This is my completely informal, uncertified, unreviewed and otherwise completely unofficial blog inspired by my reading of our eighth Threat Horizons Report (full version) that we just released (the official blog for #1 report, my unofficial blogs for #2, #3, #4, #5, #6 and #7).
My favorite quotes from the report follow below:
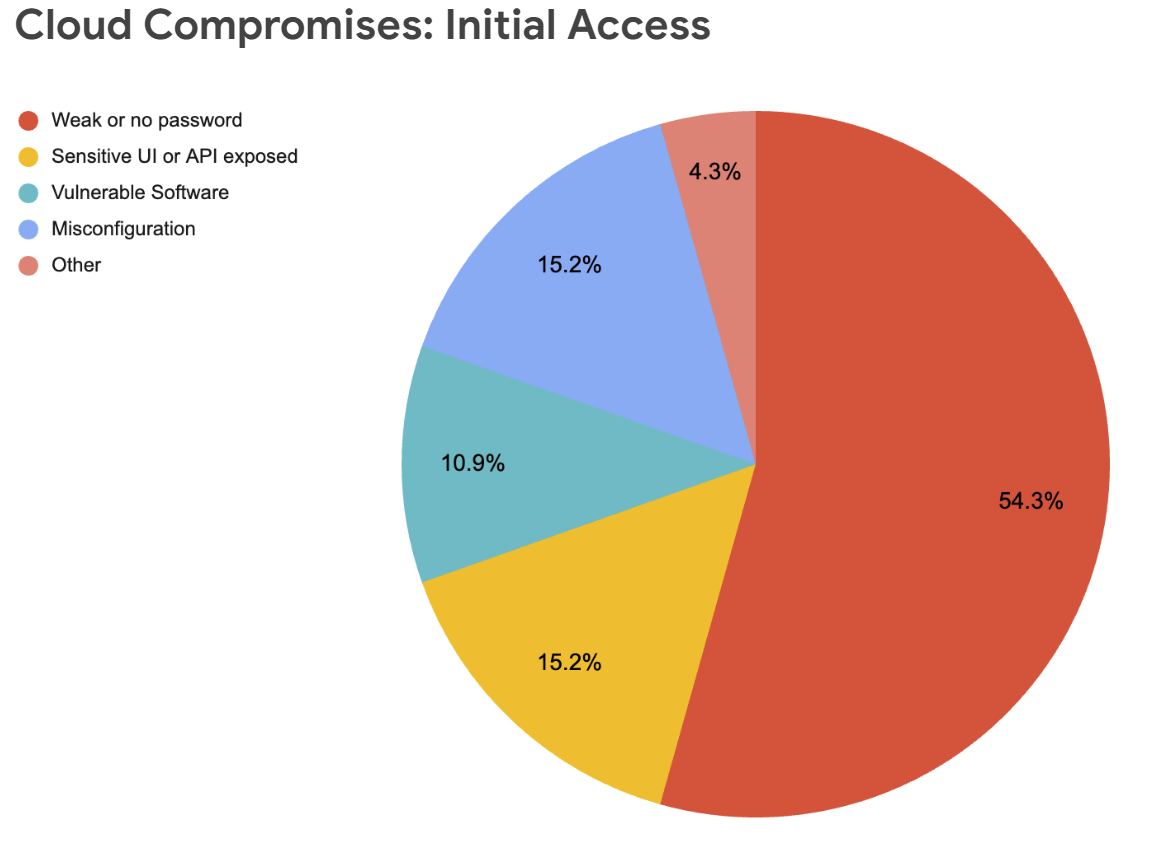
- “The cloud compromise factors and outcomes observed in Q2 2023 were largely similar to previous quarters and consistent with the last 12 months of reporting. […] weak credentials continue to represent the largest compromise factor where many observed instances were a result of attackers brute forcing default accounts, Secure Shell (SSH), and the Remote Desktop Protocol (RDP)” [A.C. — as usual, shocking but not surprising. Perhaps the surprise is that it is NOT changing over 2–3 years of ‘clouding’…]
- Here is the data averaged over a few reports — the data is actually fairly stable over time, sad though it may be.
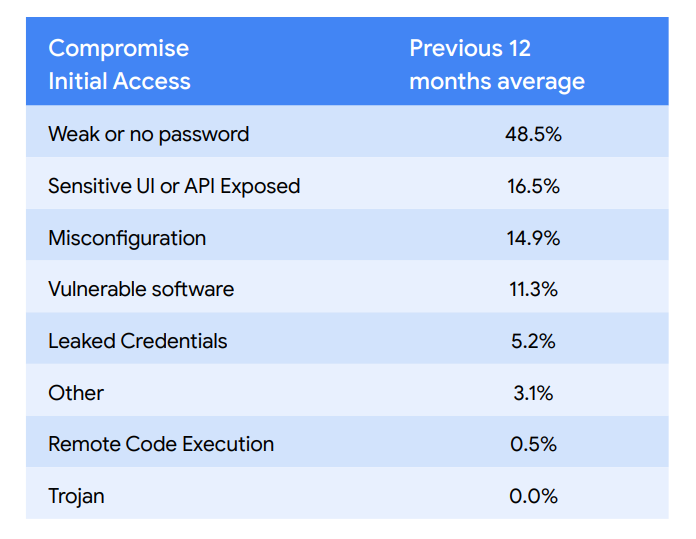
- “In the Q2 2022 Threat Horizons Report, we highlight that a disproportionate percentage of attackers opportunistically use coin mining across Cloud products and alter their tactics to evade discovery. This is consistent with this quarter’s findings, as this is the most observed outcome from compromises.” [A.C. -another ‘resilient’ finding, most cloud attackers just cryptomine]
- … and the data averaged over time:
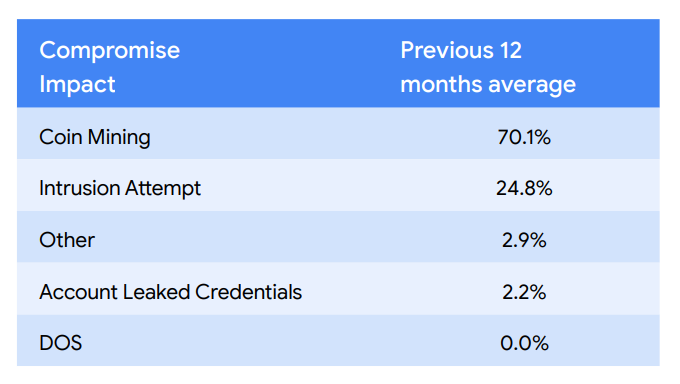
- “This quarter our teams observed a 8.5% increase in vulnerable software compromises led primarily by PostgreSQL being the most exploited.” [A.C. — an interesting choice, perhaps some of the instances got ransomed too? Also, I sense this is related to credentials above…]
- “SaaS providers were also targeted earlier in the year by suspected financially-motivated DPRK actors in order to gain access to downstream victims.” [A.C. — this is interesting, SaaS as a stepping stone! Is SaaS — likely SaaS credentials, frankly, your weakest link?]
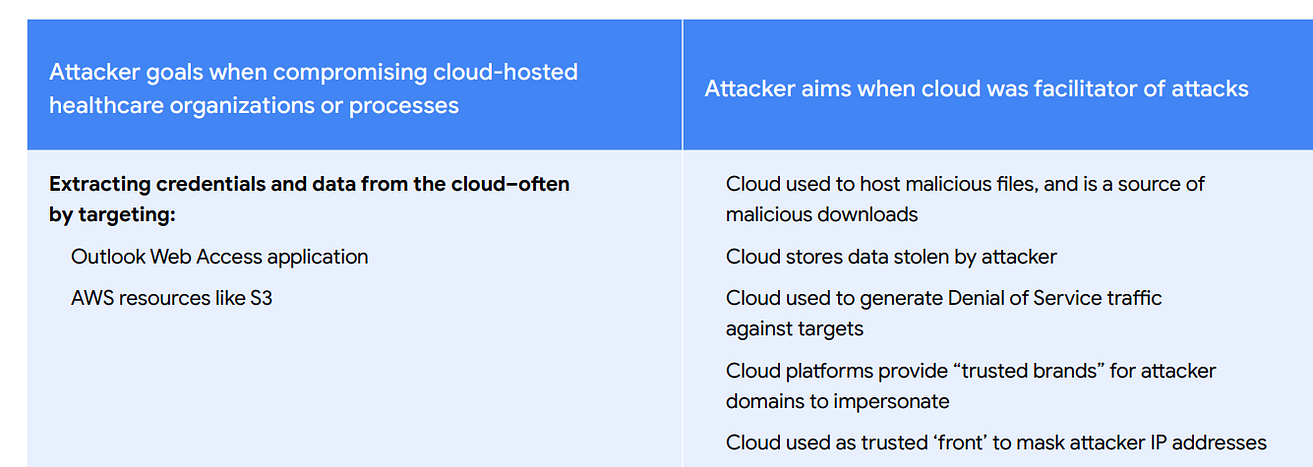
- Finally, here is some interesting data focused on healthcare cloud compromises
Now, go and read the report!
Related posts:
- Google Cybersecurity Action Team Threat Horizons Report #7 Is Out!
- Google Cybersecurity Action Team Threat Horizons Report #6 Is Out!
- Google Cybersecurity Action Team Threat Horizons Report #5 Is Out!
- Google Cybersecurity Action Team Threat Horizons Report #4 Is Out!
- Google Cybersecurity Action Team Threat Horizons Report #3 Is Out!
- Google Cybersecurity Action Team Threat Horizons Report #2 Is Out!
- Illicit coin mining, ransomware, APTs target cloud users in first Google
- Cybersecurity Action Team Threat Horizons report
- All past and future reports are posted at Google Cybersecurity Action Team site.
*** This is a Security Bloggers Network syndicated blog from Dr Anton Chuvakin Blog (Original) authored by Anton Chuvakin. Read the original post at: http://chuvakin.blogspot.com/2023/11/google-cybersecurity-action-team-threat.html