![]()
One of the main responsibilities of DevOps teams is to build the cloud infrastructure businesses need as quickly and efficiently as possible. This focus on speed drives cloud operations to create and use automation wherever possible, which is why, in cloud environments, there are myriad identities with access permissions that far exceed any set of identities required in on-premises environments.
Shadow Access: The Evolution of Shadow IT in Cloud Environments
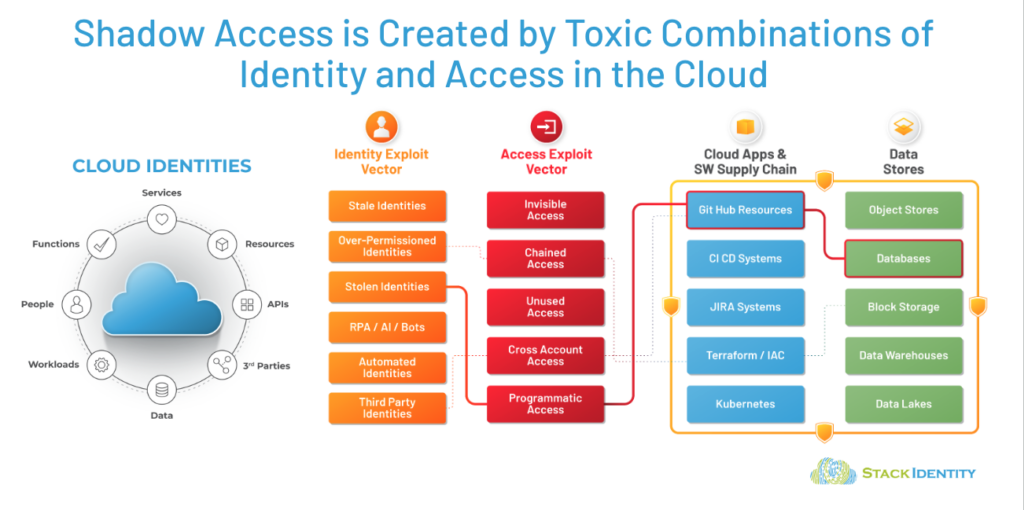
The speed and automation of cloud operations inherently introduce a large number of unmonitored identities and corresponding access permissions that are often spun up and then either forgotten about or that are invisible from the start. This leaves SecOps teams in the dark while trying to secure enterprise environments.
There is a new industry term that describes this phenomenon, which captures the cloud security risk generated by the dynamically changing identities and access patterns in the cloud: Shadow access.
Shadow access, akin to Shadow IT, is a struggle for organizations to understand, much less to manage and control. Shadow Access is the evolution of Shadow IT in a cloud-native world.
Cloud Automation Inadvertently Creates Shadow Access
In the cloud, identities are automatically created for multiple purposes, for API access, third-party access and data sharing, along with the creation and management of workloads, services and resources. Because DevOps teams are continuously building new systems, with automated creation of infrastructure and identities, there is an ever-growing number of identities and associated access permissions.
At the same time, SecOps teams are left with limited visibility and control while being simultaneously tasked with the responsibility to reduce risk. They need to remove under-utilized identities and over-permissioned access but cannot rely on traditional identity and access management (IAM) solutions for the visibility, detection and remediation necessary, as existing tools are not designed to work at the pace and rate of change of cloud environments.
Toxic Combinations of Identities and Access Permissions Enabled Multiple Cloud Data Breaches
Shadow access generates a vast attack surface ungoverned and unmanaged by existing identity and access management (IAM) tools and processes. Stack Identity’s industry-first Shadow Access impact report shared real-world findings about how the 10 different types of shadow access can and have been exploited to breach cloud environments and exfiltrate data. Analysis of live cloud environments provided statistical results and findings:
● 96% of identities in the cloud are non-human, automatically generated by APIs, cloud workloads, data stores, microservices and other multi-cloud services, which means the majority of cloud identities are not managed by existing IAM and governance tools and processes
● 28% of policies in the cloud have some level of permission management and 75% of policies used in cloud environments include write permissions. That means there are large gaps through which organizations can suffer cloud breaches, intellectual property and sensitive data loss
● In live environments, shadow access enabled an S3 bucket to be used for cryptomining and malware hosting, enabled a Lambda function to be replaced with malicious code and enabled the LastPass data breach.