
2023-10-16 20:39:42 Author: securityboulevard.com(查看原文) 阅读量:3 收藏
Introduction
If you are an individual using Linux or one who has been a fan of Looney Tunes/Toons then do read further to find out how Looney Toons is a step away from taking down your Linux-based application and how Deepfactor helps you identify and prevent such exploits.
What is the glibc dynamic loader?
The GNU C Library, commonly known as glibc, comprises standard C library functions which serve as an interface for system calls related to file I/O, string manipulation, memory allocation, etc. in the Linux kernel. The dynamic loader ensures availability of all the shared libraries that the application requires and links them to the executable at runtime.
What is the use of the GLIBC_TUNABLES environment variable?
Tunables is a glibc feature that provides the capability of manipulating the runtime library behavior related to memory allocation, dynamic linking, hardware capabilities, etc., primarily using an environment variable GLIBC_TUNABLES. It expects : separated name=value pairs (<tunable1>=<val1>:<tunable2>:<val2>…) where name is a predefined/custom attribute which follows the format <top namespace>.<tunable namespace>.<tunable name>
Example:
glibc.malloc.mmap_max can be used to manipulate the maximum number of chunks that can be allocated using mmap
Default value: 65536
CVE-2023-4911 (Looney Tunables)?
A new vulnerability (CVE-2023-4911) was recently identified by the Qualys Threat Research Unit associated with the glibc dynamic loader processing logic of the GLIBC_TUNABLES environment variable.
The buffer overflow vulnerability exists in the workflow where the dynamic loader parses the GLIBC_TUNABLES environment variable value and overrides the runtime library behavior. The parser typically trims dangerous SXID_ERASE security-level runtime library manipulations and only accepts SXID_IGNORE/NONE security level tunables. It goes for a toss though if the value of the environment variables does not follow the expected semantics.
Example: <tunable1>=<tunable2>=AAA
Assuming both tunable1 and tunable 2 have a security level SXID_ERASE, they should ideally be trimmed and no overriding of the runtime library behavior should take place. The bug instead results in a buffer overflow while parsing such values, giving an opportunity to hackers to eventually acquire root privileges, crash applications, and execute remote code.
Default installations of Fedora 37/38, Ubuntu 22.04/23.04, and Debian 12/13 are susceptible to this vulnerability but other Linux distributions could be potentially exploited as well. Alpine Linux remains an exception due to its use of musl libc instead of glibc.
Technical Details: https://www.qualys.com/2023/10/03/cve-2023-4911/looney-tunables-local-privilege-escalation-glibc-ld-so.txt
Is there a fix available?
The glibc library has been fixed for some of the linux distributions/versions as highlighted in:
- https://security-tracker.debian.org/tracker/CVE-2023-4911
- https://ubuntu.com/security/CVE-2023-4911
- https://access.redhat.com/security/cve/cve-2023-4911
- https://lists.fedoraproject.org/archives/list/[email protected]/message/4DBUQRRPB47TC3NJOUIBVWUGFHBJAFDL/
- https://lists.fedoraproject.org/archives/list/[email protected]/message/NDAQWHTSVOCOZ5K6KPIWKRT3JX4RTZUR/
- https://lists.fedoraproject.org/archives/list/[email protected]/message/DFG4P76UHHZEWQ26FWBXG76N2QLKKPZA/
An upgrade is necessary to patch the vulnerability.
How does Deepfactor help in identifying and preventing such issues?
Some of the questions that should be answered to tackle such issues include:
1) Is my application built on top of a vulnerable OS distribution?
Deepfactor can help identify the OS distribution associated with the application through the SCA scan and runtime monitoring capabilities.
2) Is my application composed of the vulnerable version of a package i.e is the package part of the SBOM (Software Bill Of Materials)? Are there exploits available in the wild for the identified vulnerability? Is a fix available?
Deepfactor SCA scans enable users to scan artifacts and in turn:
- Generate an SBOM
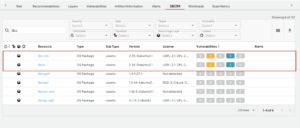

- Gather vulnerability insights i.e vulnerability metadata including CVSS scores, fix versions, exploitability information, upgrade recommendations
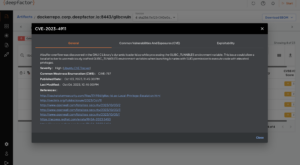
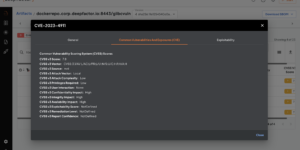
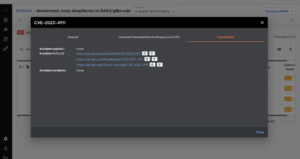
- Configure policy rules to detect and generate alerts in case of violations
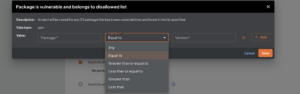
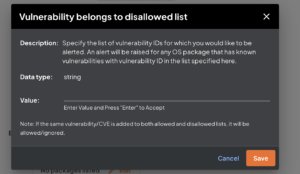
3) Is my application using the vulnerable package at runtime? Is it being loaded into the memory and executed?
Deepfactor runtime instrumentation for container, non-container and Kubernetes workloads monitors applications at runtime. It highlights instances of packages being loaded and executed along with a bunch of useful security insights.
The runtime and SCA correlation capabilities help us answer the question related to what the application is composed of and what is actually being used, which in turn simplifies vulnerability prioritization.
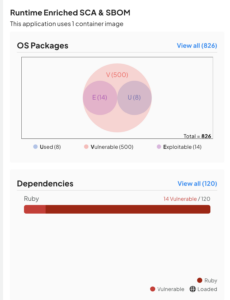
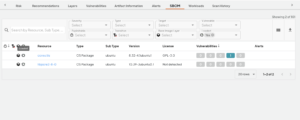
4) Does the application include a process running with elevated privileges? Does the application use buffer overflow APIs? Is there an occurrence of a remote code execution?
Deepfactor runtime security insights, along with the ability to use predefined and custom policies, enables it to detect such issues.

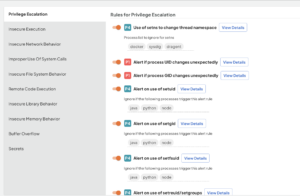
5) Are there instances of unexpected environment variable manipulation at runtime which suggest potential exploit attempts?
Deepfactor’s runtime security insights, along with the ability to use predefined and custom policies, enables it to detect such issues.
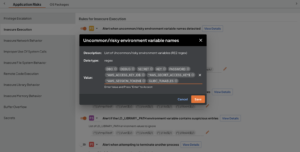
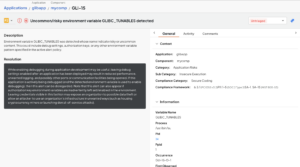
Deepfactor can help answer these and many other related questions. Deepfactor is a new approach to AppSec that combines SBOM, software composition analysis, container scans, and container runtime security into a powerful integrated platform.
The post Looney Tunables? CVE-2023-4911? You might be using a vulnerable Linux distribution. appeared first on Deepfactor.
*** This is a Security Bloggers Network syndicated blog from Deepfactor authored by Naman Tandon. Read the original post at: https://www.deepfactor.io/looney-tunables-cve-2023-4911-you-might-be-using-a-vulnerable-linux-distribution/
如有侵权请联系:admin#unsafe.sh
