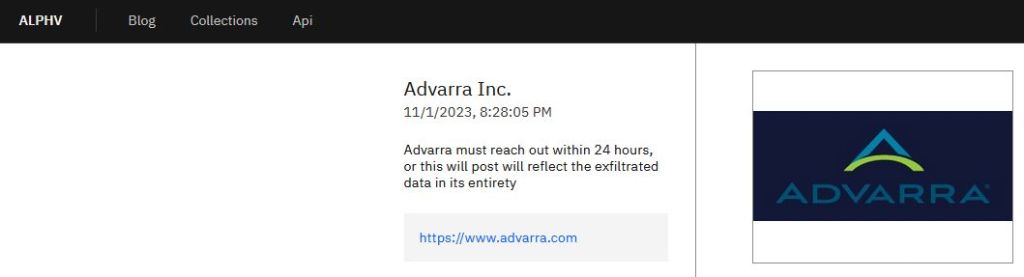
Clinical research company Advarra has reportedly been compromised after a SIM swap on one of their executives.
SIM swapping, also known as SIM jacking, is the act of illegally taking over a target’s cell phone number. This can be done in a number of ways, but one of the most common methods involves tricking the target’s phone carrier into porting the phone number to a new SIM which is under the control of the attacker.
In the case of Advarra, the ransomware group ALPHV reportedly managed to transfer the executive’s cellphone number, allowing them access to the company’s resources and copy information that the group is now threatening to sell.
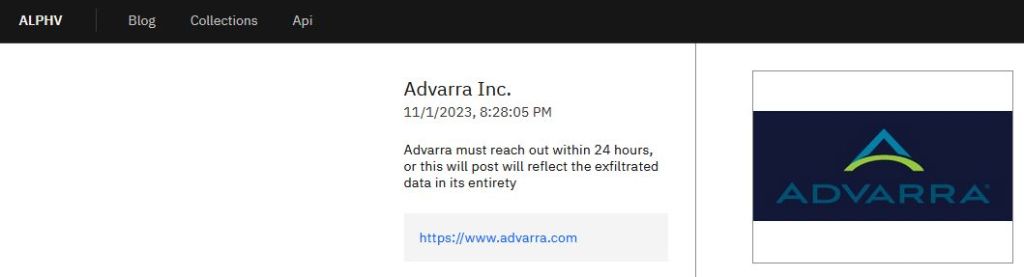
Advarra entry on the ALPHV leak site
However, Advarra isn’t willing to play ball, saying it doesn’t “pay digital terrorists”.
Advarra said it’s business as usual:
“An Advarra colleague was the victim of a compromise of their phone number. The intruder used this to access some of the employee’s accounts, including LinkedIn, as well as their work account.
We have taken containment actions to prevent further access and are investigating with third-party cyber experts. We also notified federal law enforcement. At this time we believe the matter is contained. We further believe that the intruder never had access to our clients’ or partners’ systems and it is safe to connect to Advarra’s systems. Importantly, we have no evidence that the Advarra systems and products that clients use to interface with us were compromised or accessed. At this time, our business operations have not been disrupted as a result of this activity and we continue to operate as normal. In addition, we continue to take steps to enhance the overall security of our systems in line with industry best practices.
Our investigation remains ongoing, and we will provide additional updates as appropriate.”
Octo Tempest
We recently wrote about the growing concern around criminal gang Octo Tempest. In 2022, Octo Tempest began selling SIM swaps to other criminals and performing account takeovers of high-net-worth individuals in order to steal their cryptocurrency. Since then the group has expanded its range of activities to include targeting organizations providing cable telecommunications, email, and tech services, and partnering with the ALPHV ransomware group.
So it’s quite possible that here Octo Tempest used their SIM swapping knowledge to compromise the executive’s account and use that leverage to steal information, which is now being used to extort Advarra
Even if the incident didn’t go down exactly as we think, there are a few takeaways:
- Social engineering has shown time and again to be the most reliable tool for cybercriminals. It can even hurt companies with enterprise grade security.
- The security of your private accounts matters to the company you work for. A breach of one of your accounts can provide an entrance to your employer.
- SIM swapping is one of the reasons why some forms of MFA are better than others. Spoiler alert: text messages and call-based verification are not the best options.
How to avoid ransomware
- Block common forms of entry. Create a plan for patching vulnerabilities in internet-facing systems quickly; and disable or harden remote access like RDP and VPNs.
- Prevent intrusions. Stop threats early before they can even infiltrate or infect your endpoints. Use endpoint security software that can prevent exploits and malware used to deliver ransomware.
- Detect intrusions. Make it harder for intruders to operate inside your organization by segmenting networks and assigning access rights prudently. Use EDR or MDR to detect unusual activity before an attack occurs.
- Stop malicious encryption. Deploy Endpoint Detection and Response software like Malwarebytes EDR that uses multiple different detection techniques to identify ransomware, and ransomware rollback to restore damaged system files.
- Create offsite, offline backups. Keep backups offsite and offline, beyond the reach of attackers. Test them regularly to make sure you can restore essential business functions swiftly.
- Don’t get attacked twice. Once you’ve isolated the outbreak and stopped the first attack, you must remove every trace of the attackers, their malware, their tools, and their methods of entry, to avoid being attacked again.
Malwarebytes Managed Detection and Response (MDR) simply and effectively closes your security resources gap, reduces your risk of unknown threats, and increases your security efficiency exponentially. Malwarebytes MDR staffs highly experienced Tier 2 and Tier 3 analysts who are hands-on with customer endpoints, ensuring critical threats are quickly identified and a thorough response is rapidly deployed.
Want to learn more about MDR? Get a free trial below.