2023-10-11 00:0:0 Author: securityboulevard.com(查看原文) 阅读量:3 收藏
Introduction
As an API hacker, you should know vulnerability metrics like the Common Vulnerability Scoring System (CVSS). It is used to supply a qualitative measure of severity to vulnerabilities that you find and report.
CVSS is used to help organizations properly assess and prioritize their vulnerability management processes. In fact, during security triage, you may find yourself answering questions that are input into scoring your vulnerability by CVSS.
For example, HackerOne uses the CVSS v3 calculator to distinguish the severity of reports they triage.
But here’s a reality check for you. According to some research, vendors can only fix between 5% and 20% of the vulnerabilities reported to them in a given month. This means they must prioritize which vulnerabilities they can invest in fixing.
CVSS can’t answer that for them. Sure, a higher score may prioritize some decisions. But the fact is that there are too many bugs to tackle everything.
This is where the Exploit Prediction Scoring System (EPSS) comes in.

Understanding the Exploit Prediction Scoring System (EPSS)
The Exploit Prediction Scoring System (EPSS) is a metric designed to predict the likelihood that a particular vulnerability will be exploited in the wild within the next 30 days.
Unlike CVSS, which provides a static severity score based on the characteristics of a vulnerability, EPSS offers a dynamic prediction that evolves over time based on real-world observations and data.
With EPSS, security teams can add an additional layer of intelligence to their vulnerability management decisions, prioritizing fixes for those vulnerabilities that are not just severe but also likely to be exploited by attackers.
And this makes sense. History has shown that only 2% to 7% of the published vulnerabilities are actually ever seen exploited in the wild.
Where CVSS attempts to assess a vulnerability’s severity, EPSS attempts to measure the probability that the vulnerability will be used in an exploit.
Here is an interesting graphic FIRST publishes about the EPSS model and its effectiveness against CVSS alone:

When it comes to API hacking, the relevance of the Exploit Prediction Scoring System (EPSS) cannot be overstated. As a gateway to an application’s logic, APIs are often lucrative targets for attackers. An API vulnerability could potentially expose sensitive data or allow unauthorized data manipulation.
The EPSS becomes crucial in this context, as it helps security teams predict which vulnerabilities are most likely to be exploited, enabling them to prioritize their remediation efforts accordingly. By using the EPSS, security teams can focus their resources on the API vulnerabilities that pose the most significant threat, thereby enhancing the security of the application and safeguarding it from potential breaches.
This strategic approach to vulnerability management is pivotal in fortifying an organization’s cyber defense strategy.
The Role of EPSS in API Security
The Exploit Prediction Scoring System (EPSS) has radically transformed the vulnerability management landscape by introducing an element of foresight. Unlike traditional systems that only measure the severity of a vulnerability, EPSS employs a predictive approach, estimating the probability of a vulnerability being exploited.
This forward-thinking model is made possible by utilizing machine learning algorithms that analyze historical data of exploits. By doing so, EPSS successfully identifies patterns and trends, contributing significantly to predicting future exploits.
EPSS’ predictive capabilities allow for an informed and strategic approach to API security. The ability to predict potential exploits provides an edge in fortifying defenses ahead of time.

By focusing on likely threats, organizations can efficiently use their resources and significantly decrease their risk exposure. Not only does EPSS enhance API security, but it also contributes to the organization’s broader cybersecurity strategy by fostering a proactive, data-driven, and risk-informed culture.
In an era where cyber threats are continuously evolving and escalating, the predictive capabilities of EPSS are an invaluable tool in enhancing API security. It provides a robust defense mechanism that is not just reactive but also proactive, leading the way in modern vulnerability management.
Leveraging EPSS for Effective API Hacking
Leveraging EPSS effectively requires integrating it within your API hacking methodology. To do this, regularly incorporate the EPSS score into your vulnerability management workflows. Keep track of the vulnerabilities with high EPSS scores and prioritize them.
This in itself may surprise you. For many API hackers, especially those that focus on bug bounties, this sort of investment in time and effort is hard to come to terms with. I actually covered this previously in my article on when bug bounty hunters should give up on an API target. You have to “go deep” and learn how the API is built and used and what vulnerabilities it may be susceptible to.
Tracking the languages and components used can give you a leg up when conducting API security testing.
Keep track of API components
If you read my article on how to leverage SBOMs to attack APIs, you know that keeping track of the libraries, frameworks, and dependencies of an API can help you find the maximum window of exposure for a vulnerability. Tools published by OWASP, like the Dependency Tracker, can help with this. And since Dependency Tracker already has EPSS built in, it will help with exploit prediction and offer impact analysis at the same time to help you decide where to be looking first.

Establish a protocol for reviewing EPSS updates. The predictive nature of EPSS means that scores can change as more data becomes available. Regularly reviewing these updates will ensure you are aware of any changes in risk trends.
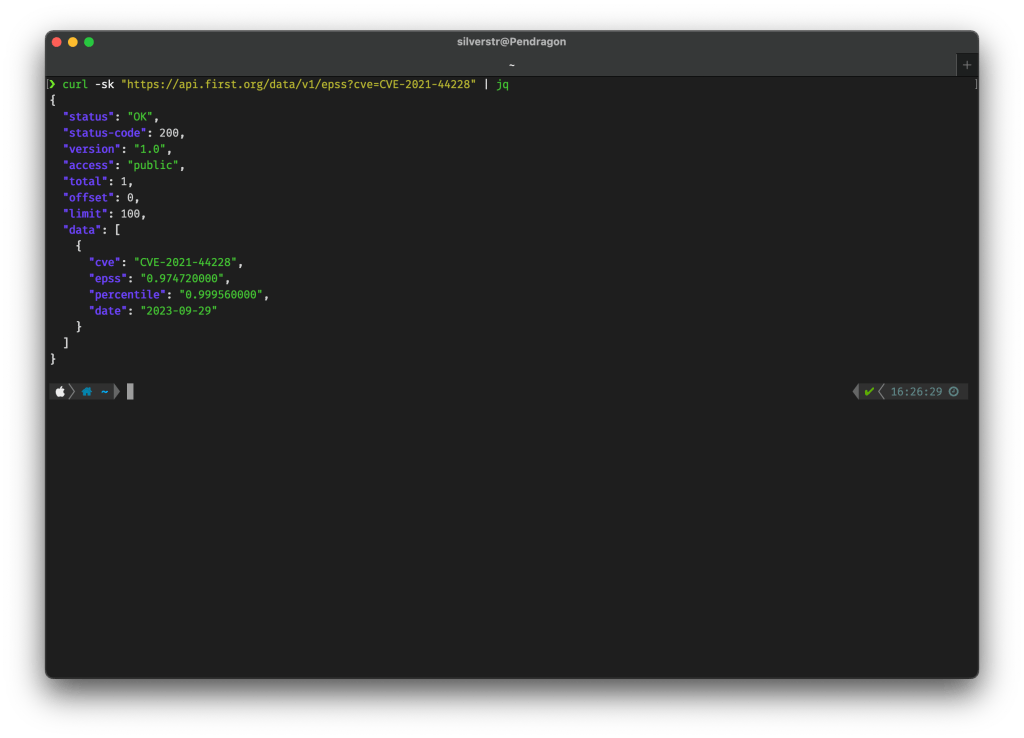
You can even leverage the EPSS API to stay on top of this. For example, as you track particular CVEs, you can query the EPSS API and pull back its severity and predicted exploitability. Here is an example check against CVE-2021-44228 (Log4J):

Consider your exploit score in the context of your target environment
Consider the EPSS score in the context of your target APIs’ specific environment. Not all vulnerabilities carry the same risks in every context; some might be more or less severe depending on the specifics of your API and how it’s used.
Consider also how your target API is integrated with other systems and what potential impacts a vulnerability may have on them. This will help you determine the best approach for prioritizing security testing.
One fun way to stay on top of this is to use sites like cvsdetails.com and look for delta changes to EPSS scores that affect you. Here is an example query that shows all CVEs whose EPSS score increased by over 10% from the original report.

Cross-referencing EPSS and the CISA KEV Catalog
There is a direct correlation between EPSS scoring and the CISA Known Exploited Vulnerabilities (KEV) catalog. The CISA catalog identifies the known attempts to exploit a specific vulnerability and their success metrics. By cross-referencing your EPSS findings with the KEV catalog, you’ll be able to identify CVEs that are not only exploitable but actively being exploited.
This information can help shape your API attack plans. Also, keep an eye on the CISA Vulnerability Bulletins for the latest information on known vulnerabilities and potential exploits. By staying informed about active threats, you can prioritize your security testing efforts accordingly.
BTW, there is a dedicated query for this on cvedetails.com as well.

Use insights to drive pentest efforts
Use the insights gained from EPSS to inform your penetration testing efforts. Prioritize potential exploits predicted by EPSS when conducting security tests. This approach will help align your testing strategy with real-world threat trends, making it more effective and efficient.
Through these steps, you can effectively integrate EPSS into your API hacking methodology, allowing you to proactively manage vulnerabilities and strengthen your API’s defenses.
Prioritizing CVEs with EPSS
There was a great presentation at BSides Dublin by Yahoo’s TheParanoids on using decision trees (ala SSVC) along with EPSS and other data sources to prioritize risk. They also shared a GitHub repo for a risk-based prioritization taxonomy for prioritizing CVEs (Common Vulnerabilities and Exposures).
You can watch their presentation on YouTube here:
Conclusion
The Exploit Prediction Scoring System (EPSS) is a crucial tool in API hacking, allowing you to forecast potential exploits accurately and adapt your testing strategies accordingly. The EPSS not only helps identify possible vulnerabilities but also aids in prioritizing where security testing should be done based on real-world trends.
This proactive approach to API security testing is important as it permits organizations to stay ahead of potential risks, thereby strengthening their defenses against cyber-attacks. Leveraging EPSS with other tools and assessments, such as CVE prioritization, can provide a comprehensive and robust API security strategy.

Looking ahead, the surge in machine learning and artificial intelligence use in API security will only increase. By leveraging these technologies, security teams will be able to automate vulnerability detection, making the process faster and more efficient. EPSS will be critical as it can provide the necessary data for these systems to learn from and adapt to.
This will lead to a shift towards more proactive API security strategies. Rather than reacting to breaches after they occur, organizations will focus on predicting and preventing them. The predictive abilities of EPSS will be integral to these proactive measures, enabling you to anticipate potential threats, test for them, and mitigate them before they become an issue.
The role of EPSS in future API security trends will be significant. It will be at the forefront of new technologies, proactive strategies, and integration efforts, aiding security teams in their ongoing battle against cyber threats.
As an API hacker, it’s important you understand EPSS so you can adapt and leverage it as an input into your API hacking methodology. If you don’t, it won’t be too long before some new security vendor tries selling your CTO on replacing you with it.
One last thing…

The API Hacker Inner Circle continues to grow. It’s my FREE weekly newsletter where I share articles like this, along with pro tips, industry insights, and community news that I don’t tend to share publicly. If you haven’t yet, join us by subscribing at https://apihacker.blog.
The post What API hackers need to know about the Exploit Prediction Scoring System appeared first on Dana Epp's Blog.
*** This is a Security Bloggers Network syndicated blog from Dana Epp's Blog authored by Dana Epp. Read the original post at: https://danaepp.com/exploit-prediction-scoring-system
如有侵权请联系:admin#unsafe.sh
