
2023-10-8 01:0:0 Author: securityboulevard.com(查看原文) 阅读量:5 收藏

Introduction
In 2023, malware detection has never been more critical. As cyber threats evolve, understanding the latest techniques to identify and block malicious software is essential for safeguarding your digital assets. This article delves into how malware is detected. It describes the cutting-edge methods used in malware detection, offering you the knowledge you need to stay one step ahead of cybercriminals.
The Current State of Malware Threats
The landscape of malware threats is in constant flux, adapting to new technologies and security measures. In 2023, we’re witnessing an unprecedented surge in sophisticated malware attacks, targeting everything from individual devices to large-scale enterprise networks. This escalation not only poses a significant risk to data integrity but also impacts financial stability and public trust. As malware becomes increasingly complex, traditional detection methods are often rendered ineffective, making the need for advanced cybersecurity solutions more urgent than ever.
What is Malware? A Quick Refresher
Malware, short for malicious software, is a broad term that encompasses various types of software designed to harm, exploit, or otherwise compromise the functionality of computer systems. The primary types of malware include:
- Viruses: Attach themselves to clean files and spread throughout a computer system.
- Worms: Self-replicating programs that infect networks.
- Trojans: Disguised as legitimate software, they grant hackers unauthorized access.
- Ransomware: Encrypts files and demands payment for their release.
- Spyware: Collects sensitive information without user consent.
- Adware: Unwanted software that displays advertisements.
Understanding these types is the first step in effective malware detection and prevention.
How Malware Infects Your System
Cybercriminals employ a variety of tactics to infiltrate your system with malware. Some common methods include:
- Phishing Emails: Disguised as legitimate messages, these emails contain malicious attachments or links.
- Drive-By Downloads: Unintentional downloads that occur when visiting an infected website.
- Malvertising: Malicious ads that can install malware upon clicking.
- USB Drives: Infected external drives that spread malware when connected.
- Social Engineering: Manipulative tactics that trick users into revealing sensitive information or downloading malware.
- Exploit Kits: Tools that find and exploit vulnerabilities in your system to deliver malware.
Being aware of these tactics is crucial for effective malware detection and prevention.
Signature-Based Detection: The Classic Approach
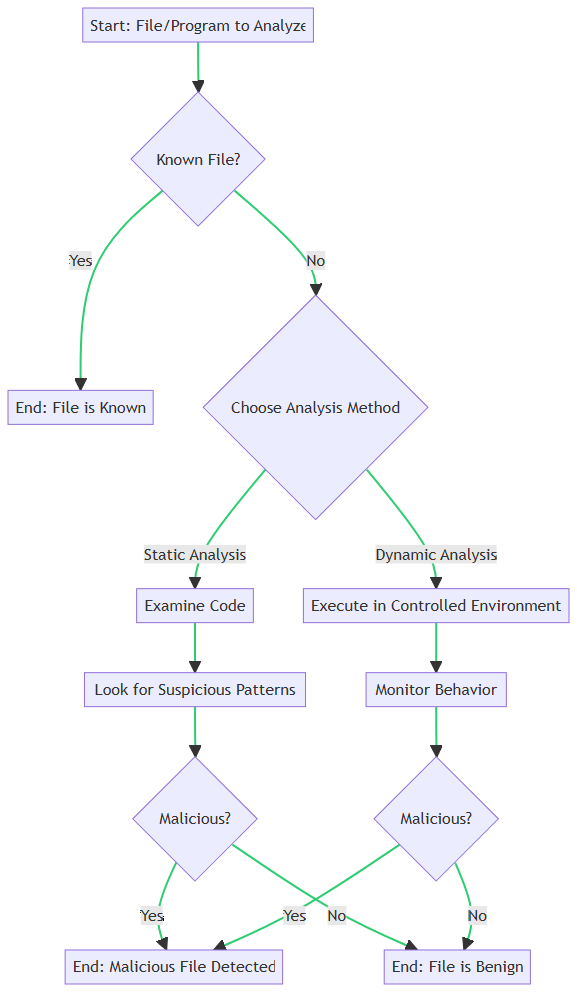
One of the oldest and most straightforward methods for detecting malware is signature-based detection. This technique relies on a database of known malware signatures—unique strings of data or characteristics of the malware file. When a file or program matches a signature in the database, it’s flagged as malicious. While effective against known threats, this method struggles with zero-day attacks and polymorphic malware, which constantly change their code to evade detection.
Static and Dynamic Analysis: A Deeper Look
Static and dynamic analysis are advanced techniques that go beyond signature-based detection.
- Static Analysis: Examines the code of a file before it’s executed. It looks for suspicious patterns or behaviors but doesn’t require the file to be run.
- Dynamic Analysis: Observes the behavior of a program while it’s in operation. This method is effective for detecting malware that evades static analysis.
Both methods have their pros and cons. Static analysis is faster but may miss complex threats. Dynamic analysis is more thorough but can be resource-intensive.
Machine Learning and Behavioral Analysis: The Future is Here
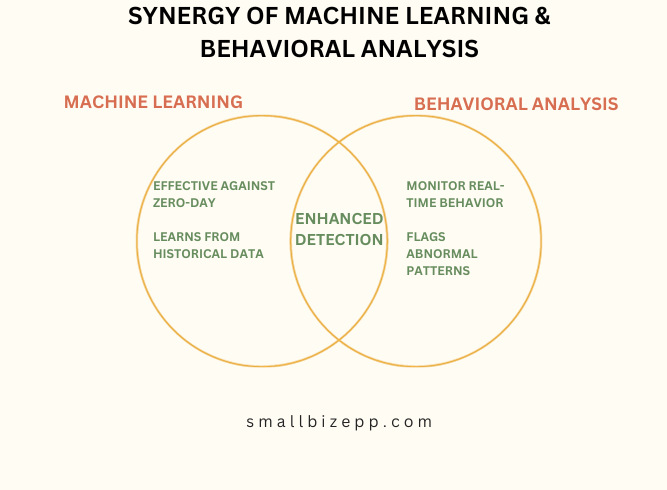
Machine learning and behavioral analysis are revolutionizing the field of malware detection. These cutting-edge techniques employ algorithms that learn from historical data and user behavior to predict and identify new malware threats.
- Machine Learning: Utilizes algorithms to analyze large datasets, learning to distinguish between benign and malicious activities. It’s particularly effective against zero-day attacks.
- Behavioral Analysis: Monitors system behavior in real-time, flagging any abnormal patterns that could indicate a malware infection.
These methods offer a more proactive approach, enabling quicker and more accurate malware detection, even for previously unknown threats.
Real-World Examples: Malware Detection in Action
WannaCry Ransomware Attack
On May 12, 2017, the WannaCry ransomware attack began, affecting hundreds of thousands of computers across the globe. Initially, traditional signature-based detection methods failed to identify this new variant of ransomware. However, by May 14, machine learning algorithms had adapted and started successfully identifying and mitigating the WannaCry threat. This case highlights the adaptability and speed of machine learning in malware detection.
Stuxnet Worm Discovery
The Stuxnet worm was discovered on June 17, 2010, targeting Iranian nuclear facilities. Behavioral analysis methods were employed, and by June 20, they had successfully detected the worm’s complex functionalities. The discovery and subsequent public awareness, announced on June 22, showcased the effectiveness of behavioral analysis against highly sophisticated and targeted malware threats.
These real-world examples provide invaluable insights into the effectiveness of various malware detection methods, especially when dealing with new or complex threats.
Endpoint Protection Platforms and Intrusion Detection Systems
Endpoint Protection Platforms (EPP) and Intrusion Detection Systems (IDS) play pivotal roles in fortifying cybersecurity measures, particularly in malware detection.
EPPs serve as the first line of defense, safeguarding individual devices like computers and smartphones. They employ a combination of signature-based, behavioral, and machine learning algorithms to detect and prevent malware attacks.
IDS, on the other hand, monitor network traffic for suspicious activities. They use pattern recognition and anomaly detection to identify potential malware threats, alerting administrators to take appropriate action.
Both EPP and IDS are integral components of a comprehensive cybersecurity strategy, offering layered protection against a wide range of malware threats. By working in tandem, they provide a more robust and adaptive malware detection framework.
Conclusion and Next Steps
In this article, we’ve delved into the intricacies of malware detection, from traditional methods like static and dynamic analysis to advanced techniques involving machine learning and behavioral analysis. We’ve also highlighted real-world examples that underscore the effectiveness of these methods. Endpoint Protection Platforms and Intrusion Detection Systems further fortify these strategies, offering layered protection against a myriad of malware threats.
We encourage you to share your thoughts and experiences in the comments below. Your insights could be invaluable to others navigating the complex landscape of malware detection in 2023.
The post How is Malware Detected in 2023? Uncover the Latest Techniques appeared first on Endpoint Security.
*** This is a Security Bloggers Network syndicated blog from Endpoint Security authored by Michael Toback. Read the original post at: https://smallbizepp.com/malware-detected/?utm_source=rss&utm_medium=rss&utm_campaign=malware-detected
如有侵权请联系:admin#unsafe.sh
