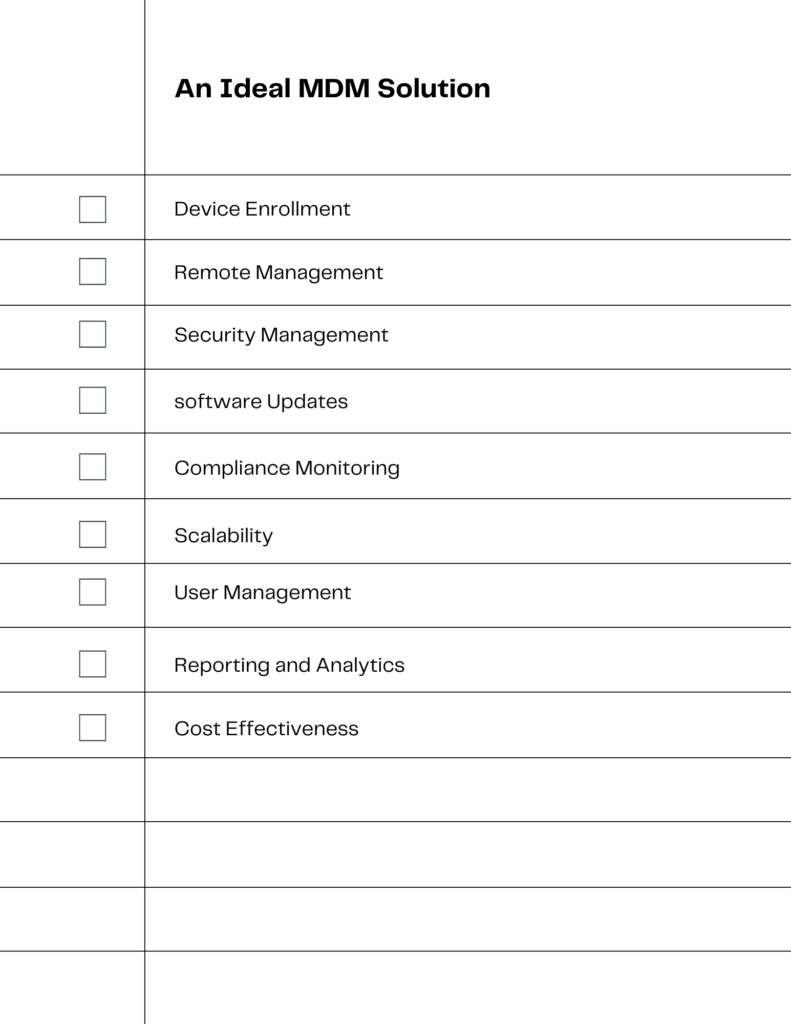
When it comes to Mobile Device Management, not all solutions are created equal. For small businesses, certain features are non-negotiable. Here’s a rundown of the essential components to look for in an MDM solution:
Device Enrollment
The first step in device management is enrollment. An ideal MDM solution should offer a seamless, automated process for adding new devices to your network.
Remote Management
The ability to manage devices remotely is crucial. Look for solutions that allow you to control device settings, push updates, and even lock or wipe devices from a centralized dashboard.
Security Management
Security is paramount. Essential features include device encryption, remote lock, and the ability to wipe data. These features ensure that your business data remains secure, even if a device is lost or stolen.
Software Updates
Automated software updates are a must. This feature ensures that all devices run the latest, most secure versions of software and apps, reducing the risk of security vulnerabilities.
Compliance Monitoring
Compliance with industry standards and regulations is essential. An MDM solution should offer features that help you monitor and ensure that all devices meet these standards.
Scalability
As your business grows, your MDM solution should grow with it. Scalability ensures that the system can handle an increasing number of devices without performance issues.
User Management
User management features allow you to control who has access to what. This includes setting permissions and even restricting access to certain apps or data.
Reporting and Analytics
Insight into device usage and performance is invaluable. Look for an MDM solution that offers robust reporting and analytics features.
Cost-Effectiveness
Finally, consider the cost. While MDM is an investment, the returns in terms of security and efficiency can be significant. Look for solutions that offer a good balance between cost and features.
By focusing on these key features, you’ll be well-equipped to choose an MDM solution that not only meets your immediate needs but also scales with your business.
Understanding Different Types of MDM Solutions
When it comes to Mobile Device Management, one size doesn’t fit all. The right solution for your business depends on various factors, including your specific needs, the size of your organization, and your budget. Here are the different types of MDM solutions you should consider:
Table: Comparison of Different Types of MDM Solutions
| Feature/Type | Cloud-Based MDM | On-Premises MDM | Unified Endpoint Management (UEM) |
|---|---|---|---|
| Deployment | Hosted on a cloud service | Installed on local servers | Can be either cloud-based or on-premise. |
| Initial Setup | Easier and quicker | More complex and time-consuming | Moderate complexity |
| Cost | Subscription-based, scalable | Higher upfront costs | Varies based on features |
| Security | High, but dependent on cloud provider | High, but requires internal expertise | High, integrates multiple security layers |
| Scalability | Highly scalable | Limited by server capacity | Highly scalable |
| Maintenance | Vendor handles updates | IT team responsible for maintenance | Vendor or IT team based on deployment |
| Customization | Limited | Highly customizable | Moderate to high customization |
| User Experience | Generally user-friendly | May require specialized training | User-friendly with more features |
| Compliance | Vendor often handles compliance | Business is responsible for compliance | Business or vendor based on deployment |
| Best For | Small to medium businesses | Large enterprises with complex needs | Businesses needing comprehensive solutions |
Cloud-Based MDM
Cloud-based solutions are generally easier to set up and are scalable, making them ideal for small to medium-sized businesses. However, you’re reliant on the cloud provider for security and compliance.
On-Premises MDM
On-premises solutions offer more customization and are often chosen by larger enterprises. They require a higher initial investment and your IT team will be responsible for maintenance and compliance.
Unified Endpoint Management (UEM)
UEM solutions offer the most comprehensive feature set, combining MDM with other forms of device management. They are highly scalable and can be either cloud-based or on-premises, offering the best of both worlds.
By understanding the pros and cons of each type, you can make an informed decision that best suits the needs and goals of your small business.
How to Evaluate MDM Solutions
Choosing the right MDM solution is a critical decision that can significantly impact your business operations and security. Here are some key criteria to consider when evaluating your options:
Budget
First and foremost, determine how much you’re willing to invest. While MDM is essential, it should also be cost-effective for your business.
Security Features
Look for robust security features like device encryption, remote lock, and data wipe capabilities. These are non-negotiable for protecting sensitive business data.
Scalability
As your business grows, your MDM solution should be able to scale with it. Check for scalability features and any additional costs involved.
User Experience
A solution that’s difficult to use can hinder adoption. Opt for an MDM solution that offers a user-friendly interface and straightforward management features.
Vendor Reputation
Research the vendor’s reputation. Customer reviews and case studies can provide valuable insights into the reliability and performance of the solution.
Compliance
Ensure the solution meets industry compliance standards, especially if you’re in a regulated sector like healthcare or finance.
Support and Maintenance
Consider the level of support offered by the vendor. Timely and effective support can be a lifesaver in critical situations.
By carefully evaluating MDM solutions based on these criteria, you’ll be better positioned to select a solution that aligns with your business needs and goals.
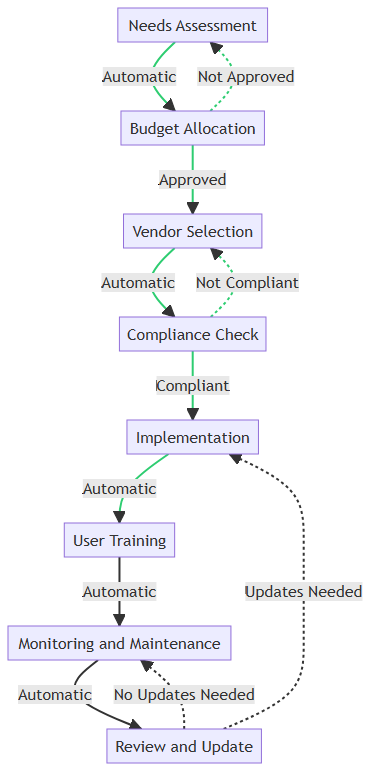
Implementation Steps for MDM
Implementing an MDM solution starts with a thorough Needs Assessment to identify your organization’s specific requirements. Once you’ve established your needs, you’ll move on to Budget Allocation. If the budget is approved, the next step is Vendor Selection, where you’ll choose an MDM solution based on your criteria. Should the budget not be approved, you’ll need to revisit the Needs Assessment.
After selecting a vendor, you’ll conduct a Compliance Check to ensure the solution meets industry standards. If the solution is compliant, you proceed to Implementation; otherwise, you’ll need to reconsider your vendor selection.
Following successful implementation, User Training is essential to ensure your staff knows how to use the new system effectively. After training, the focus shifts to Monitoring and Maintenance to keep the system up-to-date and secure.
Finally, you’ll engage in periodic Review and Update sessions. If updates are needed, you’ll loop back to the Implementation phase; otherwise, you’ll continue with ongoing monitoring and maintenance.
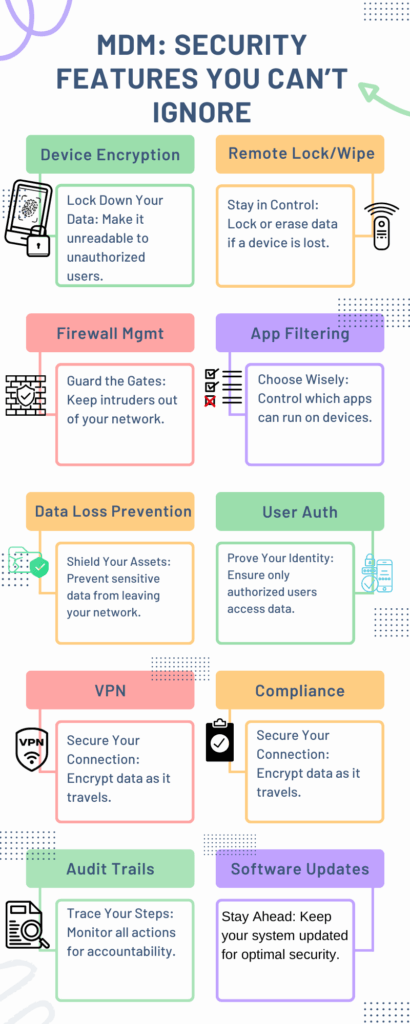
Security Features You Can’t Ignore
When it comes to Mobile Device Management (MDM) for small businesses, security is paramount. Here are some essential security features you can’t afford to overlook:
Device Encryption
Lock Down Your Data: Encryption makes the data on your devices unreadable to unauthorized users. It’s the first line of defense in case of device loss or theft.
Remote Lock and Wipe
Stay in Control: If a device is lost or stolen, the ability to remotely lock it or wipe its data is crucial. This feature ensures that sensitive information doesn’t fall into the wrong hands.
Firewall Management
Guard the Gates: A robust firewall prevents unauthorized access to your network. It’s essential for keeping intruders at bay and protecting your data.
App Filtering
Choose Wisely: Control which apps can be installed or run on your devices. This helps to prevent malicious software from compromising your network.
Data Loss Prevention (DLP)
Shield Your Assets: DLP features prevent sensitive data from being sent outside your network. This is vital for compliance and protecting intellectual property.
User Authentication
Prove Your Identity: Multi-factor authentication ensures that only authorized users can access your network. It adds an extra layer of security that goes beyond just passwords.
VPN Configuration
Secure Your Connection: A Virtual Private Network (VPN) encrypts data as it travels through the internet. This is especially important for remote workers to securely access the company network.
Compliance Reporting
Stay Accountable: Regular compliance reports help you keep track of your security posture and meet industry regulations.
Audit Trails
Trace Your Steps: Audit trails record all actions taken within the system. This is crucial for accountability and investigating any security incidents.
Software Updates
Stay Ahead: Regular software updates patch vulnerabilities and keep your system secure. Never underestimate the power of staying updated.
Cost Considerations
When implementing an MDM solution for your small business, budgeting is a critical factor. Here are some key considerations:
Initial Setup Costs
The upfront costs can include hardware, software, and licensing fees. Make sure to allocate funds for these essentials.
Monthly or Annual Subscriptions
Many MDM solutions come with recurring fees. Factor these into your ongoing operational budget.
User Training
Don’t overlook the costs associated with training your staff to use the new system. This is an investment in secure and efficient operations.
Maintenance and Updates
Regular system maintenance and software updates may incur additional costs. Plan for these to avoid surprises.
Compliance Costs
Meeting industry regulations often requires additional features or services, which can add to the overall cost.
Scalability
As your business grows, your MDM needs will evolve. Choose a solution that can scale with you to avoid future costs.

Real-world Case Studies
Understanding the practical application of Mobile Device Management (MDM) can be invaluable for small businesses. To illustrate this, let’s explore two hypothetical case studies that demonstrate the challenges and benefits of implementing MDM solutions.
Case Study 1: The Remote Work Challenge

A small marketing agency with a 15-member team faced challenges when they shifted to remote work due to the pandemic. Security incidents were on the rise, and managing devices became a headache. After implementing an MDM solution with robust device encryption and remote lock and wipe features, the agency experienced a significant reduction in security incidents within a month. The team could now work remotely more efficiently and securely access company data from anywhere.
Case Study 2: The Growing Retail Business

A local retail business with multiple outlets struggled with managing inventory and sales data across various devices. They opted for an MDM solution that offered strong data loss prevention features and app filtering capabilities. As a result, the business streamlined its inventory and sales processes. The MDM system even flagged a potential data breach, enabling the company to take immediate action.
In conclusion, these case studies highlight the transformative impact that a well-chosen MDM solution can have on a small business. They serve as practical examples for any small business manager or IT personnel considering implementing an MDM system.
Conclusion
Implementing a Mobile Device Management (MDM) solution is no longer a luxury but a necessity for small businesses in today’s digital landscape. From understanding the crucial security features to considering cost factors and learning from real-world case studies, we’ve covered the essentials you need to make an informed decision. Now, it’s your turn to take the reins and secure your business’s digital future.
We encourage you to share your experiences or questions in the comments section below. Your insights could be invaluable to other small business managers and IT personnel navigating the complexities of MDM.
Graphic for Blog Post: A comprehensive infographic that encapsulates the entire content, from the importance of MDM to choosing the right solution.
The post Unlocking MDM for Small Business: What you need to know appeared first on Endpoint Security.
*** This is a Security Bloggers Network syndicated blog from Endpoint Security authored by Michael Toback. Read the original post at: https://smallbizepp.com/mdm-for-small-business/?utm_source=rss&utm_medium=rss&utm_campaign=mdm-for-small-business
如有侵权请联系:admin#unsafe.sh
