Friday, November 3, 2023 17:11
Today, Talos is publishing a glimpse into the most prevalent threats we've observed between Oct. 27 and Nov. 3. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org , or ClamAV.net .
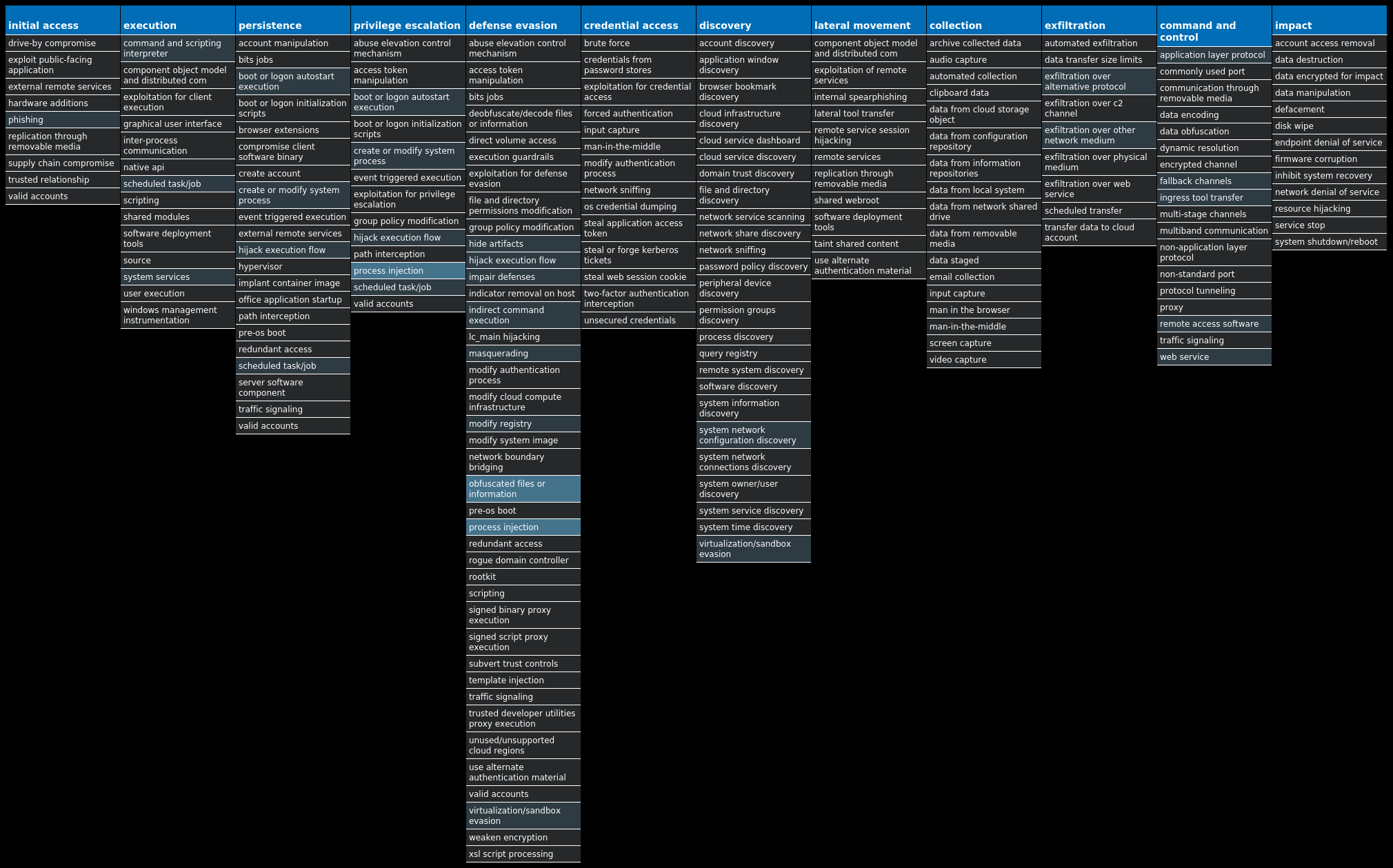
For each threat described below, this blog post only lists 25 of the associated file hashes and up to 25 IOCs for each category. An accompanying JSON file can be found here that includes the complete list of file hashes, as well as all other IOCs from this post. A visual depiction of the MITRE ATT&CK techniques associated with each threat is also shown. In these images, the brightness of the technique indicates how prevalent it is across all threat files where dynamic analysis was conducted. There are five distinct shades that are used, with the darkest indicating that no files exhibited technique behavior and the brightest indicating that technique behavior was observed from 75 percent or more of the files.
The most prevalent threats highlighted in this roundup are:
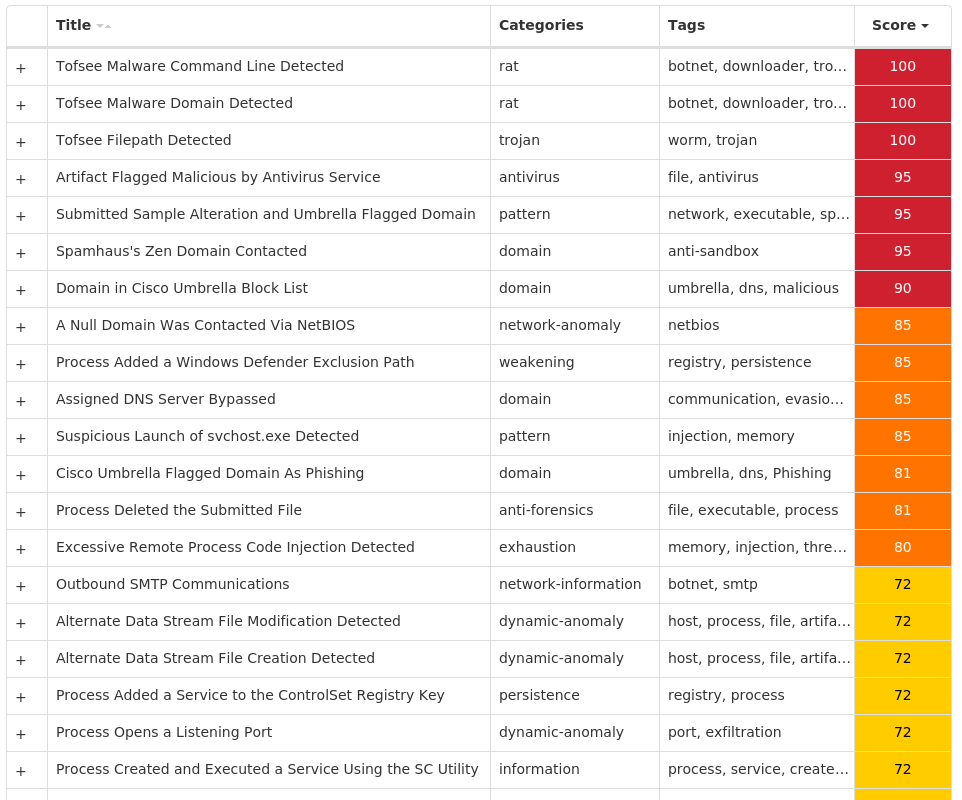
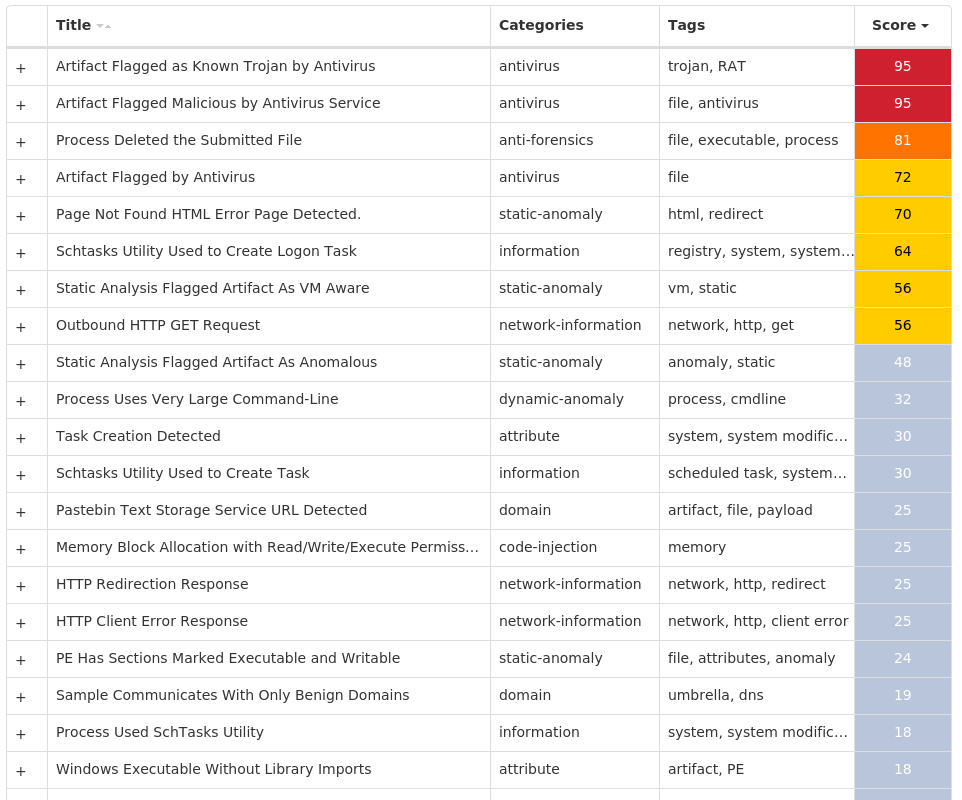
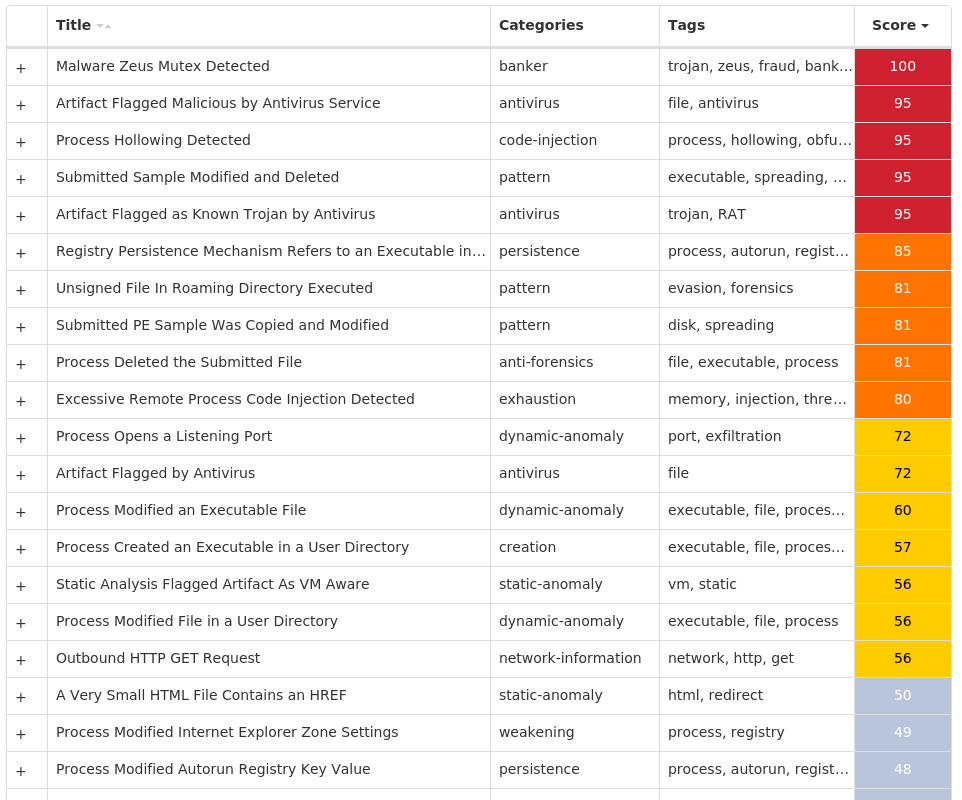
Threat Name Type Description Win.Dropper.Tofsee-10012832-0 Dropper Tofsee is multi-purpose malware that features a number of modules used to carry out various activities such as sending spam messages, conducting click fraud, mining cryptocurrency, and more. Infected systems become part of the Tofsee spam botnet and send a large volume of spam messages to infect additional systems and increase the size of the botnet under the operator's control. Win.Trojan.Miner-10012902-0 Trojan This malware installs and executes cryptocurrency mining software. You can read more about this kind of threat on our blog https://blog.talosintelligence.com/2018/07/blocking-cryptomining.html. Win.Dropper.Glupteba-10012922-0 Dropper Glupteba is a multi-purpose trojan that is known to use the infected machine to mine cryptocurrency and steal sensitive information like usernames and passwords, spreads over the network using exploits like EternalBlue, and leverages a rootkit component to remain hidden. Glupteba has also been observed using the Bitcoin blockchain to store configuration information. Win.Packed.Razy-10012926-0 Packed Razy is frequently a generic detection name for a Windows trojan. It collects sensitive information from the infected host and encrypts the data, and sends it to a command and control (C2) server. Information collected may include screenshots. The samples modify auto-execute functionality by setting and creating a value in the registry for persistence. Win.Dropper.Zeus-10012956-0 Dropper Zeus is a trojan that steals information such as banking credentials using methods such as key-logging and form-grabbing. Xls.Malware.Valyria-10012971-0 Malware Valyria is a malicious Microsoft Word document family that distributes other malware, such as Emotet.
Threat Breakdown Win.Dropper.Tofsee-10012832-0 Indicators of Compromise IOCs collected from dynamic analysis of 25 samples Registry Keys Occurrences \.DEFAULT\CONTROL PANEL\BUSES 4 \.DEFAULT\CONTROL PANEL\BUSES Value Name: Config2 4 \.DEFAULT\CONTROL PANEL\BUSES Value Name: Config1 4 \.DEFAULT\CONTROL PANEL\BUSES Value Name: Config0 4 \SYSTEM\CONTROLSET001\SERVICES\KUWRNFEA 2 \SYSTEM\CONTROLSET001\SERVICES\KUWRNFEA Value Name: Type 2 \SYSTEM\CONTROLSET001\SERVICES\KUWRNFEA Value Name: Start 2 \SYSTEM\CONTROLSET001\SERVICES\KUWRNFEA Value Name: ErrorControl 2 \SYSTEM\CONTROLSET001\SERVICES\KUWRNFEA Value Name: DisplayName 2 \SYSTEM\CONTROLSET001\SERVICES\KUWRNFEA Value Name: WOW64 2 \SYSTEM\CONTROLSET001\SERVICES\KUWRNFEA Value Name: ObjectName 2 \SYSTEM\CONTROLSET001\SERVICES\KUWRNFEA Value Name: ImagePath 2 \SYSTEM\CONTROLSET001\SERVICES\SCEZVNMI Value Name: ErrorControl 1 \SYSTEM\CONTROLSET001\SERVICES\SCEZVNMI Value Name: DisplayName 1 \SYSTEM\CONTROLSET001\SERVICES\SCEZVNMI Value Name: WOW64 1 \SYSTEM\CONTROLSET001\SERVICES\SCEZVNMI Value Name: ObjectName 1 \SYSTEM\CONTROLSET001\SERVICES\SCEZVNMI Value Name: Description 1 \SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS Value Name: C:\Windows\SysWOW64\scezvnmi 1 \SYSTEM\CONTROLSET001\SERVICES\KUWRNFEA Value Name: Description 1 \SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS Value Name: C:\Windows\SysWOW64\kuwrnfea 1 \SYSTEM\CONTROLSET001\SERVICES\RBDYUMLH 1 \SYSTEM\CONTROLSET001\SERVICES\RBDYUMLH Value Name: Type 1 \SYSTEM\CONTROLSET001\SERVICES\RBDYUMLH Value Name: Start 1 \SYSTEM\CONTROLSET001\SERVICES\RBDYUMLH Value Name: ErrorControl 1 \SYSTEM\CONTROLSET001\SERVICES\RBDYUMLH Value Name: DisplayName 1
Mutexes Occurrences Global\14
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 176[.]113[.]115[.]1365 80[.]66[.]75[.]45 176[.]113[.]115[.]1355 45[.]143[.]201[.]2385 176[.]113[.]115[.]845 62[.]122[.]184[.]925 80[.]66[.]75[.]775 83[.]97[.]73[.]445 84[.]201[.]152[.]2205 31[.]13[.]65[.]1743 31[.]13[.]65[.]523 172[.]217[.]165[.]1323 142[.]250[.]72[.]993 34[.]120[.]241[.]2143 52[.]101[.]8[.]493 142[.]250[.]65[.]1962 93[.]115[.]25[.]492 93[.]115[.]25[.]132 93[.]115[.]25[.]102 93[.]115[.]25[.]732 20[.]236[.]44[.]1622 172[.]217[.]21[.]1642 149[.]154[.]167[.]991 31[.]31[.]196[.]811 172[.]217[.]165[.]1311
*See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences 249[.]5[.]55[.]69[.]in-addr[.]arpa5 www[.]google[.]com5 vanaheim[.]cn5 249[.]5[.]55[.]69[.]bl[.]spamcop[.]net4 249[.]5[.]55[.]69[.]cbl[.]abuseat[.]org4 249[.]5[.]55[.]69[.]dnsbl[.]sorbs[.]net4 249[.]5[.]55[.]69[.]sbl-xbl[.]spamhaus[.]org4 249[.]5[.]55[.]69[.]zen[.]spamhaus[.]org4 microsoft-com[.]mail[.]protection[.]outlook[.]com4 microsoft[.]com4 i[.]instagram[.]com3 www[.]instagram[.]com3 www[.]evernote[.]com3 www[.]google[.]com[.]tw2 www[.]google[.]com[.]co1 www[.]google[.]be1 www[.]google[.]ch1 b[.]i[.]instagram[.]com1 www[.]tiktok[.]com1 smtp[.]office365[.]com1 ca[.]account[.]sony[.]com1 t[.]me1 my[.]account[.]sony[.]com1 www[.]googleapis[.]com1 m[.]freewallet[.]org1
*See JSON for more IOCs
Files and or directories created Occurrences %TEMP%\.exe 5 %SystemRoot%\SysWOW64\config\systemprofile4 %SystemRoot%\SysWOW64\config\systemprofile:.repos4 %SystemRoot%\SysWOW64\kuwrnfea2 %SystemRoot%\SysWOW64\oyavrjie1 %SystemRoot%\SysWOW64\scezvnmi1 %SystemRoot%\SysWOW64\rbdyumlh1
File Hashes 0097a9426a4c40673425c9d58f0bc7b724ffcf06eb816a527db36bc68053f6b7
Coverage
Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
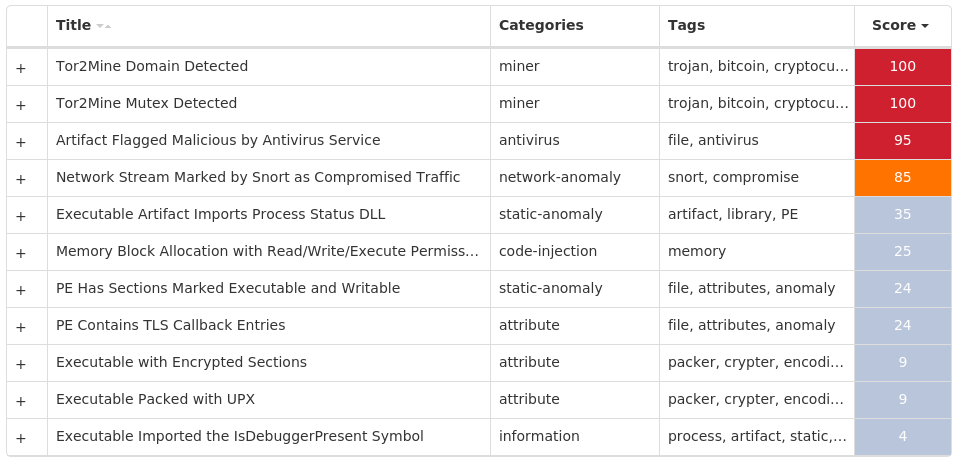
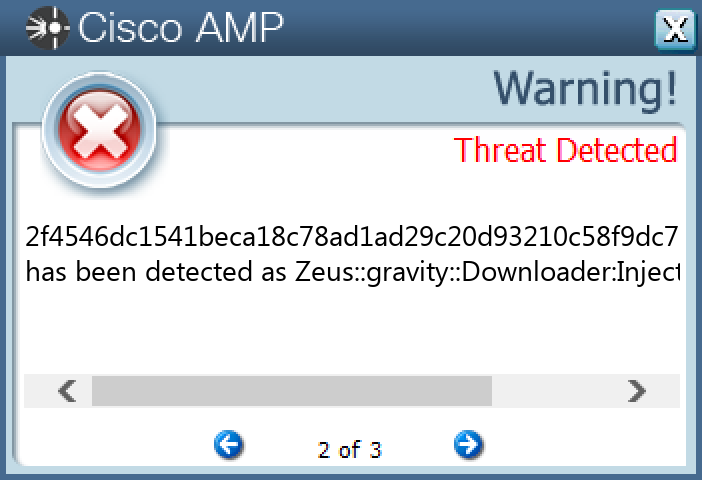
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Trojan.Miner-10012902-0 Indicators of Compromise IOCs collected from dynamic analysis of 11 samples Mutexes Occurrences 4pC39Ev2yuzFY8izw76DGDJR11
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 185[.]10[.]68[.]1236 95[.]214[.]24[.]353 185[.]10[.]68[.]2202 109[.]71[.]252[.]452
Domain Names contacted by malware. Does not indicate maliciousness Occurrences eu[.]minerpool[.]pw11
File Hashes 12450b3415939ac685ea225c32f52a9a0fd9542b3306fa473694e84fbbbc24e7
Coverage
Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
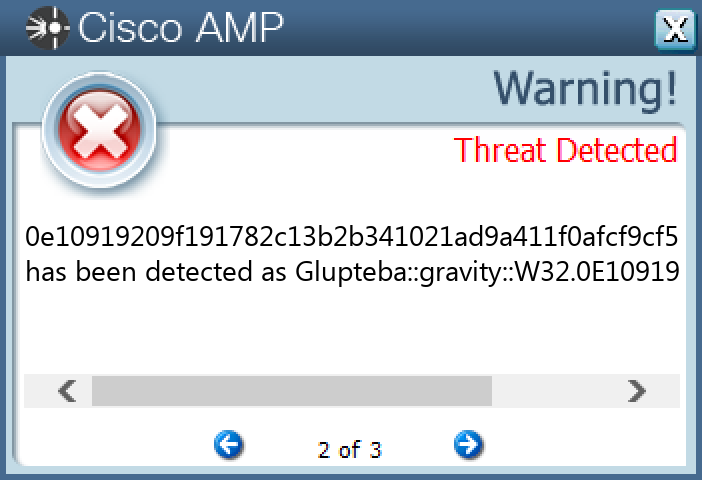
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Glupteba-10012922-0 Indicators of Compromise IOCs collected from dynamic analysis of 105 samples Registry Keys Occurrences \SOFTWARE\MICROSOFT\A1890984 Value Name: PatchTime 105 \SOFTWARE\MICROSOFT\A1890984 Value Name: PGDSE 105 \SYSTEM\CONTROLSET001\SERVICES\VBOXWDDM Value Name: ImagePath 105 \SYSTEM\CONTROLSET001\SERVICES\VBOXWDDM Value Name: DisplayName 105 \SYSTEM\CONTROLSET001\SERVICES\VBOXWDDM Value Name: WOW64 105 \SYSTEM\CONTROLSET001\SERVICES\VBOXWDDM Value Name: ObjectName 105 \SYSTEM\CONTROLSET001\SERVICES\VBOXSF Value Name: Type 105 \SYSTEM\CONTROLSET001\SERVICES\VBOXSF Value Name: Start 105 \SYSTEM\CONTROLSET001\SERVICES\VBOXSF Value Name: ErrorControl 105 \SYSTEM\CONTROLSET001\SERVICES\VBOXSF Value Name: ImagePath 105 \SYSTEM\CONTROLSET001\SERVICES\VBOXSF Value Name: DisplayName 105 \SYSTEM\CONTROLSET001\SERVICES\VBOXSF Value Name: WOW64 105 \SYSTEM\CONTROLSET001\SERVICES\VBOXSF Value Name: ObjectName 105 \SYSTEM\CONTROLSET001\SERVICES\VBOXMOUSE Value Name: Type 105 \SYSTEM\CONTROLSET001\SERVICES\VBOXMOUSE Value Name: Start 105 \SYSTEM\CONTROLSET001\SERVICES\VBOXMOUSE Value Name: ErrorControl 105 \SYSTEM\CONTROLSET001\SERVICES\VBOXMOUSE Value Name: ImagePath 105 \SYSTEM\CONTROLSET001\SERVICES\VBOXMOUSE Value Name: DisplayName 105 \SYSTEM\CONTROLSET001\SERVICES\VBOXMOUSE Value Name: WOW64 105 \SYSTEM\CONTROLSET001\SERVICES\VBOXMOUSE Value Name: ObjectName 105 \SYSTEM\CONTROLSET001\SERVICES\VBOXGUEST Value Name: Type 105 \SYSTEM\CONTROLSET001\SERVICES\VBOXGUEST Value Name: Start 105 \SYSTEM\CONTROLSET001\SERVICES\VBOXGUEST Value Name: ErrorControl 105 \SYSTEM\CONTROLSET001\SERVICES\VBOXGUEST Value Name: ImagePath 105 \SYSTEM\CONTROLSET001\SERVICES\VBOXGUEST Value Name: DisplayName 105
Mutexes Occurrences Global\SetupLog105 Global\WdsSetupLogInit105 Global\h48yorbq6rm87zot105 WininetConnectionMutex105 Global\qtxp9g8w105 Global\xmrigMUTEX3133715
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 204[.]79[.]197[.]219105 20[.]150[.]38[.]22864 172[.]67[.]212[.]18863 20[.]150[.]70[.]3661 20[.]150[.]79[.]6861 104[.]21[.]23[.]18440 185[.]82[.]216[.]10832 185[.]82[.]216[.]10431 185[.]82[.]216[.]11125 162[.]159[.]130[.]23324 162[.]159[.]134[.]23322 162[.]159[.]133[.]23321 162[.]159[.]129[.]23320 162[.]159[.]135[.]23318 81[.]3[.]27[.]4417 142[.]250[.]112[.]12717 142[.]250[.]144[.]12717 185[.]82[.]216[.]9617 172[.]253[.]120[.]12716 142[.]250[.]15[.]12712 74[.]125[.]128[.]12710 3[.]33[.]249[.]2489 15[.]197[.]250[.]1926
Domain Names contacted by malware. Does not indicate maliciousness Occurrences msdl[.]microsoft[.]com105 vsblobprodscussu5shard35[.]blob[.]core[.]windows[.]net105 vsblobprodscussu5shard60[.]blob[.]core[.]windows[.]net105 cdn[.]discordapp[.]com105 walkinglate[.]com103 stun[.]stunprotocol[.]org19 stun[.]l[.]google[.]com17 stun2[.]l[.]google[.]com17 stun[.]ipfire[.]org17 stun3[.]l[.]google[.]com16 stun[.]sipgate[.]net15 79102df1-5f9d-4ca9-bdf6-1fa1060285b4[.]uuid[.]datadumpcloud[.]org14 stun1[.]l[.]google[.]com13 stun4[.]l[.]google[.]com10 79102df1-5f9d-4ca9-bdf6-1fa1060285b4[.]uuid[.]databaseupgrade[.]ru10 79102df1-5f9d-4ca9-bdf6-1fa1060285b4[.]uuid[.]dumperstats[.]org8 79102df1-5f9d-4ca9-bdf6-1fa1060285b4[.]uuid[.]theupdatetime[.]org8 79102df1-5f9d-4ca9-bdf6-1fa1060285b4[.]uuid[.]statsexplorer[.]org7 79102df1-5f9d-4ca9-bdf6-1fa1060285b4[.]uuid[.]allstatsin[.]ru7 79102df1-5f9d-4ca9-bdf6-1fa1060285b4[.]uuid[.]alldatadump[.]org7 79102df1-5f9d-4ca9-bdf6-1fa1060285b4[.]uuid[.]dumppage[.]org6 79102df1-5f9d-4ca9-bdf6-1fa1060285b4[.]uuid[.]myfastupdate[.]org6 79102df1-5f9d-4ca9-bdf6-1fa1060285b4[.]uuid[.]filesdumpplace[.]org5 79102df1-5f9d-4ca9-bdf6-1fa1060285b4[.]uuid[.]statstraffic[.]org5 79102df1-5f9d-4ca9-bdf6-1fa1060285b4[.]uuid[.]createupdate[.]org5
*See JSON for more IOCs
Files and or directories created Occurrences %SystemRoot%\Logs\CBS\CBS.log105 %SystemRoot%\rss105 %SystemRoot%\rss\csrss.exe105 %TEMP%\csrss105 %TEMP%\csrss\dsefix.exe105 %TEMP%\csrss\patch.exe105 %System32%\drivers\Winmon.sys105 %System32%\drivers\WinmonFS.sys105 %System32%\drivers\WinmonProcessMonitor.sys105 %TEMP%\Symbols105 %TEMP%\Symbols\ntkrnlmp.pdb105 %TEMP%\Symbols\ntkrnlmp.pdb\9E22A5947A15489895CE716436B45BE02105 %TEMP%\Symbols\ntkrnlmp.pdb\9E22A5947A15489895CE716436B45BE02\download.error105 %TEMP%\Symbols\pingme.txt105 %TEMP%\Symbols\winload_prod.pdb105 %TEMP%\Symbols\winload_prod.pdb\B7B16B17E078406E806A050C8BEE2E361105 %TEMP%\Symbols\winload_prod.pdb\B7B16B17E078406E806A050C8BEE2E361\download.error105 %TEMP%\dbghelp.dll105 %TEMP%\ntkrnlmp.exe105 %TEMP%\osloader.exe105 %TEMP%\symsrv.dll105 %TEMP%\csrss\DBG0.tmp105 %System32%\Tasks\csrss105 %TEMP%\csrss\injector105 %TEMP%\csrss\injector\NtQuerySystemInformationHook.dll105
*See JSON for more IOCs
File Hashes 01aaff065260cd63f0c18f9f4fa41ebac93d8bc14b04cd0e121226e23f2ae5c0
Coverage
Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
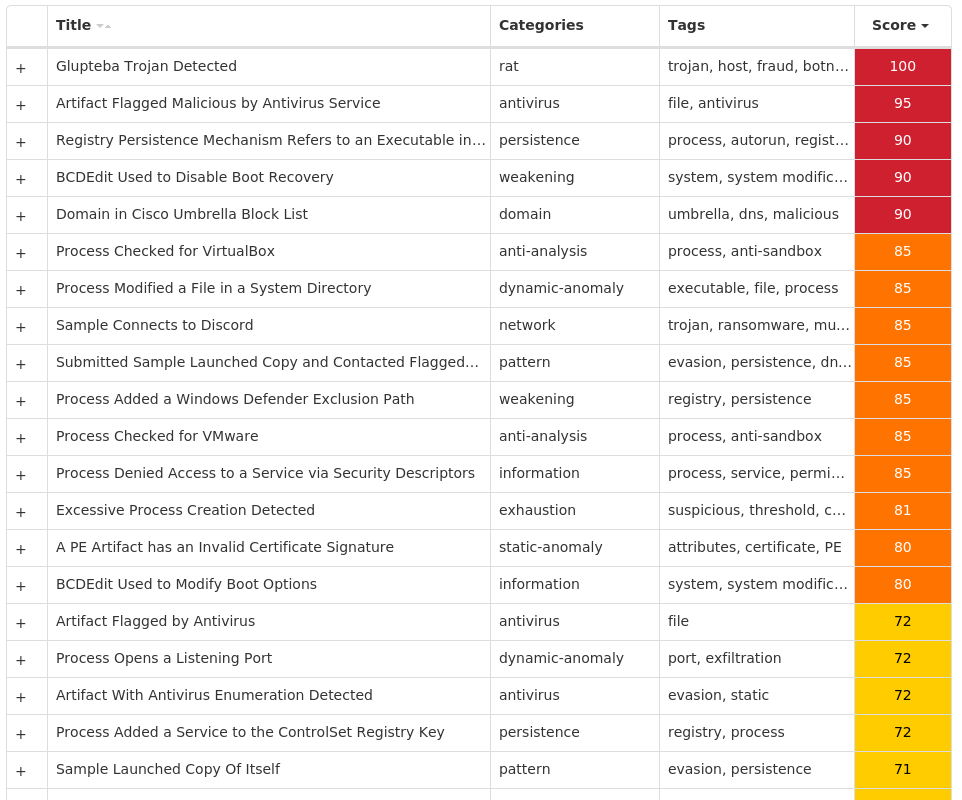
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Packed.Razy-10012926-0 Indicators of Compromise IOCs collected from dynamic analysis of 25 samples IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 142[.]250[.]65[.]17425 104[.]20[.]68[.]14312 172[.]67[.]34[.]1707 104[.]20[.]67[.]1436
Domain Names contacted by malware. Does not indicate maliciousness Occurrences pastebin[.]com25 w[.]google[.]com25 www[.]odtka3180h[.]com1 www[.]tiowrgijve[.]com1 www[.]bztonapwpl[.]com1 www[.]peygqgx19k[.]com1 www[.]dk7m9xlvx6[.]com1 www[.]mzepqiwos7[.]com1 www[.]ksqijdlyco[.]com1 www[.]6bxzawid0x[.]com1 www[.]szvg1jscbo[.]com1 www[.]5g14dh09da[.]com1 www[.]31dbqaqbv7[.]com1 www[.]2z9is2h9ij[.]com1 www[.]chj5xirdp2[.]com1 www[.]vcgbwtxren[.]com1 www[.]qqoqcncrkk[.]com1 www[.]pdpdhkt5in[.]com1 www[.]mvay5eclml[.]com1 www[.]am1mehlnnu[.]com1 www[.]fspreo58vc[.]com1 www[.]jmgaabxx0e[.]com1 www[.]hii7d4vsoa[.]com1 www[.]zaqkbsqz6a[.]com1 www[.]vm609jjbfh[.]com1
*See JSON for more IOCs
Files and or directories created Occurrences %System32%\Tasks\Google_Trk_Updater25
File Hashes 04ecaf9dad1ca60c52143ec089fb5463c87e4645725a3853d84402fd3961073f
Coverage
Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
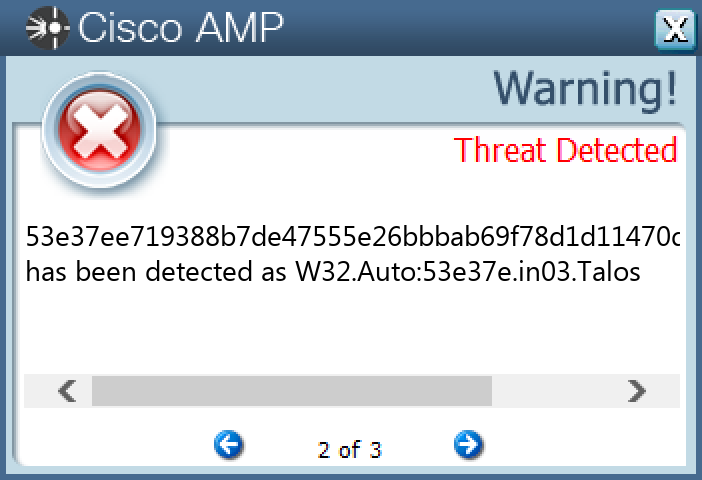
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Zeus-10012956-0 Indicators of Compromise IOCs collected from dynamic analysis of 13 samples Registry Keys Occurrences \SOFTWARE\LOCAL APPWIZARD-GENERATED APPLICATIONS 13 \SOFTWARE\LOCAL APPWIZARD-GENERATED APPLICATIONS\IMAGEVIEWER 13 \SOFTWARE\LOCAL APPWIZARD-GENERATED APPLICATIONS\IMAGEVIEWER\RECENT FILE LIST 13 \SOFTWARE\LOCAL APPWIZARD-GENERATED APPLICATIONS\IMAGEVIEWER\SETTINGS 13 \SOFTWARE\MICROSOFT\INTERNET EXPLORER\PRIVACY Value Name: CleanCookies 1 \SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.100 Value Name: CheckSetting 1 \SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.102 Value Name: CheckSetting 1 \SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.104 Value Name: CheckSetting 1 \SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.101 Value Name: CheckSetting 1 \SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.103 Value Name: CheckSetting 1 \SOFTWARE\MICROSOFT\XAUGYT 1 \SOFTWARE\MICROSOFT\XAUGYT Value Name: Xiycweva 1 \SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: {579CCBAF-A961-2396-8190-F1E6D0D72F00} 1
Mutexes Occurrences Local\{B188B787-D549-C582-8190-F1E6D0D72F00}1 Local\{9A2ED2B6-B078-EE24-8190-F1E6D0D72F00}1 Local\{B188B784-D54A-C582-8190-F1E6D0D72F00}1 GLOBAL\{} 1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 23[.]219[.]154[.]1361 185[.]215[.]4[.]561
Domain Names contacted by malware. Does not indicate maliciousness Occurrences apps[.]identrust[.]com1 angryflo[.]ru1
Files and or directories created Occurrences %TEMP%\tmpb0d3b90f.bat1 %APPDATA%\Hevot1 %APPDATA%\Hevot\otgi.exe1 %APPDATA%\Ogpal1 %APPDATA%\Ogpal\ymvuu.tei1
File Hashes 1b5e3aab3032393e53222dbb2de14b102d616408d77de1daed4d5b7d634e7575
Coverage
Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
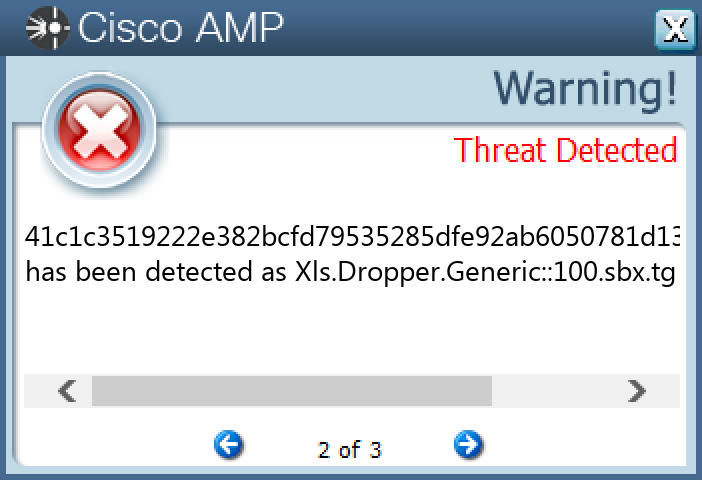
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Xls.Malware.Valyria-10012971-0 Indicators of Compromise IOCs collected from dynamic analysis of 10 samples Mutexes Occurrences Local\10MU_ACB10_S-1-5-5-0-6786310 Local\10MU_ACBPIDS_S-1-5-5-0-6786310
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 162[.]241[.]120[.]1803 70[.]32[.]23[.]942
Domain Names contacted by malware. Does not indicate maliciousness Occurrences creditcollectionglobal[.]co4 greenpayindia[.]com3 treasuringchristonline[.]com2 kadsec[.]com1
Files and or directories created Occurrences %APPDATA%\notepad.js4 %APPDATA%\brisk.vbs3 %APPDATA%\notepads.js2 %APPDATA%\credit.vbs1
File Hashes 3a37360930f0d13d19523597d36813f500afc518ab89c9076c6cc2386bedd44a
Coverage
Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK
文章来源: https://blog.talosintelligence.com/threat-roundup-1027-1103/