Quishing is phishing using QR (Quick Response) codes. QR codes are basically two-dimensional barcodes that hold encoded data, and they can be used to work as a link. Point your phone's camera at a QR code and it will ask you if you want to visit the link.
The use of QR codes in malicious campaigns is not new, and because they can provide contactless access to a product or service they grew in popularity during the Covid-19 pandemic.
In August, 2023 we wrote about an email campaign that used QR codes to phish for Microsoft credentials. The links in the QR codes redirected from legitimate domains associated with Bing, Salesforce, and Cloudflare to send the targets to phishing sites that were after Microsoft credentials. Since the subject of the emails were often fake Microsoft security notifications, the Bing URLs would not have looked out of place to any victims who gave them a cursory examination.
Lately, there has been an increase in quishing emails, which either send victims to malware-infested sites or ones looking for credentials.
The usual methods are used to make the emails look convincing: The email will pretend to come from a bank or another organization you trust, or might look like internal mails from the organization you work for, perhaps pretending to come from HR or the IT department. The QR codes in these mails are either embedded or sent as an attachment.
Most of the email contains little to no text, which reduces the chances of the scammer making a mistake and gives spam filters less to read. The message is displayed in an image, which also helps the email get through spam filters.
Example
I personally received a quishing mail pretending to be from the KVK (the Dutch Chamber of Commerce), telling me I had to request a digital key within the next 3 days or my company would be registered as inactive.

As you can see, a lot of the normal signs by which we can recognize a phishing mail are there:
- Urgency
- A link leading to a site to fill out personal information
- Sloppy lay-out of the mail
I was also able to recognize it as false because the sender address didn’t belong to the organization it claimed to be from.
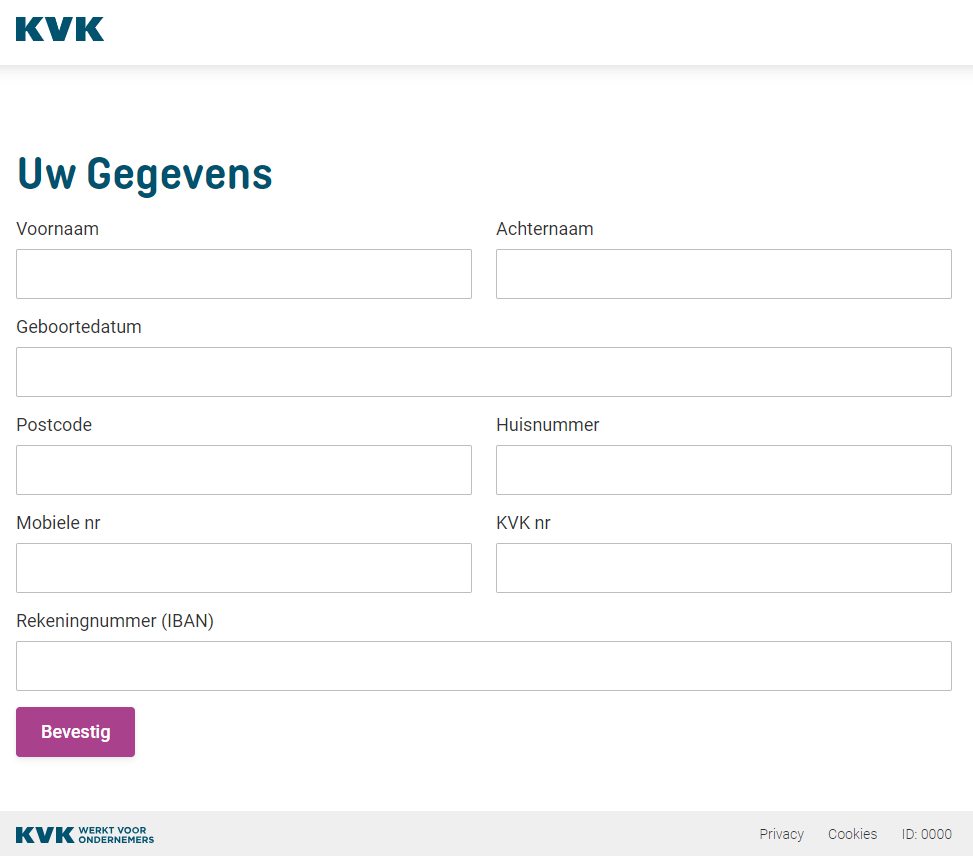
The QR code contained a link to the lihi1.com URL shortener which pointed me to a clone of the KVK site.

It asked for my name, birth date, address, mobile phone number, my KVK registration number and my bank account number. A succesfull phisher can probably sell that data for a few bucks on the dark web.
To stay safe from quishing, you can follow the same advice we provide for phishing, because that’s what it is. It's just that the method to obfuscate the phishing site is a bit more sophisticated, which also makes the use of it more suspicious.
One extra measure you can take is to install a QR code scanner that doesn’t take you to the destination in the URL, but displays it for you, so you can decide whether you want to proceed.
Stay alert for hallmarks of phishing campaigns, such as a sense of urgency, appeals to your emotions. Be extremely wary if a QR code takes you to a site that asks for personal information, login credentials or payment.
We don’t just report on threats—we remove them
Cybersecurity risks should never spread beyond a headline. Keep threats off your devices by downloading Malwarebytes today.