2023-10-26 21:0:18 Author: unit42.paloaltonetworks.com(查看原文) 阅读量:20 收藏

This post is also available in: 日本語 (Japanese)
Executive Summary
In this article, we’ll explore the use of pluggable authentication module (PAM) application programming interfaces (APIs) in malicious software. We’ll also demonstrate why keeping an eye on PAM APIs in a sandboxed environment could be useful.
PAM is a widely used framework for authentication and authorization on Linux systems. Many popular applications and services on Linux systems rely on PAM and use its APIs for authentication, which includes SSH service, GNOME Display Manager (GDM) and system services such as sudo.
The flexible and modular design of PAM makes it an attractive target for attackers, who seek to leverage PAM APIs in malware as a way to intercept or manipulate the authentication process.
Advanced WildFire for Linux monitors and logs PAM API usage for ensuring that potential security threats like credential access are identified and addressed promptly.
| Related Unit 42 Topics | Sandbox, Linux |
Table of Contents
PAM API Usage in Malware
Orbit malware
Azazel rootkit
Derusbi malware
Skidmap malware
Conclusion
Advanced WildFire PAM Activity Capture
Indicators of Compromise
Introduction
PAM is a flexible and modular authentication framework for Linux systems, which provides a unified method to manage user access and authorization. The modular design of PAM is based on the concept of pluggable modules, which are shared object libraries that handle specific authentication and authorization tasks. These modules can be developed independently and plugged into the PAM framework to extend its functionality.
One example of a PAM module is pam_unix, which is a shared object library that handles authentication and authorization tasks using traditional Unix-style password files (/etc/passwd and /etc/shadow). This module can be plugged into the PAM framework, allowing applications to authenticate users based on their Unix passwords.
The PAM framework consists of a central library (libpam) that communicates with various PAM modules. Applications that require authentication or authorization, interact with the central library using PAM APIs, which then delegates the tasks to the appropriate modules. In short, libpam is responsible for loading and managing PAM modules (such as pam_unix.so) and facilitating communication between applications and the PAM modules.
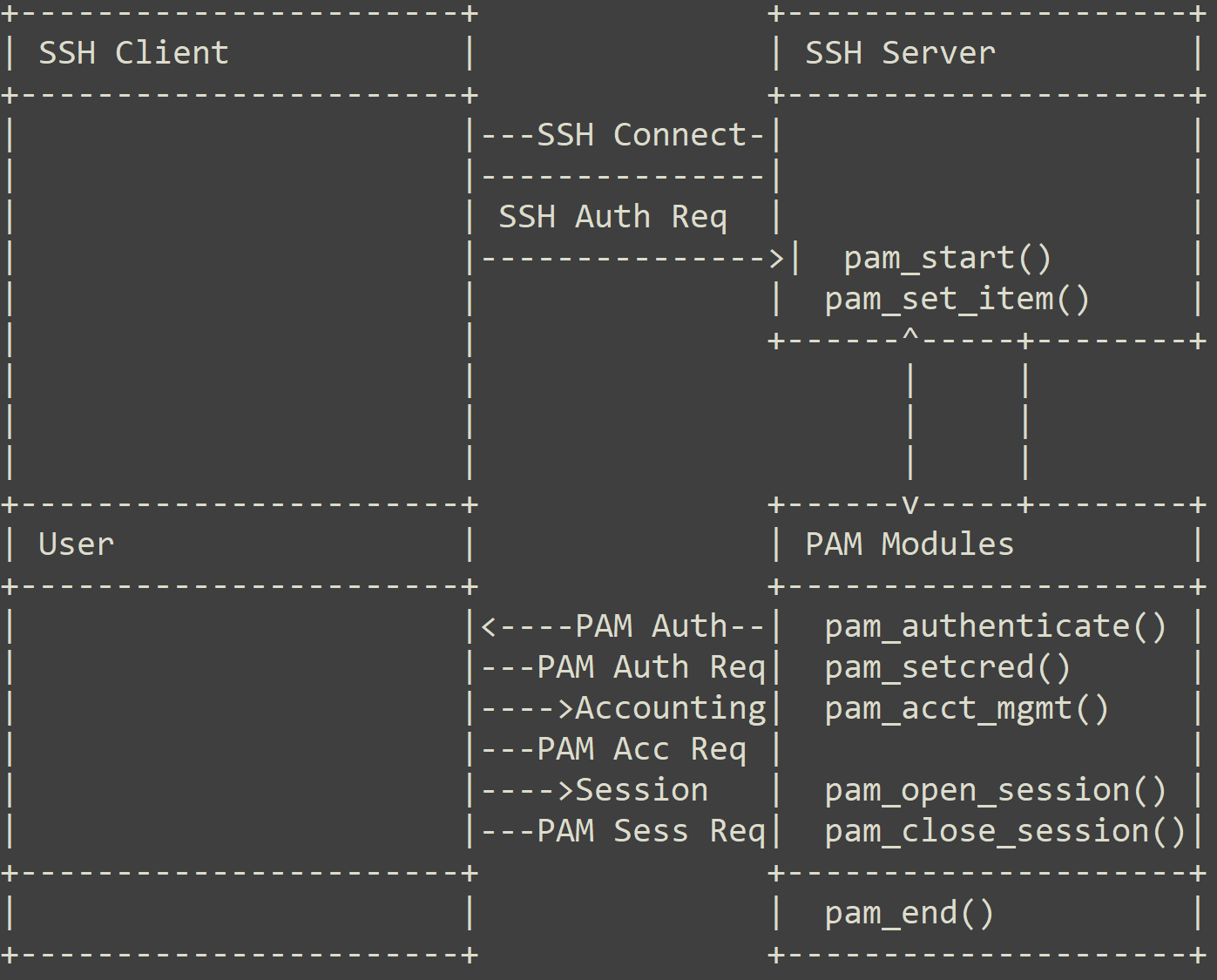
Numerous widely-used applications and services within Linux systems depend on PAM, utilizing its APIs for authentication. These encompass the SSH service, GNOME Display Manager (GDM), and system services like sudo. Figure 1 shows the authentication process for SSH utilizing PAM.
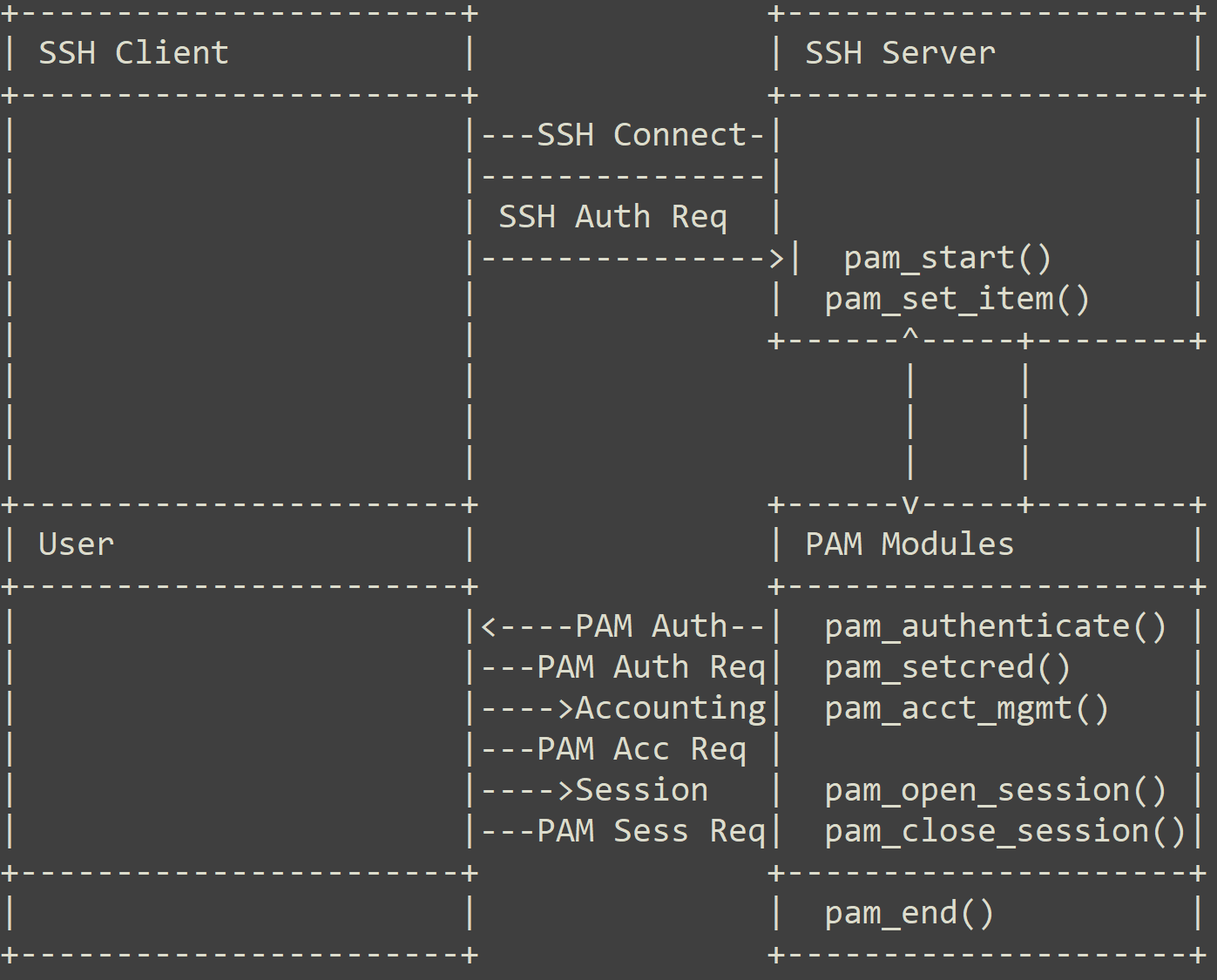
Attackers have used the modularity and flexibility of PAM to intercept or manipulate the authentication process. Malware has leveraged PAM APIs to compromise victim systems’ security.
PAM API Usage in Malware
The following are some malware families that have used PAM APIs for logging user credentials and establishing remote access.
Orbit malware
The Orbit malware was discovered in 2022. It hooks various shared object libraries’ APIs, including PAM APIs. The Orbit malware’s payload hooks pam_open_session, pam_authenticate and pam_acct_mgmt() APIs to log the victim’s SSH password in a file.
The pam_open_session() API initiates a new session for the user upon successful authentication. The pam_authenticate() API handles the user authentication process, and the pam_acct_mgmt() API manages user account information, such as checking if the account is expired or if the user is allowed to access the system at a specific time.
Azazel rootkit
Azazel rootkit is an open-source rootkit that targets older Linux kernels. Azazel is based on the LD_PRELOAD technique. Figure 2 shows how the rootkit uses PAM APIs (pam_open_session, pam_authenticate and pam_acct_mgmt()) to allow remote entry into the victim’s machine.
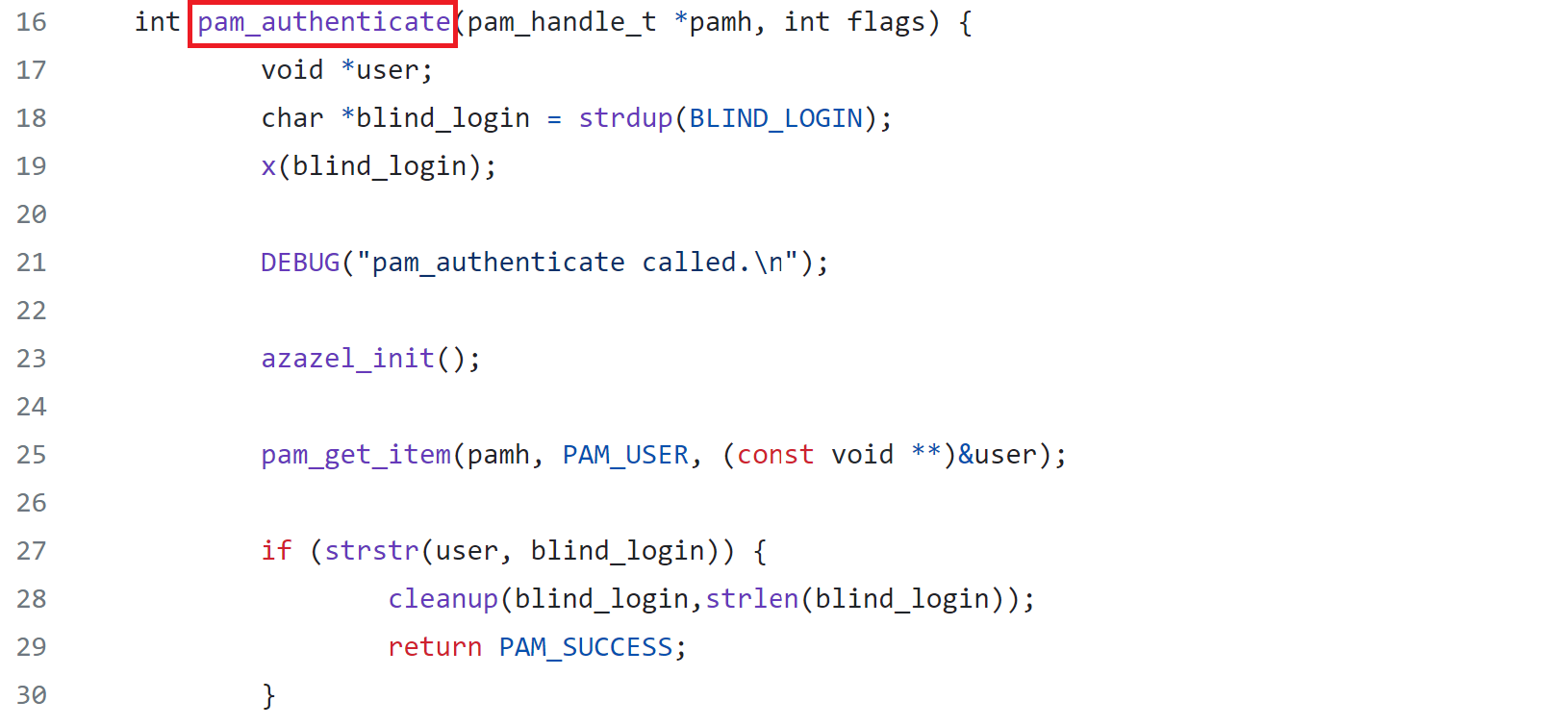
Derusbi malware
Derusbi is a malware family known for targeting both Linux and Windows systems. Threat operators primarily use Derusbi for gaining and maintaining remote access to targeted systems, allowing attackers to steal sensitive information, conduct reconnaissance and perform other malicious activities. The Derusbi malware also employs the LD_PRELOAD technique to load the malicious shared object library, which exports PAM APIs.
Skidmap malware
Skidmap malware was first seen in 2019 and primarily targets Linux systems for cryptomining. To gain access to the victim machine, Skidmap replaces the legitimate pam_unix.so library with a malicious one. The malicious pam_unix.so file accepts a specific password for any user, thus allowing the attackers to log in as any user in the machine.
Conclusion
PAM is a critical component in the Linux system because it offers a standardized, flexible, modular and secure framework for user authentication. Keeping an eye on PAM APIs in a sandboxed environment is crucial for maintaining a secure authentication system and protecting sensitive data.
In a secure and isolated environment, monitoring the PAM API with other potentially suspicious activities can aid in detecting malicious attempts that try to tamper with the authentication process through PAM APIs. By closely observing usage of the LD_PRELOAD environment variable and other related events, you can pinpoint instances where attackers might be trying to interfere with the authentication process by using PAM APIs.
Advanced WildFire PAM Activity Capture
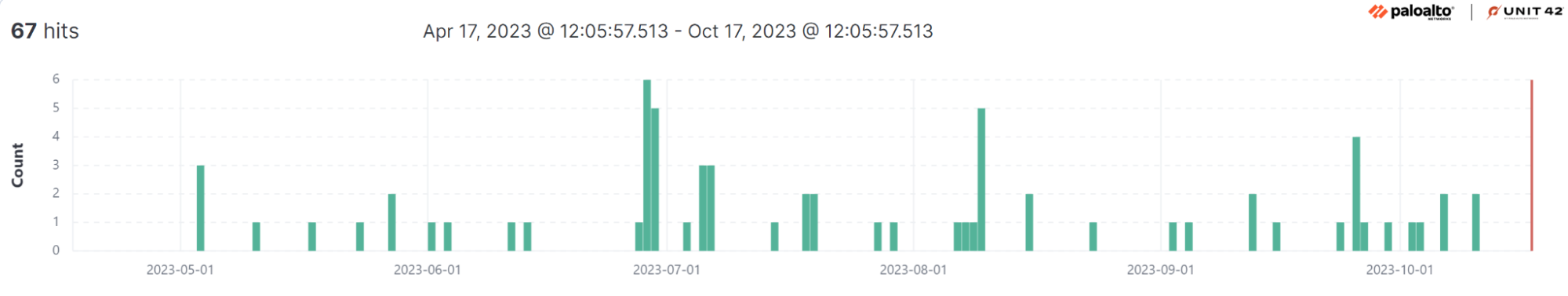
Palo Alto Networks Advanced WildFire for Linux monitors and logs PAM API usage to ensure that potential security threats like credential access are identified and addressed promptly. The graph in Figure 3 shows the occurrence of malware (over the course of six months) detected by WildFire that use PAM APIs.
Palo Alto Networks has shared our findings, including file samples and indicators of compromise, with our fellow Cyber Threat Alliance (CTA) members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. Learn more about the Cyber Threat Alliance.
Indicators of Compromise
Azazel malware family
- SHA256 hash: 2ad5993cf4db52ef72e299590d79dd7414bc3b119f5d8be8274ad89bec4cbbae
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
如有侵权请联系:admin#unsafe.sh