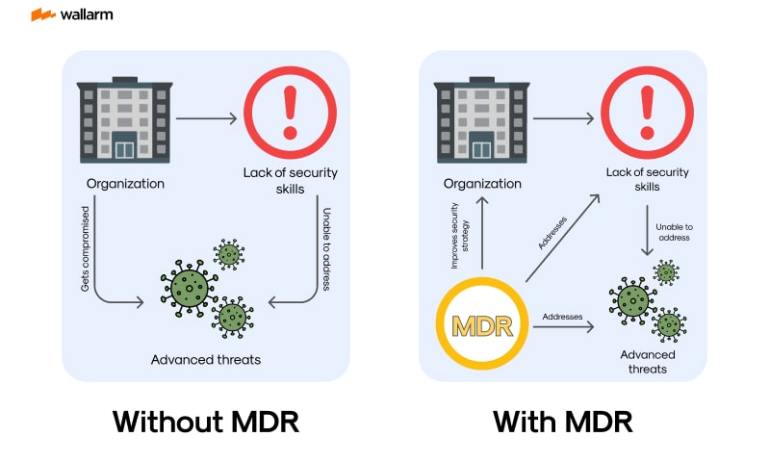
Gaining Insight: Decoding MDR's Functions
As we navigate the continually evolving cybersecurity landscape, Managed Detection and Response (MDR) surfaces as a game-changing strategy. But, what does MDR truly signify? In its purest form, MDR marries technical expertise with sector-specific knowledge to arm companies with effective strategies for pinpointing, examining, and sorting prospective security breaches. This all-encompassing security approach transcends conventional paradigms and provides a more extensive digital obstacle against potential vulnerabilities.
Digging deeper into the MDR strategy:

-
Management: A specialist external agency is in charge, managing all facets of threat detection and response. Such management includes uninterrupted surveillance, threat cognizance, incident orchestration, and more.
-
Identification: This aspect pertains to noticing impending threats or cyber incursions on an organization's network. The focus here is on a preventive stance rather than a reactive one—heading off security risks before they can wreak havoc.
-
Reactions: This portion relates to the actions taken subsequent to a threat's detection. It might involve cordoning off the impacted systems, eradicating the menace, and reinstating routine business operations. It also entails gleaning learnings from the incident to thwart similar incursions reciprocating attacks in the future.
MDR isn't synonymous with a singular tool or technology. Instead, it is an amalgamation of multiple services strategically designed to create a comprehensive security contour. This includes components like advanced data analysis, threat understanding, ongoing surveillance, and the capability to administer incidents.
Below is a comparison to illustrate how MDR departs from standard security measures:

| Standard Security Measures | MDR |
|---|---|
| Responsive attitude | Preventive attitude |
| Emphasis on thwarting | Emphasis on discovery and reaction |
| Confined to regular business hours | Round-the-clock surveillance |
| Adheres to preset protocols | Utilizes superior analytics and threat cognizance |
| Manual incident management | Balanced use of automation and manual interventions |
Primarily, MDR is about addressing threats at their origination point before they escalate into full-blown incursions, reacting promptly and effectively to minimize harm. It champions a contemporary, holistic cybersecurity approach, proffering sturdy protection in an ever-changing cyber threat domain.
Assessing the Importance of Proactive Defense Systems in Our Digital Age
In an era where data has become a precious commodity sometimes referred to as the new oil, it's of utmost importance for businesses worldwide to adequately protect this valuable asset from digital predators. It is here when a proactive method like Proactive Defense Systems (PDS- an alternate term for MDR) underlines its importance. PDS is not a mere buzzword in the realm of information protection; it acts as a bedrock in establishing and preserving a company's digital fortresses.
Surveying the prevailing landscape of cyber hazards can further underscore the significance of PDS. A study released by NormShield Cybersecurity Forecast (an alternative for Cybersecurity Ventures) predicted that by 2021, the worldwide annual cost related to cybercrime could hit $6 trillion, marking a notable climb from $3 trillion in 2015. This staggering escalation underscores the daunting challenge that the corporate sector is grappling with in the current times.
Against this backdrop, PDS introduces a comprehensive strategy to confront and overcome these dangers. It amalgamates latest-generation technology solutions with human discernment to promptly identify, examine and counteract potential threats. This dynamic game plan contrasts sharply with the traditional protective strategies, which typically focused on prevention and conformity with the regulatory norms.
The following points succinctly elucidate the necessity of PDS in the present cyber ambiance:
- Preemptive Threat Hunt: As opposed to passive anticipation of an attack — a method adopted by conventional security systems — PDS services actively traces looming threats within your virtual territory. This forward-looking strategy is engineered to detect and neutralize threats even before they can cause any significant damage.
<code class="language-python">#Typical Approach
def wait_for_invasion():
# Hold on until a threat appears
pass
# PDS Approach
def seek_out_danger():
# Vigorously identify likely threats
pass</code>
-
Perpetual Network Watch: Cyber intrusions are not bound by any standard time or day. They may surface anytime, even on days off and public festivals. PDS consistently guarantees the surveillance of your network to keep it safe around the clock.
-
Shared Expertise and Wisdom: PDS collaborates with units equipped with information safety professionals who hold an expansive gamut of skills and experience, competent enough to tackle a wide array of threats. By applying their specific talents, they can analyze threat-related data and respond competently.
-
Employing Progressive Techniques: PDS utilizes advanced methodologies such as artificial cognitive systems and automatic learning to identify and ward off threats. These advanced technologies are skilled at noting sequences and discrepancies that might indicate a violation of security.
-
Economically Feasible: Not all establishments are capable of bearing the financial burden associated with maintaining an in-house digital shield team. PDS steps up, providing top-tier services at an affordable price.
| Classical Security Measures | PDS Services |
|---|---|
| Wait-and-watch approach | Preemptive threat hunt |
| Restricted monitoring scope | Perpetual network watch |
| Requirement of in-house expertise | Access to proficient information safety units |
| Basic technological instruments | Progressive artificial cognitive and automatic learning methodologies |
| High costs | Economically viable |
In essence, PDS has a pivotal role in securing businesses in the modern digital domain by offering an adaptable, comprehensive, and budget-friendly solution against cyber threats. As these threats continue to evolve and exhibit more complexity in the future, the irreplaceable role of PDS Services will only strengthen.
Exploring in Depth the Functionality of MDR
The Managed Detection and Response (MDR) framework offers an intricate fusion of technological prowess, human aptitude, and procedural methodologies, facilitating robust cybersecurity coverage for enterprises. It's essential to disassemble this MDR mechanism into its underlying elements and scrutinize their synergy in preventing digital perils.
Technological Aspect: The engine driving any MDR strategy is its arsenal of technological assets. Such assets encapsulate innovative tools dedicated to detecting cyber threats, fortifying endpoints, reinforcing network defenses, and executing cybersecurity incident resolution. These ingenious applications aim to counteract threats, precluding them from inflicting substantial harm.
<code class="language-python"># Illustrative code showcasing a fundamental threat detection
algorithm
def find_threat(input_data):
for item in input_data:
if item['danger_grade'] > THRESHOLD:
return True
return False</code>
Human Talent: Despite the pivotal role of technology, MDR notably leans on the proficiency and cognizance of cybersecurity stalwarts. These experts oversee the system, dissect threat data, and dictate crucial strategies to handle potential breaches.
Procedural Blueprint: Underlying the MDR structure is an extensive procedure framework dictating the collaboration between human talent and technology. It warrants prompt threat identification, efficient response coordination, and seamless system functionality.
| Procedure | Explanation |
|---|---|
| Danger Identification | Spotting potential security dangers based on unusual behavioural patterns. |
| Incident Resolution | Engaging measures to contain recognized threats and suppress their influence. |
| Ongoing Surveillance | Vigilant system observation to detect shifts signalling potential danger. |
| Danger Intel | Accumulating and dissecting intelligence on possible threats to bolster the system's threat sensing and containment abilities. |
Considering the fundamental components of MDR, let's delve into their collective functionality.
Upon sensing possible threats, the MDR infrastructure escalates an alarm. Cybersecurity professionals investigate this alert, assess the data to verify the threat validity and potential severity, and, if required, launch a protocol to mitigate the threat and limit potential fallout.
The MDR infrastructure persistently surveils the network while gathering vital data. Such data refines the danger detection protocols, enhancing the system's overall efficacy.
In summation, the MDR framework orchestrates a delicate dance of technology, human acumen, and procedural methodologies. Their concerted efforts surpass conventional security provisions, offering superior cybersecurity resilience.
Our next chapter will delve into the instrumental role MDR plays in contemporary security architecture. Keep an eye out for it!
`
`
Interpreting the Quintessential Role of MDR in Present-day Safeguarding Structures
Presently, Managed Detection and Response (MDR) has attained considerable prominence amidst the matrix of safeguarding structures. Acknowledged as a dynamic procedure within the realm of cybersecurity, MDR adeptly amalgamates technology's capacity, human tact, and intelligent strategies, allowing for real-time detection, analysis, and mitigation of cyber threats. This chapter will delve into the pivotal aspects of MDR's role within the contemporary safeguarding regime, its significance and operations, thereby enhancing the protections against the cyber attack wave.
Instrumental to MDR is its commitment towards persistent alertness and tackling complex threats. It transcends traditional security strategies that chiefly aim at prevention, instigating a more predictive approach wherein threats are spotted before they inflict serious harm.
Consider this simple analogy: conventional security measures are like a locked door- whilst they can prevent unwelcome entrances, a skillful lock picker could enter undetected. On the other hand, MDR can be likened to an unwinking surveillance camera that vigilantly observes all activities, notifying security personnel at the detection of break-in attempts.
Here is a basic Python framework demonstrating MDR's workings:
<code class="language-python">class MDR:
def __init__(self):
self.detected_dangers = 0
def monitor(self, traffic_flow):
for information_packet in traffic_flow:
if self.spot_danger(information_packet):
self.detected_dangers += 1
self.neutralize_danger(information_packet)
def spot_danger(self, information_packet):
# Code for detecting danger should be written here
pass
def neutralize_danger(self, information_packet):
# Code for neutralizing danger should be written here
pass</code>
In the presented Python code, the MDR class continuously watches the flow of data, spotting and neutralizing dangers as they are discovered.
MDR's crucial aspects within the contemporary safeguarding framework can be divided into four main focus points:
-
Danger Recognition: MDR employs advanced data examination and computational learning to identify dangers that could slip past traditional security methods. These threats often include unrevealed software holes, intricate persistent threats (IPTs), and concealed internal dangers.
-
Danger Analysis: On discovering a danger, MDR meticulously investigates it to ascertain its nature and potential aftermath. This includes identifying the offender, acknowledging the exploited weakness, and understanding the possible fallout.
-
Danger Mitigation: MDR's abilities exceed merely spotting and analyzing threats- it also dynamically mitigates them. The responsive measures could encompass isolating affected systems, blacklisting malicious IP addresses, and setting in motion legal actions against the offenders.
-
24/7 Watch: MDR ensures round-the-clock surveillance over the safeguarding infrastructure, minimizing potential cyber harm through real-time danger detection and response.
To summarize, MDR plays a crucial role in the present-day safeguarding landscape, providing uninterrupted surveillance and swift response to threats, allowing businesses to maintain one step ahead of cyber offenders. With the escalating intricacy of cyber threats, the impact of MDR in the security regime is expected to gain preeminent importance exponentially.In the constantly evolving realm of internet safety, a hegemonic approach known as Managed Detection and Response (MDR) has made its entrance. However, is it up to the task when pitted against established security tactics? Let's delve into the differences and understand the unique facets of MDR.
Cinematographic style safeguards, including tools such as protective software-walls, virus defense programs, and intrusion recognition systems, have been the fortress in the battlefield of cyber protection for eons. They operate based on preset rules and identifiers to detect and neutralize familiar digital menaces. Unfortunately, these age-old instruments falter when faced with the growing intricacy of cyber threats.
In contrast, MDR personifies a predictive and holistic strategy for cyber defense. It blends cutting-edge tech applications with the astute rigor of human experts to spot, analyze, and diffuse digital threats swiftly.
Let's explore the core variations between MDR and the traditional methods:
-
Detection and Neutralization of Threats:
Standard Security Measures: Rely on identifier-oriented tactics that can only identify known threats, leaving them vulnerable to unfamiliar threats like zero-day intrusions and advanced consistent threats.
MDR: Incorporates trailblazing technologies like artificial intelligence (AI) and machine learning (ML) to identify a mixture of known and unforeseen threats. It offers a swift defense reaction to mitigate the fallout of a security infringement.
-
Protection Range:
Standard Security Measures: Bolster defenses at the periphery, primarily blocking invasions.
MDR: Promises extensive security, safeguarding networks, end-user devices, cloud platforms, and software applications. It not only obstructs but also detects and reverses threats permeating the holistic digital ecosystem.
-
Human Involvement:
Conventional Security Procedures: Rely heavily on automating processes, providing minute human intervention, which can result in erroneous alerts and overlooked threats.
MDR: Marries automated maneuvers with human perceptiveness. Cyber defense professionals constantly monitor the system, evaluate notifications, and perform necessary actions to disarm threats.
-
Threat Insight:
Conventional Security Procedures: Lack the ability to provide real-time threat knowledge.
MDR: Provides continual updates regarding emerging threats, helping businesses to maintain an edge over potential cyber malefactors.
To wrap up, while traditional security styles lay down a fundamental line of defense, MDR etches a comprehensive and proactive defense model. By merging state-of-the-art technology and human intelligence, MDR detects and neutralizes threats promptly, bestowing unrivaled safety against the modern-day variety of digital threats.
The Novice's Roadmap to Implementing MDR: A Step-By-Step Method
Integrating Managed Detection and Response (MDR) into your business's protection blueprint can be daunting, particularly for beginners. However, understanding the sequence of implementation and following a structured methodology, allows everyone to seamlessly infuse MDR within your security practices.
Here are the stages to prompt this voyage:
-
Identify Your Security Needs: Before entering the MDR domain, it's crucial to comprehend the specific security needs of your corporation. This involves identifying key assets, apprehending the threats they face, and gauging the level of risk your business can sustain.
-
Find the Ideal MDR Vendor: MDR vendors do not all provide an identical range of services. It's fundamental to select a supplier that can fulfil your distinct security needs, is budget-friendly, and aligns with your corporate principles. Prioritize vendors that ensure constant monitoring, threat detection, problem resolution, and regular upgrades.
-
Establish Your Protection Guidelines: Safety guidelines are roadmaps that guide how your enterprise responds to security complexities. These should be lucid and distributed to every employee. They should address things like authority control, data conservation, handling of security occurrences, and measures for data recovery after a disaster.
-
Implement the MDR System: After you've found a vendor and established your protection guidelines, it's time to implement the MDR system. This requires integrating the MDR software within your existing IT framework, personalizing the software to meet your security needs, and gauging the system's efficacy through audits.
-
Educate Your Team: Your workforce is an integral part of your security plan. Their training should include understanding how the MDR system operates, detecting and reporting security challenges, and adhering to your protection guidelines.
-
Assess and Enhance: After implementing the MDR system, it's vital to regularly evaluate its performance and make necessary improvements. This comprises analysing security logs, doing routine investigations, and staying abreast of emerging security threats and methodologies.
Here's a simplistic comparison to distinguish between conventional security tactics and MDR:
| Conventional Security Techniques | MDR |
|---|---|
| Defensive security approach | Proactive security approach |
| Limited sight of threats | Comprehensive view of threats |
| Manual resolution of security issues | Automated handling of security issues |
| Extensive dependence on internal resources | Supervised by an expert provider |
Here's a Python code sample to illustrate how an MDR solution could perpetually defend against security threats:
<code class="language-python">def maintain_security_with_mdr(mdr_system):
while True:
security_challenges = mdr_system.identify_incidents()
if security_challenges:
for challenge in security_challenges:
mdr_system.handle_challenge(challenge)</code>
Remember, MDR integration is not a one-time event. It's an ongoing activity involving regular evaluation, frequent updates, and readiness to adapt to the continually evolving cyber threat landscape. Despite the challenges, with a smart strategy and efficient resources, you can remarkably reinforce your business's capacity to repel cyber intrusions.
Investigating Practical Illustrations: Unveiling MDR Benefits for Companies?
In digital protection sphere, the Strategy of Monitored Defense and Reactions (MDR) has surfaced as a profound alternation in the trajectory for commercial ventures. To thoroughly comprehend the tangible impact of MDR, let's unfurl a few demonstrative instances of how corporations have harvested the advantages of this progressive protection strategy.
Instance 1: Monetary Consultancy Corporation
A moderately-scale financial advisory corporation was grappling with a flurry of digital violations. Despite having a conventional protection system installed, the corporation was ineffective in accurately identifying and tackling these intricate violations. Subsequently, the corporation opted to employ an MDR strategy and the results were striking.
The MDR solution provider's sophisticated violation identification capacities found a formerly unnoticed malicious software in the corporation’s network. The MDR crew rapidly segregated the compromised systems, averting the spread of Malicious software. The corporation seamlessly carried on its operations, circumventing plausible fiscal deficits and damage to its reputation.
Instance 2: Online Retail Firm
An online-based retail firm encountered difficulties in handling its protection operations due to an insufficiency of specialist personnel. The firm made a decision to collaborate with an MDR solution provider.
The MDR crew established a round-the-clock monitoring system, which became aware of a forceful unauthorized access made on the firm’s website. The MDR crew promptly retaliated by deactivating the IP locations linked with the unauthorized access. The firm successfully warded off a plausible data violation, ensuring the security of its clients' confidential data.
`
`
Instance 3: Medical Care Service
A medical care service was grappling with adherence issues related to the Health Coverage Portability and Accountability Regulation (HIPAA). The service opted to utilize MDR to ensure adherence and strengthen its defensive posture.
The MDR solution provider assisted the medical service in meeting HIPAA standards by establishing a robust protection infrastructure. The MDR crew also facilitated continuous monitoring and violation identification, assisting the service in averting potential cyber intrusions.
These tangible examples underscore the sizeable advantages of MDR, including:
-
Improved Violation Identification: The advanced violation identification capacities of MDR enable commercial ventures to find and tackle violations in real-time, avoiding possible infringements.
-
Adherence Assistance: MDR solution providers can assist enterprises in meeting adherence standards by establishing a solid protection infrastructure.
-
Fiscal Savings: By averting possible infringements, MDR can save enterprises from fiscal deficits linked with cyber intrusions.
-
Exposure to Proficiency: MDR solution providers offer corporations exposure to digital protection specialists, eradicating the necessity for in-house security teams.
In summary, MDR provides enterprises an anticipatory strategy to digital protection, enabling them to identify and tackle violations in real-time. By employing MDR, enterprises can boost their defense posture, fulfill adherence standards, and safeguard their precious assets.
如有侵权请联系:admin#unsafe.sh