2023-10-23 02:33:0 Author: www.boredhackerblog.info(查看原文) 阅读量:22 收藏
I came across this during a pentest. The techniques mentioned here are not new and there are already some detections in place but I don't see these techniques being used regularly...
Command redirection
The concept of redirection for command line is well known and is commonly used. (This should provide more info: https://ss64.com/nt/syntax-redirection.html)
For example, you can do `COMMAND > output.txt` to save output from a command.
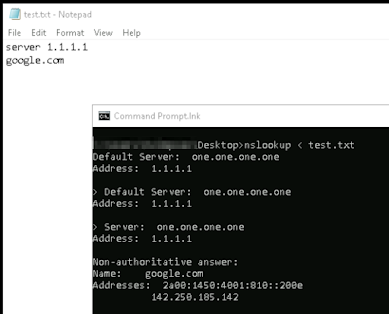
There is also `<` where you can pass input from a file to an interactive binary or executable.
Additionally, you can also do | to pass input to a binary.
Here are examples:
The redirection technique using < is what I observed during an alert from a pentest.
Essentially, the attacker added their commands for ntds dump to a text file then passed the text file to ntdsutil.exe using <. so `ntdsutil < filewithcommands.txt`
Usually, this is what you may see: ntdsutil.exe 'ac i ntds' 'ifm' 'create full c:\temp' q q
If your detections are looking specifically for command w/ "ac i ntds" and "create full" and the attacker uses the redirection technique, you may miss a detection.
There are sigma rules here that would and wouldn't miss this: https://detection.fyi/search/?query=ntdsutil
I just thought it was interesting for the attacker to write commands to text file and dump ntds.dit this way since I've never seen it being done like that.
Rundll32 w/ ordinals
This once again is not new. If you've done malware analysis, you've probably seen dll functions being called by the ordinal #.
Essentially, you can call a function by ordinal instead of the function name.
These articles should explain the concept better:
https://www.pcmatic.com/blog/running-dll-files-malware-analysis/
Here's an example:
instead of using LaunchApplication, I can use #1 as that's the ordinal.
The way this technique was abused during pentest was for lsass dump. The attacker used rundll32 w/ C:\windows\System32\comsvcs.dll to dump lsass.
Typical command you'll see for this is ".\rundll32.exe C:\windows\System32\comsvcs.dll, MiniDump 624 C:\temp\lsass.dmp full"
If we go look at comsvcs.dll and for MiniDump, we'll see MiniDumpW at 18 (hex -> decimal would be 24)
Instead of writing MiniDump with comsvcs.dll in rundll32, the attacker replaced it with #24. If you're looking specifically for comsvcs and minidump, the rule would miss this. Again, this was the first time I've seen someone do lsass dump this specific way.
There are some rules here that would and wouldn't detection this technique: https://detection.fyi/search/?query=comsvcs
Just wrote this to share and to keep this in mind when looking at alerts, hunting, or writing detections.
This assumes you only have 4688/command line logs. I'm aware that there are other ways to detect this activity but 🧂 sometimes you're lucky to even have 4688. 🧂 (yeah I work for a managed security provider)
https://twitter.com/cyb3rops/status/1389592014812024843
https://www.linkedin.com/posts/the-cyber-security-hub_activity-6909066000407633921-jVZQ
如有侵权请联系:admin#unsafe.sh




