2023-11-6 16:44:0 Author: paper.seebug.org(查看原文) 阅读量:26 收藏
Author: Knownsec 404 Team
Chinese version: https://paper.seebug.org/3062/
一.Abstract
There are numerous VPN nodes in the cyberspace, and what kind of organizations or individuals are behind these VPN nodes? What do they do with VPN nodes?
This article applies the concepts of "behavioral mapping" and "cross-mapping" in practice, taking SoftEther VPN nodes as an example. By identifying the characteristics of SSL certificates used by VPN nodes, the organizations behind VPNs are categorized. With the data from the ZoomEye cyberspace search engine [3] andKNOWNSEC SAFETY BRAIN [4], the article analyzes and studies the network behaviors of certain organizations from a data analysis perspective.
The identified "xxh organization" and "LiuChang organization" are presumed to be active black-gray hat organizations in mainland China.
-
Most of the IP addresses used by these two organizations' VPN nodes are flagged as threat IPs by knownsec's Threat Intelligence Platform (as they have initiated network attack requests within the past three months).
-
These two organizations primarily use VPN nodes for bulk malicious web page data scraping and crawling. They also engage in malicious scans and vulnerability attacks targeting specific websites. It is inferred that their intent is to sell the acquired data for profit.
-
The majority of VPN nodes are home routers and cameras. It is speculated that these two organizations exploit vulnerabilities in compromised home routers and cameras, install SoftEther VPN software, and utilize them as springboards for conducting network attack activities. Home routers and cameras are easier for organizations to control over an extended period since very few home users are conscious or capable of performing security checks on their home network devices.
-
By utilizing the network asset characteristics of these two organizations, it is possible to expand the discovery of additional network assets. Although these discovered network assets may not be VPN nodes, the majority of them are employed by the organizations for conducting network attack activities.
Without having access to dedicated malicious samples from these organizations, analysis based on cyberspace mapping data and KNOWNSEC SAFETY BRAIN data can classify VPN nodes used by black-gray hat organizations and subsequently analyze the network behaviors of these VPN nodes. This demonstrates that utilizing "behavioral mapping" and "cross-mapping" in cyberspace for feature analysis of black-gray hat organizations can compensate for the shortcomings of relying solely on traditional malicious sample analysis, such as incomplete coverage and inaccurate classification.
二.SoftEther VPN Nodes
On the ZoomEye cyberspace search engine platform, using the following search query, we obtained data on SoftEther VPN nodes surveyed in mainland China after January 1st, 2023 (search conducted on September 25th, 2023).
title:"SoftEther VPN Server" +country:"CN" -subdivisions:"hong kong" -subdivisions:"taiwan" -subdivisions:"macau" +after:"2023-01-01"
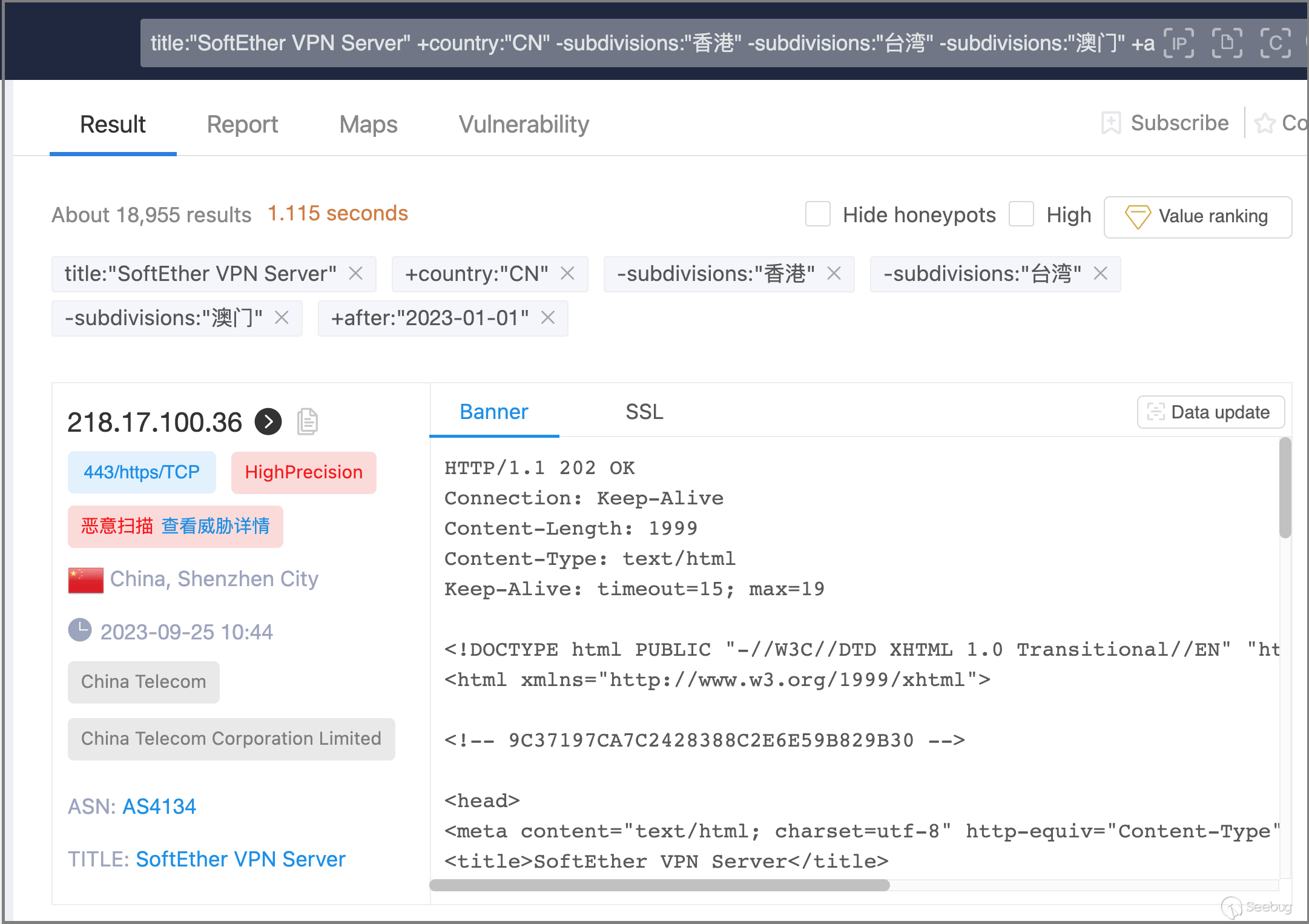
After removing duplicates, we obtained a total of 16,582 IP addresses of SoftEther VPN nodes. Next, we will analyze and study the relevant information regarding these IP addresses.
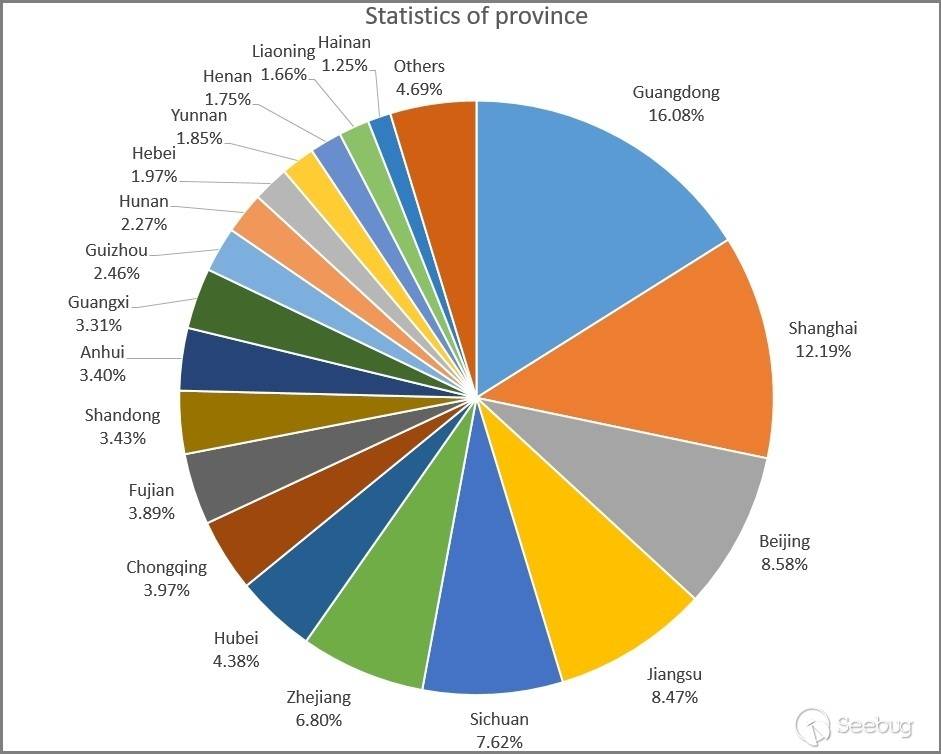
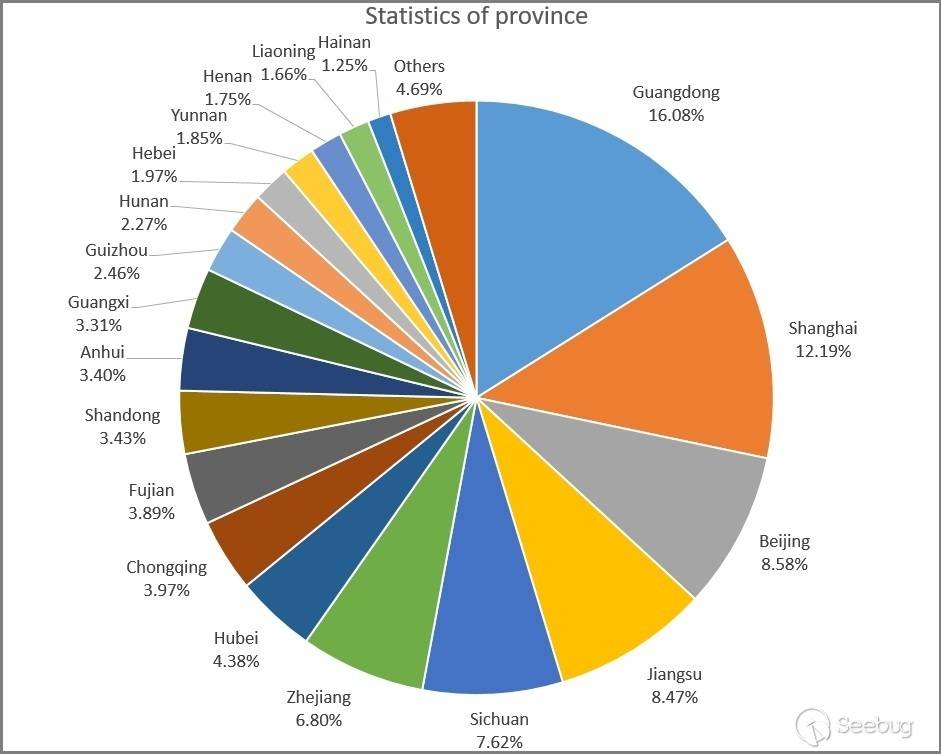
2.1 Geographical Distribution
Examining the geographical distribution of these IPs, as shown in the graph below, we can observe that a significant number of them are located in economically developed provinces and cities. This distribution is similar to the overall geographical distribution of ordinary IP addresses.
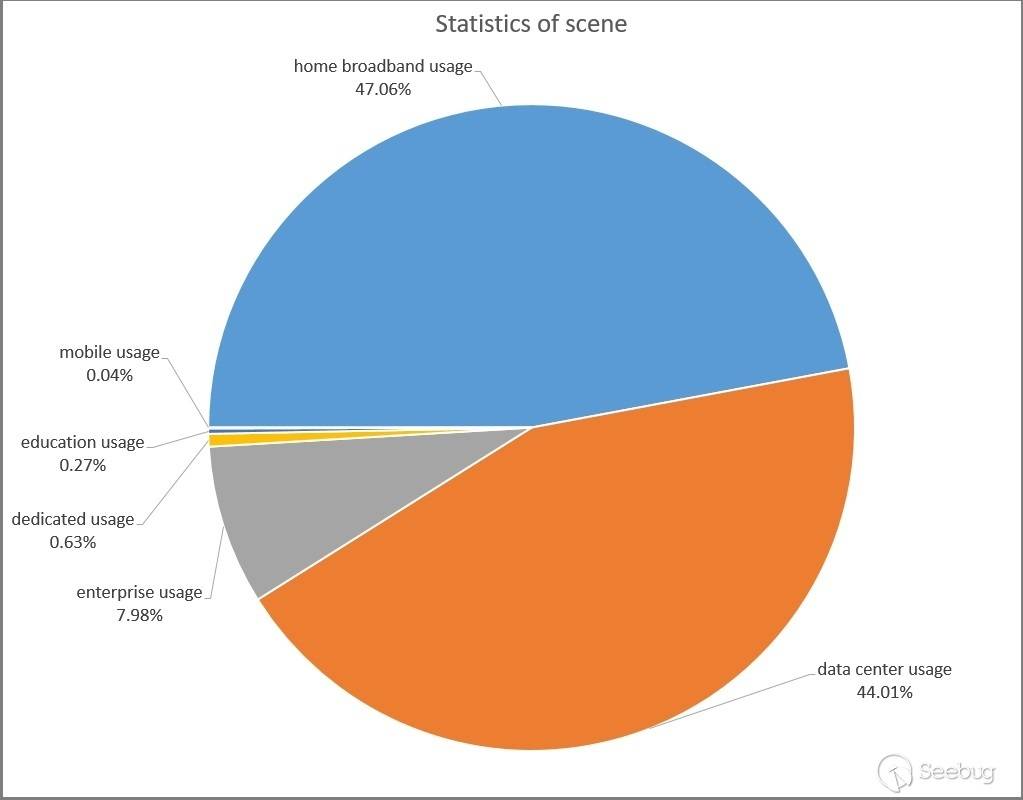
2.2 Application Scenarios
Looking at the application scenarios of these IPs, as presented in the graph below, the majority of them are utilized in home broadband and data centers.
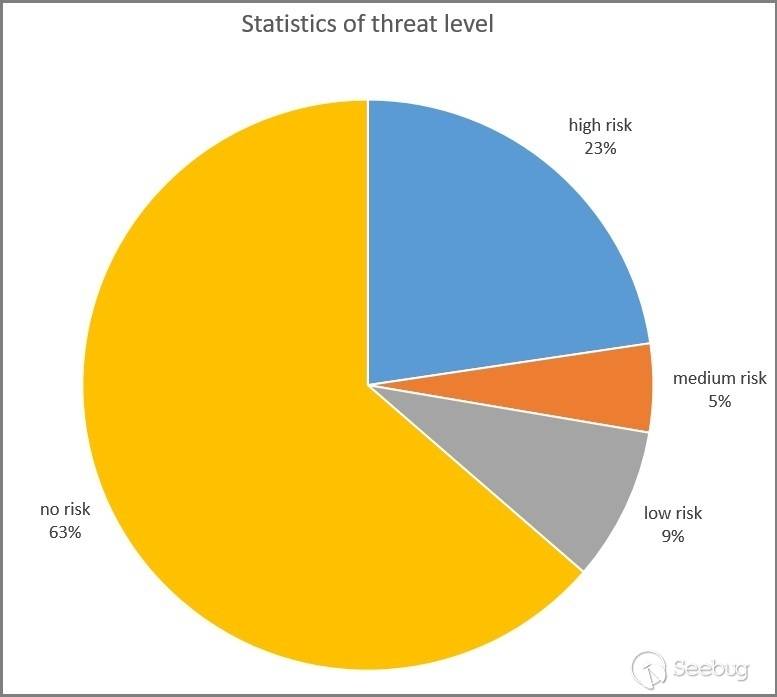
2.3 Security Threat Level
Using KNOWNSEC SAFETY BRAIN, we examined the threat level of these 16,582 SoftEther VPN node IP addresses. The graph below illustrates the distribution of threat levels. A higher threat level indicates that the IP address has initiated a greater number of network attacks in recent months, targeting more valuable assets, and employing more advanced attack techniques.
From the graph, we can observe that 37% of SoftEther VPN node IP addresses are marked as threat IPs, indicating that these IPs have launched network attack requests within the past three months. This suggests a relatively high proportion of users engaging in network attacks among SoftEther VPN users.
2.4 Certificate Issuers
Accessing the "Search Aggregation Analysis" page on the ZoomEye cyberspace search engine, we entered the search query mentioned at the beginning of this chapter in the search box and selected "ssl_issuer" in the aggregation field to view information about the SSL certificate issuers used by these IP addresses, as shown in the graph below. It can be observed that the majority of these SSL certificates are self-signed certificates (SoftEther VPN software includes a self-signing certificate capability).
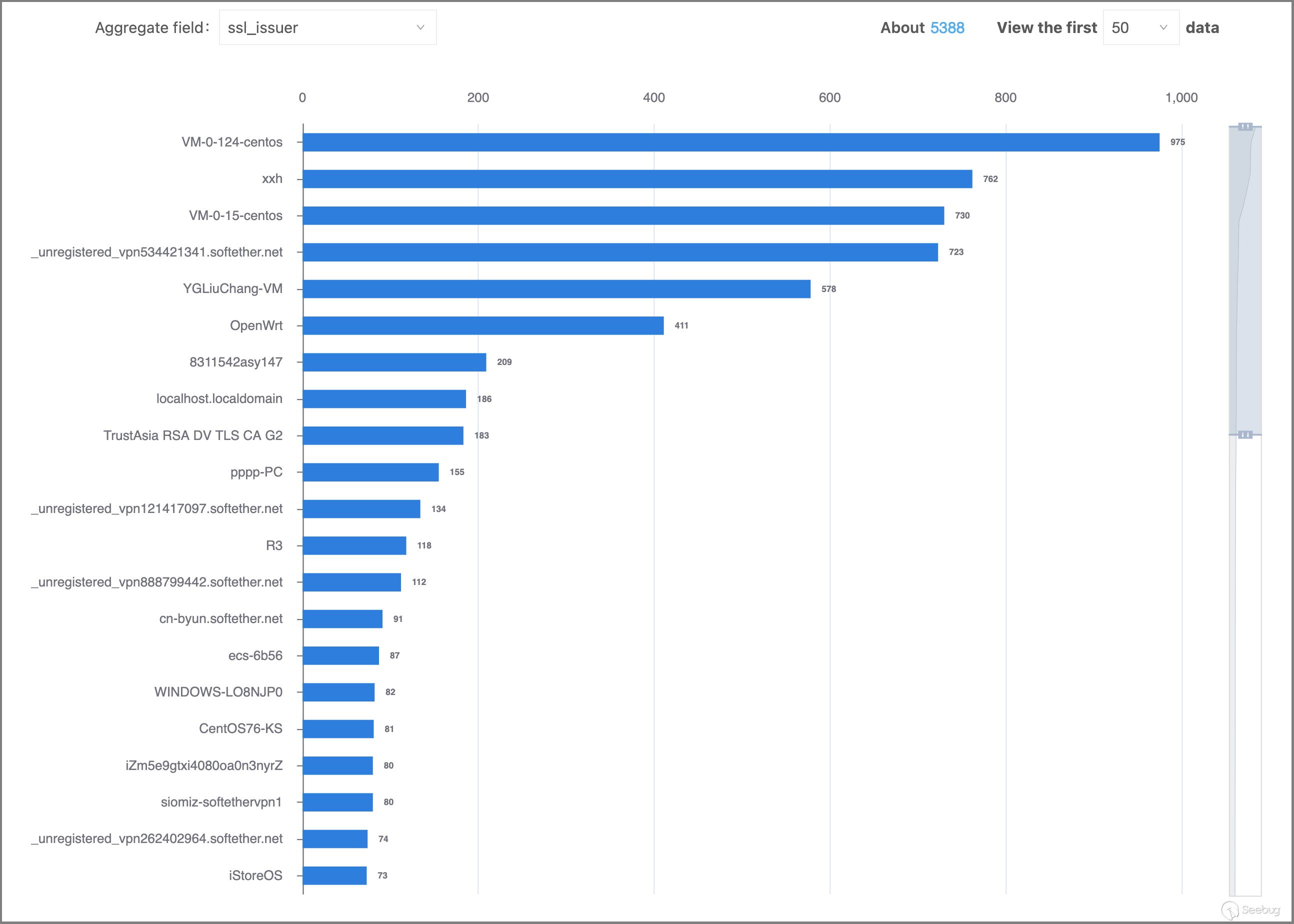
Among the top-ranked values in terms of quantity, some exhibit distinct differentiating features, such as "xxh," "YGLiuChang-VM," "YG-LiuChang64," and "VM-0-124-centos." We will conduct focused analysis on these in subsequent chapters.
3. "xxh Organization"
From the SoftEther VPN node data, we filtered out the data with the "ssl_issuer" field set to "xxh." After removing duplicates, we obtained 726 unique IP addresses of SoftEther VPN nodes with the "ssl_issuer" field as "xxh."
Since the value of the "ssl_issuer" field in the SSL certificate is manually set as "xxh," we consider these 726 SoftEther VPN node IPs to belong to the same organization (referred to as the "xxh organization" hereafter).
Next, we will analyze and study the relevant information regarding the 726 IP addresses associated with the "xxh organization."
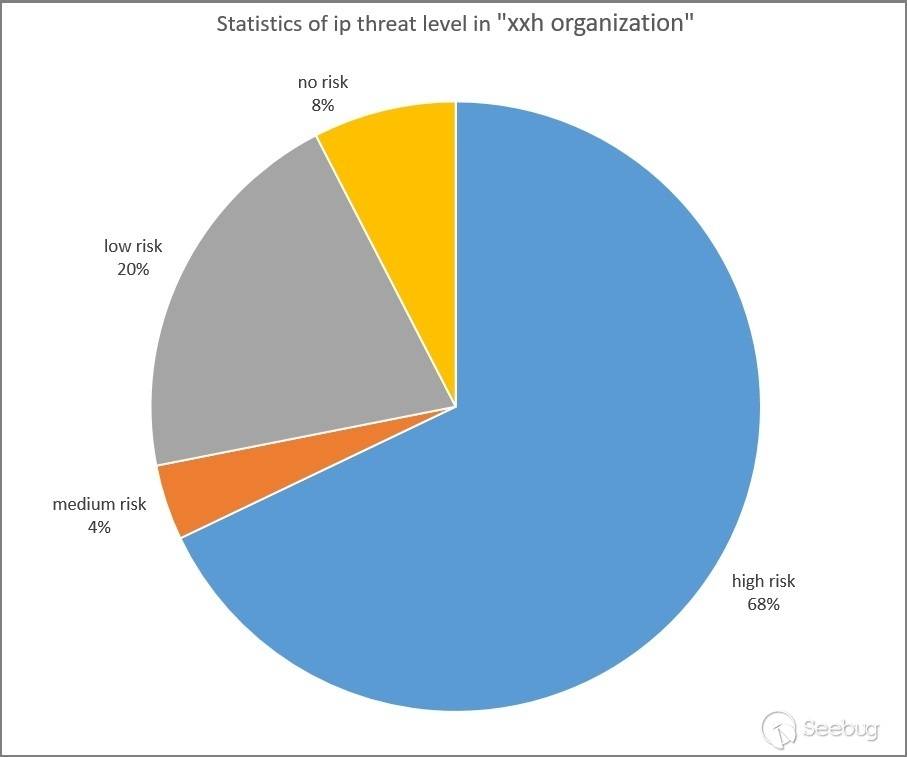
3.1 Threat Level
Using the KNOWNSEC SAFETY BRAIN, we examined the threat level of the 726 IP addresses associated with the "xxh organization." As shown in the graph below, it can be observed that 671 IP addresses were marked as threat IPs, accounting for 92% of the total. This indicates that the organization is highly likely to be involved in conducting network attack activities.
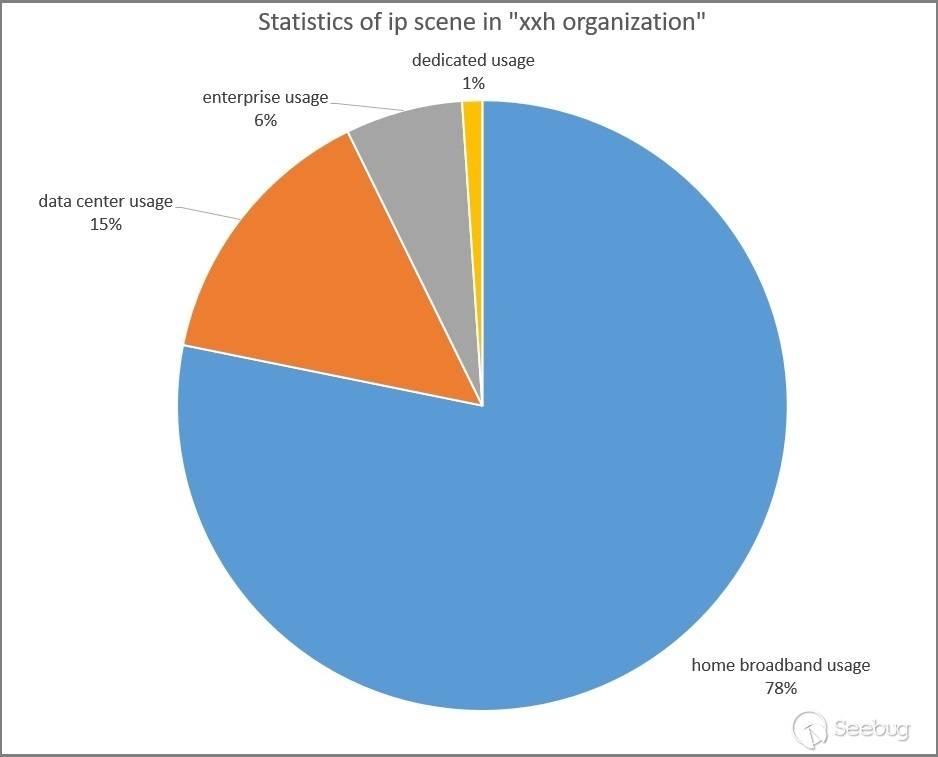
3.2 Application Scenarios
We examined the application scenarios of the 671 threat IP addresses associated with the "xxh organization," as shown in the following figure. The majority of these IP addresses are associated with home broadband, accounting for 78%. By querying network assets with the application scenario of home broadband IP addresses using the ZoomEye network space search engine platform, it was discovered that most of them are home routers and cameras. This suggests that the organization attacks vulnerable home routers and cameras, installs Softether VPN software on them, and uses them as jumping-off points for launching network attacks.
3.3 Attack Targets
Using the KNOWNSEC SAFETY BRAIN, we analyzed the attack log data of the 671 threat IP addresses associated with the "xxh organization" between September 1, 2023, and September 25, 2023, to determine their attack targets.
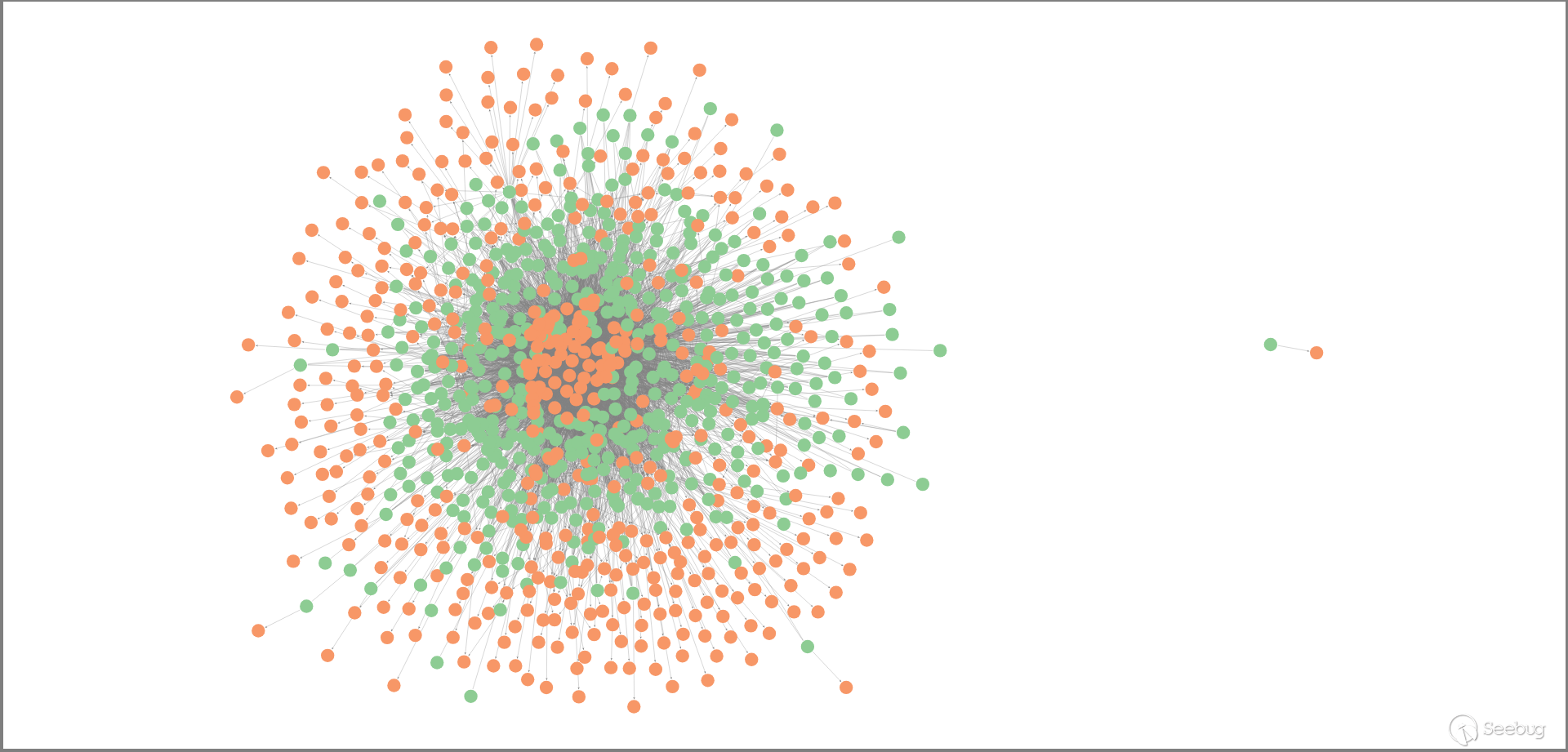
During this period, it was found that 598 IP addresses attacked 524 sites, as shown in the following figure. The green dots represent IP addresses, the orange dots represent websites, and the lines between them indicate that the corresponding IP addresses have attacked the sites.
From the figure, it can be observed that only one IP address has independent attack data, while the remaining IP addresses and attack targets are interconnected, indicating that these IP addresses are used by the same organization. Therefore, it can be inferred that these IP addresses belong to the same organization.
3.4 Attack Details
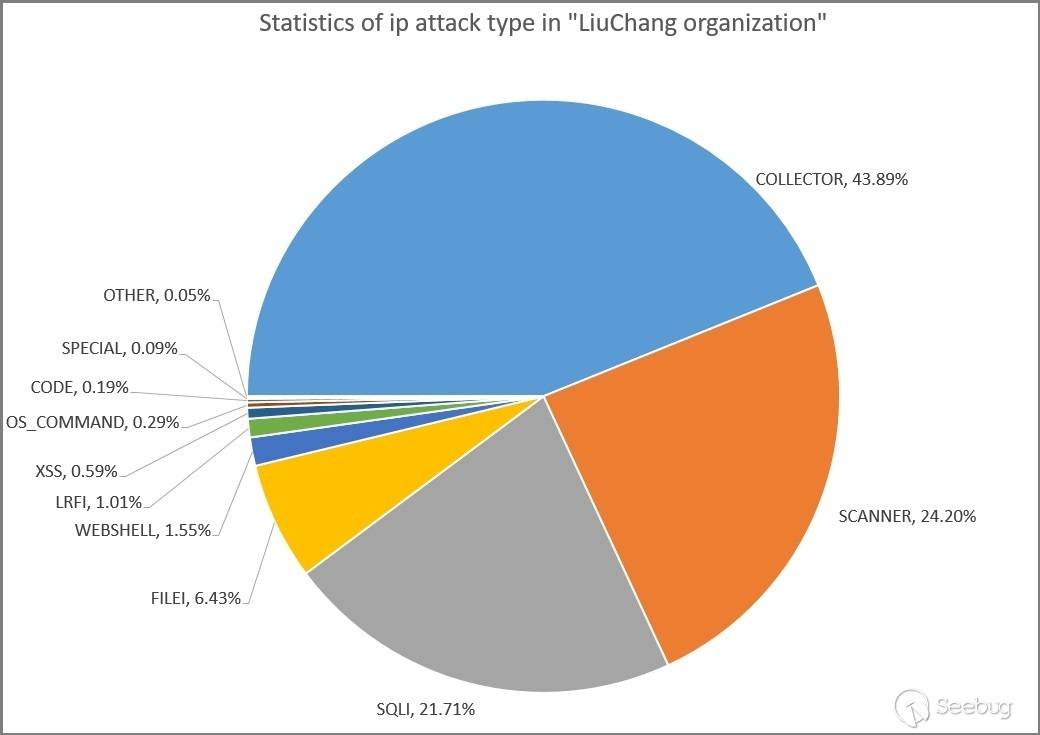
Using the KNOWNSEC SAFETY BRAIN, we analyzed the attack log data of the 671 threat IP addresses associated with the "xxh organization" and determined the percentage of different attack types, as shown in the following chart.
The main attack request types used by the "xxh organization" are: malicious collection (63.56%), malicious scanning (19.47%), and SQL injection attacks (10.75%). This indicates that the organization utilizes these VPN nodes primarily for large-scale malicious data collection through script programs, as well as malicious scanning and targeted vulnerability attacks on websites.
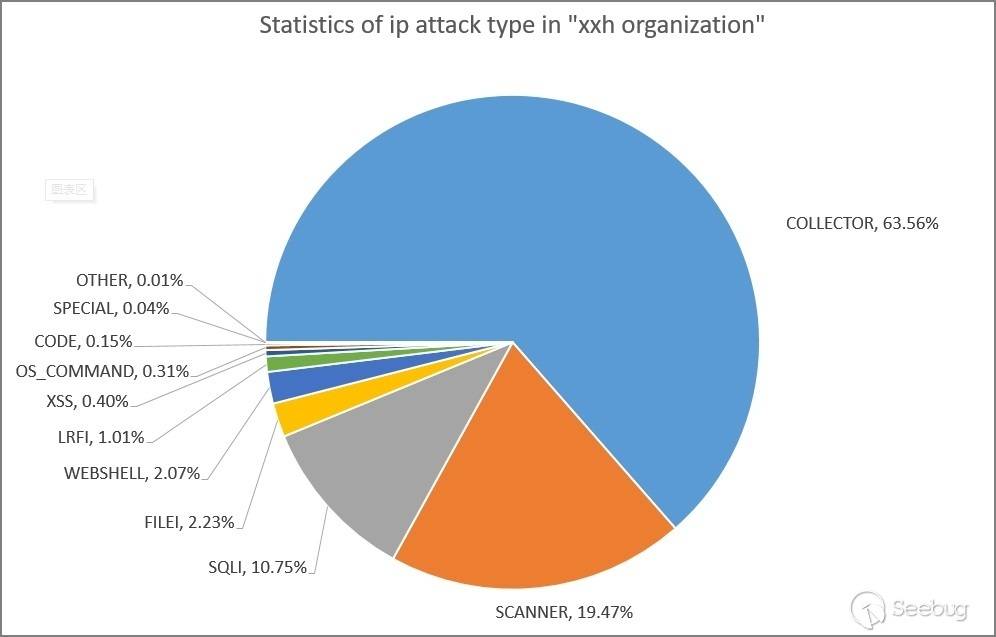
| Attack Type Percentage | Attack Type (English) | Attack Type (Chinese) | Attack Type Description [4] |
|---|---|---|---|
| 63.56% | COLLECTOR | Malicious Data Collection | Malicious data collection, where hackers utilize programs to collect and extract web page data in large quantities. |
| 19.47% | SCANNER | Malicious Scanning | Malicious scanning, typically conducted by non-browser machines accessing the target. |
| 10.75% | SQLI | SQL Injection Vulnerability Attack | SQL Injection Vulnerability Attack |
| 2.23% | FILEI | Sensitive file access | Sensitive file or directory access attack, such as log file access. |
| 2.07% | WEBSHELL | Website Backdoor Attack | Website Backdoor Attack |
| 1.01% | LRFI | File Inclusion Vulnerability Attack | Local/Remote File Inclusion Vulnerability Attack |
| 0.40% | XSS | Cross-Site Scripting (XSS) Attack | Cross-Site Scripting (XSS) Attack |
| 0.31% | OS_COMMAND | Arbitrary Command Execution Vulnerability Attack | Arbitrary Command Execution Vulnerability Attack |
| 0.15% | CODE | Arbitrary Code Execution Vulnerability Attack | Arbitrary Code Execution Vulnerability |
| 0.04% | SPECIAL | Specialized Attack | This is marked for specific vulnerabilities (such as exploiting a vulnerability in Discuz), without specifically referring to a particular type of attack |
| 0.01% | OTHER | Other Attack | Other Attack |
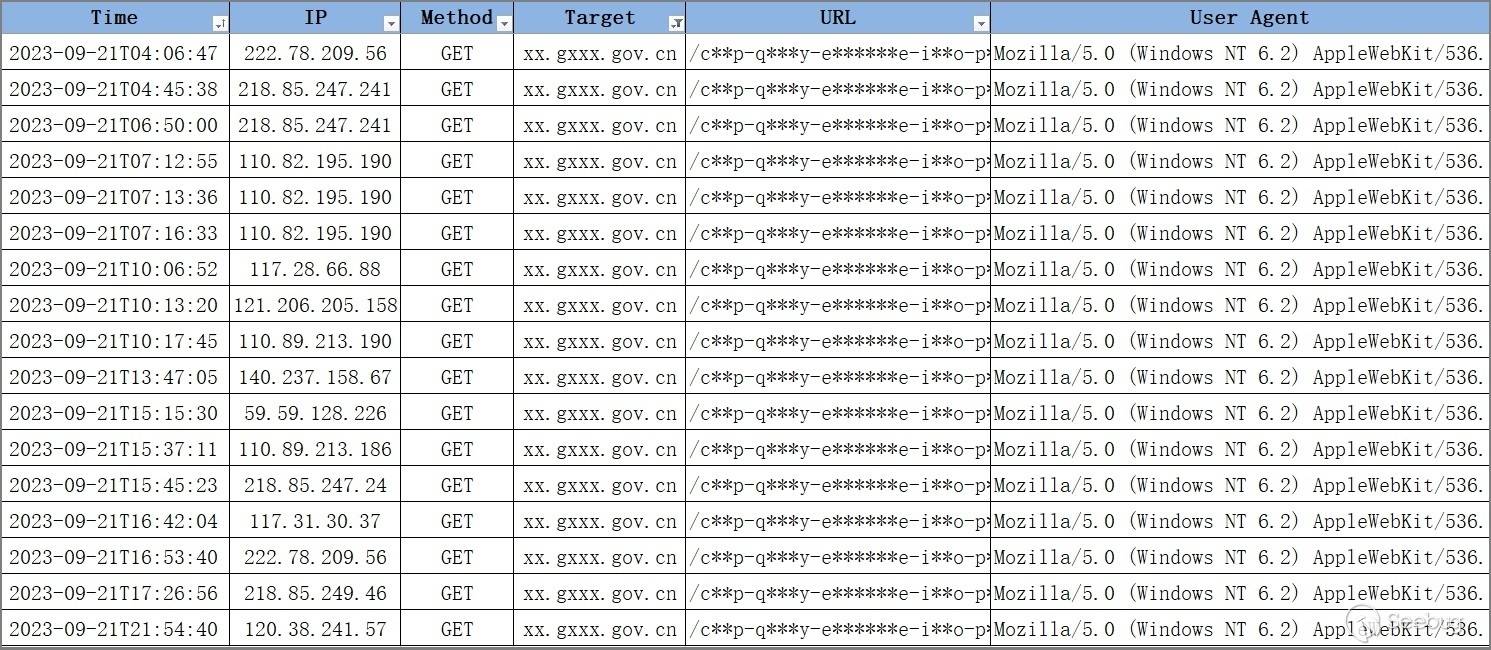
From the attack log data, select attack requests with the same date, the same target domain, and the same User Agent, as shown in the example data below. Although the source IP addresses of these attack requests are different, the target URL is same, with only the Payload parameter being different. It can be inferred that these attack requests are initiated by the same organization. This inference can be corroborated by the fact that the 'ssl_issuer' field value of the Softether VPN node IP is 'xxh' and belongs to the same organization.
3.5 "Expand an organization's network assets
Using the asset feature of "ssl_issuer" with the field "xxh", we tried to expand the ZoomEye cyberspace search engine to find more "xxh Organization "web assets using the following search statement:
ssl:"Issuer: CN=xxh" +after:"2023-01-01" -title:"SoftEther VPN Server"
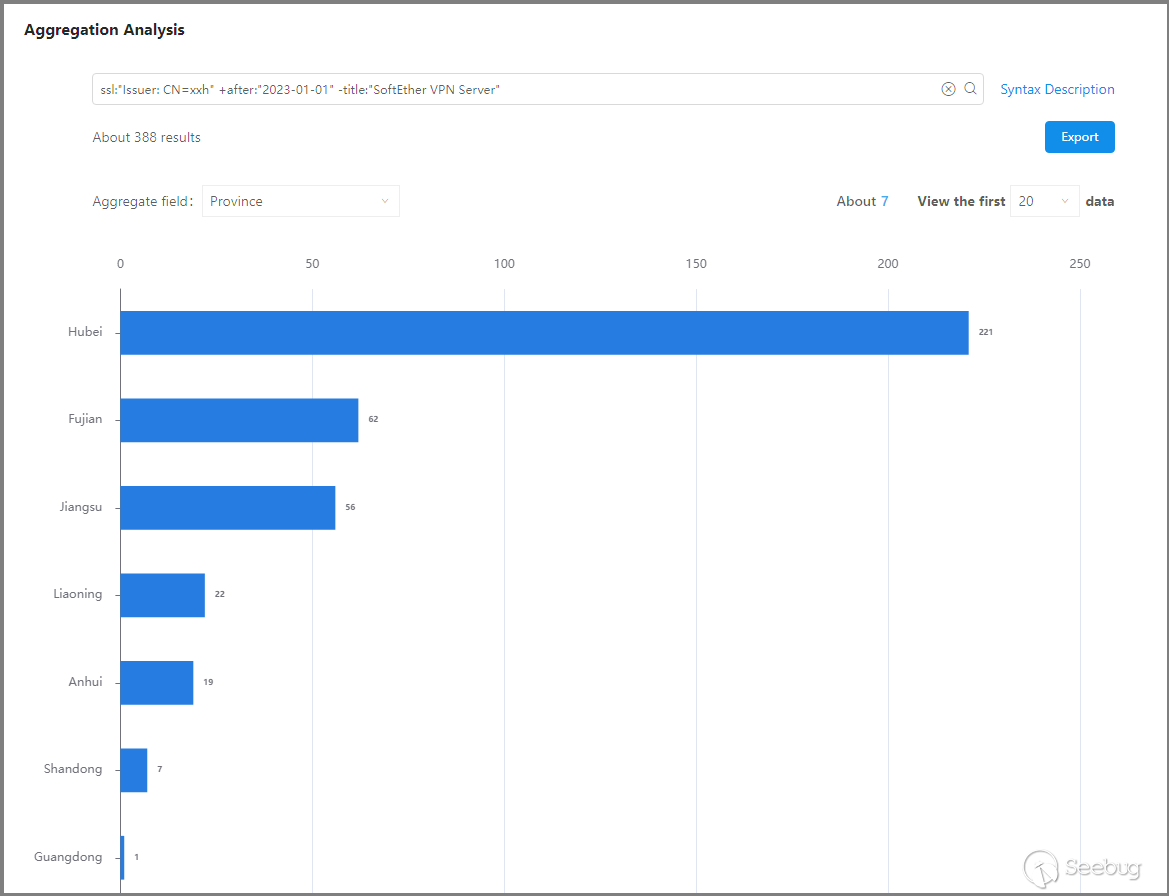
Expanding the investigation revealed 388 network assets, and based on the analysis of port usage and geographical distribution (country/province), it was found that all of these network assets are located in mainland China. Among them, two ports are open: 3389 (Remote Desktop Services) and 5555 (rplay service). This indicates that the "xxh organization" operates within mainland China, and their dedicated certificates are not only used on SoftEther VPN nodes but also on network assets with Remote Desktop Services and rplay services enabled.
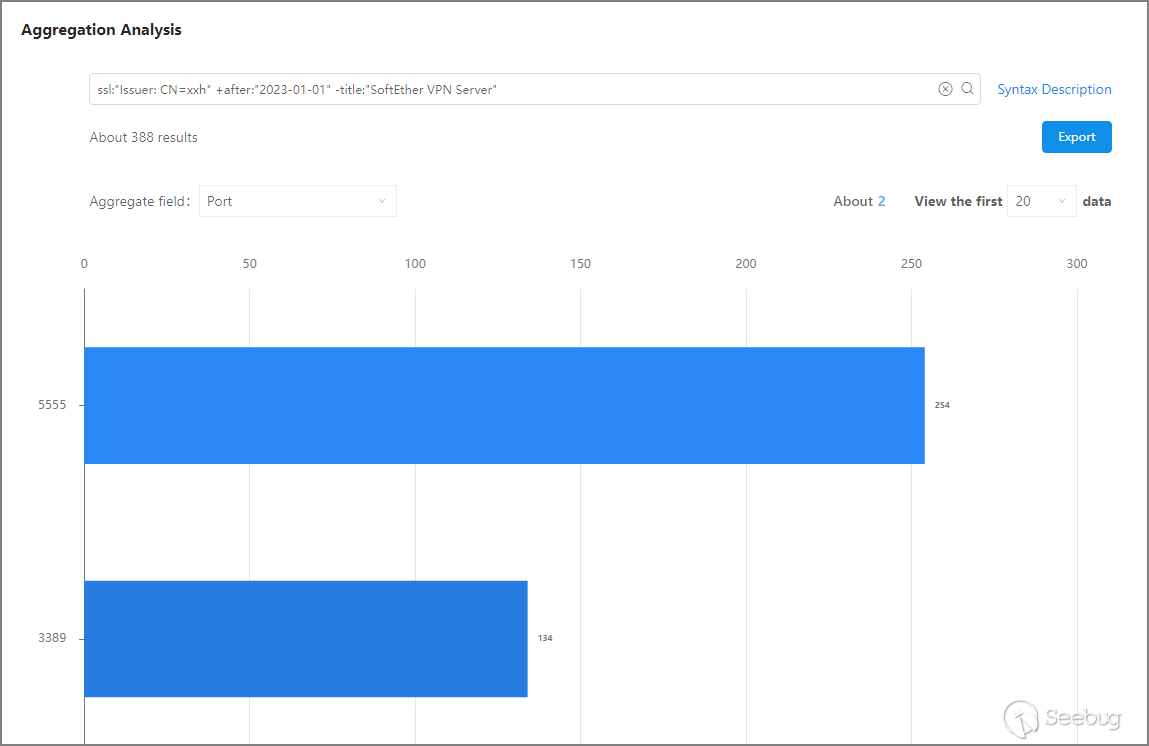
After the IP addresses of these network assets are duplicated, 361 IP addresses are obtained. Using KNOWNSEC SAFETY BRAIN to check its threat level, it was found that 331 IP addresses were marked as threat IP, accounting for 91%. It shows that most of the expanded network assets of "xxh organization" are used by organizations to carry out cyber attacks.
4. "Liuchang Organization"
We screened out the data with "ssl_issuer" fields of "YGLiuChang-VM" and "YG-LiuChang64" from the SoftEther VPN node data. After these IPS are duplicated, 643 IP addresses are obtained.
The value of "ssl_issuer" field in SSL certificate is artificially set to "YGLiuChang-VM" and "YG-LiuChang64", and the "YGLiuChang" string contained in these two values is a non-universal string, so we think that these 643 SoftEther VPN node IPS belong to the same organization (following referred to as "LiuChang organization").
Next, we analyze the information about 643 IP addresses of "LiuChang Organization".
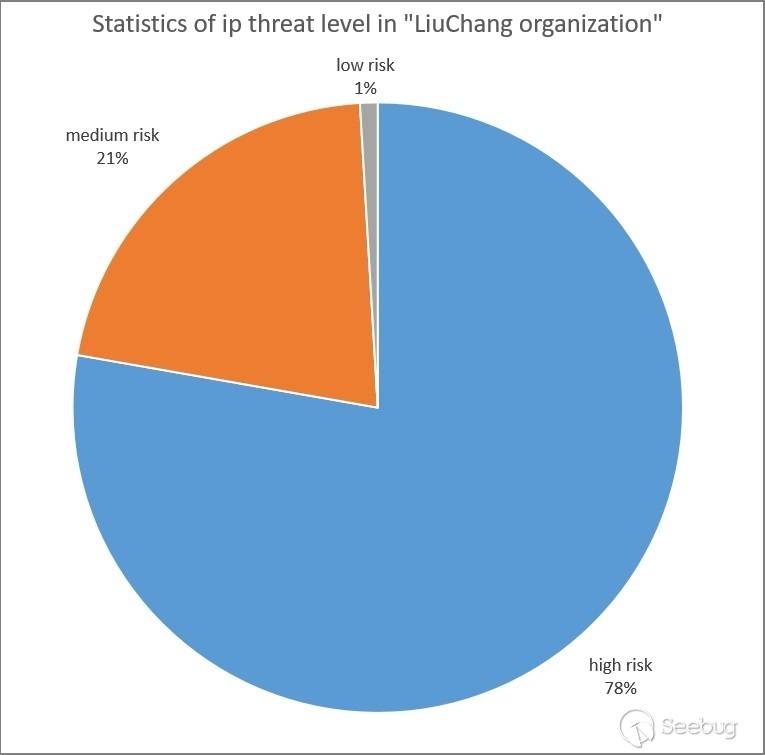
4.1 Security Threat Level
Use KNOWNSEC SAFETY BRAIN to check the threat level of 643 IP addresses of "LiuChang Organization", as shown in the figure below. These 643 IP addresses are all marked as threat IP, among which high-risk IP accounts for 78%. It shows that the organization is an organization that carries out cyber attacks with high probability.
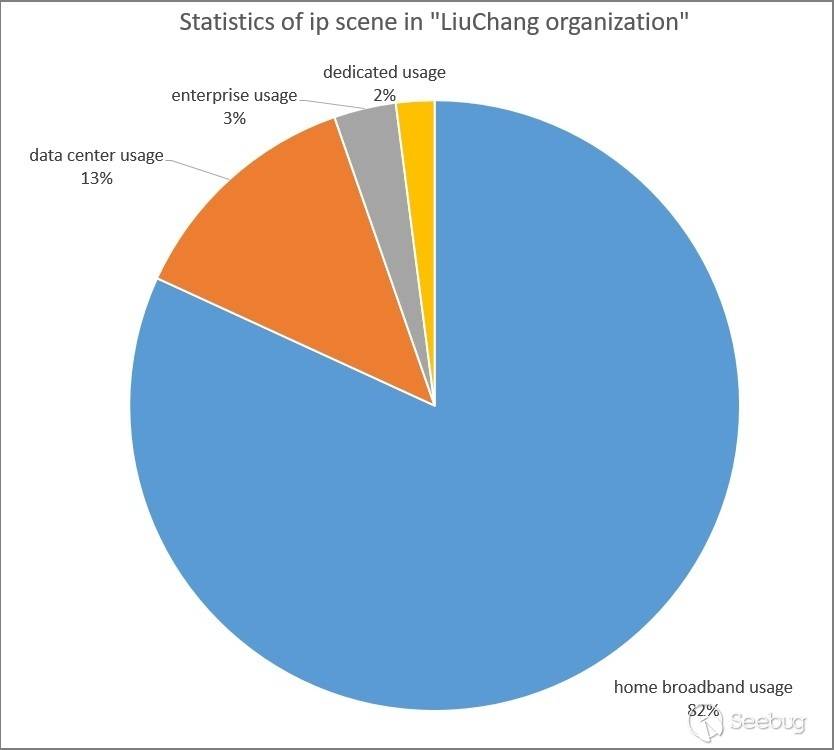
4.2 Application Scenario
Check the 643 IP application scenarios of LiuChang Organization, as shown in the following figure. Home broadband has the largest number of IPS, accounting for 82%; Most of them are routers and cameras.
This situation is basically same as "xxh organization" in the previous chapter. It is inferred that these organizations attack home routers and cameras with loopholes in control, install Softether VPN software, and then use them as springboard to launch network attacks. Home routers and cameras are easier to be controlled by organizations for a long time. After all, few home users have the consciousness and ability to check the safety of home network equipment.
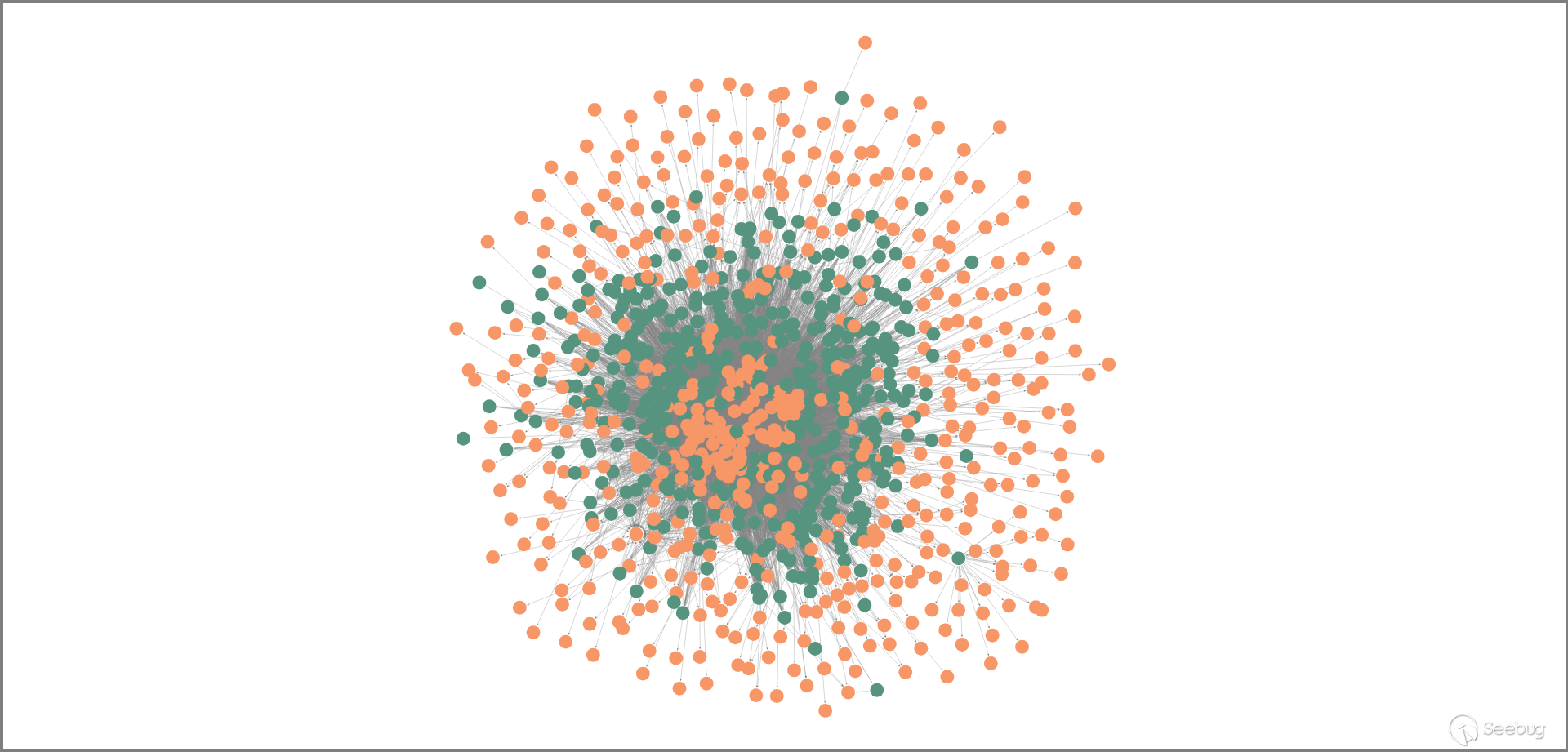
4.3 Attacking sites
Using KNOWNSEC SAFETY BRAIN,the attack log data of 643 IPs of "LiuChang Organization" from September 1, 2023 to September 25, 2023 were checked, and the attack sites were counted.
From September 1, 2023 to September 25, 2023, it was found that 603 IP addresses attacked 568 sites, as shown in the following figure. In the figure, the green dot represents an IP address, the orange dot represents a site, and the connection between the two points indicates that the IP address has attacked the site.
As can be seen from the figure, some sites are only associated with one attack IP address, but most IP addresses are associated with the attack sites, indicating that these IP addresses are used to attack the same batch of sites. Therefore, we infer that these IP addresses are used by the same organization。
4.4 Attack Details
Using KNOWNSEC SAFETY BRAIN, we checked the attack log data of 643 IP of "LiuChang Organization", found that the proportion types of attack requests was similar to that of "xxh Organization", and the top three were still malicious collection, malicious scanning and SQL injection vulnerabilities.
4.5 Expanding organizational network assets
We try to use the asset characteristics of "ssl_issuer" fields as "YGLiuChang-VM" and "YG-LiuChang64" to expand and find more "LiuChang Organization" network assets on the ZoomEye cyberspace search engine. The search sentences used are as follows:
(ssl:"Issuer: C=US,CN=YGLiuChang-VM,O=YGLiuChang-VM,OU=YGLiuChang-VM" ssl:"Issuer: C=US,CN=YG-LiuChang64,O=YG-LiuChang64,OU=YG-LiuChang64") +after:"2023-01-01" -title:"SoftEther VPN Server"
Expanded discovery found 114 network assets, through analysis of port and country/province distribution, it was found that these network assets are all located in mainland China, with the same open port: 5555 (rplay service). This indicates that the "LiuChang Organization" operates within mainland China, and their dedicated certificates are not only used on SoftEther VPN nodes but also on network assets with the rplay service enabled.
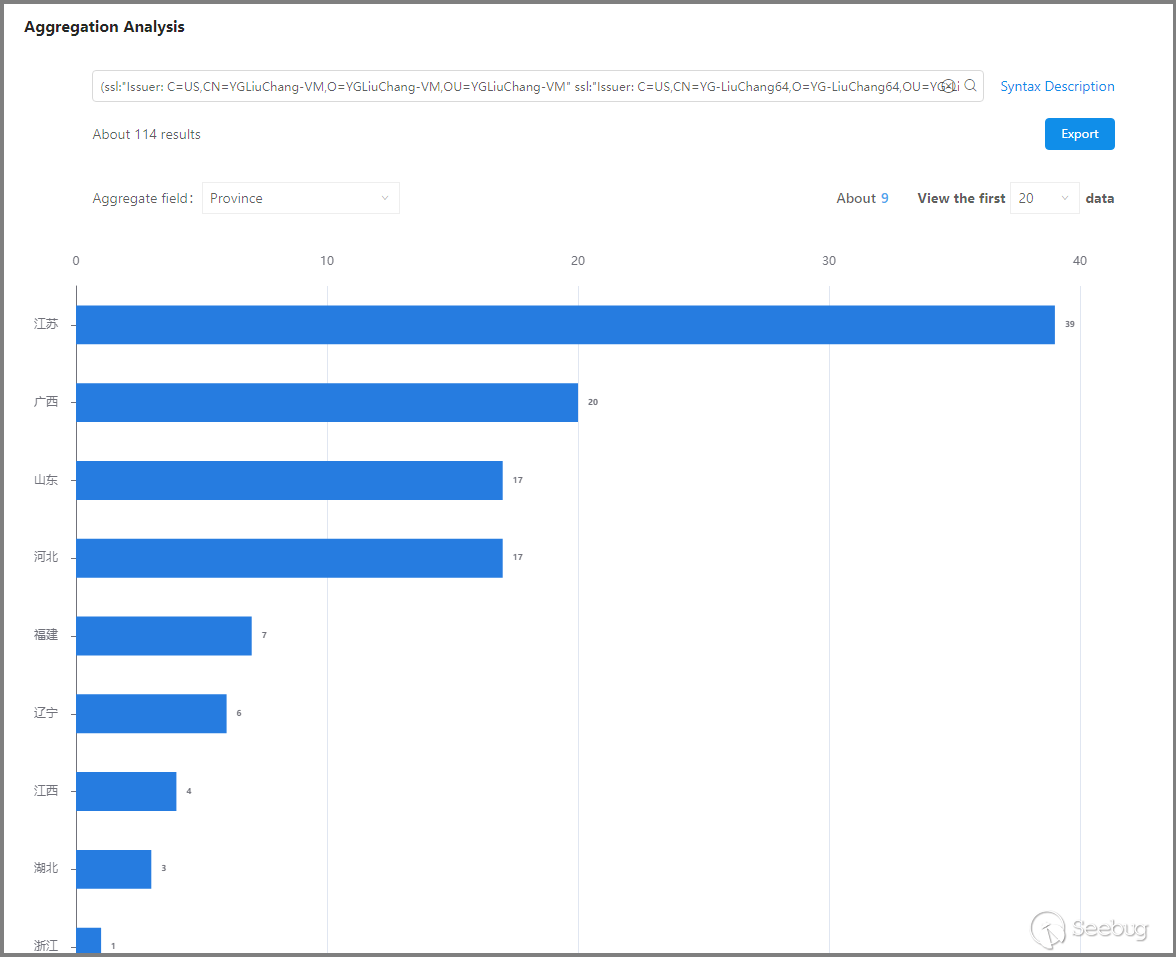
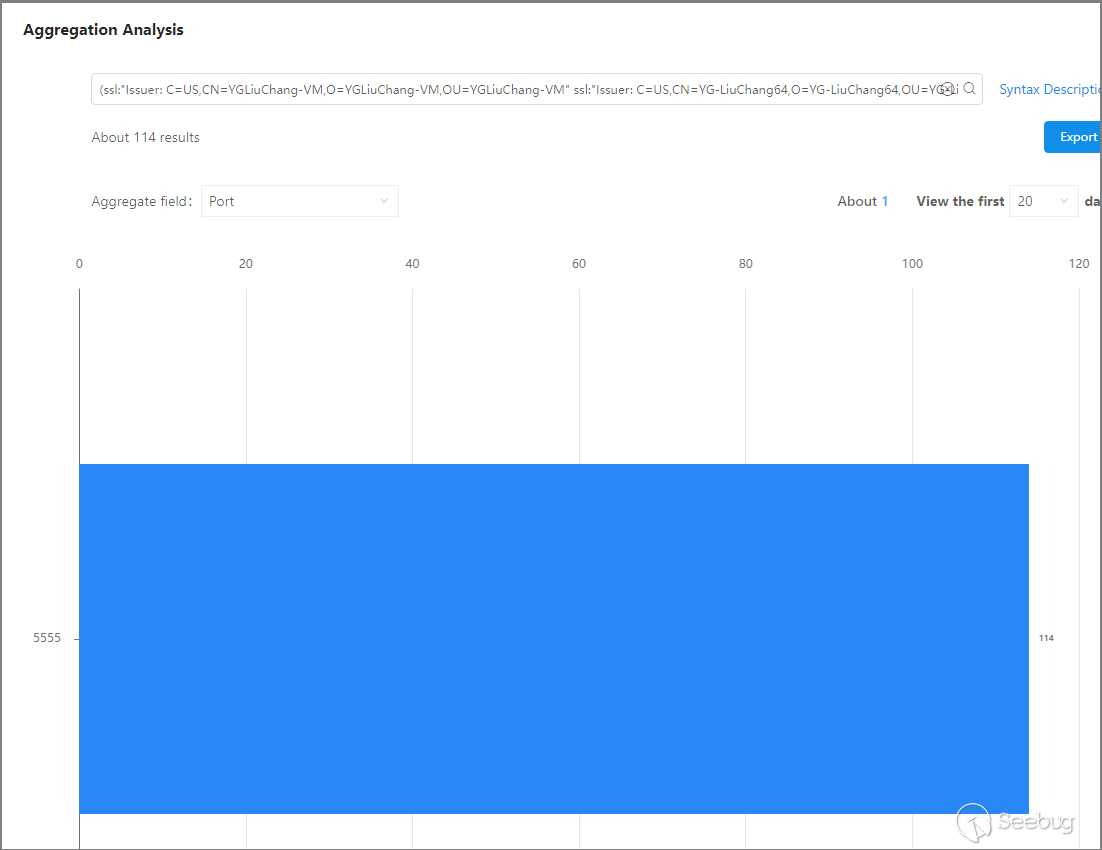
After the IP addresses of these network assets are duplicated, 114 IP addresses are obtained. Using KNOWNSEC SAFETY BRAIN to check its threat level, we found that 111 IP addresses were marked as threat IP, accounting for ninety-seven percent. It shows that most of the expanded "LiuChang Organization" network assets are used by organizations to carry out cyber attacks.
We screened out the data with the field of "ssl_issuer" as "VM-0-124-centos" from the SoftEther VPN node data. After these IP addresses are de-duplicated, 623 IP addresses are obtained.
We believe that these 623 SoftEther VPN node IPS belong to the same organization (following referred to as "VM124 organization").
Looking at 623 IP application scenarios and IP affiliated institutions, it is found that all the application scenarios are "data centers" and all the affiliated institutions are "Tencent Company". Using KNOWNSEC SAFETY BRAIN, the threat level of 623 IP addresses is checked, and it is found that 96% IP addresses are non-threatening. Therefore, we speculate that "VM124 organization" is an enterprise that uses Tencent Cloud services, and these VPN nodes are used by its own normal business.
In the process of configuring the SoftEther VPN node certificate, different organizations will show different unique characteristics. We use these behavioral characteristics to analyze the cyberspace mapping data, which is the concept of "behavioral mapping".
This paper is based on the concept of "behavioral mapping", combined with "cross-mapping", using the data of ZoomEye cyberspace search engine and Chuangyu Security Intelligence, and analyzing the SoftEther VPN node; Based on the characteristics of SSL certificate issuers used by VPN nodes, two suspected black and gray organizations are identified, and the behavior of organizations using these VPN nodes to carry out network attacks is found.
The method for the black-and-white organization to obtain the control rights of these VPN nodes can be control the network devices such as computers, servers and IOT through vulnerability attacks, and then install VPN software; It is also possible to spread VPN software installation programs and Docker images with hidden backdoors through supply chain attacks, to lure netizens to download, install and use them, and then gain control through the back door.
Without obtaining organization-specific malicious samples, through the analysis of cyberspace mapping data and KNOWNSEC SAFETY BRAIN, VPN nodes used by black and gray organizations can be classified, and then the network behavior of these VPN nodes can be analyzed. It shows that analyzing the characteristics of black ash production tissues based on "behavior mapping" and "cross mapping" in cyberspace can make up for the shortcomings of incomplete coverage and inaccurate classification existing in traditional analysis relying solely on malicious samples.
-
Talking about "Behavior Mapping" in cyberspace https://mp.weixin.qq.com/s/Rbzsq7rgggQekvYxj4t9kA
-
Discussing "Cross-Mapping" and Tracing in cyberspace https://mp.weixin.qq.com/s/QTyfHbcnoMYoVUXhcbCYCw
-
ZoomEye Cyberspace Search Engine https://www.zoomeye.org
-
KNOWNSEC SAFETY BRAIN https://gac.yunaq.com
-
Explanation and Illustration of Attack Types https://help.yunaq.com/faq/334/index.html
 本文由 Seebug Paper 发布,如需转载请注明来源。本文地址:https://paper.seebug.org/3063/
本文由 Seebug Paper 发布,如需转载请注明来源。本文地址:https://paper.seebug.org/3063/
如有侵权请联系:admin#unsafe.sh