2023-11-3 06:4:59 Author: securityboulevard.com(查看原文) 阅读量:3 收藏
Unraveling the Mysteries Behind the Zero Trust Network Access (ZTNA) Paradigm
Digital protection strategies have traditionally relied heavily on the concept of trust. However, these conventional notions, which assume a considerable measure of security within an organization’s connectivity sphere, often fail to efficiently navigate the complex terrains of modern digital ecosystems. Enter Zero Trust Network Access (ZTNA), a groundbreaking approach to network security.
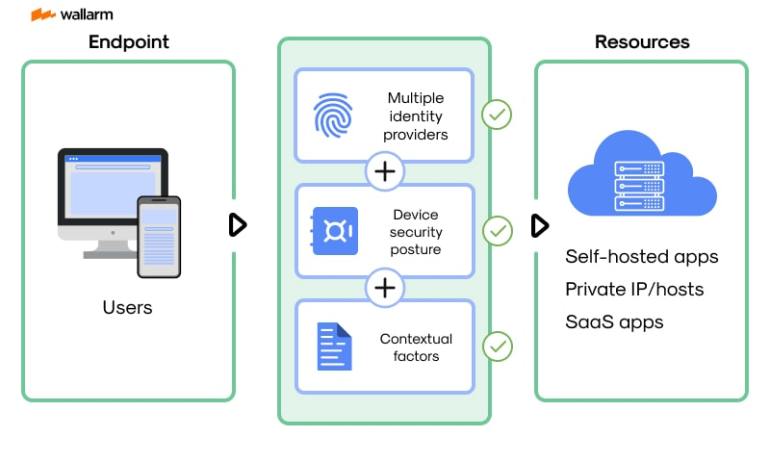
The innovative ZTNA model challenges the established trust dynamics within an organization’s machinery. Its core mantra can be summed up as "Trust nothing, validate perpetually". All attempts to access the network, regardless of the origin, are regarded as a possible security risk. This condition compels each access request to go through comprehensive validation before being granted.
The Zero Trust perspective represents a daring departure from long-standing security tactics. Instead of concentrating solely on shielding the network boundaries, it directs focus towards the safeguard of individual users and their corresponding network activities. This concept becomes even more crucial when faced with the complexities of remote working modes, cloud-centric infrastructures, and mobile application environments.
The dichotomy between established trust approaches and Zero Trust methodology is elaborated in the table below:
| Established Trust Perspective | Zero Trust Perspective |
|---|---|
| Assumed safety within internal network | Application of Zero Trust irrespective of location |
| Emphasis on bolstering network peripheries | Focus on safeguarding individual users and their activities |
| Anticipated threats primarily from external sources | Assumption of potential danger arising from any direction |
Implementing the ZTNA blueprint requires the integration of several technological instruments like multi-factor verification (MFA), identity and access governance (IAM), and endpoint protection protocols. These tools collaborate to confirm every user’s identity, authenticate their device, and control their access rights to network resources.
Here is a simple code example that shows how MFA might ascertain a user’s credentials in a ZTNA environment:
<code class="language-python">def validate(user, authentication_factors):
#Affirm user's identity
if not user.establish():
return Failure("Verification unsuccessful")
#Establish each authentication factor
for factor in authentication_factors:
if not factor.establish():
return Failure(f"{factor.component} verification unsuccessful")
# If all examinations are successful, permit access
return Accomplished</code>
In the given Python script, the validate function manages a user’s identity and a collection of authentication factors. It affirms the identity and each factor consecutively. If any validation process is not successful, it returns a Failure. If every evaluation passes, access is granted.
In conclusion, ZTNA is a contemporary shift in network security, inspecting each access petition with scrutiny. It requires all users and devices to complete verification processes before gaining entry to network resources. This state-of-the-art tactic is more adept at tackling the intricate digital landscape of today rather than sticking to the outmoded trust system.In our discussion, we’re going to decipher the core construct that forms the backbone of Zero Trust Network Access (ZTNA) Architecture’s robust and ingenious engineering.
The core belief that buttresses the ZTNA Blueprint is undeniably simple yet powerful – no immediate trust should be granted to any person or entity desiring to interface with our network, irrespective of their location vis-Ã -vis the network’s boundaries. This foundational principle underlines the imperative for stringent scrutiny of every individual or cybernetic component attempting to access our network’s specified resources. With this in mind, let’s dissect the primary elements that forge the distinctive framework of the ZTNA.
- Identity & Access Supervision Module (IASM): Acting as the core support of ZTNA, IASM insists on rigorous ratification of both user and device identities. Utilizing methods like multi-stratum authentication (MSA), universal accreditation (UA) and identity normalization, IASM ensures only verified users or devices interact with the network.
<code class="language-python"># Sample code for basic IASM configuration
class Participant:
def __init__(self, identification, key):
self.identification = identification
self.key = key
class ConnectionProtocol:
def authenticate_participant(self, participant):
# Insert your identity confirmation logic here
pass</code>
-
Rigorous Access Rights Distribution: Execution of this guideline guarantees that users and appliances are only provided the absolute necessary capabilities to execute their respective tasks, thus lowering the risk if an infringement should occur.
-
Partitioned Safe Zones: This notion involves bisecting a network into fortified and orderly segments. Each distinct unit abides by specific engagement regulations, mitigating risk exhibition.
-
Continual Surveillance & Evaluation: The ZTNA approach promotes consistent reassessment of probable threats linked to user activity patterns and associated machinery. This requires monitoring of anomalies, analysis of user-system trends, and the requirement to adjust access privileges when appropriate.
-
Augmented Security, Rapid Motion & Reactions (ASRMR): This authoritative component accelerates the process of threat detection and responses to impending security hazards, which helps in enhancing instant counteractive measures during security breach occurrences.
-
Shielded Service Interaction Boundary (SSIB): This blueprint integrates the functionality of broad-band networks (BBN) with the security-based network solutions like ZTNA, Secure Web Gates (SWG), Firewalls-in-reserve (FiR) and so forth.
| Component | Explanation |
|---|---|
| IASM | Gives network participation rights only to authenticated users and devices |
| Rigorous Access Rights Distribution | Restricts users and machines to strictly necessary functions |
| Partitioned Safe Zones | Cuts a network into fortified and handleable parts |
| Continual Surveillance & Evaluation | Monitors anomalies and adjusts access rights as needed |
| ASRMR | Enables quicker discovery and reaction to threats |
| SSIB | Merges broad-band network (BBN) with multiple security assessments |
Finally, the combined strength of these ZTNA factors forges a comprehensive security paradigm that eclipses traditional boundary-centered defenses. ZTNA weaves a precautionary and modifiable plan for safeguarding networks by authenticating all users and devices, regulating access benefits, carving the network into operational clusters, maintaining constant surveillance, and promoting rapid reactions.
Rethinking Our Antiquated Security Model: The Need to Embrace ZTNA Now
As we advance deeper into the digital era, traditional security frameworks are increasingly showing signs of aging. What is regularly alluded to as the "castle-and-moat" approach is slowly but surely losing its relevance. This plan rests on the premise that items within the network enclosure, including firewalls and VPNs, can be presumed secure. Yet the rise of cloud infrastructures, distributed operational schemes, and protocols concerning personal device usage for official tasks (widely referred to as BYOD) have exposed this premise’s fallacy. Zero Trust Network Access (ZTNA), a security model that puts zero faith on initial appearances and validates every element, is the needed game-changer.
Several reasons underpin why ZTNA is seen as the next frontier for network security:
- Adaptability to Recent Work Environments: ZTNA is designed to cater to contemporary distributed workforce needs. It provides secure network connectivity without dependency on the user’s geographical location or the devices being deployed.
<code class="language-python"># Sketch of a typical ZTNA rule
policy = {
"user": "any",
"location": "any",
"device": "any",
"access": "validate"
}</code>
- Micro-Segmentation Empowerment: ZTNA fosters an environment for micro-segmentation, enabling the network to be divided into tiny, isolated sections. This reduces the lateral spread of threats, thereby enhancing overall security.
<code class="language-python"># Illustrating micro-segmentation in ZTNA
network_layout = {
"segments": [
{"label": "HR", "access": "limited"},
{"label": "Finance", "access": "limited"},
{"label": "IT", "access": "unrestricted"}
]
}</code>
- Scaled-Down Access Privileges: ZTNA abides by the principle of least privilege, meaning users are granted just the sufficient rights to execute their job functions. This mitigates potential damage from compromised access credentials.
<code class="language-python"># Illustrating scaled-down access privileges in ZTNA
access_rights = {
"id": "John",
"role": "HR",
"access_to": ["HR database", "Email"]
}</code>
- Ongoing Verification: In contrast to the traditional model that authenticates users at session setup, ZTNA continuously verifies the users’ identities and context-related data during the entire session.
<code class="language-python"># Illustration of ongoing verification in ZTNA
authentication_process = {
"user": "John",
"login_time": "08:00",
"logout_time": "17:00",
"verification": "continuous"
}</code>
- Enhanced User Experience: ZTNA promises an improved user experience compared to the often sluggish and complex VPNs, offering users quick, hassle-free access to applications.
<code class="language-python"># Illustrating enhanced user experience in ZTNA
user_engagement = {
"user": "John",
"login_speed": "instant",
"performance_rating": "excellent"
}</code>
In the final analysis, ZTNA is regarded as the inevitable future of network security compatible with the realities of contemporary work environments, offering unmatched security and user experience. It’s about time we relinquished the traditional security models and usher in a new era with ZTNA.
ZTNA: The Impenetrable Bulwark in the Digital Realm

In today’s interconnected grand scale, the specter of cyber threats perpetually looms over business enterprises. Conventional defense mechanisms, such as boundary protection by firewalls and malicious software detection with antivirus, are becoming inadequate to thwart intricate cyber transgressions. This is the juncture where the cyber defense strategy known as Zero Trust Network Access (ZTNA) comes to our aid. ZTNA’s fundamental philosophy revolves around not placing blind faith in any element, whether internal or external to the network parameters. It insists on validating each connection solicitation to its infrastructure prior to permitting access.
ZTNA’s function as a safeguard within the realm of cyber threats extends multiple dimensions. It presents a formidable barrier against an array of digital threats, inclusive of harmful software attacks, deceptive information solicitation, unauthorized data intrusion, and threats originating from internal sources. Let’s further explore how ZTNA acts as a shield to these digital menaces.
Fortification Against Malware:
Harmful software or ‘malware’ signifies a prevalent menace in the digital realm capable of wreaking havoc on the infrastructure. ZTNA counters malware by imposing rigorous access regulations. Its mechanism guarantees network access only to verified users and authenticated devices, thereby shrinking the malware’s potential field of operation.
<code class="language-python"># A representation of ZTNA restricting access
def control_access(user, device, network):
if user.has_approval() and device.is_certified():
network.authorize_entry()
else:
network.block_entry()</code>
Shielding From Phishing Attacks:
Phishing onslaughts manipulate users into voluntary divulgement of sensitive particulars, such as passcodes and card details. ZTNA curtails such phishing potentials by utilizing multi-factor validation (MFA). MFA mandates the furnish of multiple proofs of identity prior to granting network access, upping the complexity for illegitimate intrusion.
<code class="language-python"># A sample of ZTNA multi-factor validation
def validate(user, password, token):
if user.confirm_password(password) and user.check_token(token):
return True
else:
return False</code>
Countermeasure Against Data Breaches:
Data breaches typically involve illegitimate entry to restricted data. ZTNA forestalls such incidents by adopting the least privilege principle (PoLP). PoLP guarantees that users possess only the bare minimum access rights required for task execution, minimizing the prospective harm in a breach scenario.
<code class="language-python"># An instance of ZTNA employing least privilege principle
def allocate_rights(user, task):
rights = fetch_base_rights(task)
user.allocate_rights(rights)</code>
`
`
Curtailment of Insider Threats:
Threats originating from within the enterprise’s own circumference form part of the insider threats. ZTNA minimizes such risks by relentless surveillance and trail mapping of user actions. This enables the swift identification of abnormal behavior and immediate retaliation against possible threats.
<code class="language-python"># A segment demonstrating ZTNA monitoring user activities
def supervise_actions(user):
while True:
activity = user.fetch_activity_record()
if is_abnormies(activity):
notify_security_force(activity)</code>
To sum up, ZTNA offers a far-reaching protective cover against a spectrum of cyber threats. By imposing stringent access regulations, deploying multi-factor authentication, adhering to the least privilege principle, and ceaseless vigilance, ZTNA ensures your network’s fortification remains impregnable amidst continually transforming digital threats.
Methodological Guide: Establishing a Zero Trust Network Access Framework

Planning and executing the establishment of Zero Trust Network Access (ZTNA) can be an intricate undertaking, necessitating a strategic approach. This chapter will offer a methodological guide for setting up ZTNA within your business framework.
Phase 1: Comprehend Your Network Framework
The initial step towards establishing ZTNA entails comprehending the design and layout of your network infrastructure. Recognition and knowledge of all your network components, their data storage capabilities, and their present security measures are crucial at this stage.
Phase 2: Spot Your Crucial Data
Pinpointing data that requires secure handling is the next step. This could extend from confidential client details, proprietary business knowledge to any other vital data. Having recognized this data, you can then estimate the level of security it warrants.
Phase 3: Establish Your Guidelines
It is vital to prepare your ZTNA guidelines. These guidelines must originate from the concept of minimum privilege—that is, users should merely have admission to the data and resources required for their designated tasks.
For instance, your policy might look like this:
<code class="language-python">if user.position == 'staff':
permission = 'controlled'
elif user.position == 'team-leader':
permission = 'intermediate'
else:
permission = 'complete'</code>
Phase 4: Incorporate Your Chosen ZTNA Framework
Select a ZTNA framework that complements your business’s requirements. This could range from cloud-centric frameworks, on-site solutions, or a fusion of both. Once chosen, this solution can then be integrated into your network.
Phase 5: Supervise and Modify
Subsequent to integrating your selected ZTNA framework, regular supervision and modifications are crucial. This encompasses routine assessment of your guidelines and making necessary alterations to align with your business’s dynamic needs.
Here’s a comparison table reviewing the methodological guidances implementing ZTNA:
| Phases | Explanation |
|---|---|
| Comprehend Your Network Framework | Understand the whereabouts of all your network elements, their data storage capabilities, and their present safety measures. |
| Spot Your Crucial Data | Define the data that deems secure handling and compute the degree of safety measures it warrants. |
| Establish Your Guidelines | Draft your ZTNA guidelines based on the concept of minimum privilege. |
| Incorporate Your Chosen ZTNA Framework | Identify and integrate a ZTNA framework that complement your business’s demands. |
| Supervise and Modify | Regularly check and modify your ZTNA framework as needed. |
Implementing ZTNA doesn’t end at the final installation step—it’s an ongoing process that demands regular supervision and modification. By adhering to these steps, one can assure the protection of the organization’s data and brace themselves against impending cybersecurity challenges.
Deciphering the Role of ZTNA in Bolstering Cloud Security Measures
The advanced digital era presents us both beneficial opportunities and substantial challenges. Undoubtedly, cloud technology has revolutionized business processes by delivering brilliant scalability, growth perspectives, and practical solutions. However, it has unmasked certain limitations in our traditional security frameworks that fail to mitigate the evolved risks presented by the fluid nature of cloud offerings. Zero Trust Network Access (ZTNA) can play a significant role in addressing these security concerns.
ZTNA can be envisioned as an unyielding sentinel in the digital realm. Its principle is based on inherent distrust, irrespective of their origin. Zero Trust emphasizes confirming the privileges and access rights of all users, applications, and devices seeking to utilise network resources. This approach is especially effective in the ambiguous perimeters of cloud-based situations.
Let’s dissect how ZTNA amplifies the security resilience of cloud-oriented solutions.
-
User Verification: By utilizing advanced Identity and Access Management (IAM) systems, ZTNA holds the responsibility of confirming the legitimacy of all users and devices attempting network access. This aspect becomes vital in a cloud environment, where resources are available at all times from any location.
<code class="language-python"># Illustrating IAM method in Python def verify_user(user, key): if user_db.confirm(user, key): return True return False</code> -
Principle of Minimum Authority: ZTNA endorses the ‘Principle of Minimum Authority’, where only necessary permissions are granted for task completion. This strategy significantly reduces pathways for unauthorized penetration into sensitive cloud data.
<code class="language-python"># Demonstrating Principle of Minimum Authority in Python def assign_permissions(user, component): if user.role == 'administrator': component.give_full_access(user) elif user.role == 'staff': component.allow_limited_access(user)</code> -
Network Partitioning: ZTNA splits the network into separate sectors, each with its own independent security protocols. This prevents malicious activities from proliferating through the network, thereby improving the security of cloud services.
-
Routine Analysis and Assessment: ZTNA produces regular reports on network functions, facilitating swift detection and response to unusual behaviours or threats.
-
Smooth Integration with Additional Security Mechanisms: ZTNA can readily be included with other safety systems like Security Information and Event Management (SIEM), anomalies detection tools, and firewalls to create a comprehensive defense solution.
| Protection Software | Function | Collaboration with ZTNA |
|---|---|---|
| SIEM | Collects and evaluates security data | Provides ZTNA with data for access decision-making |
| IDS | Identifies anomalies in network actions | Alerts ZTNA of potential disruptions |
| Firewall | Controls two-way network traffic | Collaborates with ZTNA in establishing safety guidelines |
In essence, ZTNA presents a scalable security architecture that evolves along with the rapidly shifting cloud environment. It plays a critical role in bolstering cloud security by verifying each user and device, implementing the ‘Principle of Minimum Authority’, partitioning the network into safe zones, and integrating smoothly with other security mechanisms to erect a formidable shield of defense. As organizations continue to expand their digital footprint and reliance on cloud services, the significance of ZTNA in strengthening cloud defense measures is set to skyrocket.
The Prospective Course of Zero Trust Network Access (ZTNA)
As we navigate the forward voyage of Zero Trust Network Access (ZTNA), it’s imperative to acknowledge that the landscape of cybersecurity is in a constant state of flux. The escalating complexity of cyberattacks, coupled with the swift embrace of cloud technologies, demands an ongoing and flexible strategy for network protection. ZTNA, with its enduring mantra of "discard trust, perpetually validate," is likely to be a formidable force in dictating the subsequent trajectory of cybersecurity.
`
`
The prospective course of ZTNA can be generally divided into these key domains:
Merging with Artificial Intelligence (AI) and Machine Learning (ML): AI and ML can greatly bolster the functionality of ZTNA. They have the potential to streamline the process of detection and response, thereby curtailing the mitigation period. As an illustration, AI can be utilized to scrutinize user activity and perceive irregularities that may be suggestive of a possible security transgression.
<code class="language-python"># A model code snippet portraying how AI can be leveraged in ZTNA import numpy as np from sklearn.ensemble import IsolationForest # Assume 'data' is a numpy array encapsulating user behavior data clf = IsolationForest(contamination=0.01) clf.fit(data) # Foresee the anomalies in the data anomalies = clf.predict(data)</code>
Broadening the Scope of ZTNA to Internet of Things (IoT) Equipment: As IoT equipment proliferate, safeguarding these devices acquires immense importance. ZTNA can assert its importance in this sector by bestowing secure access to these gadgets based on minimum privilege.
Amplified Implementation in the Cloud Sphere: As a greater number of firms transition their workings to the cloud, the application of ZTNA in cloud safety is likely to magnify. ZTNA can facilitate secure access to cloud assets, thus aiding firms in safeguarding their confidential data.
Superior User Experience: Future strides in ZTNA are poised to concentrate on amplifying user experience. This might comprise minimizing the delay in network linkages and bestowing uninterrupted access to resources.
Regulatory Compliance: The mounting emphasis on data confidentiality and protection positions regulatory compliance as a priority for firms. ZTNA can aid firms in adhering to regulations by facilitating secure data access and keeping detailed records of access.
| Present Status | Prospective Course |
|---|---|
| ZTNA primarily employed in enterprise networks | Broadening the scope of ZTNA to IoT equipment |
| Manual detection and response | Merging with AI and ML for streamlined threat detection and response |
| Restricted implementation in cloud safety | Amplified implementation of ZTNA in cloud safety |
| User experience is often sacrificed for security | Superior user experience without sacrificing security |
| Compliance is often an afterthought | Regulatory compliance is a vital consideration in ZTNA deployment |
In summing up, the forward trajectory of Zero Trust Network Access (ZTNA) seems quite encouraging. With progressive tech strides and a growing emphasis on cybersecurity, ZTNA is expected to be a crucial determinant of the evolution of network security. Nevertheless, a successful ZTNA deployment calls for an in-depth comprehension of its principles and a strategic blueprint for its roll-out.
The post What Is Zero Trust Network Access (ZTNA) ? appeared first on Wallarm.
*** This is a Security Bloggers Network syndicated blog from Wallarm authored by Ivan Novikov. Read the original post at: https://lab.wallarm.com/what/zero-trust-network-access-ztna-redefining-network-security-for-the-modern-digital-landscape/
如有侵权请联系:admin#unsafe.sh
