Today I’ll be doing (as the title says) unconventional hacking with a phone. I will be using some tool(s), the most complicated of which being radare2 and with the power of an android I will use radare2 to reverse engineer something in order to obtain a password. I won’t go through the whole thing, just a simple demo. First thing’s first, fire up our terminal and get started:
Ok, now after entering that command, we will begin our decent into the disassembly process
We can see the word “radare2” printed in plain text at 0x9fd and since the program asks us to enter a password, we will try this for the first key.
Now the program asks us for a second password, I won’t give the exact answer but I will show where to locate it and go on to say that you may open a new session to again use radare2 to obtain the second key. As for the third key, find that on your own
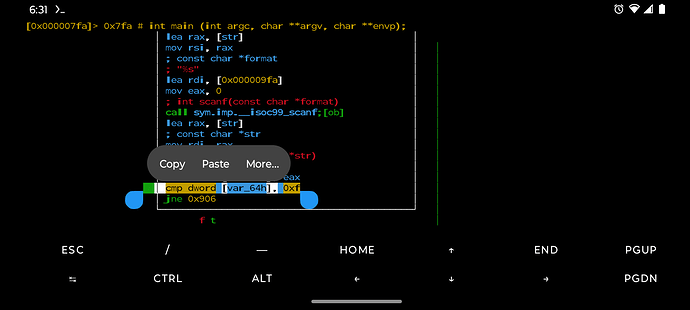
For those who don’t know assembly language too well, we know the password has something to do with the above highlighted section as it is comparing our input which is the [var_64h] and we know this is a string of comparison because of the cmp at the beginning of it.
Good luck, and hope all can have fun and learn not only hacking with a conventional PC or laptop, but also take the time to learn the unconventional and more difficult challenges of using a cellular device to do so